LANCOM is not so well known German company that is the partner when it comes to “business” DSL routers for Telekom and T-Systems customers and as such they are conducting the worst closed source rippoff of their customers possible. multiple […]
mass surveillance is real & cencorship is real: Why does Google hate Tor? Because Google is a mass-surveillance AI. And surveillance hates anonymizing networks such as Tor. That’s why the visitor of this website SHOULD donate to Tor and Signal […]
one fine day, DNS stopped working. the reason this time was NOT on the server-side, but on the Google side, blocking all DNS servers that are NOT google. while this can be understood in the terms of CyberSec: + (manipulation […]
Efficiency is good in terms of: saving resources. Same results with less (power and other) input. BUT: good people need to be cultivated, by culture. Culture does not simply mean “gifts on Christmas” and “Lederhosen”. (that’s what it has become, […]
Open Source is about enabling users “Amazon, Microsoft, Google” and the White House, want to help make Open Source more secure… https://www.golem.de/news/openssf-150-millionen-us-dollar-sollen-open-source-absichern-2205-165382.html https://www.golem.de/news/openssf-linux-foundation-will-security-praxis-vereinheitlichen-2008-150036.html src of src: “White House OSS Mobilization Plan” 2022: https://openssf.org/blog/2022/05/11/testimony-to-the-us-house-committee-on-science-and-technology/ 2020: “The OpenSSF is a cross-industry collaboration […]
what is great about books vs blogs? (+) paper books don’t need electricity and hightech to function. energy grid and tcp networks (up to now) have worked pretty reliably, but at any given day, a massive solar flare or a […]
in short: humans per default, without an education might just be “better” apes. Some parts of mankind behave very primitive and clearly show no signs of higher intelligence or education. The troubles start, when the tools become more and more […]
Apple wants to become the new Google: BigBadBoldBigDataMothership why more developers should chose GPL to publish programs: as a once proud Apple user… (yes GNU Linux Debian 10 actually runs pretty well on the Intel-Macbook-Pros) yes they are beautiful spies… […]
it sounds crazy but… as machines as cars and tractors become more complicated and computerized not only are their parts DELIBERATELY designed to break after a certain time (planned obsolescence) (in order to sell more spare parts, make more profit) […]
