0) for security: keep all internet connected devices as up to date as possible!
“Freifunk updates its router firmware and closes a critical security vulnerability that could allow attackers to install their own firmware on the devices” (src: heise.de)
Also update the user regularly on it-sec & privacy news:
- here is a list of sources that might be usefull to watch
- try to subscribe to itsec rss feeds, many desktop and mobile apps can do rss
1) use GNU Linux, use tails:
for tails’ wifi to work special adapters are needed (that are supported by open source drivers)
2) use privacy respecting web browsers & search engines
warning:
- EN: ATTENTION! ABSOLUTE IT SECURITY AND ONLINE PRIVACY DO NOT EXIST! NO HOWTO IS PERFECT! IF THE PC/LAPTOP/SMARTPHONE ALREADY HAS SPYWARE PREINSTALLED (WINDOWS OR OSX) A VPNs & FIREWALLS ARE BETTER THAN NOTHING, BUT WILL NOT GIVE ABSOLUTE PROTECTION! YOU HAVE BEEN WARNED!
- DE: ACHTUNG! DIE ABSOLUTE IT SICHERHEIT UND ONLINE PRIVATSPHÄRE GIBT ES NICHT! KEIN HOWTO IST PERFEKT! WENN DER PC/LAPTOP/SMARTPHONE SCHON SPYWARE (WINDOWS ODER OSX) VORINSTALLIERT HAT, BRINGT DAS GANZE AUCH NICHT VIEL! SIE WURDEN GEWARNT!
- RU: ВНИМАНИЕ! АБСОЛЮТНОЙ ИТ-БЕЗОПАСНОСТИ И КОНФИДЕНЦИАЛЬНОСТИ В ИНТЕРНЕТЕ НЕ СУЩЕСТВУЕТ! НЕТ HOWTO ИДЕАЛЬНО! ЕСЛИ НА ПК / НОУТБУКЕ / СМАРТФОНЕ УЖЕ ПРЕДУСТАНОВЛЕНО ШПИОНСКОЕ ПО (WINDOWS ИЛИ OSX), VPN И БРАНДМАУЭРЫ ЛУЧШЕ, ЧЕМ НИЧЕГО, НО НЕ ДАДУТ АБСОЛЮТНОЙ ЗАЩИТЫ! ВЫ ПРЕДУПРЕЖДЕНЫ!
- UA: УВАГА! АБСОЛЮТНОЇ ІТ-БЕЗПЕКИ ТА КОНФІДЕНЦІЙНОСТІ В ІНТЕРНЕТІ НЕ ІСНУЄ! ЖОДНЕ ХАУТО НЕ Є ІДЕАЛЬНИМ! ЯКЩО НА ПК/НОУТБУЦІ/СМАРТФОНІ ВЖЕ Є ПОПЕРЕДНЬО ІНСТАЛЬОВАНІ ШПИГУНСЬКІ ПРОГРАМИ (WINDOWS АБО OSX), VPN & FIREWALLS КРАЩЕ, НІЖ НІЧОГО, АЛЕ НЕ ДАСТЬ АБСОЛЮТНОГО ЗАХИСТУ! ВАС ПОПЕРЕДИЛИ!
- ES: ¡ATENCIÓN! ¡LA SEGURIDAD ABSOLUTA DE TI Y LA PRIVACIDAD EN LÍNEA NO EXISTEN! ¡NO HOWTO ES PERFECTO! SI LA PC / COMPUTADORA PORTÁTIL / TELÉFONO INTELIGENTE YA TIENE SPYWARE PREINSTALADO (WINDOWS U OSX) UNA VPN Y FIREWALLS SON MEJORES QUE NADA, ¡PERO NO DARÁN PROTECCIÓN ABSOLUTA! ¡HAS SIDO ADVERTIDO!
