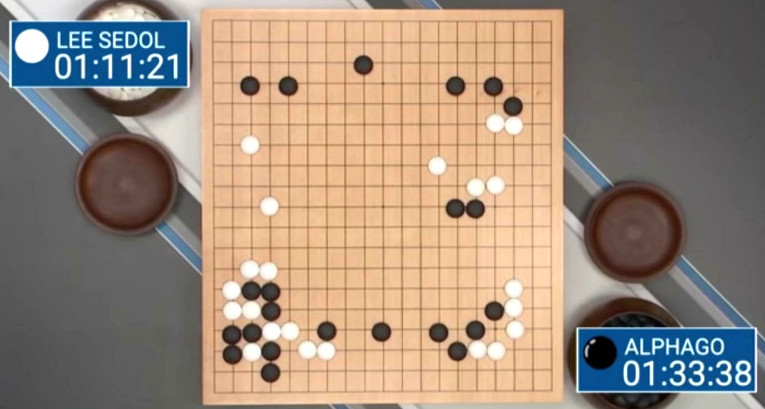
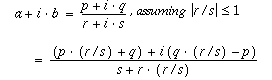Musk grabbed deeply into the Toilet, by wasting Billions on it’s twitter buy, he could have build 100x Twitters from scratch, with this amount of money. Understanding Elon Musk – (the day Elon almost destroyed Tesla by accident) – good […]
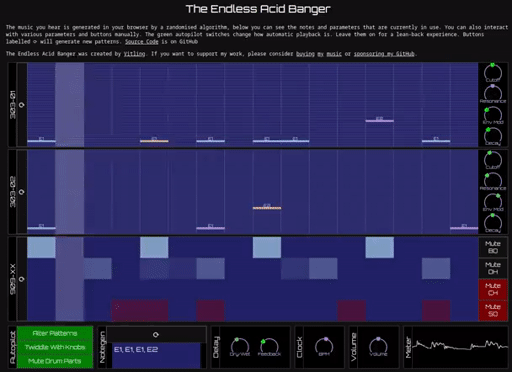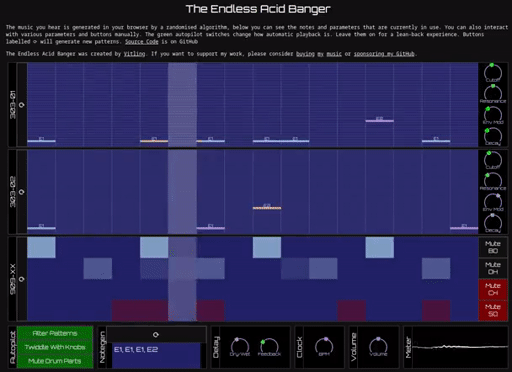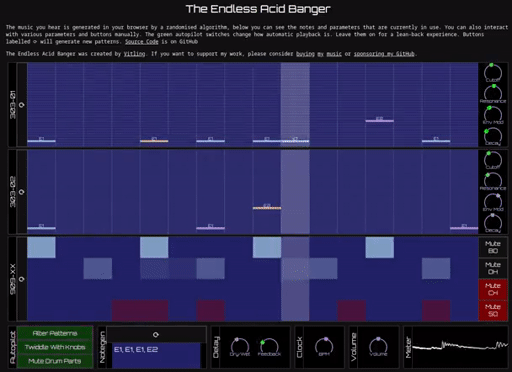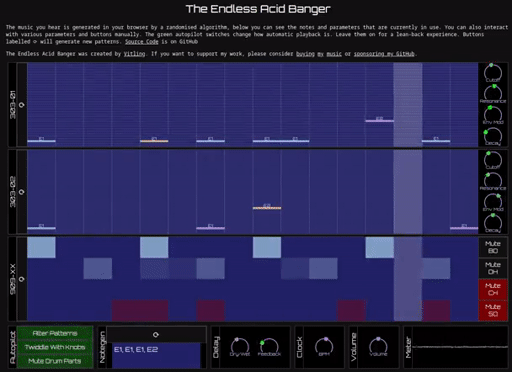
was ALWAYS wondering… why are there not “band sessions” “mixing” all done in the browser? (it was done with Flash) was javascript & HTML(5) lacking the multi medial capabilities? (it surely was not designed for this but CHECK THIS OUT: […]
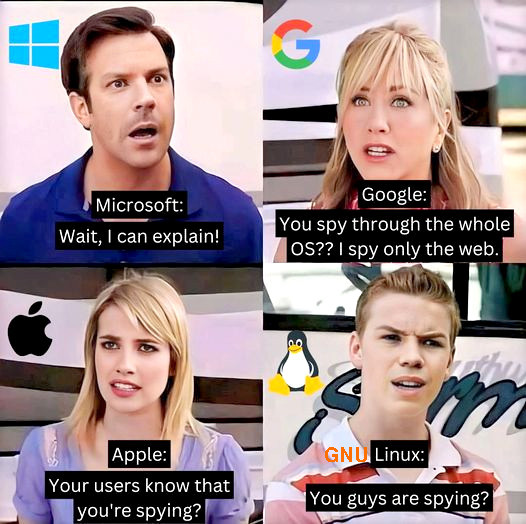
Let me be frank. Once upon the time, was a Windows user. Then was happy to have to use OSX for a transition to GNU Linux. But once on GNU Linux (Debian) do not miss neither Windows nor OSX at […]
“Founded in 2016, the annual fair in Paris is one of Europe’s top-tier technology events, this year attracting 2,400 start-ups – double the number it hosted in its first year – and more than 2,000 investors looking to fund the […]
Paying taxes is no fun Paying taxes double and tripple is even less fun. Because let’s face it: when buying a pair of NEW shoes in Germany the average German Joe already pays at least 19% MwSt. plus the income […]
why it’s really time to occupy Mars & how the internet has changed post-babyboomer attitude to sharing Had an interesting conversation with a 65 year old, babyboomer, who has never personally seen war and who has not grown up with […]
