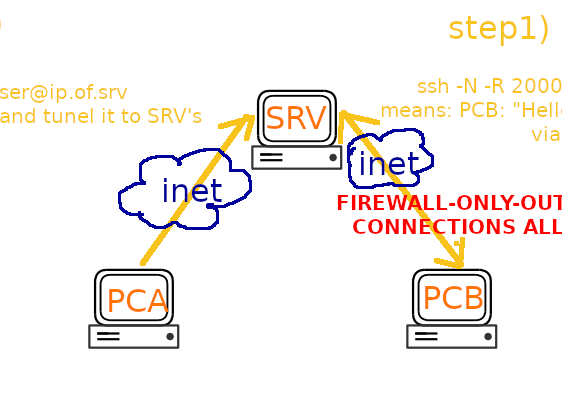
scroll down to: “how to access user-dev-admin’s home network boxes from anywhere via reverse-ssh-tunnel! :D” ssh tunnel remote deviceD’s port access a device’s port that is only available via a specific machine 😀 or in other words: ssh-tunnel port of […]
network mac’s are used to uniquely identify systems and users and thus a privacy problem so mac randomization should be enabled per default on every distribution for every wifi network card (maybe interactively during setup ask the user to enable […]
per default Debian (unfortunately) does not log ssh logins (why? afraid of harddisk overflows?) every user and admin wants to see “who and what is going on” the system usefull also for debugging purposes: what if a ssh client is […]
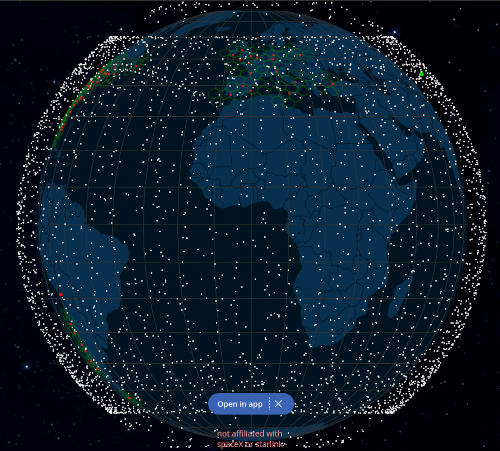
Starlink is a cost effective internet-via-satellite provider run by SpaceX at 2024-01 currently (2014-01) counts over x > 2 mio customers SpaceX plans to put 12.000 to 42.000 satellites into Low Earth Orbit (LEO). currently (2024-01) 5289 satellites (Wiki) in […]
so every android user is in a hurry to update update update to Google’s latest firmware because of it’s security issues really would like to see a smart phone that can run almost unchanged GNU Linux kernel 😀 (yes would […]
in the past, this was no issue. no matter what. neither: ifup enp0s25 # nor ifconfig enp0s25 up # nor ip link set enp0s25 up # worked two notebook NICs were connected with a known-to-be-good LAN cable but both interfaces […]
“wlx123 Interface doesn’t support scanning : Device or resource busy” this error occurs during manual terminal bash based scanning of wifi wlan networks: hostnamectl; # tested on Operating System: Debian GNU/Linux 12 (bookworm) Kernel: Linux 6.1.0-13-686-pae Architecture: x86 su – […]
it truly works OUT OF THE box 😀 (without complicated manual compilation of drivers) this screenshot says “disabled” because wifi adapters were “soft blocked” # tested on lsb_release -d Description: Debian GNU/Linux 12 (bookworm) (x86 and ARMv7 (ODROID XU4)) su […]
methods for detecting network loops -> Realtek Remote Control Protocol – Loop Detect Packet – absolutley nothing wrong with it. (src) also interesting that HP switches are using a Cisco MAC address?
