BIT FLIPS are a COMMON thing in the universe 😀 so EEC RAM ACTUALLY MAKES SENSE 😀 “Studies by IBM in the 1990s suggest that computers typically experience about one cosmic-ray-induced error per 256 megabytes of RAM per month”[15] As […]
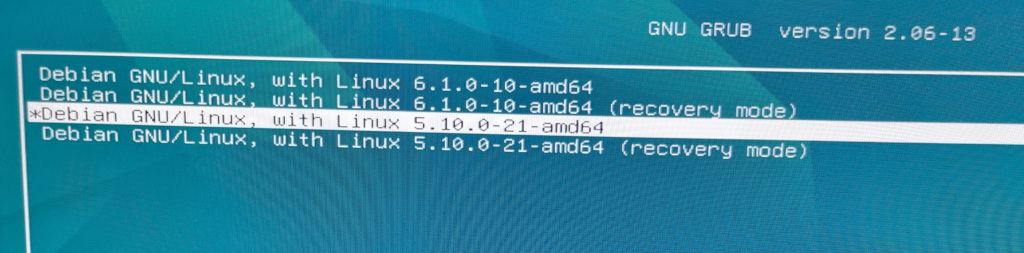
“os-prober is disabled with the grub 2.06 upload, which is obviously a bit controversial and the outcome is not necessarily in the best interest of our users” “os-prober is inherently insecure as it mounts all partitions on your disk using […]
Musk grabbed deeply into the Toilet, by wasting Billions on it’s twitter buy, he could have build 100x Twitters from scratch, with this amount of money. Understanding Elon Musk – (the day Elon almost destroyed Tesla by accident) – good […]
why it’s really time to occupy Mars & how the internet has changed post-babyboomer attitude to sharing Had an interesting conversation with a 65 year old, babyboomer, who has never personally seen war and who has not grown up with […]
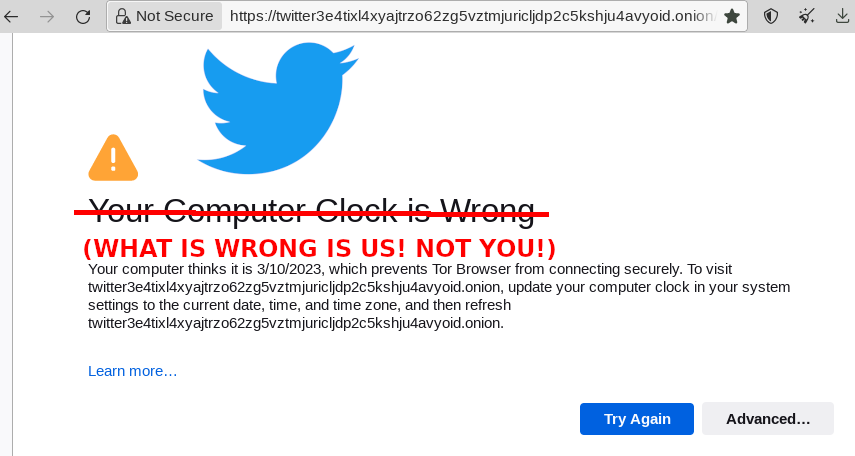
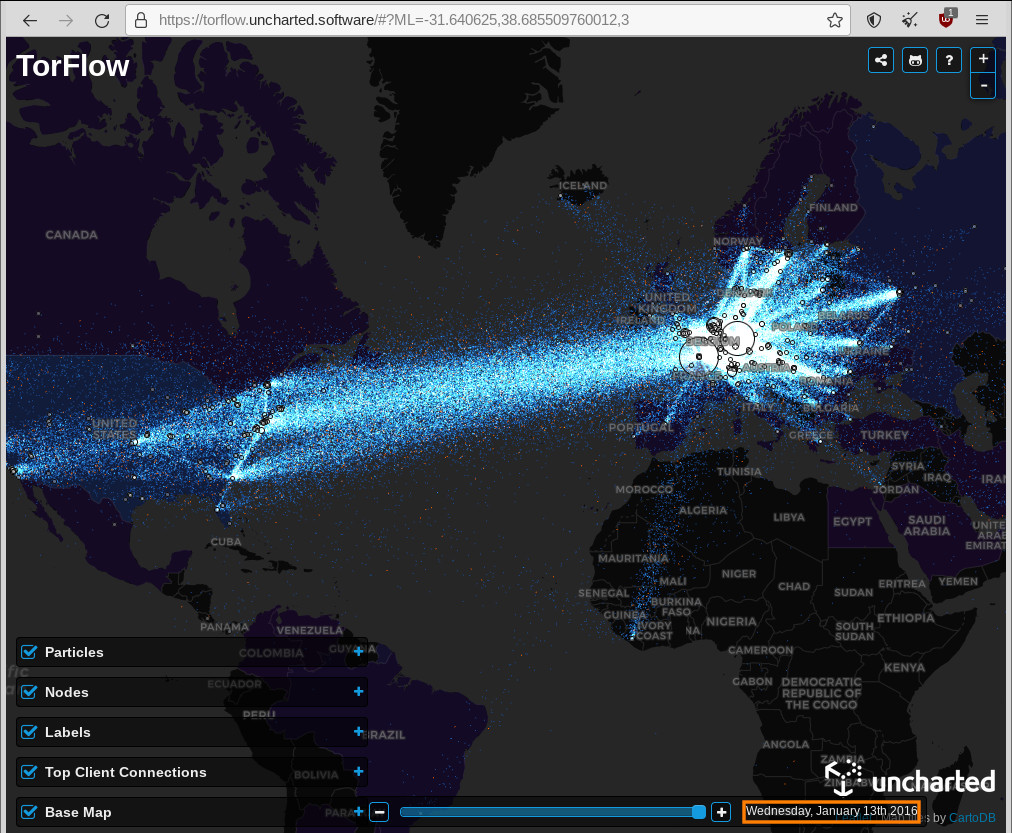
have to give a HUGHE praise to the Tor Project! just checked and they DO AN EXCELLENT job at keeping the user private the developers who constantly work to make the system better the thousands of volunteering admins that run […]
an new wallbox needs to be jumper reset, otherwise it won’t be recognized by “SixAbCon.exe” the tool to setup new devices for Sidexis the service pwd is the first 4 digits of the current date, backwards this is from […]