Open Source is about enabling users “Amazon, Microsoft, Google” and the White House, want to help make Open Source more secure… https://www.golem.de/news/openssf-150-millionen-us-dollar-sollen-open-source-absichern-2205-165382.html https://www.golem.de/news/openssf-linux-foundation-will-security-praxis-vereinheitlichen-2008-150036.html src of src: “White House OSS Mobilization Plan” 2022: https://openssf.org/blog/2022/05/11/testimony-to-the-us-house-committee-on-science-and-technology/ 2020: “The OpenSSF is a cross-industry collaboration […]
will be redone soon
yes, thank you is not enough, public healthcare is massively underfunded, there needs to be a massive pay rise, there is no time to wait for the rise of the AI nursing robots (aka Tesla Bots). “Hospital closures continue in […]
what is great about books vs blogs? (+) paper books don’t need electricity and hightech to function. energy grid and tcp networks (up to now) have worked pretty reliably, but at any given day, a massive solar flare or a […]
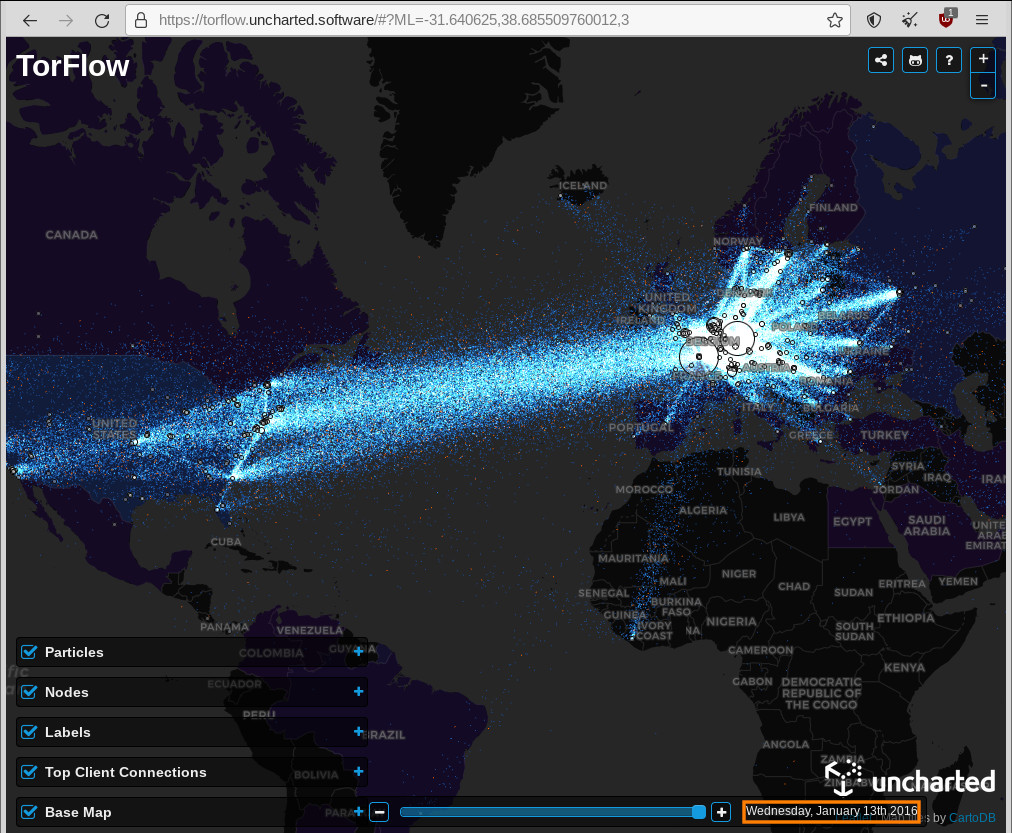
criminals abusing tor for malicous behavior should be blocked, right? “50% of the attacks are leveraging the Tor anonymity service to mask their true origins” https://thehackernews.com/2021/12/new-local-attack-vector-expands-attack.html this could destroy the “honest” part of the network that truly exists, because it […]
Apple wants to become the new Google: BigBadBoldBigDataMothership why more developers should chose GPL to publish programs: as a once proud Apple user… (yes GNU Linux Debian 10 actually runs pretty well on the Intel-Macbook-Pros) yes they are beautiful spies… […]