EDIMAX EW-7612UAn V2 THE ONLY (?) GNU Linux WIFI WLAN Adapter that works OUT OF THE BOX on all GNU Linux systems (ODROID RASPBERRY AND Desktop GNU Linux) it’s a solid high quality USB WIFI dongle stick known as Edimax […]
software minimalism is key for stability, maintainability, security and performance so regularly check, what services are running and if they can be disabled/uninstalled 🙂 systemd: systemctl.man.txt # list all units (list can be /searched like less) systemctl # list all […]
currently wrestling with a LTE modem, that used to work under Ubuntu, but refuses to work under Debian 11. while true; do echo “=== show modem status:”; mmcli -m 1|grep -e model -e primary -e state -e signal; echo -e […]
this is a quick bash hack, to set overwrite the current ip with an fixed ip or add an virtual interface for an additional fixed ip this will (brute force) OVERWRITE all mess done by network managers of various origins […]
0) for security: keep all internet connected devices as up to date as possible! “Freifunk updates its router firmware and closes a critical security vulnerability that could allow attackers to install their own firmware on the devices” (src: heise.de) Also […]
and: is the EU / Germany location simply unattractive for many companies in view of the data protection craze? “In the end, it may be bitter for Quad9 that they only got into the trouble by moving to Europe, where […]
the specs CPU Allwinner A20,32 Bit Cortex™-A7 2-Core 1G GPU ARM® Mali400MP2 -> get the GPU going SDRAM 1GB DDR3 (shared with GPU) 432Mhz Storage “SD Card up to 64GB (SDXC) 1 SATA up to 2TB “ Network 4x Gigabit […]
the most fundamental networking settings are ever changing it used to be /etc/resolv.conf where nameservers are set systemd is doing it’s own thing /etc/systemd/resolved.conf and Ubuntu (based on Debian) is doing (again) it’s entirely own thing (netplan) frankly: this sucks […]
nfs is to GNU-Linux what smb is to Windows: sharing dirs & files “The Network File System (NFS) was developed to allow machines to mount a disk partition on a remote machine as if it were a local disk. It […]
remember that discussion about ever changing non-standard ways of defining network interfaces and ip addresses under /etc/network… well guess what, canonical just came up with a completely new config file format X-D (guess, everything is a yaml.yml now) hostnamectl; # […]
update: join me @ online-coworking-space.com https://play.workadventu.re/@/online/coworking/space.com first of: the online conferecing as RPG game format is really fun and innovative idea to make online events more fun! 🙂 (it is accompanied by live streams via vimeo or youtube) Corona will […]