as most users know, Ubuntu (a Nguni Bantu term meaning “humanity”) is, still (luckily) based on GNU Linux Debian. But more software is not necessarily better. What Ubuntu nicely does: more recent kernel it aims for even greater hardware compatibility […]
Open Source is about enabling users “Amazon, Microsoft, Google” and the White House, want to help make Open Source more secure… https://www.golem.de/news/openssf-150-millionen-us-dollar-sollen-open-source-absichern-2205-165382.html https://www.golem.de/news/openssf-linux-foundation-will-security-praxis-vereinheitlichen-2008-150036.html src of src: “White House OSS Mobilization Plan” 2022: https://openssf.org/blog/2022/05/11/testimony-to-the-us-house-committee-on-science-and-technology/ 2020: “The OpenSSF is a cross-industry collaboration […]
will be redone soon
to swap or not to swap? That is the question. definitely define a large swap space (3x or 4x times RAM) unless the user has a really good reason (like not enough harddisk space) for example: without insane amounts of […]
criminals abusing tor for malicous behavior should be blocked, right? “50% of the attacks are leveraging the Tor anonymity service to mask their true origins” https://thehackernews.com/2021/12/new-local-attack-vector-expands-attack.html this could destroy the “honest” part of the network that truly exists, because it […]
Motorola, Apple, Samsung, and now even Fairphone 4: NO 3.5mm headphone jack!!! For the audio junkies among us, this is a no go. Was so looking forward to the Fairphone, but will probably use a phone with audio jack as […]
