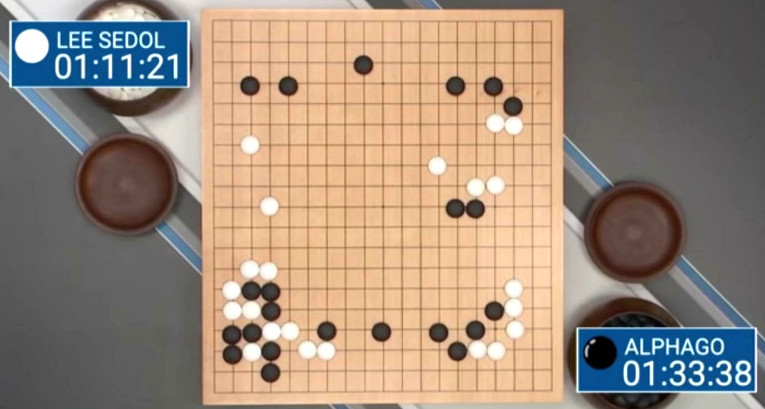
scientists predict human leven AI by 2047 so DON’T HOLD THE BREATH WHILE UNDOUBTATLY MACHINES ARE VERY FAST AT CALCULATING STUFF How many operations per second ((F)OPS) a human brain can do is up to debate + ongoing research, it […]
why are not more companies, schools, governments, banks using GNU Linux? Some might claim because of lack of standardization. but imho that is not true. from a biologists point of view biodiversity is actually a very good thing, as it […]
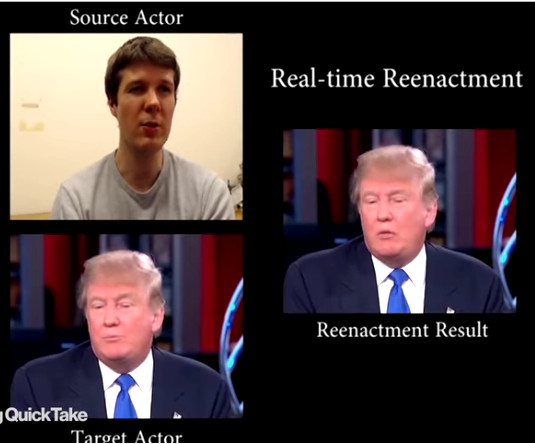
https://www.youtube.com/watch?v=UheOilps2zQ “know in some countries they believe Telegram is safe. I will show you how safe it is,” he said, before showing a screen in which he appeared to scroll through the Telegram contacts of one Kenyan strategist https://www.theguardian.com/world/2023/feb/15/revealed-disinformation-team-jorge-claim-meddling-elections-tal-hanan SS7 […]
scientists predict human leven AI by 2047 so DON’T HOLD THE BREATH It is a wrongful simplification to reduce humans to robots. No matter how much humans treat humans like robots (behaving like robots in the process), it does not […]
0) for security: keep all internet connected devices as up to date as possible! “Freifunk updates its router firmware and closes a critical security vulnerability that could allow attackers to install their own firmware on the devices” (src: heise.de) Also […]
the risks of all digital (no cash) payment systems & amok AI: “This happens quite often with customers of the Cashgroup banks (@DeutscheBank / @Postbank / @Commerzbank / @Comdirect) as soon as their algorithms hit your account is directly without […]
