Update: 2021-02
“A statement from the German Federal Criminal Police Office about their participation in Operation Ladybird said prosecutors seized 17 servers in Germany that acted as Emotet controllers.”
and many bars of gold and cash were seized in Ukraine… as can be seen on youtube.
https://krebsonsecurity.com/2021/01/international-action-targets-emotet-crimeware/
update: Emotet trying to spread by WIFI since 2018
https://thehackernews.com/2020/02/emotet-malware-wifi-hacking.html
BUT ALSO VIA PDF!
on the heise security conference last year was said: Virus Scanners since around 10 years are not sufficient anymore.
(heise a computer focused news outlet itself was infected on Mai 2019 with emotet trojan probably via word.doc (src))
today that statement has become reality.
neither ClamAV nor Antivir were able to spot the virus or virus-loader in the word.doc attachment.
The “System” collects mails of hacked systems to send out pretty authentic SPAM Mails with Attachment Word.doc or File.pdf macro virus attachments.
(that’s what one is conviced… why are macros even allowed to be embedded in those formats? ? (M$, ADOBE WHAT WERE YOU THINKING?)
it was (phone call) confirmed that a dental practice has been virus infected which started sending mails with those auto generated spam word.doc via multiple servers.
with all this fancy AI + BigData = auto generating and mass mailing (emotet) very authentic
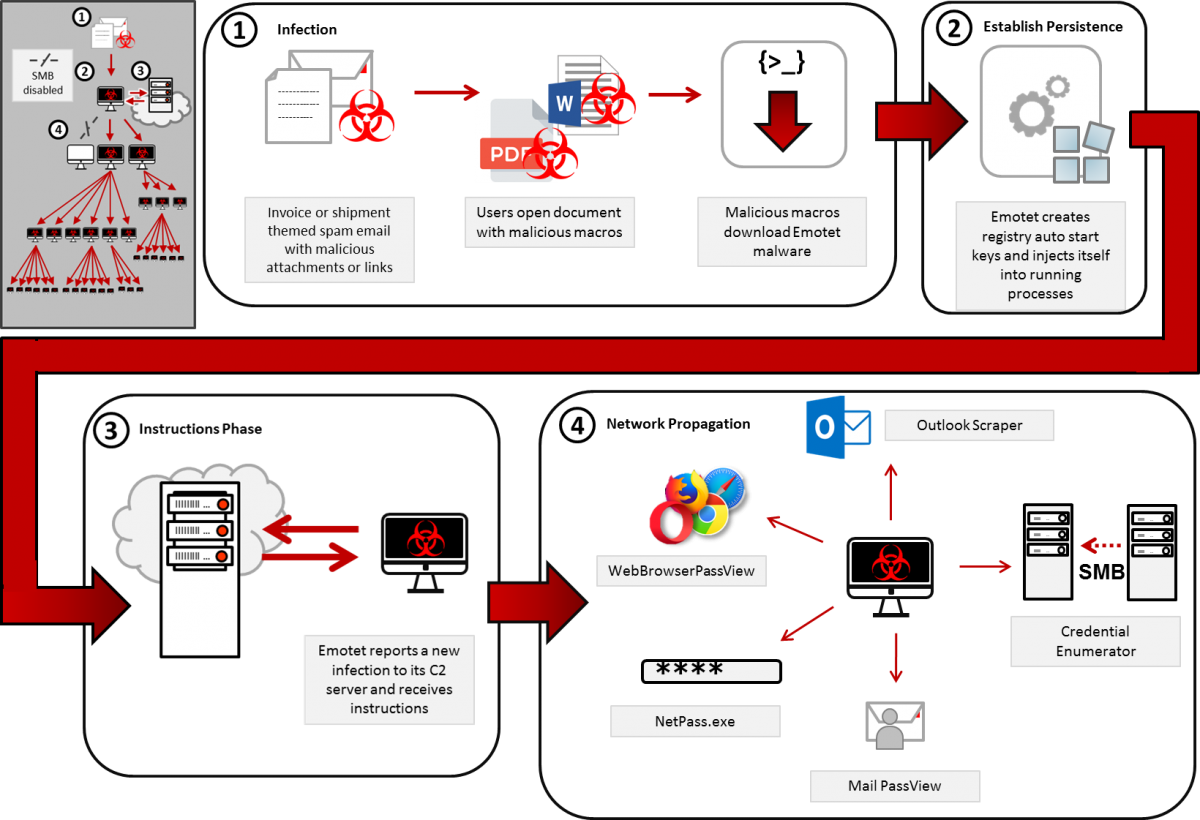
how emotet works:
Currently, Emotet uses five known spreader modules: NetPass.exe, WebBrowserPassView, Mail PassView, Outlook scraper, and a credential enumerator.
- NetPass.exe is a legitimate utility developed by NirSoft that recovers all network passwords stored on a system for the current logged-on user. This tool can also recover passwords stored in the credentials file of external drives.
- Outlook scraper is a tool that scrapes names and email addresses from the victim’s Outlook accounts and uses that information to send out additional phishing emails from the compromised accounts.
- WebBrowserPassView is a password recovery tool that captures passwords stored by Internet Explorer, Mozilla Firefox, Google Chrome, Safari, and Opera and passes them to the credential enumerator module.
- Mail PassView is a password recovery tool that reveals passwords and account details for various email clients such as Microsoft Outlook, Windows Mail, Mozilla Thunderbird, Hotmail, Yahoo! Mail, and Gmail and passes them to the credential enumerator module.
