the positive vision (always start with something positive) if big data about every keystroke every step we make (the police: every step you make) algorithms determine how mankind will live and thus: technology is “neutral” until it is used for […]
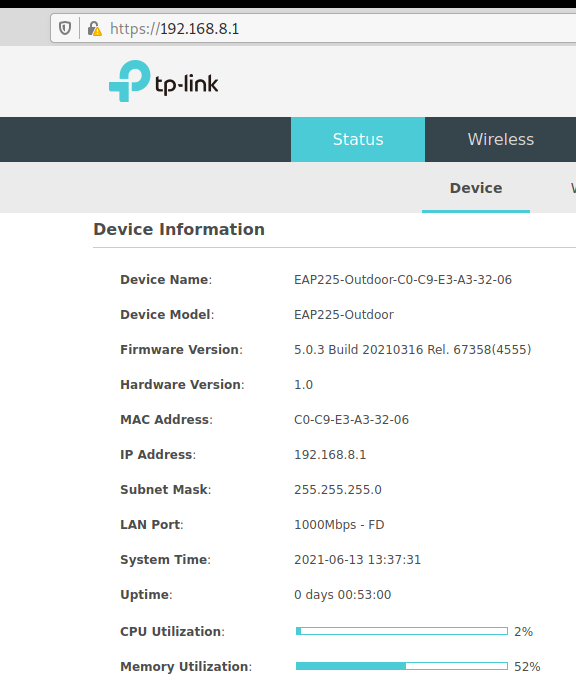
EDIMAX EW-7612UAn V2 THE ONLY (?) GNU Linux WIFI WLAN Adapter that works OUT OF THE BOX on all GNU Linux systems (ODROID RASPBERRY AND Desktop GNU Linux) How to created multiple Wifi AccessPoints connecting (WDS Wifi Bridge) to one […]
the story goes like this. multiple files were zipped under Windows 7 (Pro German/DE) and unzipped under GNU Linux Debian 10. The problem is: that the special chars of the filenames are all reported as “invalid encoding” (within the MATE […]
SecurityLab, [22.12.20 10:00] Google has explained the reasons for the massive failure of its services that took place last week. Recall that on December 14 of this year, users around the world for 47 minutes could not access Gmail, YouTube […]
Overview Recent 360Netlab unknown threat detection system to capture to a group of unknown malicious families of the sample, which a number of samples supported CPU architectures are x86(32/64), ARM(32/64), MIPS(MIPS32/MIPS-III) as well as PPC, after our analysis, which is […]
contains advertisement. to be honest, it is hard to keep up the speed at which cyber incidents are reported. here is the latest take on “Russian IT Sec Updates”. have phun! SecurityLab, [28.09.20 08:20] Last month, TikTok developers rolled […]
finally summer and climate change have both reached Europe and had several weeks of 30 C straight… without ventilation, anything above 30 is just “too much to think” (so maybe the brain CPU also would need active cooling?) of course […]
SecurityLab, [14.07.20 15:35] The Electronic Frontier Foundation (EFF) has unveiled a new database demonstrating how and where us law enforcement agencies use tracking technologies. A map of the use of tracking technologies in the United States is presented (https://www.securitylab.ru/news/510018.php) SecurityLab, […]
this age of mass surveillance… … who is observing “the observers”? guess with it-security and internet-security (internet = roads, cars = computers that users use every day) it is like with real-life-security – there is no 100% security. all users […]
this really raises the question: the mobile (complete computer) phone (number) as key to everything? is it a good idea to rely on smart phones (that are essentially a very small laptop and a cellular modem) and phone numbers to […]
now WITH SPICY COMMENTS X-D SecurityLab, [22.12.19 12:40] A Twitter user using the alias 08Tc3wBB created tfp0-an exploit that allows you to jailbreak the latest iPhone models with IOS 13.3. The functionality of the exploit has already been confirmed by […]