what is great about books vs blogs? (+) paper books don’t need electricity and hightech to function. energy grid and tcp networks (up to now) have worked pretty reliably, but at any given day, a massive solar flare or a […]
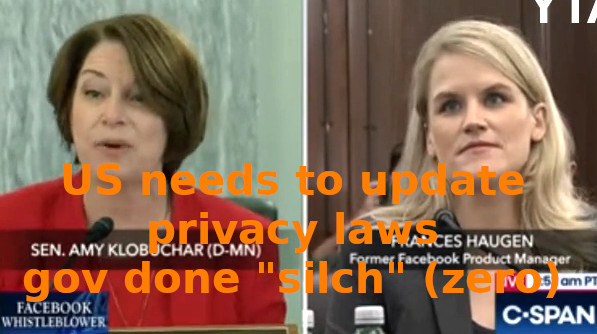
If the user got the time, watch parts of the full uncencored & uncut (thanks C-SPAN!) interview-testimony: https://ytpak.net/watch?v=GOnpVQnv5Cw Facebook/WhatsApp/Instagram and Telegram sideffects may include: ellection manipulation & manipulation of the masses massive intrusion of privacy (collect as much info as […]
the positive vision (always start with something positive) if big data about every keystroke every step we make (the police: every step you make) algorithms determine how mankind will live and thus: technology is “neutral” until it is used for […]
remember that discussion about ever changing non-standard ways of defining network interfaces and ip addresses under /etc/network… well guess what, canonical just came up with a completely new config file format X-D (guess, everything is a yaml.yml now) hostnamectl; # […]
app only? no browser support? not exactly click here: any tag topic can be seen in browser via: https://social.librem.one/tags/librem5 so it seeeems like these service are aimed at selling and be used mostly by app with the pretty expensive Librem […]
in short: humans per default, without an education might just be “better” apes. Some parts of mankind behave very primitive and clearly show no signs of higher intelligence or education. The troubles start, when the tools become more and more […]
