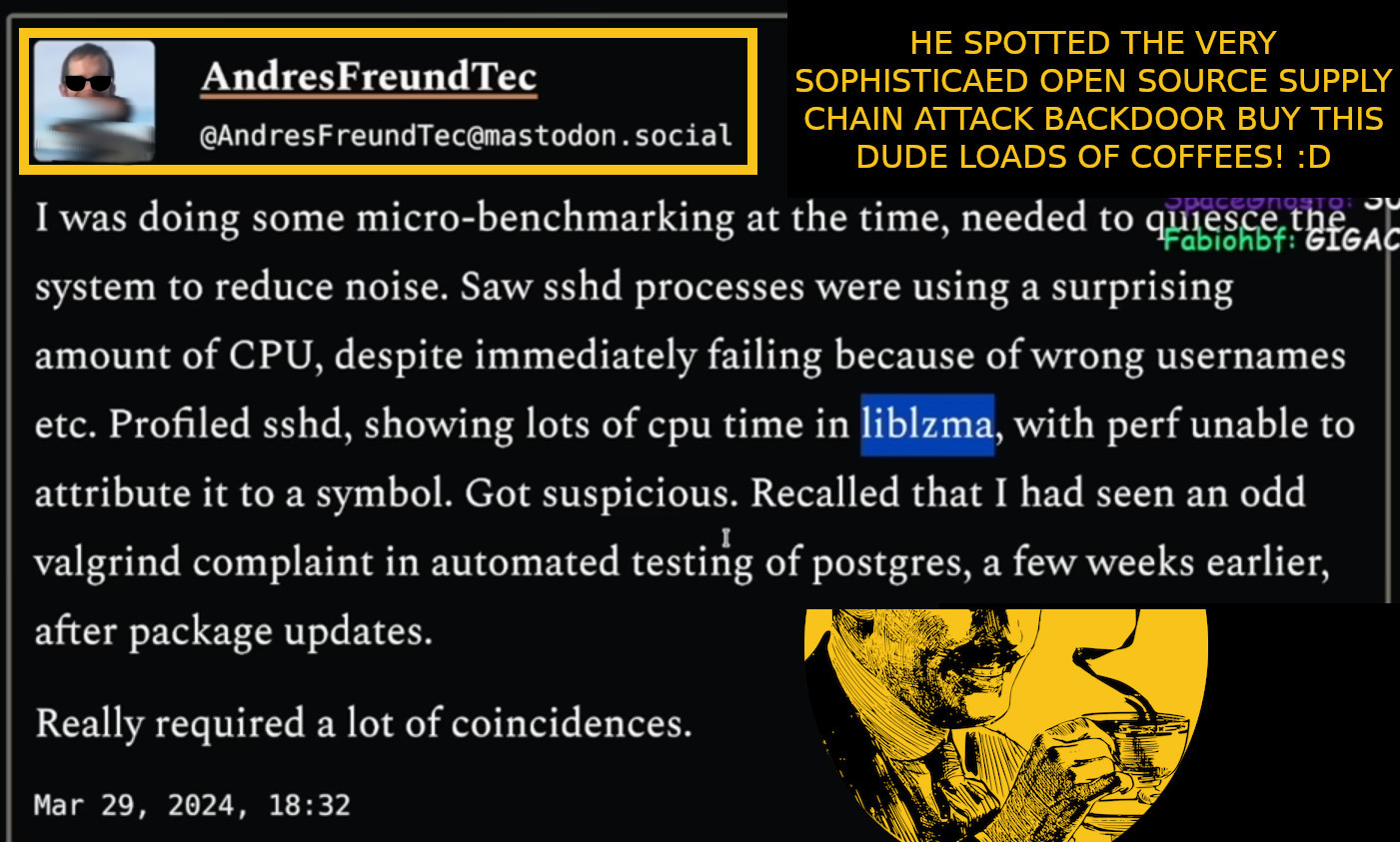
it might be the biggest “cyber” story of the year 2024 already: buy this guy MANY MANY COFFEES! he spotted the problem via know how but also luck 😀 it was a VERY VERY LONG and WILD COMPLEX and HIGHLY […]
No matter if docker repository called “hub”, Google’s App Store “PlayStore” or Apple’s App Store they are ALL facing the same security problems: https://www.bleepingcomputer.com/news/security/google-explains-how-android-malware-slips-onto-google-play-store/ plus: https://www.bleepingcomputer.com/news/security/thousands-of-android-apks-use-compression-trick-to-thwart-analysis/ what if… a malicious actor uploads an App or docker container that is totaly […]
https://www.youtube.com/watch?v=UheOilps2zQ “know in some countries they believe Telegram is safe. I will show you how safe it is,” he said, before showing a screen in which he appeared to scroll through the Telegram contacts of one Kenyan strategist https://www.theguardian.com/world/2023/feb/15/revealed-disinformation-team-jorge-claim-meddling-elections-tal-hanan SS7 […]
(knowing that manually auto-translating Russian CyberSec news to English, is not a feasable concept and need to be automated, but as this blog is non-profit, it is for curiosity.) Booking.com found an authentication vulnerability that allows account hijacking A vulnerability […]
“know in some countries they believe Telegram is safe. I will show you how safe it is,” he said, before showing a screen in which he appeared to scroll through the Telegram contacts of one Kenyan strategist https://www.theguardian.com/world/2023/feb/15/revealed-disinformation-team-jorge-claim-meddling-elections-tal-hanan
“The biggest network security threat today is a remote code execution exploit for Intel’s Management Engine.” “Every computer with an Intel chipset produced in the last decade would be vulnerable to this exploit, and RCE would give an attacker full […]
Open Source is about enabling users “Amazon, Microsoft, Google” and the White House, want to help make Open Source more secure… https://www.golem.de/news/openssf-150-millionen-us-dollar-sollen-open-source-absichern-2205-165382.html https://www.golem.de/news/openssf-linux-foundation-will-security-praxis-vereinheitlichen-2008-150036.html src of src: “White House OSS Mobilization Plan” 2022: https://openssf.org/blog/2022/05/11/testimony-to-the-us-house-committee-on-science-and-technology/ 2020: “The OpenSSF is a cross-industry collaboration […]
