“In an FFTF article published right after the vote, the group said that the elimination of the FCC’s privacy rules will allow ISPs to: Monitor and sell all your location data search history app usage and browsing habits to advertisers […]
network mac’s are used to uniquely identify systems and users and thus a privacy problem so mac randomization should be enabled per default on every distribution for every wifi network card (maybe interactively during setup ask the user to enable […]
this blog does not get tired of testing Android ROMS that enhance privacy 🙂 (actually it would be nice, if software support for those devices is at least 10 years X-D because it is a constant tiresome race) Yes it […]
want to see what’s going on in the Open Source part of Android OS? e-OS is available for many many (but not all) devices here is a detailed review of the ROM in terms of privacy. IT IS AN EXCELLENT […]
Paying taxes is no fun Paying taxes double and tripple is even less fun. Because let’s face it: when buying a pair of NEW shoes in Germany the average German Joe already pays at least 19% MwSt. plus the income […]
https://www.youtube.com/watch?v=UheOilps2zQ “know in some countries they believe Telegram is safe. I will show you how safe it is,” he said, before showing a screen in which he appeared to scroll through the Telegram contacts of one Kenyan strategist https://www.theguardian.com/world/2023/feb/15/revealed-disinformation-team-jorge-claim-meddling-elections-tal-hanan SS7 […]
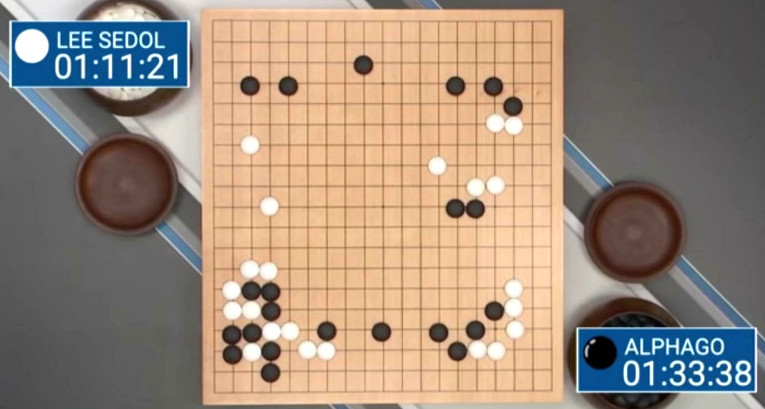
scientists predict human leven AI by 2047 so DON’T HOLD THE BREATH it is no news: that at some tasks computer+programs have outperformed humans, that is: at math and remembering things 1997: Deep Blue “AI” outperforms best human player at […]
the user has to know, that Mozilla is very much (still) dependant on Google’s money. in 2021 wrote this article. “Open Letter to Mozilla – Google’s Browser dominance – is Firefox not listening to user’s needs/requests?” They at least – […]
the positive: Okay let’s ALWAYS focus on the positive first: data, the web, free flow of information has given mankind new abilities: online learning-from-each-other (“social learning” one of said to be strong points of humans vs animals) better decision making […]
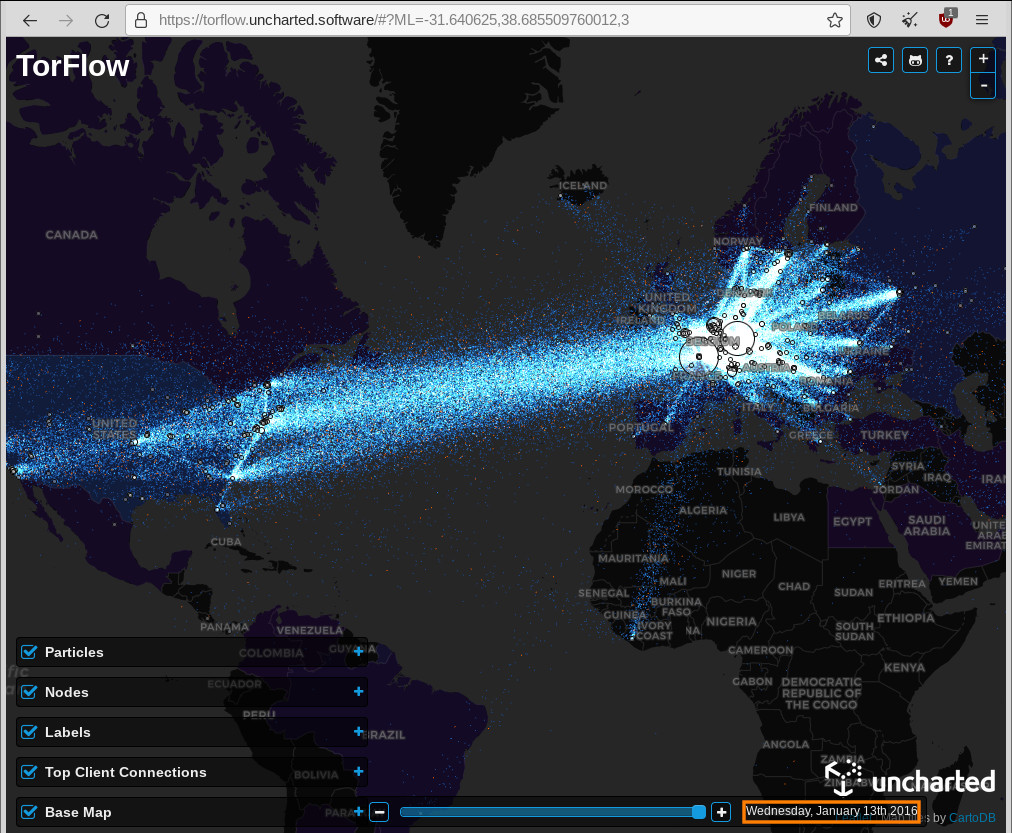
have to give a HUGHE praise to the Tor Project! just checked and they DO AN EXCELLENT job at keeping the user private the developers who constantly work to make the system better the thousands of volunteering admins that run […]
