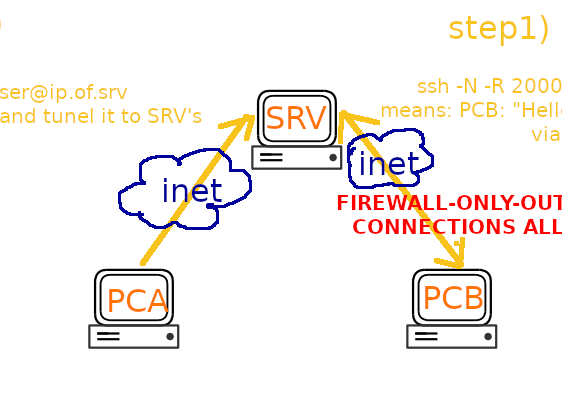
scroll down to: “how to access user-dev-admin’s home network boxes from anywhere via reverse-ssh-tunnel! :D” ssh tunnel remote deviceD’s port access a device’s port that is only available via a specific machine 😀 or in other words: ssh-tunnel port of […]
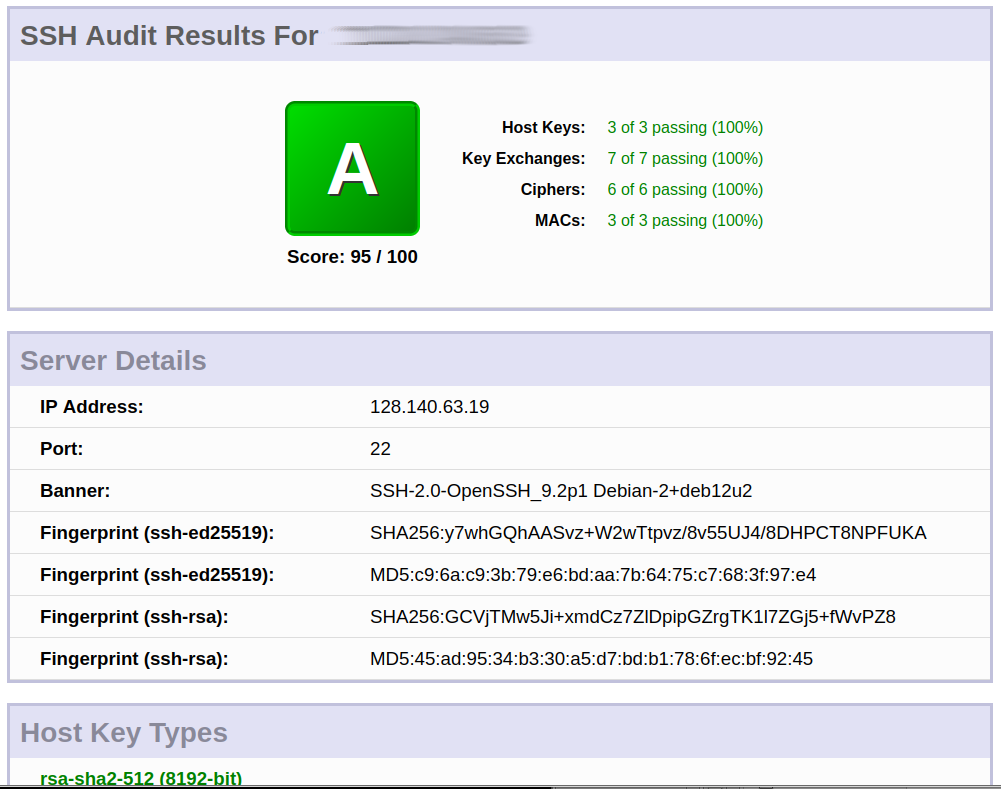
update: 2024-06: ed25519 is currently “the way to go” ssh can be regarded as “critical core infrastructure” time spend on it’s security is time well spend time + money well invested: https://www.openssh.com https://github.com/openssh current manpage: ssh.man.txt WARNING: this howto guide […]
network mac’s are used to uniquely identify systems and users and thus a privacy problem so mac randomization should be enabled per default on every distribution for every wifi network card (maybe interactively during setup ask the user to enable […]
has the system been shutdown properly “gracefully” or has it crashed? it does not have to be a software or hardware problem it could also be: insufficient shielding from terrestrial microwaves satellites lightning strike near by? or extra-terrestrial (the cosmos […]
per default Debian (unfortunately) does not log ssh logins (why? afraid of harddisk overflows?) every user and admin wants to see “who and what is going on” the system usefull also for debugging purposes: what if a ssh client is […]
the user knows, here the user get’s only the tested howtos that truly work and save a massive amount of time, trying out all the non-working howtos X-D what is mongodb (written in C++, JavaScript, Python) In 2013, 10gen changed […]
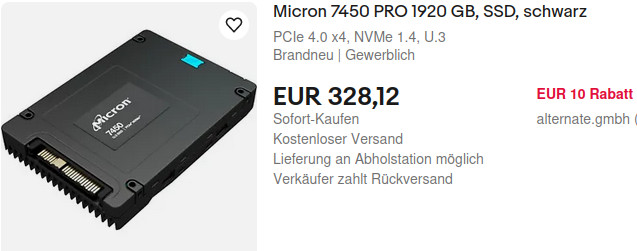
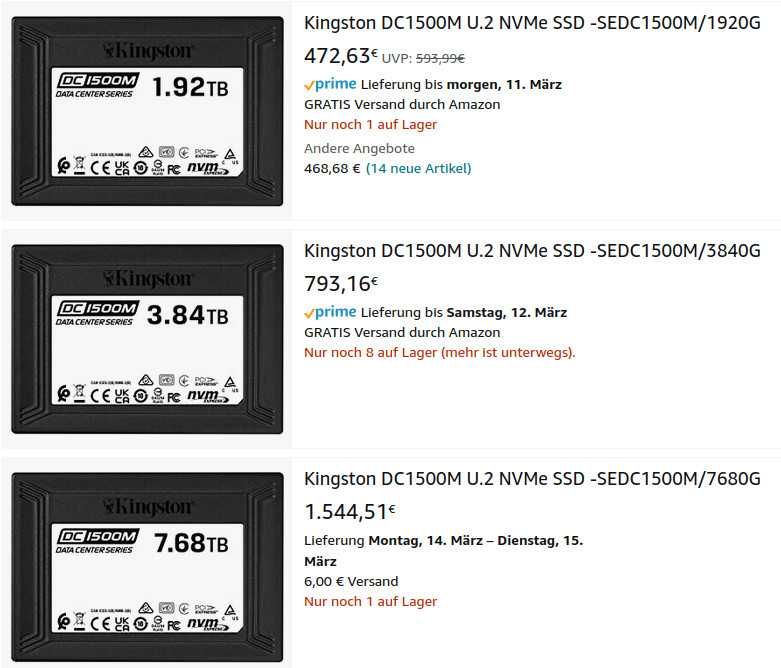
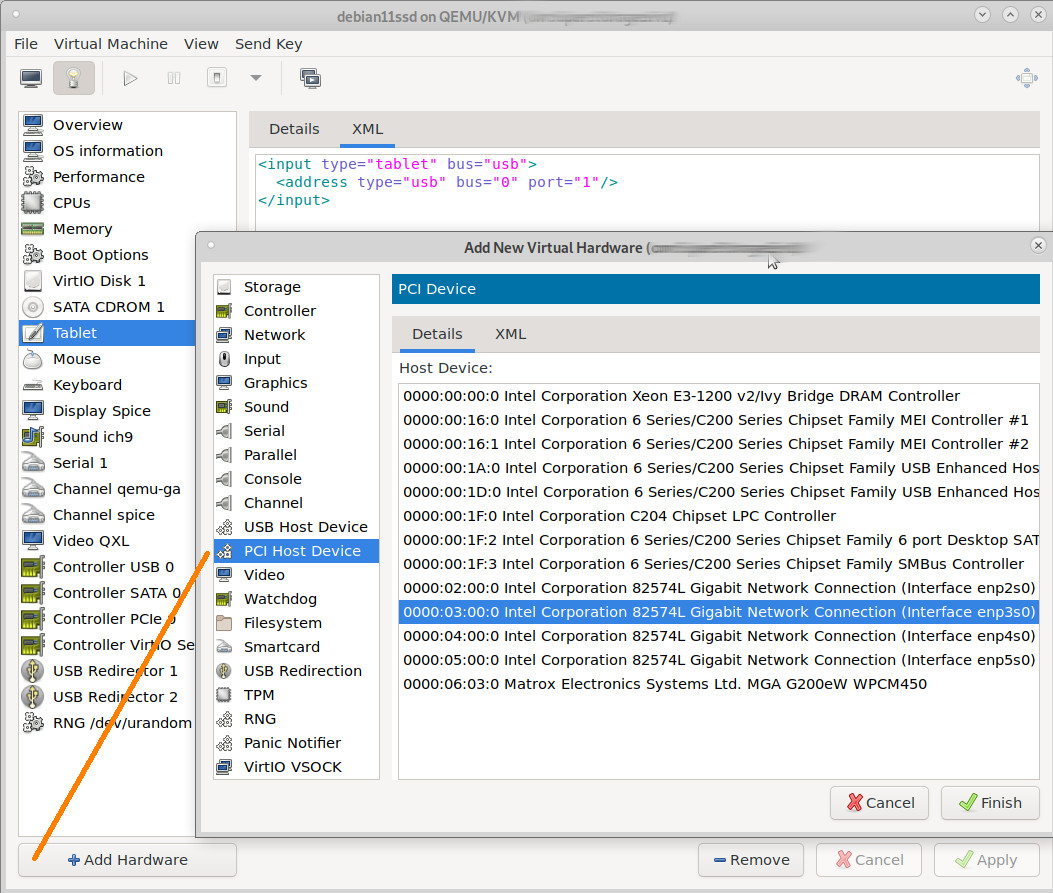