why are those data leaks problematic? because scammers and spammers will use this data to even better scam (social engineer) the affected users that is why it is essential to give those platforms (if the user needs them) as little […]
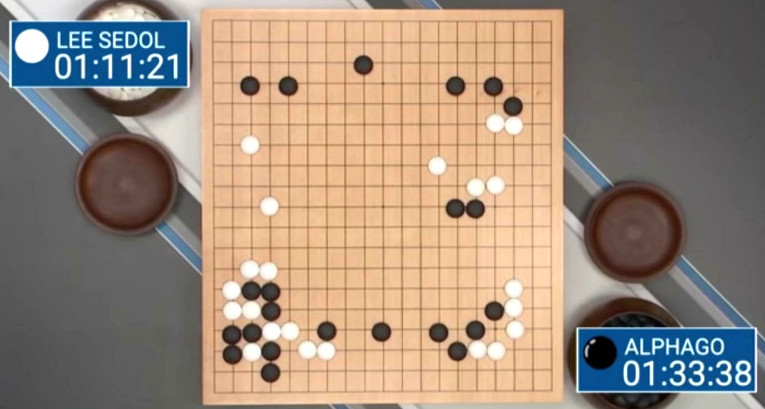
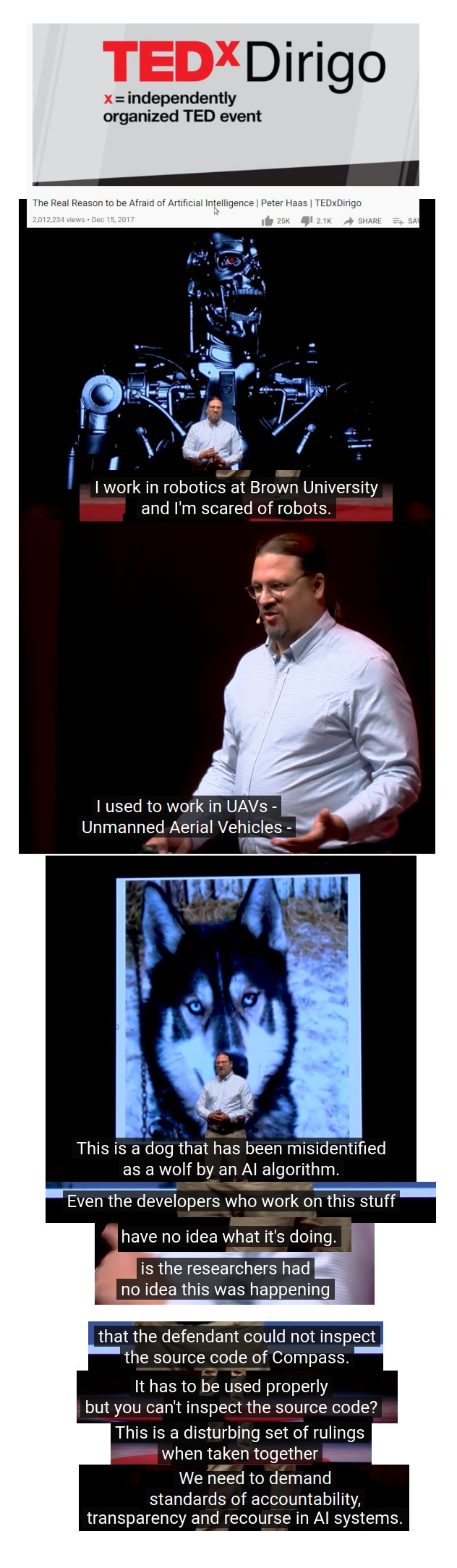
computers are no way perfect: the rise of the machines: who is scared of killer robots? who is scared of doctors, judges and police blindly trusting in AI and computer output? “we are driving in (heavy) rain right now with […]
SecurityLab, [22.12.20 10:00] Google has explained the reasons for the massive failure of its services that took place last week. Recall that on December 14 of this year, users around the world for 47 minutes could not access Gmail, YouTube […]
not sure if the news rang through… the Amazon Cloud (AWS) guy will be the new CEO of Amazon. What cloud? Amazon “cloud” Hetzner “cloud” cloud (centralized digital infrastructure) can be designed / implemented in different ways. from: the user/admin […]
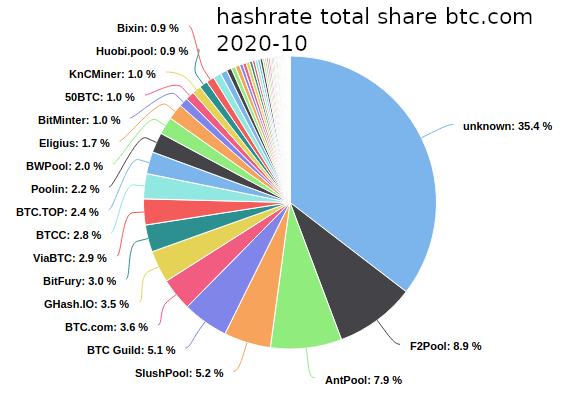
Bitcoin’s annual electricity consumption adds up to 45.8 TWh (45.800.000.000 kWh) The corresponding annual carbon emissions range from 22.0 to 22.9 MtCO2 This level sits between the levels produced by the nations of Jordan and Sri Lanka src: https://www.sciencedirect.com/science/article/pii/S2542435119302557 a […]
this age of mass surveillance… … who is observing “the observers”? guess with it-security and internet-security (internet = roads, cars = computers that users use every day) it is like with real-life-security – there is no 100% security. all users […]
update: “The sale was met with significant opposition since it involved the transfer of what is viewed as a public asset to a private equity investment firm.[45] In late January 2020, ICANN halted its final approval of the sale after […]
how can everyone help? Musk: talk about it! 🙂 spread the news! set the focus! cognitive disconnectedness between governments and science: the non-sustainability mess Let’s face it… the fossil fuel powered steam engine economy … once started… is very hard […]
Update: 2021-02 “A statement from the German Federal Criminal Police Office about their participation in Operation Ladybird said prosecutors seized 17 servers in Germany that acted as Emotet controllers.” and many bars of gold and cash were seized in Ukraine… […]