https://cve.circl.lu/cve/CVE-2019-19781 https://www.healthcare-computing.de/bsi-warnt-vor-schwachstelle-bei-vpn-produkten-von-citrix-a-964940/ https://www.cnblogs.com/lsgxeva/p/12116150.html hits healthcare hospital in Germany, causing death of (at least) 1 person https://www.businessinsider.de/politik/deutschland/hacker-legen-uniklinik-duesseldorf-lahm-staatsanwaltschaft-ermittelt-wegen-todesfall-einer-patientin/
“The Duri malware, for example, uses the Javascript blob technique. The attacks are triggered by visiting a website with the malicious code.” (this could be a well known, sincere, but hacked website) “By downloading, the malware can install itself on […]
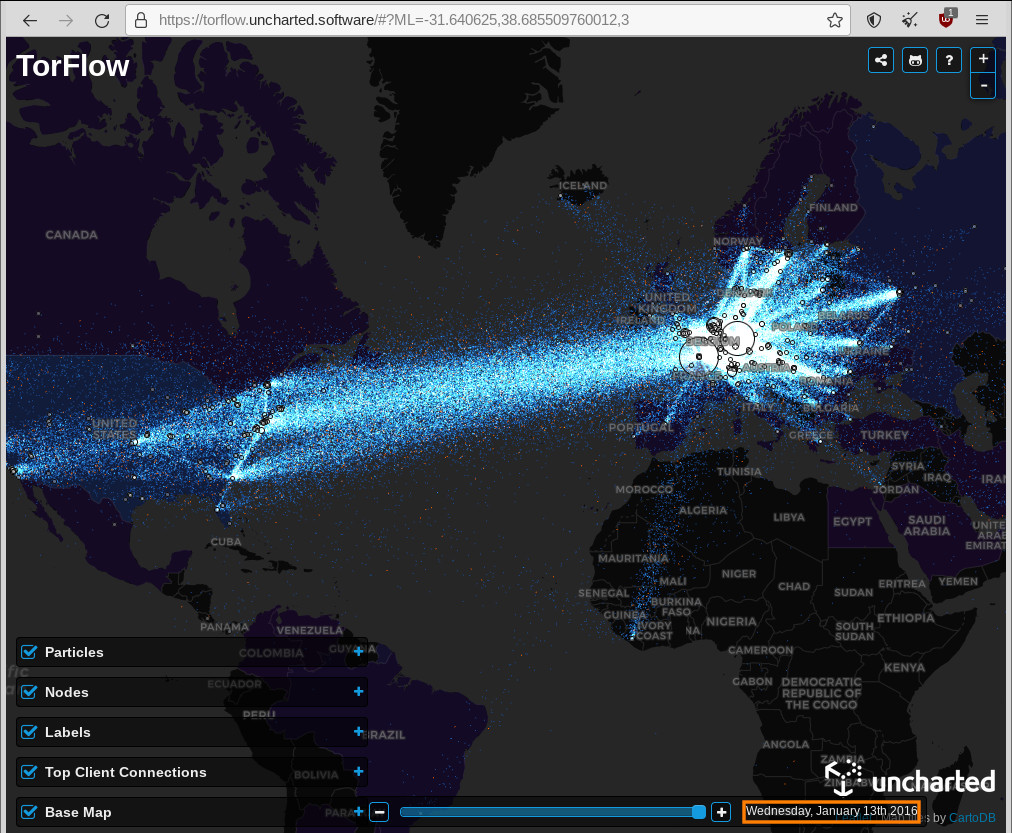
criminals abusing tor for malicous behavior should be blocked, right? “50% of the attacks are leveraging the Tor anonymity service to mask their true origins” https://thehackernews.com/2021/12/new-local-attack-vector-expands-attack.html this could destroy the “honest” part of the network that truly exists, because it […]
the positive vision (always start with something positive) if big data about every keystroke every step we make (the police: every step you make) algorithms determine how mankind will live and thus: technology is “neutral” until it is used for […]
warning: no guarantee of completeness! contains ads! (but owner of blog get’s nothing, maybe source of source does) Are the odds against the (itsec) defenders? It certainly feels that way, because no human can ever find all bugs, so Fuzzing […]
the wiki: https://en.wikipedia.org/wiki/OWASP the top 10: https://owasp.org/www-project-top-ten/2017/Top_10.html the ebook: https://github.com/OWASP/owasp-mstg/releases/download/v1.2/OWASP_MSTG-1.2.pdf the text: https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/02-Configuration_and_Deployment_Management_Testing/01-Test_Network_Infrastructure_Configuration the conferences: https://owasp.org/www-board/ https://www.blackhat.com/us-21/ the costs: https://training.owasp.org/ 2-part Training: $505 Member 2-part Training: $455 * For member discount code contact events ÄT owasp DOOOT com https://www.udemy.com/course/intro-to-bug-bounty-by-nahamsec/ it’s […]