“Von der Leyen under pressure: The head of the EU Commission refuses to release text messages about the expensive vaccine deal with Pfizer. She is accused of lack of transparency.” (src) (here is the full New York Times article on […]
both are centralized Messengers meaning: the user is in control of the device + software (to the extend that the user can understand the src) Android-Client “the client” 100% Open Source (Java 70.8% Kotlin 29.1%) iOS-Client 100% Open Source (Swift […]
“know in some countries they believe Telegram is safe. I will show you how safe it is,” he said, before showing a screen in which he appeared to scroll through the Telegram contacts of one Kenyan strategist https://www.theguardian.com/world/2023/feb/15/revealed-disinformation-team-jorge-claim-meddling-elections-tal-hanan
this has to do with Caja calculating thumbnails for EVERY (!!!) picture ever found in a folder that matches the “below this and that file size” settings. having a picture “preview” possibility in a file manager is neat but if […]
mass surveillance is real & cencorship is real: Why does Google hate Tor? Because Google is a mass-surveillance AI. And surveillance hates anonymizing networks such as Tor. That’s why the visitor of this website SHOULD donate to Tor and Signal […]
one fine day, DNS stopped working. the reason this time was NOT on the server-side, but on the Google side, blocking all DNS servers that are NOT google. while this can be understood in the terms of CyberSec: + (manipulation […]
“the internet”, “wifi”, all “electronic communication via air and wires” As with all new technologies, Einstein was hopeful, that this new technology will be used for good to bring peace by better understanding between nations and individuals alike. Of course […]
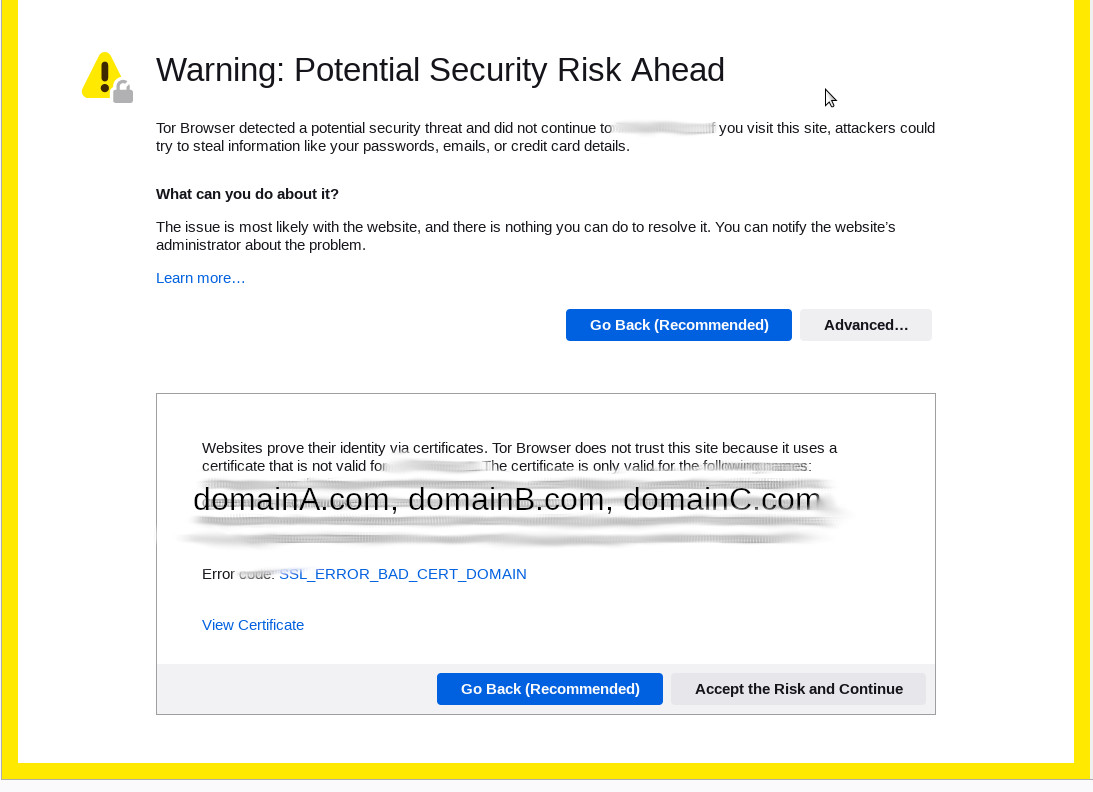
if there are problems… run this one-liner… and ESPECIALLY with let’s encrypt… watch CAREFULLY… as not all errors might show up in a nice red color as errors might NOT be reported for the domainX.com that causes the error… but […]
Efficiency is good in terms of: saving resources. Same results with less (power and other) input. BUT: good people need to be cultivated, by culture. Culture does not simply mean “gifts on Christmas” and “Lederhosen”. (that’s what it has become, […]
want to make this world a better place? want to support true alternatives? gcc makerz https://my.fsf.org/donate Debian, the still superb miniamlistic universal (runs-everywhere and anywhere) GNU Linux Distribution that is heavily how to documented in this knowledge base 😀 (never […]
correct if wrong but… checkout this picture, just uploaded to this self-hosted wordpress instance recently: it “suddenly” and without consent it also exists on this server i2.wp.com, the “cool” wordpress CDN, that is supposed to speed up loading time of […]