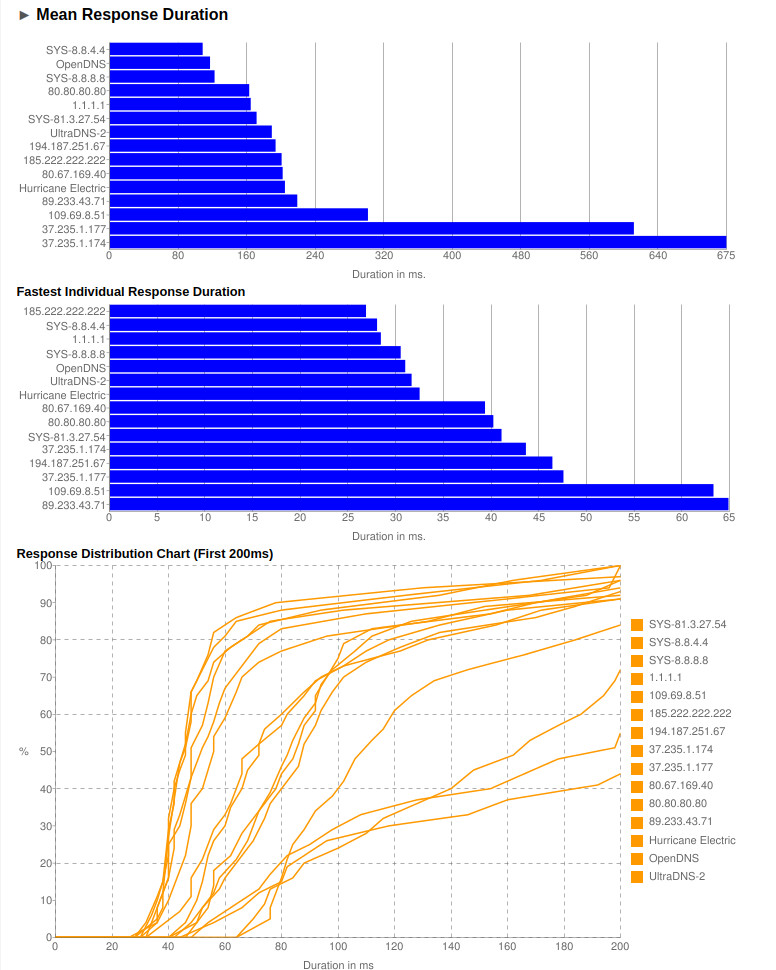
every user want’s a fast & responsive internet. BIND and DNS – the Phonebook of the internet – Berkeley Internet Name Domain – how to benchmark dns servers (find fastest) – LibreDNS There is nothing more anoying than slow loading […]
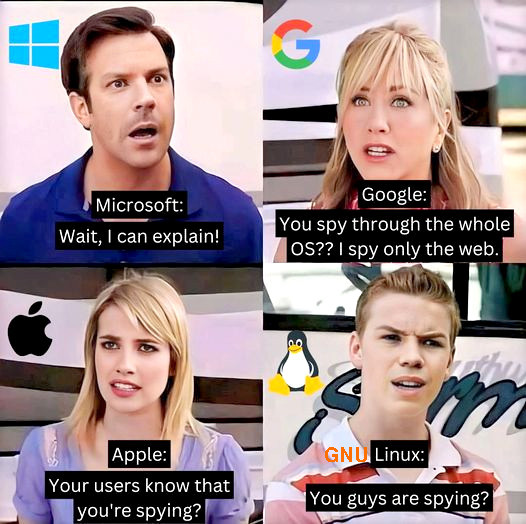
Apple wants to become the new Google: BigBadBoldBigDataMothership why more developers should chose GPL to publish programs: as a once proud Apple user… (yes GNU Linux Debian 10 actually runs pretty well on the Intel-Macbook-Pros) yes they are beautiful spies… […]
why are those data leaks problematic? because scammers and spammers will use this data to even better scam (social engineer) the affected users that is why it is essential to give those platforms (if the user needs them) as little […]
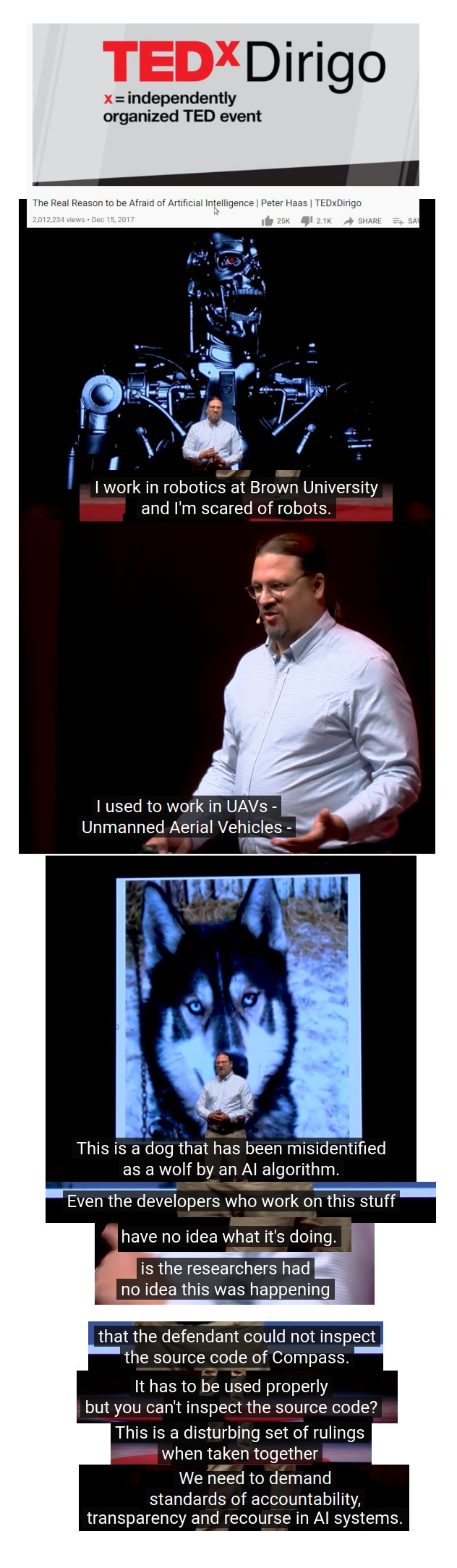
computers are no way perfect: the rise of the machines: who is scared of killer robots? who is scared of doctors, judges and police blindly trusting in AI and computer output? “we are driving in (heavy) rain right now with […]
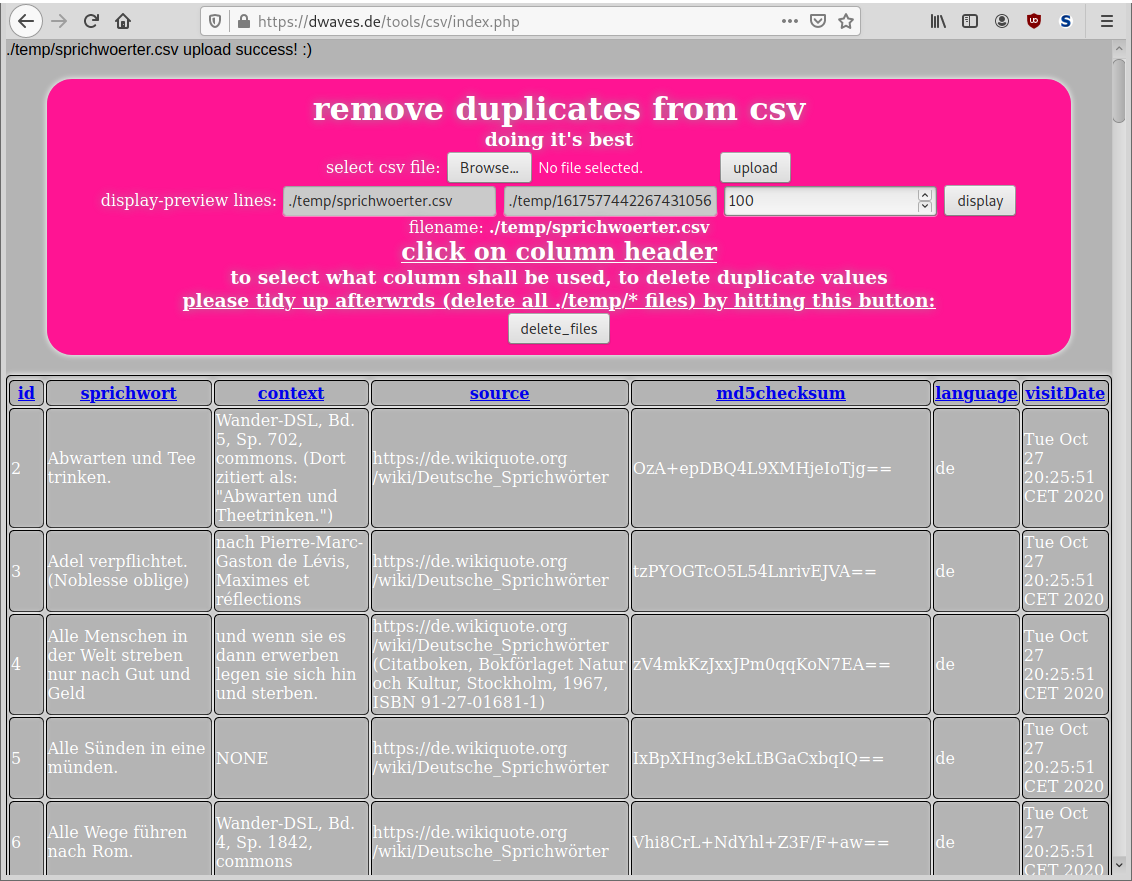
the task at hand ought to be a simple one… the user has a data table of some sort (a Excel sheet). and wants only unique data sets (no duplicates) in a certain column theoretically Libre Calc can do that, […]
Update: 2021-05: https://www.golem.de/news/irland-erste-patientendaten-im-netz-aufgetaucht-2105-156599.html Drei Krankheiten: erfolgreich kaputt gespart: schlechte Bezahlung: im Vergleich mit anderen EU-Ländern und auch USA steht Deutschland schlecht da was die Entlohnung von Ärzte an geht auch schlechter als Japan und gar Italien (!) das ist vermutlich […]