why are those data leaks problematic? because scammers and spammers will use this data to even better scam (social engineer) the affected users that is why it is essential to give those platforms (if the user needs them) as little […]
not sure if the news rang through… the Amazon Cloud (AWS) guy will be the new CEO of Amazon. What cloud? Amazon “cloud” Hetzner “cloud” cloud (centralized digital infrastructure) can be designed / implemented in different ways. from: the user/admin […]
proof wrong but, sorry to say but… would it not be possible that messing with bacteria DNA that by accident scientists creates new pathogens? new deadly diseases? so it’s one thing to write a program that dos “hello world” and […]
“floating point arithmetic is considered an esoteric subject by many people” (src: What Every Computer Scientist Should Know About Floating Point Arithmetic – David Goldberg 1991.pdf) some even do “transcendental calculations” (src) make no mistake: computer make mistakes too! not […]
DNS servers are the “yellow pages” “phone book” of the internet. whoever is running DNS servers get’s to know all queries send (what client is requesting and probably connecting to what address… basically: what websites the user have visited, this […]
SecurityLab, [14.07.20 15:35] The Electronic Frontier Foundation (EFF) has unveiled a new database demonstrating how and where us law enforcement agencies use tracking technologies. A map of the use of tracking technologies in the United States is presented (https://www.securitylab.ru/news/510018.php) SecurityLab, […]