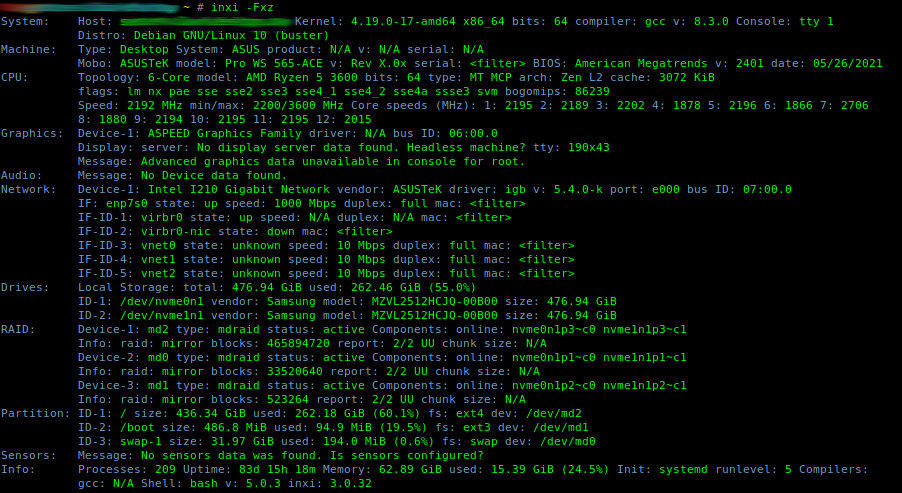
inxi – Command line system information script for console and IRC DESCRIPTION It is also used a debugging tool for forum technical support to quickly ascertain users’ system configurations and hardware. inxi shows system hardware, CPU, drivers, Xorg, Desktop, Kernel, […]
team, team, team team… In Germany, everyone is his/her own team, there are only one-man, one-woman teams. teams not necessarily help each other the best “help” you can get from another “team” is “it is somewhere in the (incomplete, outdated, […]
how to fix stuck permanent function (Fn) key BIOS / Firmware updates: but why? if everything works, vendors often say “leave it like that” because updates can have unforseen sideeffects and not all computers are “exactly” the same X-D (a […]
in short: humans per default, without an education might just be “better” apes. Some parts of mankind behave very primitive and clearly show no signs of higher intelligence or education. The troubles start, when the tools become more and more […]
it sounds crazy but… as machines as cars and tractors become more complicated and computerized not only are their parts DELIBERATELY designed to break after a certain time (planned obsolescence) (in order to sell more spare parts, make more profit) […]
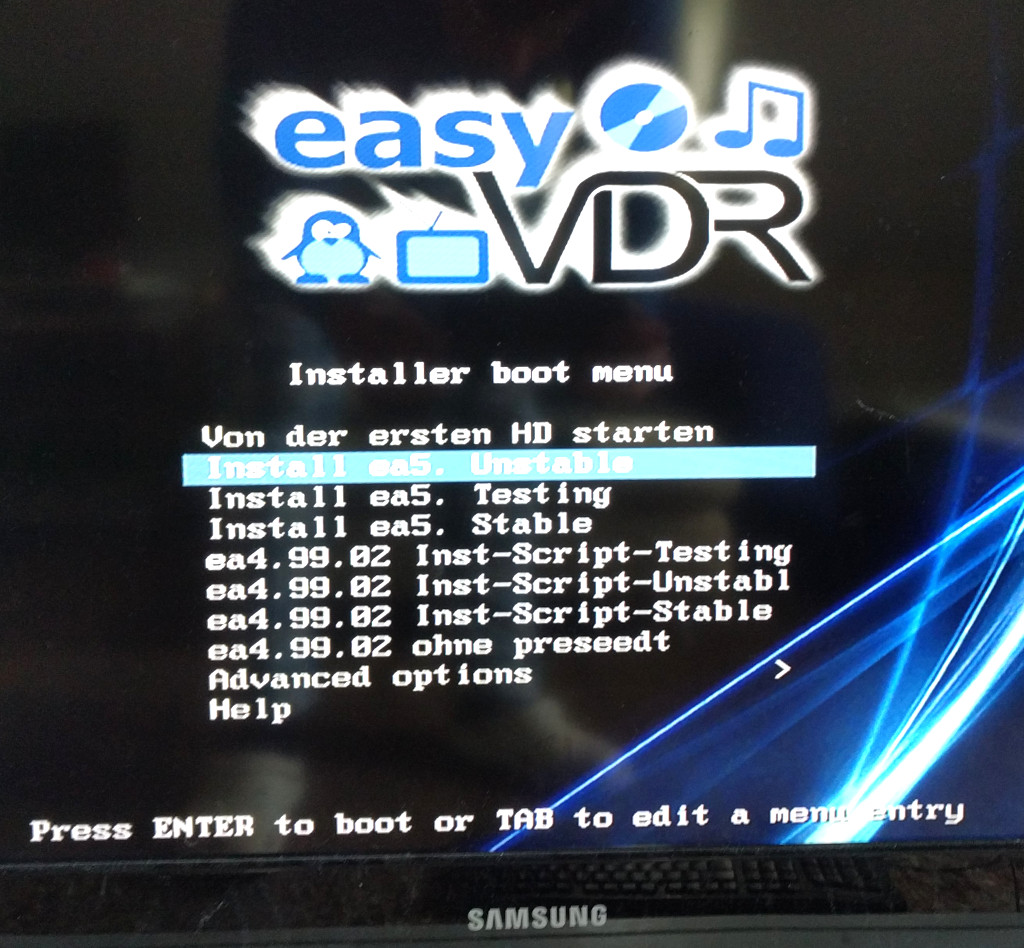
long story… good alternative? https://minidvblinux.de/ having had various frustrating experiences with the topic: TV + PC (even tried a cheap DreamBox 520 HD from eBay… which are probably good devices, but this one turned out to be faulty/unstable) now… in […]