- Credential enumerator is a self-extracting RAR file containing two components: a bypass component and a service component. The bypass component is used for the enumeration of network resources and either finds writable share drives using Server Message Block (SMB) or tries to brute force user accounts, including the administrator account. Once an available system is found, Emotet writes the service component on the system, which writes Emotet onto the disk. Emotet’s access to SMB can result in the infection of entire domains (servers and clients).
src: https://www.us-cert.gov/ncas/alerts/TA18-201A
mail header2:
Return-path: <noc@maxnetonlinebd.com> Envelope-to: user@domain.com Delivery-date: Fri, 25 Oct 2019 13:00:21 +0200 Received: from mail.maxnetonlinebd.com ([103.209.81.230] helo=smtp.banglalionmail.com) whois: 103.209.81.230 address: Aqua Tower(Level-5),43 Mohakhali C/A,Dhaka-1212 by www314.your-server.de with esmtps (TLSv1.2:DHE-RSA-AES256-GCM-SHA384:256) (Exim) (envelope-from <noc@maxnetonlinebd.com>) id 1iNxKK-0002kM-UN for user@domain.com; Fri, 25 Oct 2019 13:00:21 +0200 Received: from [213.194.151.228] (static.228.151.194.213.ibercom.com [213.194.151.228]) by smtp.banglalionmail.com (Postfix) with ESMTPSA id A3A4F1B40AA6 for <user@domain.com>; Fri, 25 Oct 2019 17:00:01 +0600 (BDT) Date: Fri, 25 Oct 2019 13:01:02 +0100 From: =?UTF-8?B?WmFobmtsaW5payBHw7xuemJ1cmcgS0ZP?= <noc@maxnetonlinebd.com> To: <user@domain.com> Subject: =?UTF-8?B?RG9rdW1lbnQgcGVyIE1haWwgdm9uIFphaG5rbGluaWsgR8O8bnpidXJnIEtGTw==?= MIME-Version: 1.0 Content-Type: multipart/mixed; boundary="----=_Part_16315_3727703759.23889407221704219670" X-Virus-Scanned: Clear (ClamAV 0.101.4/25613/Fri Oct 25 11:00:25 2019) X-Spam-Score: -1.8 (-) Delivered-To: user-user@domain.com ------=_Part_16315_3727703759.23889407221704219670 Content-Type: text/plain; charset=UTF-8 Content-Transfer-Encoding: quoted-printable
mail header1:
Return-path: <m.ringel@alumont.com> Envelope-to: user@domain.com Delivery-date: Thu, 24 Oct 2019 10:32:47 +0200 Received: from lion.totocom.de ([212.80.235.131]) whois 212.80.235.131 address: Schlittermann -- Internet & Unix Support address: D-01099 Dresden by www314.your-server.de with esmtps (TLSv1.2:DHE-RSA-AES256-GCM-SHA384:256) (Exim) (envelope-from <m.ringel@alumont.com>) id 1iNYY2-0005tE-Iq for user@domain.com; Thu, 24 Oct 2019 10:32:47 +0200 Received: from 109.red-81-32-27.dynamicip.rima-tde.net ([81.32.27.109]) by lion.totocom.de with esmtpsa (TLSv1.2:ECDHE-RSA-AES256-GCM-SHA384:256) (Exim) (envelope-from <m.ringel@alumont.com>) id 1iNYXy-0003Z9-I0 for user@domain.com; Thu, 24 Oct 2019 10:32:43 +0200 Date: Thu, 24 Oct 2019 10:32:41 +0100 From: =?UTF-8?B?WmFobmtsaW5payBHw7xuemJ1cmcgQWJyZWNobnVuZw==?= <m.ringel@alumont.com> To: <user@domain.com> Subject: unsere Antwort MIME-Version: 1.0 Content-Type: multipart/mixed; boundary="----=_Part_1914_1426462523.13408587673991828238" X-Virus-Scanned: Clear (ClamAV 0.101.4/25611/Wed Oct 23 10:58:37 2019) X-Spam-Score: -0.1 (/) Delivered-To: user-user@domain.com ------=_Part_1914_1426462523.13408587673991828238 Content-Type: text/plain; charset=UTF-8 Content-Transfer-Encoding: quoted-printable =0DAnbei erhalten Sie Ihre angeforderte Informationen f=C3=BCr Ihre Unterla= gen. =0DFreue mich von Ihnen zu h=C3=B6ren auf gute Zusammenarbeit. =0DViele Gr=C3=BC=C3=9Fe Ihr Zahnklinik Abrechnung Team =0DTelefon: 0800 XXX (kostenfrei)=0DMail:abrechnung@dr-XXX= de ------=_Part_1914_1426462523.13408587673991828238 Content-Type: application/msword; name="INF 2019_10_ 24_20.doc" Content-Transfer-Encoding: base64 Content-Disposition: attachment; filename="INF 2019_10_ 24_20.doc" 0M8R4KGxGuEAAAAAAAAAAAAAAAAAAAAAPgADAP7/CQAGAAAAAAAAAAAAAAADAAAAEgAAAAAAAAAA EAAAFAAAAAIAAAD+////AAAAABEAAABuAAAA/gAAA
Links:
https://en.wikipedia.org/wiki/Emotet
Files:
pwd encrypted.zip: VirusInfectedMail
More RansomeWare News:
Ransomware Attack Affects Municipal Computer Systems in Johnson City, Tennessee
On Oct. 21, a Johnson City employee showed a ransom note left by the ransomware attackers to city IT Director Lisa Sagona. The message asked city officials to contact an email in exchange for payment instructions. Toward that end, the note claimed that the ransomware had encrypted the city government’s backups to dissuade the municipality from attempting to recover its data by any means other than paying for a decryption key.
Ransomware Attack: Cybercriminals Hit California School District – MSSP Alert
California’s San Bernardino City Unified School District (SBCUSD) has discovered that cybercriminals recently used ransomware to lock access to district files. The ransomware attack was launched against SBCUSD’s computer servers, and these servers are currently inaccessible.
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!