UNTESTED! 😀 these drives are called: “U.2 PCIe NVMe” no kidding, search for em on ebay. “Micron has been developing some of the world’s most advanced memory technologies for more than 40 years, including DRAM (Dynamic Random Access Memory) and […]
have to give a HUGHE praise to the Tor Project! just checked and they DO AN EXCELLENT job at keeping the user private the developers who constantly work to make the system better the thousands of volunteering admins that run […]
if the option firewall -> “delete” is greyed out first the firewall needs to be “dissassociated” with the resource (VPS VM)
methods for detecting network loops -> Realtek Remote Control Protocol – Loop Detect Packet – absolutley nothing wrong with it. (src) also interesting that HP switches are using a Cisco MAC address?
WARNING! MAKE BACKUP of ALL FILES ON THE HARDDISK! that being said, this search replace script works with the tool sed which required to escape all special characters. This tool will help with that: https://dwaves.de/tools/escape/ per default it will search […]
How to create an encrypted USB stick Creating an encrypted USB stick under GNU/Linux is fairly ease. First lets install required packages and erase everything from the stick gives good overview of where is what: (in a tree view style) […]
“to swap, or not to swap, that is the question”: definitely swap more! Shakespeare! “to encrypt, or not to encrypt” (if it contains valuable data: DEFINITELY ENCRYPT!!!) (general tutorial about lvm (logical volume management) “to lvm, or not to lvm” […]
this might sound trivial, but there are multiple approaches: # for (theoretically every) Debian, but not every Debian based system: cat /etc/debian_version 11.3 # for Debian 10 and prior hostnamectl|grep Op Operating System: Debian GNU/Linux 10 (buster) # for Debian […]
