keyring is a file that stores all sorts of (for example wifi) passwords encrypted Gnome2 based MATE per default creates keyring here: ~/.local/share/keyrings/login.keyring so if the keyring password is lost, only a new keyring can be created. rm -rf ~/.local/share/keyrings/login.keyring […]
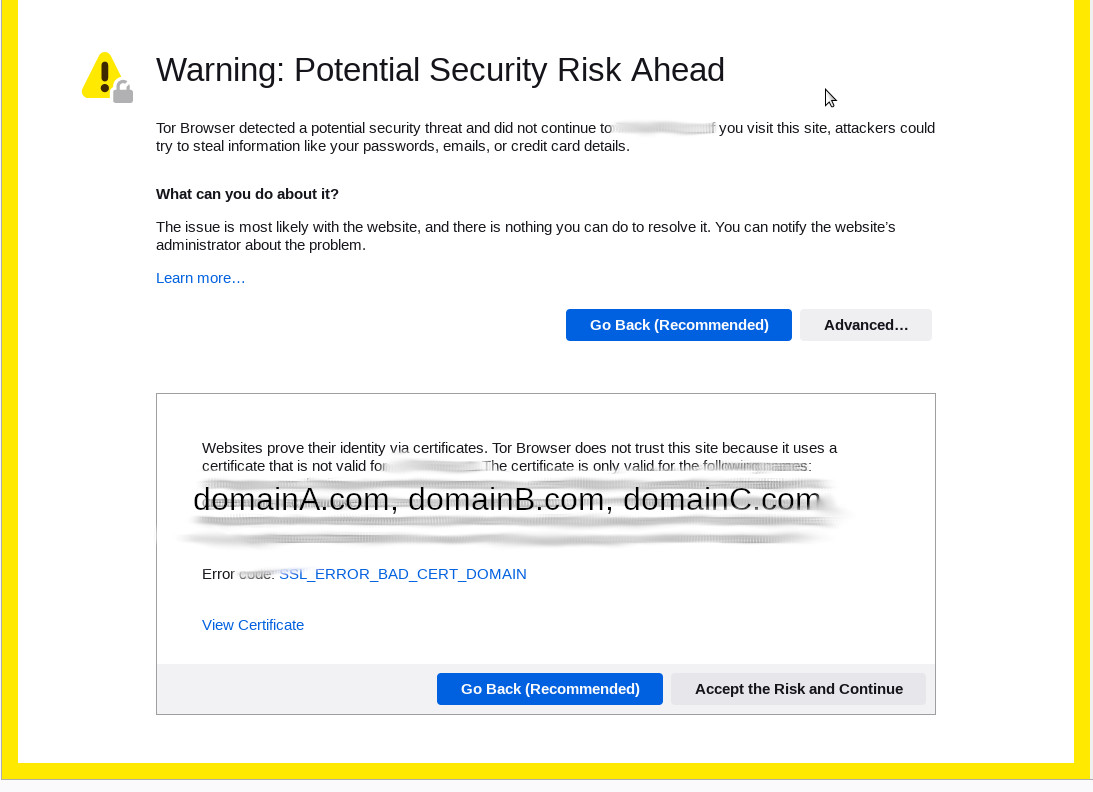
if there are problems… run this one-liner… and ESPECIALLY with let’s encrypt… watch CAREFULLY… as not all errors might show up in a nice red color as errors might NOT be reported for the domainX.com that causes the error… but […]
0) for security: keep all internet connected devices as up to date as possible! “Freifunk updates its router firmware and closes a critical security vulnerability that could allow attackers to install their own firmware on the devices” (src: heise.de) Also […]
criminals abusing tor for malicous behavior should be blocked, right? “50% of the attacks are leveraging the Tor anonymity service to mask their true origins” https://thehackernews.com/2021/12/new-local-attack-vector-expands-attack.html this could destroy the “honest” part of the network that truly exists, because it […]
not sure if the news rang through… the Amazon Cloud (AWS) guy will be the new CEO of Amazon. What cloud? Amazon “cloud” Hetzner “cloud” cloud (centralized digital infrastructure) can be designed / implemented in different ways. from: the user/admin […]
to recover the data: how to mount luks2 encrypted volume also check out alternative: GNU Linux – create new encrypted partition harddisk – how to open encrypted harddisk partition possibility: remove harddisk, attach to sata2usb adapter, then mount on different […]
All SmartPhones are spies! that’s why Merkel keeps the Nokia from 1995 (even if that device is spied on as well, because it can not end2end encrypt sms or phone calls (*FAIL*! X-D)) Putin does not have a mobile phone […]
The Age of Surveillance Capitalism: “be careful what you reveal to your friend” (the internet) https://irlpodcast.org/season4/episode5/ “where it has gone from defending America to controlling it” data google tries to collect from users: (it is probably only the tip of […]