All SmartPhones are spies! that’s why Merkel keeps the Nokia from 1995 (even if that device is spied on as well, because it can not end2end encrypt sms or phone calls (*FAIL*! X-D)) Putin does not have a mobile phone […]
The Age of Surveillance Capitalism: “be careful what you reveal to your friend” (the internet) https://irlpodcast.org/season4/episode5/ “where it has gone from defending America to controlling it” data google tries to collect from users: (it is probably only the tip of […]
The Great A.I. Awakening: A Conversation with Eric Schmidt Feb 23, 2017 as user might have noticed, the battle Amazon vs Microsoft who will get the $10Billion DoD cloud computing contract is still hot. And maybe the contract is split. […]
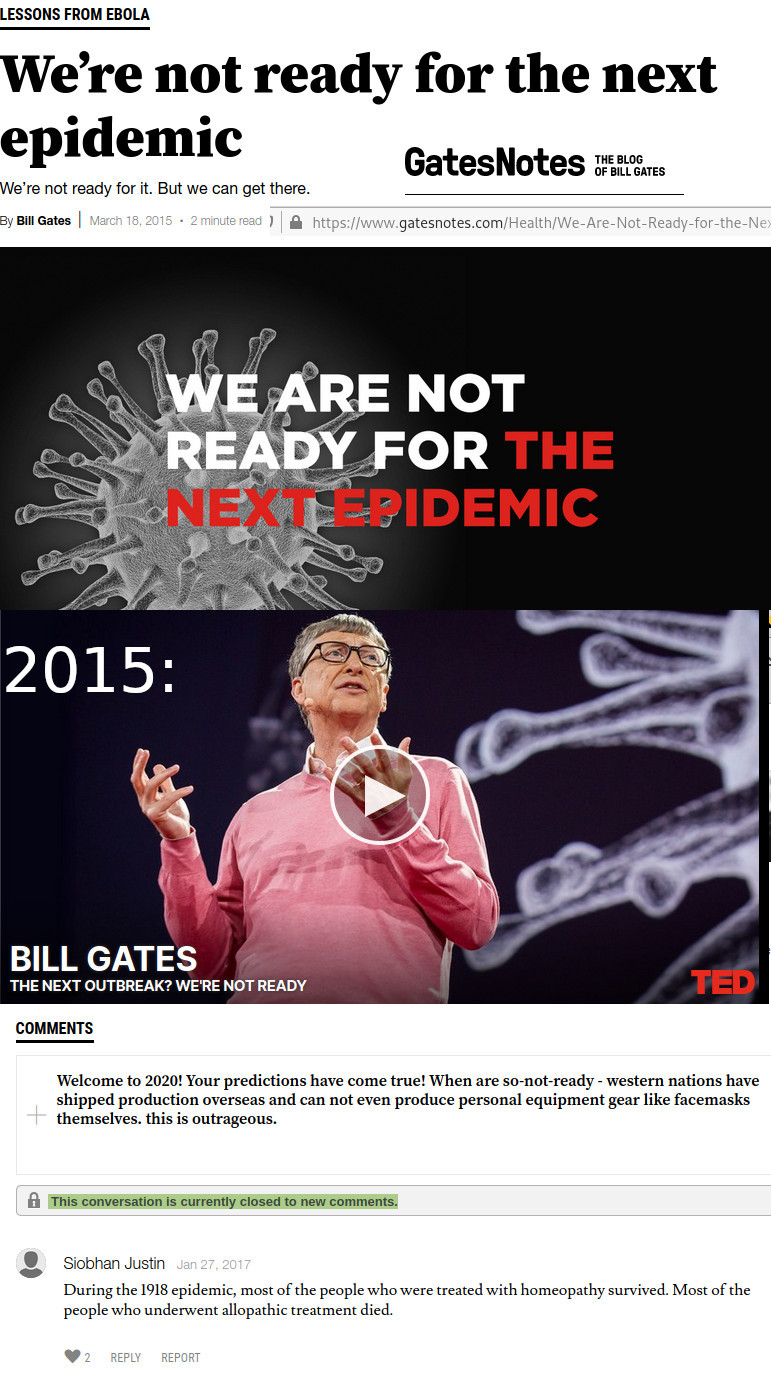
sorry this post will have to do nothing with linux X-D (unless one is pretty sure all those corona overview and prediction dashboards run on gnu linux servers) … what Mr Gates probably underestimated, that because of globalization and maximizing […]
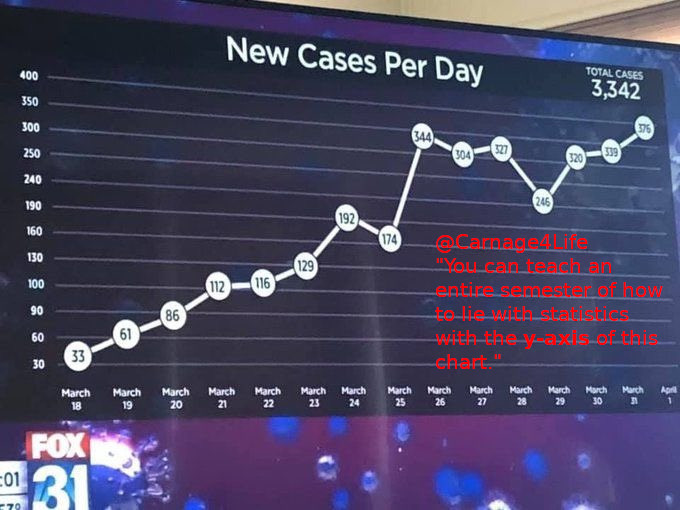
this is why high quality journalism and education are sooooo important: trust is so important & journalism should be about truth and trust context: media outlets that use numbers out of context (do those numbers apply to the US, or […]
As with all hot debated topics: Linus Torvald’s “show me the source” in this case, the source of one’s informations (always give the source!) is IMPORTANT for the information’s credibility. It is absolutely vital in science to give all sources […]