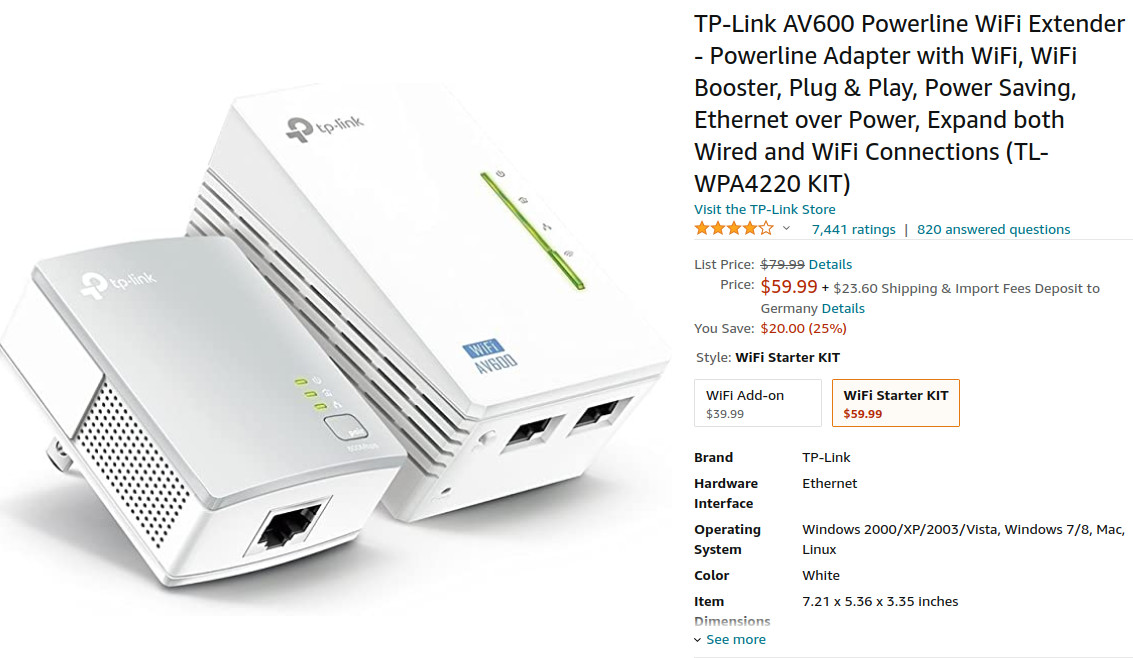
can not recommend! the connection works (benchmark results below) the major problem is: unable to disable DHCP! which means: whenever there is a disconnect from the uplink (DHCP lost) the DHCP of the TL-WPA4220KIT will “kick in” and assign completely […]
update: Starlink reduced price to 80EUR! 😀 PLUS: THE HARDWARE IS FOR FREE! (the very good hardware alone is worth ~2000USD!) Thanks Elon! 😀 Support SpaceX: mankind’s only hope to ever reach Mars! order Starlink now! Update: Amazon […]
always say something positive first: FritzBoxes are great (DSL/LTE/…) internet routers (up to now) all FritzBoxes work with 12V DC (which is great for usage with small solar power stations (that are usually 12V based)) high quality & reliable secure […]
EDIMAX EW-7612UAn V2 THE ONLY (?) GNU Linux WIFI WLAN Adapter that works OUT OF THE BOX on all GNU Linux systems (ODROID RASPBERRY AND Desktop GNU Linux) https://www.mediatek.com/products/broadbandWifi/mt7662u hostnamectl; # tested on Static hostname: lenovo t440 Operating System: Debian […]
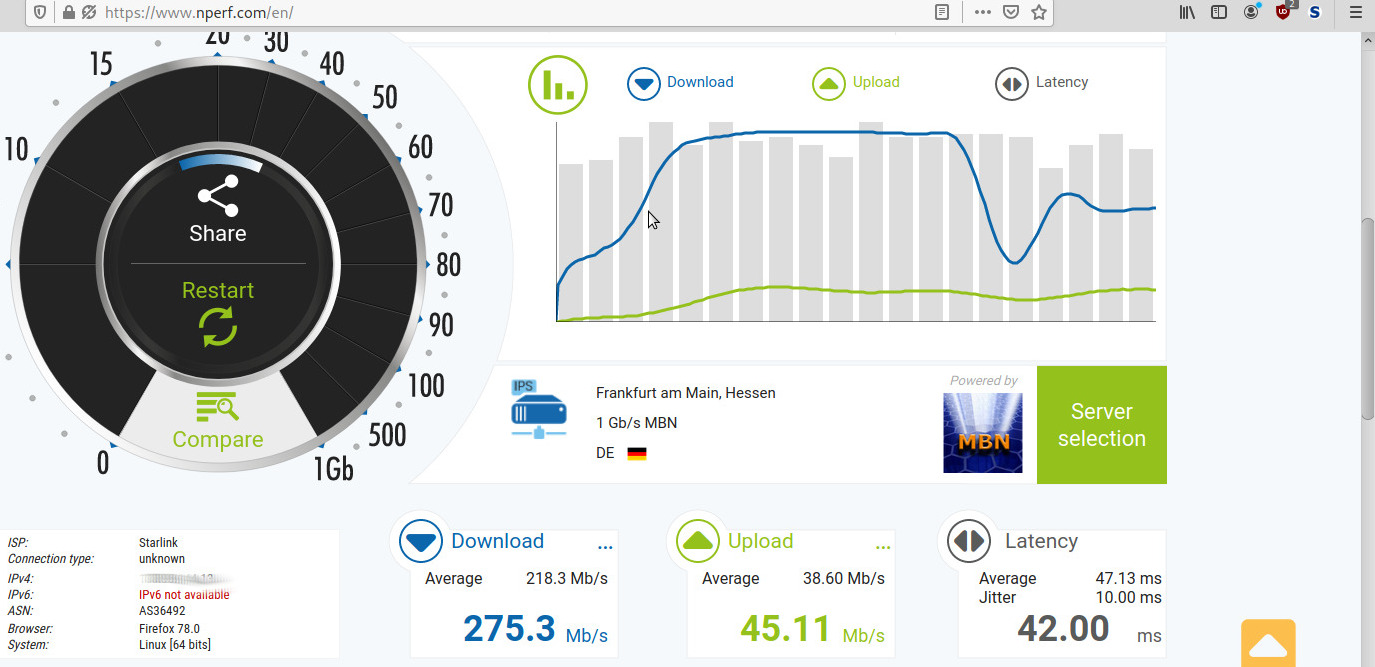
this script is for cront-job regular measurement of the available (download) bandwidth, by downloading a 100MByte dd crated (https://dwaves.de/testfile) testfile created like this (creditz): head -c 100m /dev/zero | openssl enc -aes-128-cbc -pass pass:”$(head -c 20 /dev/urandom | base64)” > […]
DNS servers are the “yellow pages” “phone book” of the internet. whoever is running DNS servers get’s to know all queries send (what client is requesting and probably connecting to what address… basically: what websites the user have visited, this […]
Overview Recent 360Netlab unknown threat detection system to capture to a group of unknown malicious families of the sample, which a number of samples supported CPU architectures are x86(32/64), ARM(32/64), MIPS(MIPS32/MIPS-III) as well as PPC, after our analysis, which is […]
“Better Than Nothing” Starlink-Beta started across the US & Canada Starlink: amazing but and also a bit “crazy” “On 15 October 2019, the United States Federal Communications Commission submitted filings to the International Telecommunication Union on SpaceX’s behalf to […]




![GNU Linux – hardware review – Wifi WLAN USB Stick Edimax N300 (EW-7612UAn V2 802.11n Wireless Adapter [Realtek RTL8192CU]) (also works with ODROID XU4 (Armbian))](https://dwaves.de/wp-content/uploads/2022/10/Wifi-WLAN-USB-Stick-Edimax-N300-EW-7612UAn-V2-802.11n-Wireless-Adapter-Realtek-RTL8192CU-scaled.jpg)