the story goes like this. multiple files were zipped under Windows 7 (Pro German/DE) and unzipped under GNU Linux Debian 10. The problem is: that the special chars of the filenames are all reported as “invalid encoding” (within the MATE […]
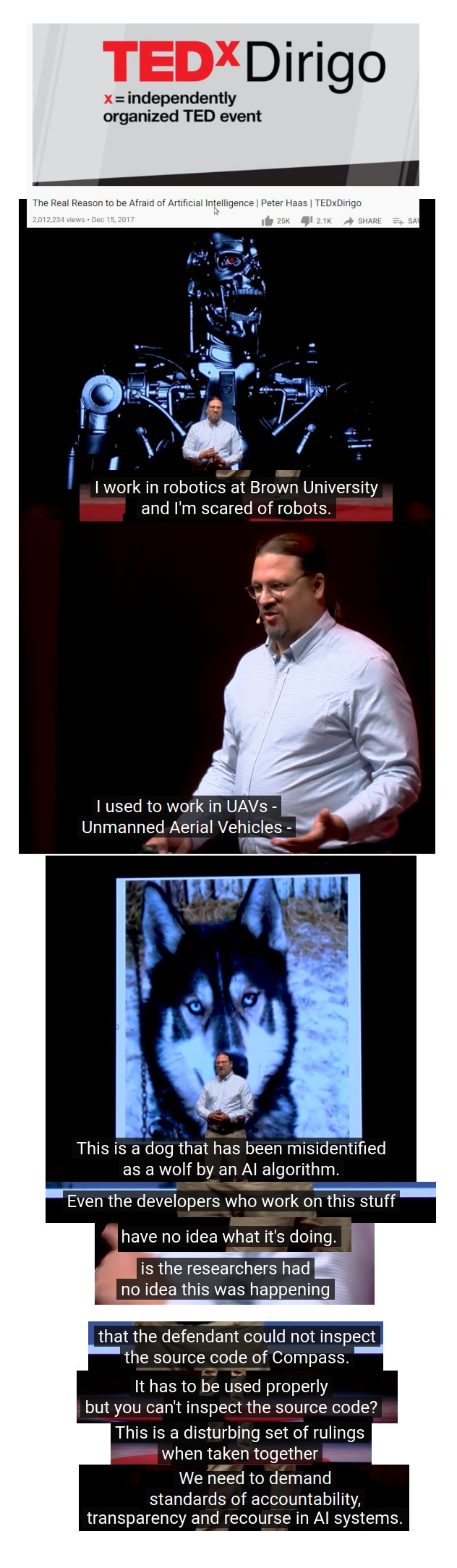
computers are no way perfect: the rise of the machines: who is scared of killer robots? who is scared of doctors, judges and police blindly trusting in AI and computer output? “we are driving in (heavy) rain right now with […]
… because one also cares about beauty… a default avatar picture is not an option… but phpBB has a very strict 6KBytes max file size limit for Profile Avatar Pictures… which is almost impossible to reach with format.jpg or format.png […]
some gui programs like gparted (very nice harddisk partitioning program) won’t start as root. hostnamectl; # tested on Operating System: Debian GNU/Linux 10 (buster) Kernel: Linux 4.19.0-13-amd64 Architecture: x86-64 su – root; # become root gvim; # fails with E233: […]
to recover the data: how to mount luks2 encrypted volume also check out alternative: GNU Linux – create new encrypted partition harddisk – how to open encrypted harddisk partition possibility: remove harddisk, attach to sata2usb adapter, then mount on different […]
in short: STAY AWAY FROM IT! all in all this mp3 player is a waste of resources and the user’s time (unless someone comes along and fixes the firmware X-D (but the playback problem could also be “in hardware”)) what […]