lsb_release -a; # tested under Description: Debian GNU/Linux 10 (buster) su – root # create new file touch /scripts/shutdown.sh chmod +x /scripts/shutdown.sh # edit and insert orange content vim /scripts/shutdown.sh #!/bin/bash echo “=== shutdown as gracefully as possible ===” # […]
create a new shared folder on the nas call it “data” enable NFSv4, disable NFSv3 specify list of IPs that are allowed to access the NFSv4 share: don’t forget to hit “Apply” the idea is “anyway” to NAS<-directly-LAN-1000MBit->PC connect the […]
IDE, SCSI, SATA, SAS now U.2 M.2… these drives are called: “U.2 PCIe NVMe” no kidding, search for em on ebay. that reminds of… “the usb cable chaos” has arrived with “Slim SAS” for another round of mass cable connector confusion […]
will be redone soon
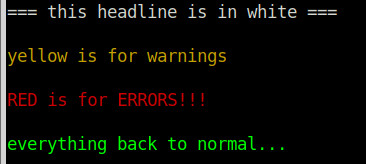
colorful text gives much more oversight. errors are easier to spot when they are marked in red colorful text is acchieved by defining color codes “switching” between color modes and back to default vim /scripts/colors.sh #!/bin/bash RED=’\033[0;31m’ WHITE=’\033[0;37m’ YELLOW=’\033[0;33m’ COLOR_OFF=’\033[0m’ […]
equals to: one neat function of the find command, it that what it found can be passed to another program for further processing. or: it can delete the file by adding the option -delete BUT (!!!) THIS IS DANGEROUS! as […]
privacy is worth swapping wifi cards! Open Source & Free Software are THE GOLD STANDARD which means: would ALWAYS prefer the hazzle of replacing a wifi mini card with an wifi mini card, that is supported by open source drivers, […]
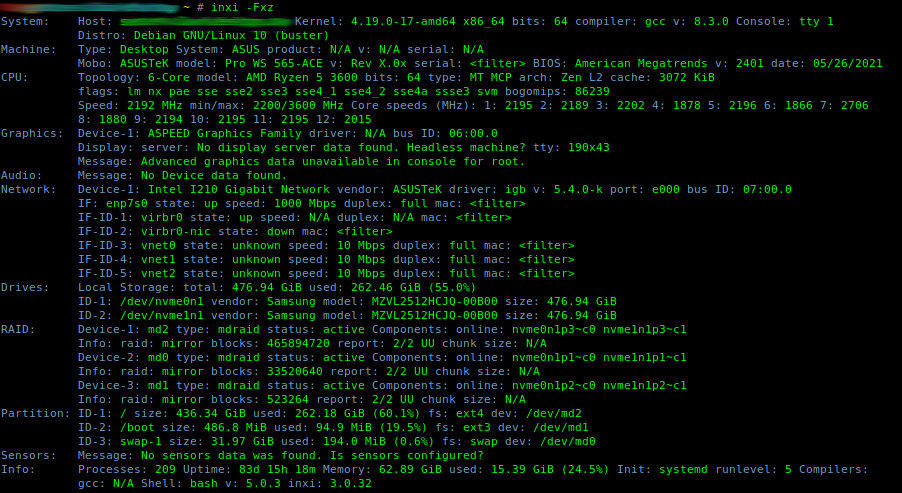