- FR: ATTENTION! LA SÉCURITÉ INFORMATIQUE ABSOLUE ET LA CONFIDENTIALITÉ EN LIGNE N’EXISTENT PAS! NO HOWTO EST PARFAIT! SI LE PC / ORDINATEUR PORTABLE / SMARTPHONE A DÉJÀ UN LOGICIEL ESPION PRÉINSTALLÉ (WINDOWS OU OSX), UN VPN ET DES PARE-FEU VALENT MIEUX QUE RIEN, MAIS NE DONNERONT PAS UNE PROTECTION ABSOLUE! VOUS ÊTES PRÉVENUS !
- CN: 注意力!绝对的IT安全和在线隐私不存在!没有如何是完美的!如果PC/笔记本电脑/智能手机已经预装了间谍软件(WINDOWS或OSX),那么VPN和防火墙总比没有好,但不会提供绝对的保护!你被警告了!
start:
- EN: Parallel to the real war, an information war is taking place on the Internet, which threatens the privacy of journalists and whistleblowers even more than usual, what possibilities are there to protect oneself?
- Snowden: “At the end of the day, saying you don’t care about privacy because you have nothing to hide is no different than saying you don’t care about free speech because you have nothing to say.”
- DE: Parallel zum realen Krieg findet ein Informations Krieg im Internet statt, welcher die Privatsphäre von Journalisten und Whistleblowern noch mehr bedroht als sonst, welche möglichkeiten gibt es sich zu schützen?
- Snowden: “zu sagen, dass einem Privatsphäre egal ist, weil man nichts zu verbergen hat, ist nichts anderes, als zu sagen, dass einem die Redefreiheit egal ist weil man nichts zu sagen hat”
- RU: Параллельно с реальной войной в интернете идет информационная война, которая угрожает частной жизни журналистов и осведомителей еще больше, чем обычно, какие есть возможности защитить себя?
- Сноуден: В конце концов, сказать, что вы не заботитесь о конфиденциальности, потому что вам нечего скрывать, ничем не отличается от того, чтобы сказать, что вы не заботитесь о свободе слова, потому что вам нечего сказать.
- UA: Паралельно з реальною війною в інтернеті йде інформаційна війна, яка загрожує приватному життю журналістів і викривачів навіть більше, ніж зазвичай, які можливості є, щоб захистити себе?
- Сноуден: Зрештою, говорити, що ви не дбаєте про приватність, тому що вам нема чого приховувати, нічим не відрізняється від того, щоб сказати, що ви не дбаєте про свободу слова, тому що вам нема чого сказати.
- ES: Paralelamente a la guerra real, se está produciendo una guerra de información en Internet, que amenaza la privacidad de periodistas y denunciantes aún más de lo habitual, ¿qué posibilidades hay para protegerse?
- Snowden: Al final del día, decir que no te importa la privacidad porque no tienes nada que ocultar no es diferente a decir que no te importa la libertad de expresión porque no tienes nada que decir.
- FR : Parallèlement à la vraie guerre, une guerre de l’information se déroule sur Internet, qui menace encore plus que d’habitude la vie privée des journalistes et des lanceurs d’alerte, quelles sont les possibilités de se protéger?
- Snowden : En fin de compte, dire que vous ne vous souciez pas de la vie privée parce que vous n’avez rien à cacher n’est pas différent de dire que vous ne vous souciez pas de la liberté d’expression parce que vous n’avez rien à dire.
- CN: 在真正的战争的同时,互联网上正在发生一场信息战,这比平时更威胁记者和举报人的隐私,有什么可能保护自己?