first some praise: the maintainers of grub did their best they could to bring about a great piece of software, no doubt about that. the question is: could less be more? when Greg Kroah-Hartman suggested to get rid of the […]
this age of mass surveillance… … who is observing “the observers”? guess with it-security and internet-security (internet = roads, cars = computers that users use every day) it is like with real-life-security – there is no 100% security. all users […]
Warning! This is probably not THE best solution and rather a dirty hack. Updates only should come via yum package manager and official repositories. After update, Telegram stops working. first thing one does is open up a terminal, and try […]
two neat tools to preview fonts hostnamectl; # tested with Operating System: Debian GNU/Linux 10 (buster) Kernel: Linux 4.19.0-18-amd64 Architecture: x86-64 su – root apt update apt install font-manager creditz: https://manned.org/font-manager/0194121f apt install font-manager gnome-font-viewer creditz: https://blogs.gnome.org/jamesh/ Adding new […]
Another reason to NOT trust EVERY human task to machines… unless one wants to get killed by a robot dressed up as dinosaur. “great” X-D “Japanese travel agent H. I. S. Group ignored warnings about a vulnerability in its Tapia […]
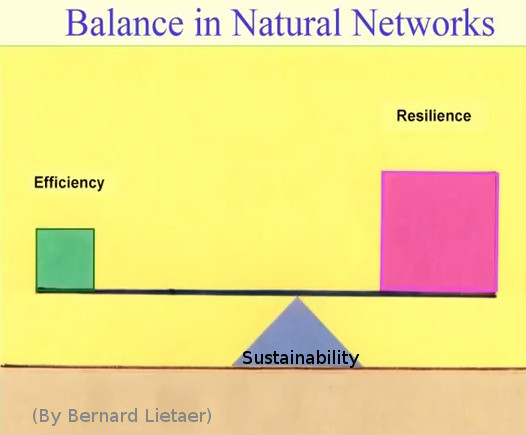
what IT can learn from nature: (src) mostly US users affected. Big Business: Big Companies and Big Money can afford Big Staff to maintain and secure their products, but they also provide Big Infrastructure (AWS, Office) and thus a single […]