this age of mass surveillance… … who is observing “the observers”? guess with it-security and internet-security (internet = roads, cars = computers that users use every day) it is like with real-life-security – there is no 100% security. all users […]
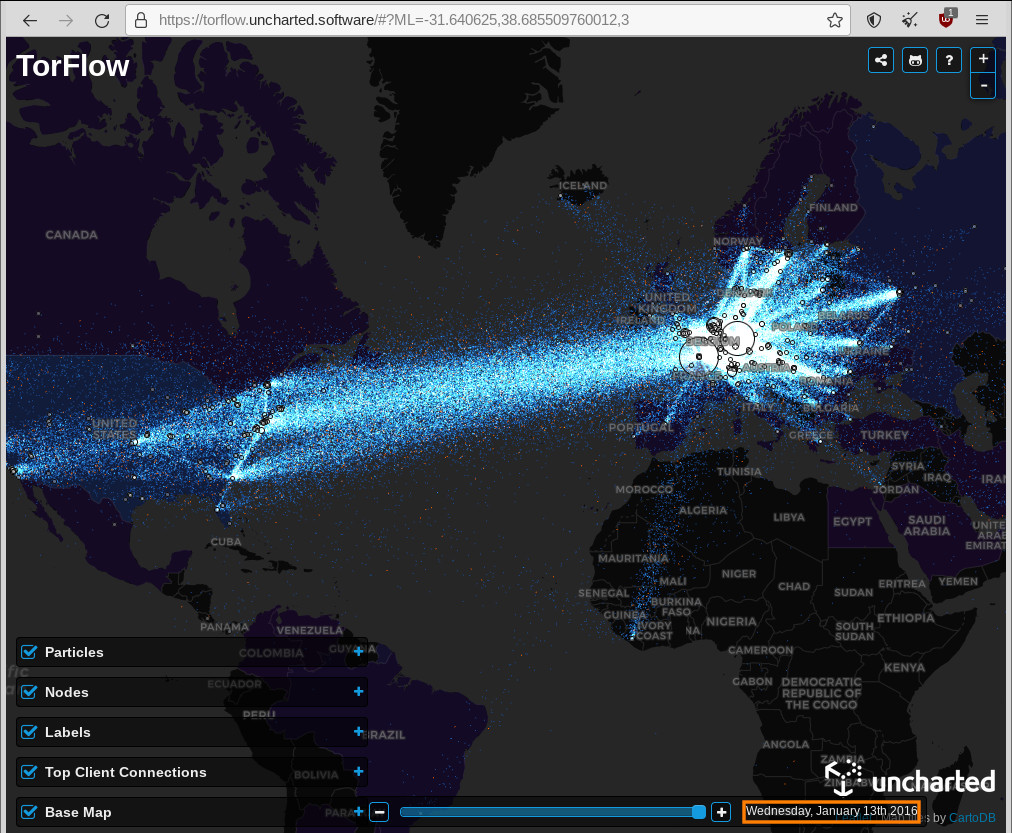
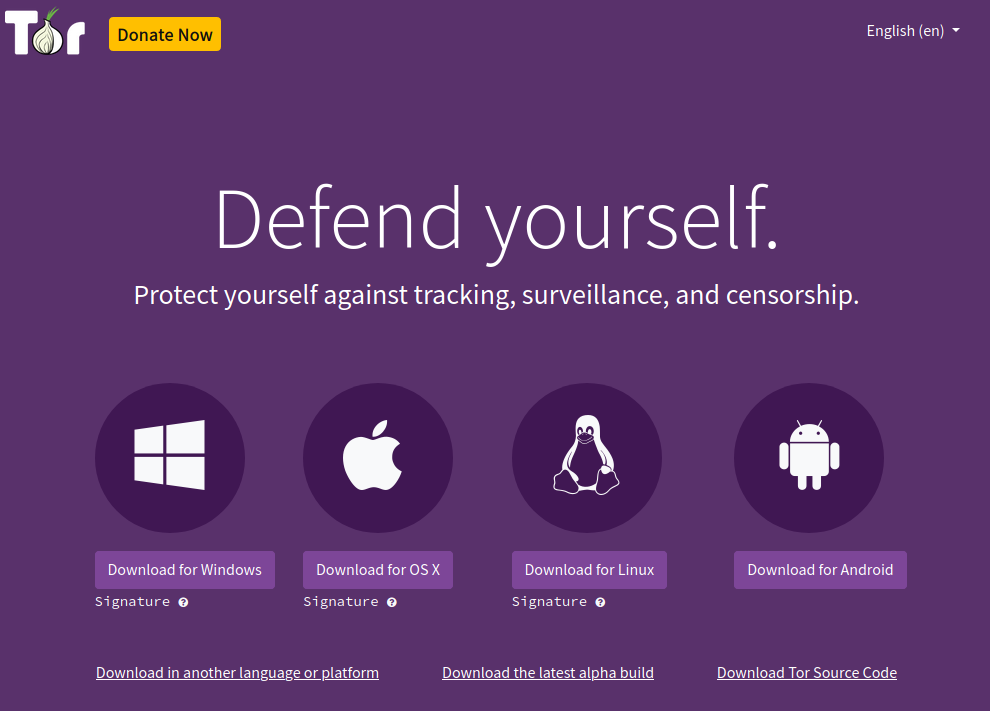
Tor is easier to use than ever superb usability! Tor is now super easy to use! (thanks all involved!) just get the tor bundle – it is tor bundled with firefox https://www.torproject.org/download/ Tor visualized: most users are legit: but criminals […]
scroll down and behave! (slaves of digital dictatorships) short version summary of 1984: short version: 1984 needs to be avoided at any cost. because: it is evil. (Google did not drop it’s motto “don’t be evil” for nothing) in essence: […]
https://theintercept.com/2020/04/03/zooms-encryption-is-not-suited-for-secrets-and-has-surprising-links-to-china-researchers-discover/ hm…. let me think where one has seen this before: TELEGRAM! Zoom’s service is “not suited for secrets” “The researchers also found that Zoom protects video and audio content using a home-grown encryption scheme, that there is a vulnerability […]
Videos: ssh thanks for sharing even when the audio is pretty crappy. slides (hard to read on video) can be found here: https://degabriele.info/slides/SSH_CCS_16.pdf “dropbear” is ambedded ssh server Made in Australia (wiki) also available as Android App naming: a “dropbear” […]
now WITH SPICY COMMENTS X-D SecurityLab, [22.12.19 12:40] A Twitter user using the alias 08Tc3wBB created tfp0-an exploit that allows you to jailbreak the latest iPhone models with IOS 13.3. The functionality of the exploit has already been confirmed by […]