“In the popular series of wireless keyboards Fujitsu LX390 found two dangerous vulnerabilities. According to researchers from the company SySS, exploitation of vulnerabilities allows nearby attackers to “spy” passwords entered on the keyboard, or even to seize control of the […]
Update: 2021-02 “A statement from the German Federal Criminal Police Office about their participation in Operation Ladybird said prosecutors seized 17 servers in Germany that acted as Emotet controllers.” and many bars of gold and cash were seized in Ukraine… […]
THE ECB BIRD WAS HACKED! “however, the internal system of the Bank has not been compromised” the site http://www.banks-integrated-reporting-dictionary.eu/ was taken offline. It is fascinating. The Europeans probably do not even know about “what is going on” and according to ex […]
is Rust safer than C/C++? “show me the src” https://github.com/rust-lang https://github.com/rust-lang/rust/tree/master/src DebConf 2019: Why would a python programmer learn rust when there are no jobs in it https://ytpak.net/watch?v=IYLf8lUqR40 “This means no matter what language you use, the only safe way […]
screw Qualcomm, what one wants is should work out of the box with recent Linux kernels on Open Source drivers only: https://dwaves.de/2019/07/03/recommended-tested-hardware-superb-wifi-wlan-adapter-chipset-atheros-ar9285-mini-pcie-for-gnu-linux-debian-10-ubuntu-and-trisquel-8-0-test-run-on-lenovo-t440-and-librebooted-lenovo-x60s/ as far as i understand this… if you are concerned about the security of your phone… (banking apps… […]
“Linux desktop remains an unpopular choice among mainstream desktop users, making up a little more than 2% of the desktop operating system market share. This is in contrast to the web server market share, which consists of 70% of Linux-based operating systems. […]
Capitalism inspires the short sighted incentives. But trust and honesty is key in long term relationships. So for a short period of time – some dishonest people might enjoy the benefits – but in the end – it comes home […]
don’t be evil “Google controls about 62% of mobile browsers, 69% of desktop browsers, and the operating systems on 71% of mobile devices in the world. 92% of internet searches go through Google and 73% of American adults use YouTube. […]
it might sound strange… and even if it sucks, but if you are concerned about security, call me paranoid but: your company’s critical infrastructure SHALL NOT BE REACHABLE BY WIFI! (especially not if you are running a nuclear power plant, […]
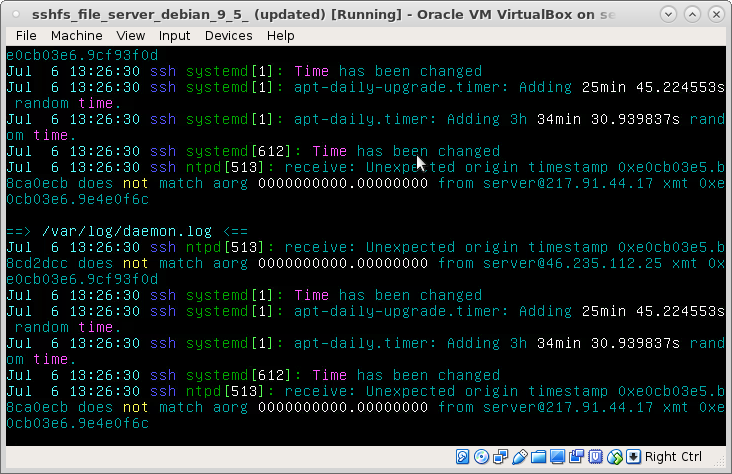