inxi – Command line system information script for console and IRC DESCRIPTION It is also used a debugging tool for forum technical support to quickly ascertain users’ system configurations and hardware. inxi shows system hardware, CPU, drivers, Xorg, Desktop, Kernel, […]
and: is the EU / Germany location simply unattractive for many companies in view of the data protection craze? “In the end, it may be bitter for Quad9 that they only got into the trouble by moving to Europe, where […]
the positive vision (always start with something positive) if big data about every keystroke every step we make (the police: every step you make) algorithms determine how mankind will live and thus: technology is “neutral” until it is used for […]
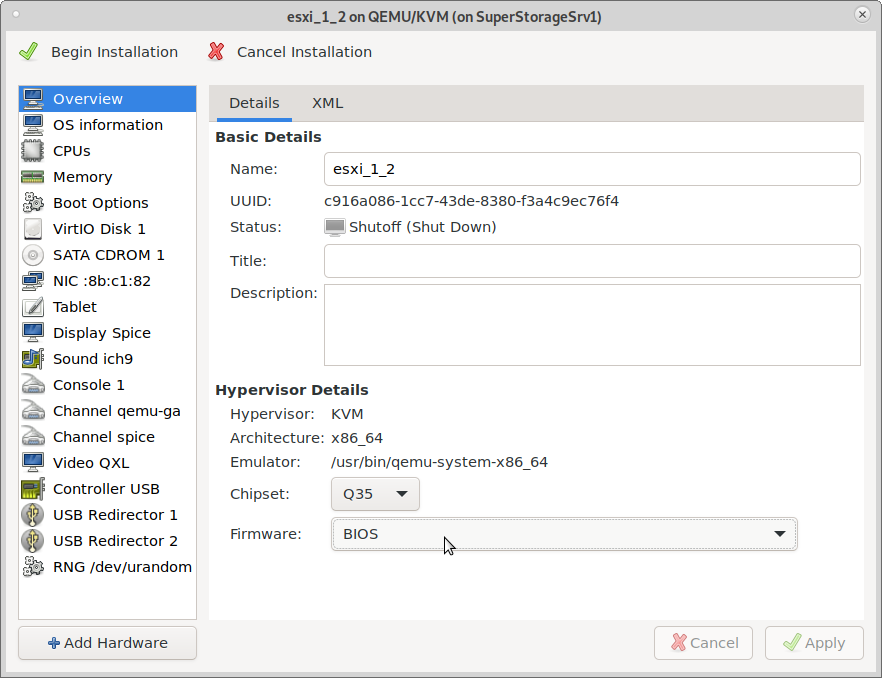
it is actually like this, in virt-manager, that chipset and bios can only be changed during first setup “begin installation” it then is fixed and can not be changed in virt-manager
the most fundamental networking settings are ever changing it used to be /etc/resolv.conf where nameservers are set systemd is doing it’s own thing /etc/systemd/resolved.conf and Ubuntu (based on Debian) is doing (again) it’s entirely own thing (netplan) frankly: this sucks […]
nfs is to GNU-Linux what smb is to Windows: sharing dirs & files “The Network File System (NFS) was developed to allow machines to mount a disk partition on a remote machine as if it were a local disk. It […]
remember that discussion about ever changing non-standard ways of defining network interfaces and ip addresses under /etc/network… well guess what, canonical just came up with a completely new config file format X-D (guess, everything is a yaml.yml now) hostnamectl; # […]