Why is quantum computing important: optimization Update: Google claims to have reached quantum supremacy The tech giant unveiled its x-quantum computer chip Bristlecone in March 2018 (src: cnet) original nasa paper: https://drive.google.com/file/d/19lv8p1fB47z1pEZVlfDXhop082Lc-kdD/view book: https://deepai.org/machine-learning/researcher/eleanor-g-rieffel https://www.amazon.com/Quantum-Computing-Introduction-Engineering-Computation/dp/0262015064 Scott’s Supreme Quantum Supremacy FAQ! […]
really don’t understand how a SoC with 3GB of RAM (!) and a 8x Core ARM can be put to the bin (as Debian GNU Linux runs on devices with as little as 1GB RAM and 2x Cores) because there […]
https://youtu.be/70Blz9hyAz8 https://devtube.dev-wiki.de/videos/watch/f979469f-5fd1-4c40-a8c4-706c20c001f7 While “backdoors” in hardware sound like a good idea… you don’t know how hackers are using it to sabotage infrastructure or extort bitcoins of another country’s companies… see “backdoor in cisco router“. IT IS F**** DANGEROUS! ESPECIALLY if […]
sad update: Peter Eckersley of Let’s Encrypt is Dead may his soul find rest in the open source nirvana from earthly troubles… may the pain of his family and friends be overcome may let’s encrypt live on! Why: Do MAJOR […]
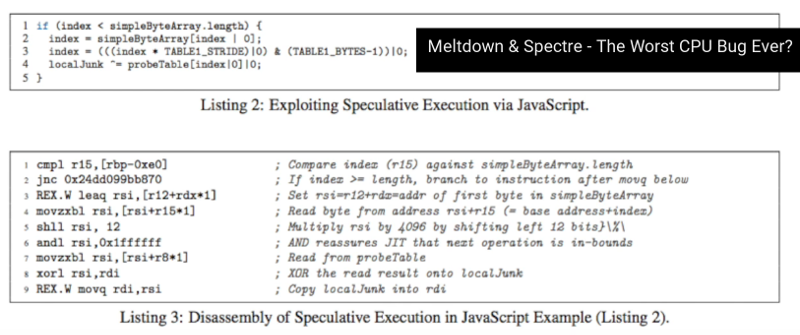
2018-04: RISC-V CPUs not affected by spectre & meltdown “No announced RISC-V silicon is susceptible, and the popular open-source RISC-V Rocket processor is unaffected as it does not perform memory accesses speculatively.” (2018-01-05 src) “If you’re selling an IoT sensor […]
LibreSignal is like Signal – the private WhatsApp and SMS service – but without using requirement for GooglePlay. So people with alterntive firmwares on their phones (CyanogenMod) can use it as well. Is it a fake alternative that started off […]
you should setup harddisk encryption during setup. to add an encrypted /home partition afterwards might be possible but a lot more effort. scroll very down if you want to know how to encrypt an usb sticks … needless to say […]
Warning! while gpg is very likely sound and solid encryption – what is far more likely to be compromised is YOUR HARDWARE – every network card – wifi card – usb UMTS G3 modem – PCI-Card – contains enough RAM […]
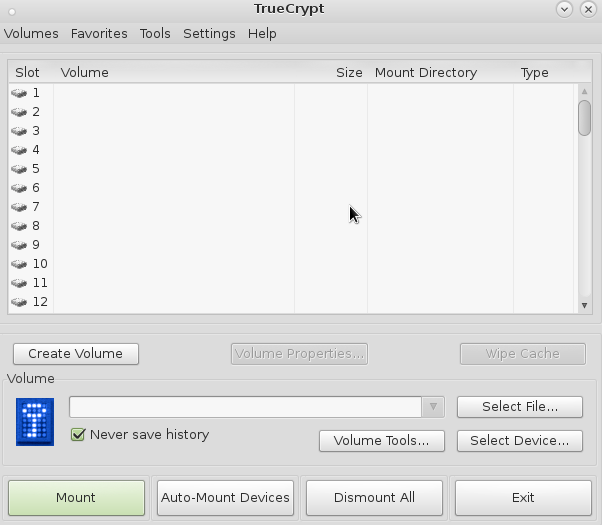