Cancer is a very depressing topic. Some say, the ONLY true cure for cancer is early detection and most healthcare systems around the globe are still pretty lousy at that. the positive the negative: bigdata + AI could help early […]
contains advertisement. to be honest, it is hard to keep up the speed at which cyber incidents are reported. here is the latest take on “Russian IT Sec Updates”. have phun! SecurityLab, [28.09.20 08:20] Last month, TikTok developers rolled […]
SecurityLab, [14.07.20 15:35] The Electronic Frontier Foundation (EFF) has unveiled a new database demonstrating how and where us law enforcement agencies use tracking technologies. A map of the use of tracking technologies in the United States is presented (https://www.securitylab.ru/news/510018.php) SecurityLab, […]
All SmartPhones are spies! that’s why Merkel keeps the Nokia from 1995 (even if that device is spied on as well, because it can not end2end encrypt sms or phone calls (*FAIL*! X-D)) Putin does not have a mobile phone […]
The Age of Surveillance Capitalism: “be careful what you reveal to your friend” (the internet) https://irlpodcast.org/season4/episode5/ “where it has gone from defending America to controlling it” data google tries to collect from users: (it is probably only the tip of […]
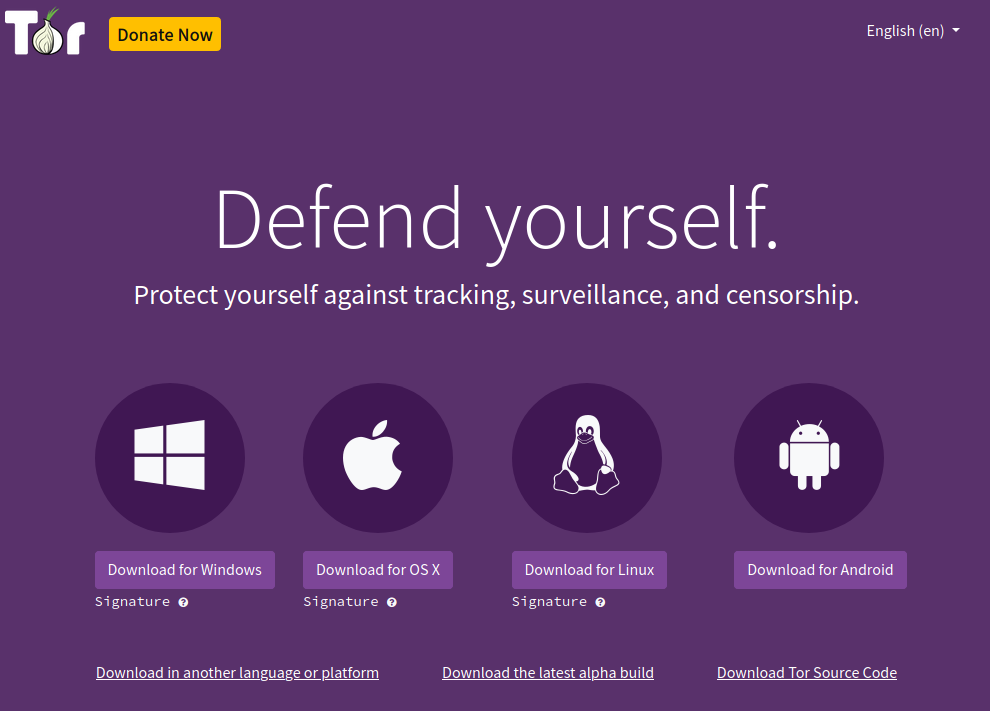
Tor is easier to use than ever superb usability! Tor is now super easy to use! (thanks all involved!) just get the tor bundle – it is tor bundled with firefox https://www.torproject.org/download/ Tor visualized: most users are legit: but criminals […]