in short: humans per default, without an education might just be “better” apes. Some parts of mankind behave very primitive and clearly show no signs of higher intelligence or education. The troubles start, when the tools become more and more […]
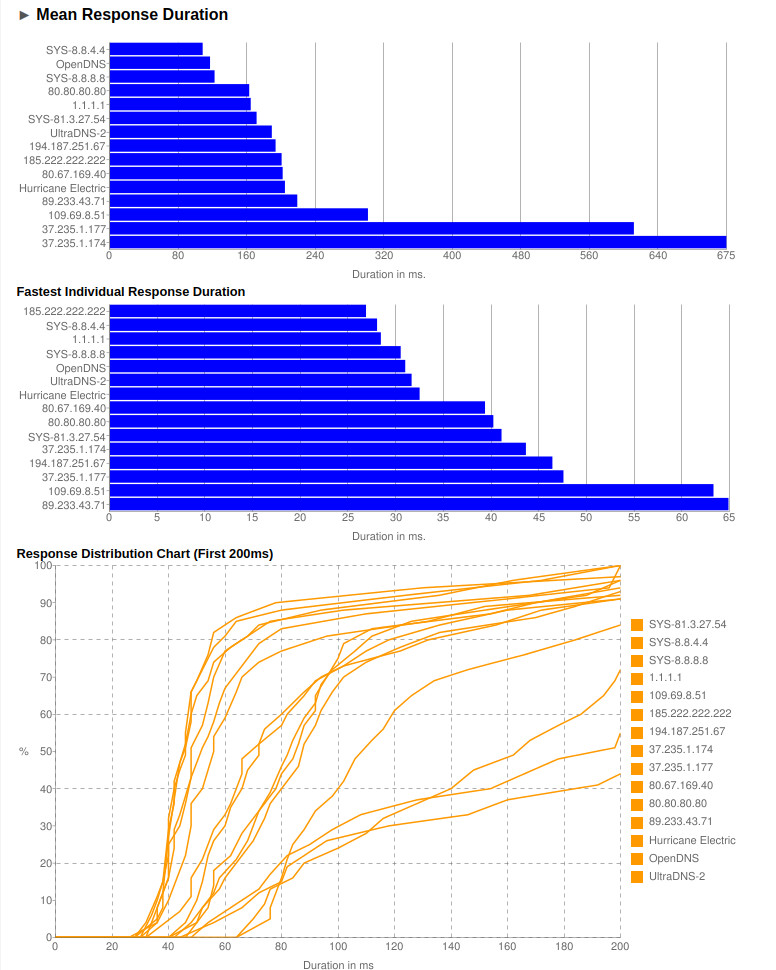
every user want’s a fast & responsive internet. BIND and DNS – the Phonebook of the internet – Berkeley Internet Name Domain – how to benchmark dns servers (find fastest) – LibreDNS There is nothing more anoying than slow loading […]
scroll down to ENGLISH “Zehntausende Mail-Server wegen Exchange-Lücke gehackt. Wegen einer vor wenigen Tagen bekanntgewordenen Sicherheitslücke sind laut US-Medienberichten Zehntausende E-Mail-Server von Unternehmen, Behörden und Bildungseinrichtungen Opfer von Hacker-Attacken geworden. “Deutsche Unternehmen sind im internationalen Vergleich besonders stark von dieser […]
SecurityLab, [22.12.20 10:00] Google has explained the reasons for the massive failure of its services that took place last week. Recall that on December 14 of this year, users around the world for 47 minutes could not access Gmail, YouTube […]
SecurityLab, [03.12.20 11:15] Vulnerabilities in open source software can go undetected for more than four years before being discovered. According to the GitHub State of the Octoverse annual report, the use of open source projects, components, and libraries is more […]
SecurityLab, [02.11.20 11:52] The 50-year-old businessman (Hunter Biden?) in April 2019 brought his device to the IT store Mac Shop in Delaware for repair, but never returned to pick it up. The device was soon seized by the FBI. According […]
Overview Recent 360Netlab unknown threat detection system to capture to a group of unknown malicious families of the sample, which a number of samples supported CPU architectures are x86(32/64), ARM(32/64), MIPS(MIPS32/MIPS-III) as well as PPC, after our analysis, which is […]
contains advertisement. to be honest, it is hard to keep up the speed at which cyber incidents are reported. here is the latest take on “Russian IT Sec Updates”. have phun! SecurityLab, [28.09.20 08:20] Last month, TikTok developers rolled […]
