https://www.youtube.com/watch?v=UheOilps2zQ
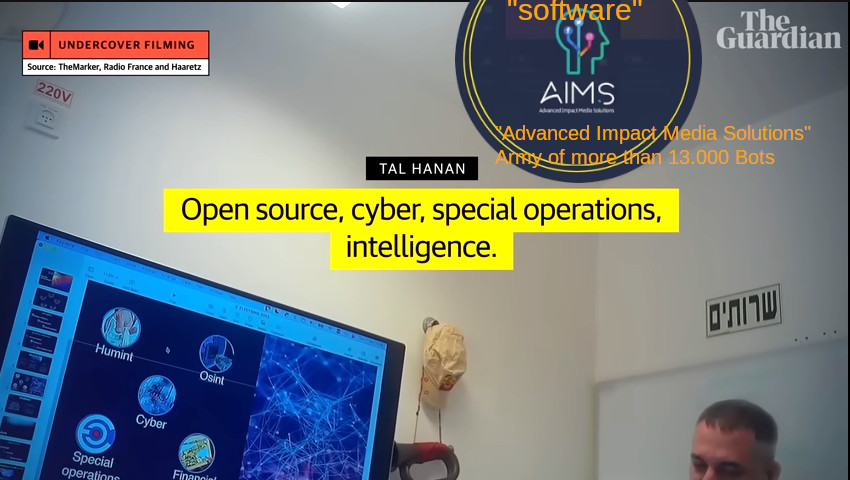
“know in some countries they believe Telegram is safe. I will show you how safe it is,” he said, before showing a screen in which he appeared to scroll through the Telegram contacts of one Kenyan strategist
SS7 highly insecure crap from 1975
why is this still in operation?
“In 2008, several SS7 vulnerabilities were published that permitted the tracking of mobile phone users.[16]
In 2014, the media reported a protocol vulnerability of SS7 by which anyone can track the movements of mobile phone users from virtually anywhere in the world with a success rate of approximately 70%.[17] In addition, eavesdropping is possible by using the protocol to forward calls and also facilitate decryption by requesting that each caller’s carrier release a temporary encryption key to unlock the communication after it has been recorded.[18] The software tool SnoopSnitch can warn when certain SS7 attacks occur against a phone,[19] and detect IMSI-catchers that allow call interception and other activities.[20][21]
In February 2016, 30% of the network of the largest mobile operator in Norway, Telenor, became unstable due to “unusual SS7 signaling from another European operator”.[22][23]
The security vulnerabilities of SS7 have been highlighted in U.S. governmental bodies, for example when in April 2016 Congressman Ted Lieu called for an oversight committee investigation.[24]
In May 2017, O2 Telefónica, a German mobile service provider, confirmed that the SS7 vulnerabilities had been exploited to bypass two-factor authentication to achieve unauthorized withdrawals from bank accounts. The perpetrators installed malware on compromised computers, allowing them to collect online banking account credentials and telephone numbers. They set up redirects for the victims’ telephone numbers to telephone lines controlled by them. Confirmation calls and SMS text messages of two-factor authentication procedures were routed to telephone numbers controlled by the attackers. This enabled them to log into victims’ online bank accounts and effect money transfers.[25]
In March 2018, a method was published for the detection of the vulnerabilities, through the use of open-source monitoring software such as Wireshark and Snort.[26][27][28] The nature of SS7 normally being used between consenting network operators on dedicated links means that any bad actor’s traffic can be traced to its source.
An investigation by The Guardian and the Bureau of Investigative Journalism revealed that the SS7 protocol was exploited in an attempt to locate Sheikha Latifa bint Mohammed Al Maktoum (II) on 3 March 2018, a day before her abduction.[29]”
(Wiki)
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!