i really like virtualbox and i think it has great potential, what i do not like SOOO much is the CIA’s involvement with Oracle. “Larry Ellison Is A Billionaire Today Thanks To The CIA” (src) VirtualBox is mostly GPL 2.0 […]
don’t be evil “Google controls about 62% of mobile browsers, 69% of desktop browsers, and the operating systems on 71% of mobile devices in the world. 92% of internet searches go through Google and 73% of American adults use YouTube. […]
servers/clients/computers/programs/services/webservers need accurate time… they usually get it from time servers that have an atomic clock attached to their USB port. (just guessing) ping time.google.com PING time.google.com (216.239.35.4) 56(84) bytes of data. 64 bytes from time2.google.com (216.239.35.4): icmp_seq=1 ttl=46 time=43.5 […]
Pwn2Own 2020: opening a pdf can be enough to compromise system! https://youtu.be/u1udr7j9MQA?t=359 thank you ccc you are doing a lovely work – make this planet more interesting by creativity and more informed about security 🙂 keep it up 🙂 https://cdn.media.ccc.de/events/gpn/gpn19/h264-hd/gpn19-45-eng-BADPDF_-_Stealing_Windows_Credentials_via_PDF_Files_hd.mp4 […]
google’s security lab “project zero“ has made itself a name. (you can subscribe to their rss feed with thunderbird.) Posted by Ben Hawkes, Project Zero (team lead) (2019-05-15) Project Zero’s team mission is to “make zero-day hard”, i.e. to make […]
as far as i understood the “string theory” and also Einstein’s Theory is that on the smallest building blocks Matter = is actually = Energy, in “string theory” this energy is resembled as a vibrating string, if it vibrates in […]