stuff: GNU Linux -> How to Install TrueCrypt / VeraCrypt / ZuluCrypt Veracrypt command line usage: manpage: veracrypt.man.txt # start interactive command line wizard veracrypt -t -c # to create a new encrypted volume or usb stick Volume type: 1) […]
Veracrypt command line usage: manpage: veracrypt.man.txt # start interactive command line wizard veracrypt -t -c # to create a new encrypted volume or usb stick Volume type: 1) Normal 2) Hidden Select [1]: # dismount all volumes currently mounted /usr/bin/veracrypt […]
I don’t know if its fake or not. Since April 2016 or since WhatsApp Version 2.8.2-5222 (iPhone) Facebook-Whatsapp seems to have added encryption. A pretty brave move of the Facebook-Whatsapp guys… if this is for real. If this is for […]
PGP stands for “PGP is the short form for Pretty Good Privacy” how it works: it is an encryption system that allows data to be encrypted with an world-known public key, then savely transported to the intended receiver and only […]
stuff: GNU Linux -> How to Install TrueCrypt / VeraCrypt / ZuluCrypt Veracrypt command line usage: manpage: veracrypt.man.txt # start interactive command line wizard veracrypt -t -c # to create a new encrypted volume or usb stick Volume type: 1) […]
checkout https://dwaves.de/2016/02/26/is-truecrypt-insecure/ and successor: https://sourceforge.net/projects/veracrypt/files/ vim /usr/bin/nautilus #!/bin/bash # set your filemanager here filemgr=thunar # set your webbrowser here, usually x-www-browser should be perfect webbrowser=x-www-browser ### DO NOT CHANGE ANYTHING BELOW HERE unless you know what you’re doing ### oldparams=$@ […]
Update: 2020-05 PDF are important file formats for document exchange, but in 2020 PDF as Mail-Attachments can not be 100% trusted anymore. how to create PDF under Linux? there are various programs that support export to PDF format least but […]
update: 2020-02: First of: thanks! PGP + enigmail + Thunderbird is is working great on for example: GNU Debian Linux 10. And setup now can be done by normal users. (the enigmail wizard is pretty nice) THANKS ALL INVOLVED 🙂 […]