let’s face it: the internet has become a gigantic surveillance machine, with hundreds of private companies, trying to collect as much data on the user as possible in order to “predict the market” while also using with AI to analyze […]
0) for security: keep all internet connected devices as up to date as possible! “Freifunk updates its router firmware and closes a critical security vulnerability that could allow attackers to install their own firmware on the devices” (src: heise.de) Also […]
the risks of all digital (no cash) payment systems & amok AI: “This happens quite often with customers of the Cashgroup banks (@DeutscheBank / @Postbank / @Commerzbank / @Comdirect) as soon as their algorithms hit your account is directly without […]
everyone hates em…. cookie banners it’s “funny” (no actually not and forbes.com is not a site this user is visiting very often, it was this article that the user was interested in: https://www.forbes.com/sites/elizabethhowell1/2022/01/04/spacex-starship-orbital-launch-delayed-further-into-2022/), https://www.space.com/author/elizabeth-howell is actually writing for space.com, so […]
all those surveillance and “in app trying to sell something” make it way slower than Win 7… which is not good for a company that want’s to be productive (security, reliability, speed, speed, speed) get a bit of free tuning […]
what is great about books vs blogs? (+) paper books don’t need electricity and hightech to function. energy grid and tcp networks (up to now) have worked pretty reliably, but at any given day, a massive solar flare or a […]
criminals abusing tor for malicous behavior should be blocked, right? “50% of the attacks are leveraging the Tor anonymity service to mask their true origins” https://thehackernews.com/2021/12/new-local-attack-vector-expands-attack.html this could destroy the “honest” part of the network that truly exists, because it […]
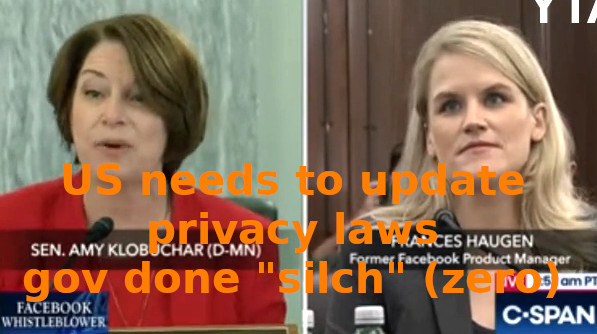
If the user got the time, watch parts of the full uncencored & uncut (thanks C-SPAN!) interview-testimony: https://ytpak.net/watch?v=GOnpVQnv5Cw Facebook/WhatsApp/Instagram and Telegram sideffects may include: ellection manipulation & manipulation of the masses massive intrusion of privacy (collect as much info as […]
the positive vision (always start with something positive) if big data about every keystroke every step we make (the police: every step you make) algorithms determine how mankind will live and thus: technology is “neutral” until it is used for […]