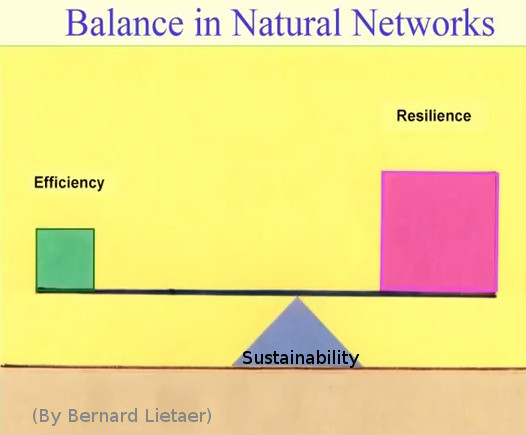
what IT can learn from nature: (src) mostly US users affected. Big Business: Big Companies and Big Money can afford Big Staff to maintain and secure their products, but they also provide Big Infrastructure (AWS, Office) and thus a single […]
don’t be evil “Google controls about 62% of mobile browsers, 69% of desktop browsers, and the operating systems on 71% of mobile devices in the world. 92% of internet searches go through Google and 73% of American adults use YouTube. […]
scroll down for ENGLISH: ) OMG! Da die IT von Baltimore sich einen Ransome-Virus eingefangen hat, können die Bürger ihre Steuern und ihre Blitzer-Tickets nicht zahlen! Wunderbar! 🙂 Mit welchem Aufwand man rechnen muss, wenn man sich von der Digitalisierung […]
20-30% of positive ratings as well as negative ratings (to make competition look bad) are fake! according to gallileo magazine this website tries to filter/debunk the fake from the real ratings: https://reviewmeta.com/
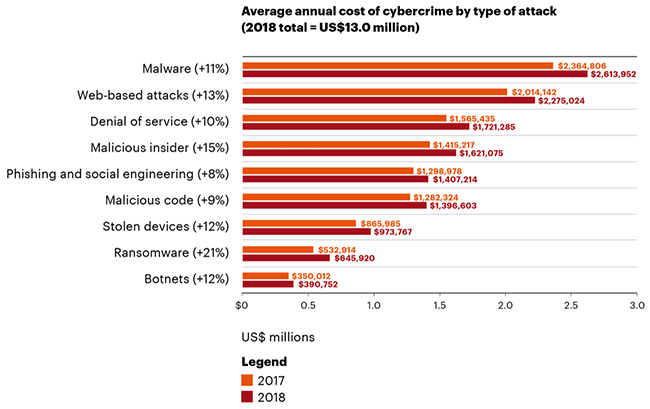
“The cost to companies from malware and “malicious insider”-related cyberattacks jumped +12 percent in 2018 and accounted for one-third of all cyberattack costs, according to new research published today by Accenture and the Ponemon Institute.” src: helpnetsecurity.com logical consequence: stop […]
is when one’s life depends on (especially when closed) source code that one has not written oneself.
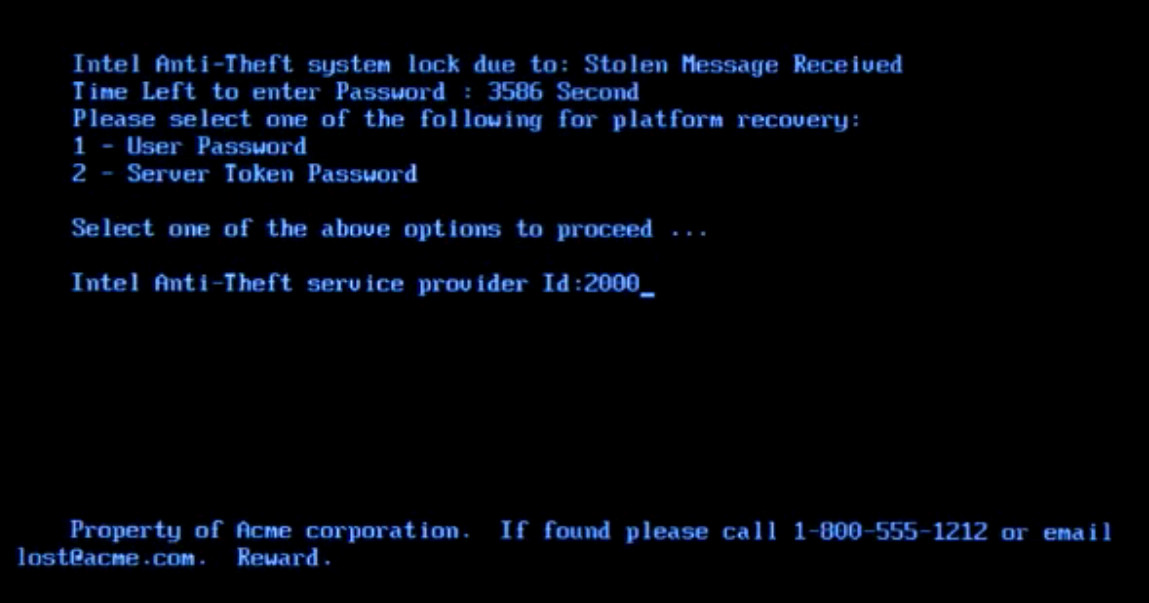
https://youtu.be/70Blz9hyAz8 https://devtube.dev-wiki.de/videos/watch/f979469f-5fd1-4c40-a8c4-706c20c001f7 While “backdoors” in hardware sound like a good idea… you don’t know how hackers are using it to sabotage infrastructure or extort bitcoins of another country’s companies… see “backdoor in cisco router“. IT IS F**** DANGEROUS! ESPECIALLY if […]
checkout the space weather today 🙂 “Schwabe cycle, is a nearly periodic 11-year change in the Sun’s activity” (src) but the sun’s particles ALSO shield from even more outer space radiation BUT the sun is ALSO protecting Earth & Mars […]
70% of decision makers increase tech budget in 2018, slightly higher than 2017. top technologies: CyberSecurity (53%) Hardware upgrades (47%) cloud services (43%) software (40%) BigData Analytics (20%) Internet of Things (18%) 35% training employees 29% want to hire new […]