As with all hot debated topics: Linus Torvald’s “show me the source” in this case, the source of one’s informations (always give the source!) is IMPORTANT for the information’s credibility. It is absolutely vital in science to give all sources […]
this really raises the question: the mobile (complete computer) phone (number) as key to everything? is it a good idea to rely on smart phones (that are essentially a very small laptop and a cellular modem) and phone numbers to […]
now WITH SPICY COMMENTS X-D SecurityLab, [22.12.19 12:40] A Twitter user using the alias 08Tc3wBB created tfp0-an exploit that allows you to jailbreak the latest iPhone models with IOS 13.3. The functionality of the exploit has already been confirmed by […]
apologize! games = windows, still ? (although there are 6000 steam games running on linux) the very first “Open Source GPU” is in the making: https://www.crowdsupply.com/libre-risc-v/m-class “The Libre RISC-V M-Class is a RISC-V chip that is libre-licensed to the bedrock. […]
i really like virtualbox and i think it has great potential, what i do not like SOOO much is the CIA’s involvement with Oracle. “Larry Ellison Is A Billionaire Today Thanks To The CIA” (src) VirtualBox is mostly GPL 2.0 […]
Update: 2021-02 “A statement from the German Federal Criminal Police Office about their participation in Operation Ladybird said prosecutors seized 17 servers in Germany that acted as Emotet controllers.” and many bars of gold and cash were seized in Ukraine… […]