servers/clients/computers/programs/services/webservers need accurate time… they usually get it from time servers that have an atomic clock attached to their USB port. (just guessing) ping time.google.com PING time.google.com (216.239.35.4) 56(84) bytes of data. 64 bytes from time2.google.com (216.239.35.4): icmp_seq=1 ttl=46 time=43.5 […]
Pwn2Own 2020: opening a pdf can be enough to compromise system! https://youtu.be/u1udr7j9MQA?t=359 thank you ccc you are doing a lovely work – make this planet more interesting by creativity and more informed about security 🙂 keep it up 🙂 https://cdn.media.ccc.de/events/gpn/gpn19/h264-hd/gpn19-45-eng-BADPDF_-_Stealing_Windows_Credentials_via_PDF_Files_hd.mp4 […]
Update: 2020.03 “The newly developed Rowhammer- attack TRRespass can crack the RAM-a security mechanism by many DDR4-DRAM-modules as well as LPDDR4 Chips. Until now, these were considered to be almost immune to Rowhammer attacks.” https://www.com-magazin.de/news/sicherheit/software-hammer-ram-schutz-attackiert-2515621.html Update: 2019.10 Zombieload is back. […]
scroll down for ENGLISH: ) OMG! Da die IT von Baltimore sich einen Ransome-Virus eingefangen hat, können die Bürger ihre Steuern und ihre Blitzer-Tickets nicht zahlen! Wunderbar! 🙂 Mit welchem Aufwand man rechnen muss, wenn man sich von der Digitalisierung […]
the best about samba: thanks for samba, it provides users with a fast (of course depends also on harddisk speed) rock-solid no-limit-to-maximum-users file-server for maximum file-transfer-and-sharing-and-storage productivity (and they will USE that T: temp drive for EVERYTHING! prepare for TERRABYTES […]
google’s security lab “project zero“ has made itself a name. (you can subscribe to their rss feed with thunderbird.) Posted by Ben Hawkes, Project Zero (team lead) (2019-05-15) Project Zero’s team mission is to “make zero-day hard”, i.e. to make […]
to be straight: have not managed yet to unlock a pin locked ipad 3 and ipad 4 and/or recover the data. it is easy to just overwrite the ipad with the latest firmware via itunes. but i want to backup […]
It is one of the most critical of digital infrastructures – update servers – thus vendors need to be EXTREEEEMELY careful how they run their update servers. they could get hacked and their downloads and updates get virus and backdoor […]
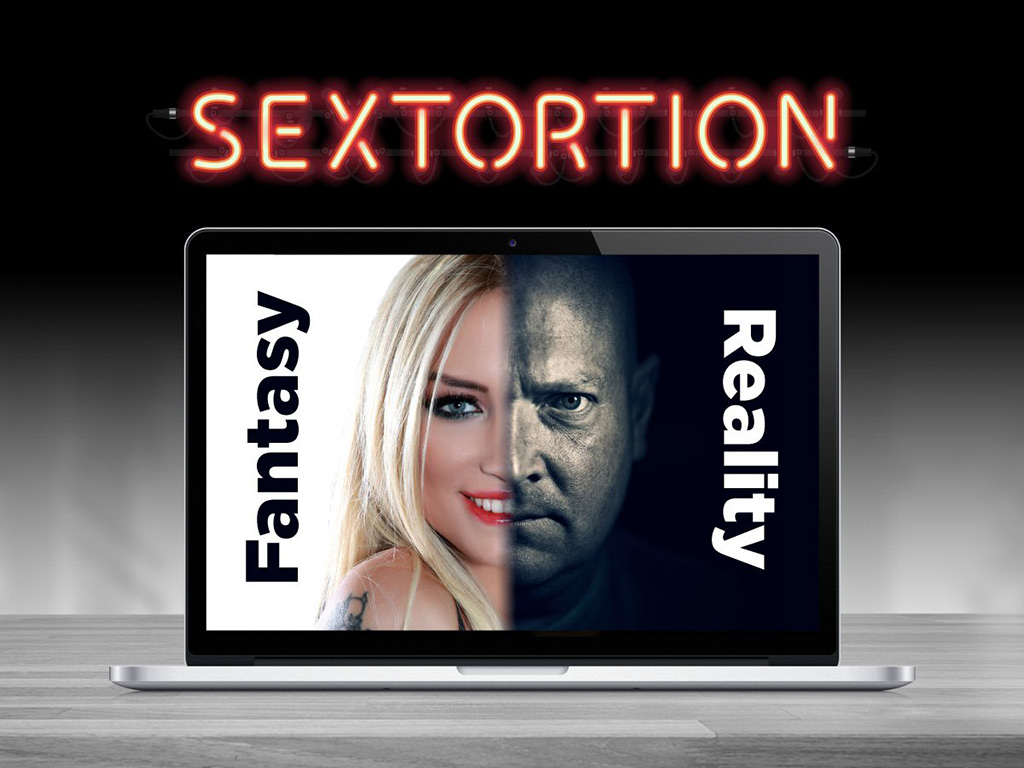
this is probably the most evil way of social engineering: fear makes a lot of money – but it can even kill already traumatized people. It works like this: criminals create fake profiles on dating sites / facebook / twitter […]
Unknown stole $7.7 million in cryptocurrency EOS 28 February, 2019 News Support 0 comments The attacker managed to steal $7.7 million in cryptocurrency EOS due to the negligence of one of the managers a black list. Hacking became known on […]