SecurityLab, [14.07.20 15:35] The Electronic Frontier Foundation (EFF) has unveiled a new database demonstrating how and where us law enforcement agencies use tracking technologies. A map of the use of tracking technologies in the United States is presented (https://www.securitylab.ru/news/510018.php) SecurityLab, […]
All SmartPhones are spies! that’s why Merkel keeps the Nokia from 1995 (even if that device is spied on as well, because it can not end2end encrypt sms or phone calls (*FAIL*! X-D)) Putin does not have a mobile phone […]
The Age of Surveillance Capitalism: “be careful what you reveal to your friend” (the internet) https://irlpodcast.org/season4/episode5/ “where it has gone from defending America to controlling it” data google tries to collect from users: (it is probably only the tip of […]
The Great A.I. Awakening: A Conversation with Eric Schmidt Feb 23, 2017 as user might have noticed, the battle Amazon vs Microsoft who will get the $10Billion DoD cloud computing contract is still hot. And maybe the contract is split. […]
SecurityLab, [04.06.20 15:05] The Chinese-language cybercrime group Cycldek (also known as Goblin Panda or Conimes) has developed the malicious tool USBCulprit to carry out attacks on physically isolated systems and steal confidential data. Cycldek APT has developed a malware for […]
this age of mass surveillance… … who is observing “the observers”? guess with it-security and internet-security (internet = roads, cars = computers that users use every day) it is like with real-life-security – there is no 100% security. all users […]
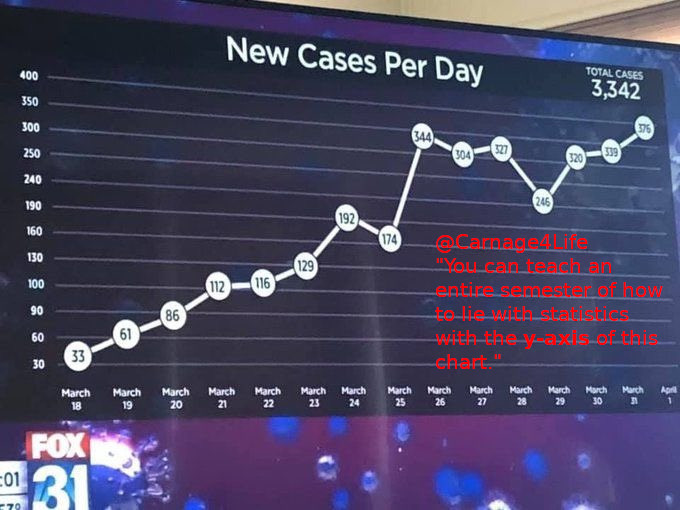
this is why high quality journalism and education are sooooo important: trust is so important & journalism should be about truth and trust context: media outlets that use numbers out of context (do those numbers apply to the US, or […]
scroll down and behave! (slaves of digital dictatorships) short version summary of 1984: short version: 1984 needs to be avoided at any cost. because: it is evil. (Google did not drop it’s motto “don’t be evil” for nothing) in essence: […]
SecurityLab, [26.03.20 08:10] The largest free hosting provider on the darknet, Daniel’s Hosting, was hacked for the second time in 16 months, and stopped working on Wednesday, March 25. Unknown attackers deleted the entire database of the hosting provider, as […]