- 斯诺登:归根结底,说你不关心隐私,因为你没有什么可隐瞒的,这与说你不关心言论自由没有什么不同,因为你无话可说。
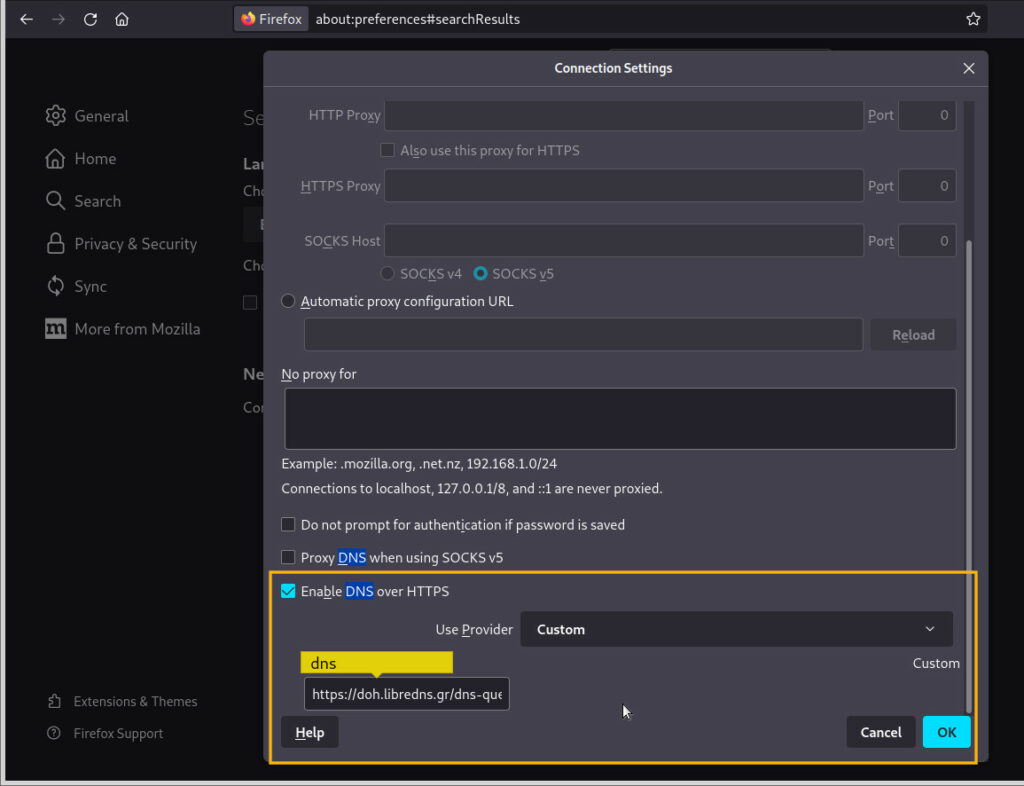
0) dns servers:
test: https://dnsleaktest.com/
- EN: there is a “phone book” server called DNS sever which are contacted before www.domain.com is loaded with the question: “which ip phone number has www.domain.com?” You have to be able to trust the DNS server, because it knows which websites have been visited.
- DE: es gibt einen “Telefonbuch” Server genannt DNS sever welche vor jeder www.domain.com anfragen gefragt wird: welche ip-telefonnummer hat denn www.domain.com? Man muss dem DNS server vertrauen können, weil dieser weiss welche websites besucht wurden.
- RU: Существует сервер «телефонной книги», называемый DNS-сервером, с которым связываются перед загрузкой www.domain.com с вопросом: «какой IP-номер телефона www.domain.com?» Вы должны быть в состоянии доверять DNS-серверу, потому что он знает, какие веб-сайты были посещены.
- UA: існує сервер “телефонної книги” під назвою DNS sever, з яким зв’язуються, перш ніж www.domain.com завантажується з питанням: “який ip-номер телефону має www.domain.com?” Ви повинні бути в змозі довіряти DNS-серверу, тому що він знає, які веб-сайти були відвідані.
- ES: hay un servidor de “libreta de teléfonos” llamado DNS sever que se contacta antes de www.domain.com se carga con la pregunta: “¿qué número de teléfono IP tiene www.domain.com?” Debe poder confiar en el servidor DNS, porque sabe qué sitios web se han visitado.
- FR: il y a un serveur « annuaire téléphonique » appelé DNS sever qui est contacté avant que www.domain.com ne soit chargé avec la question: « quel numéro de téléphone IP a www.domain.com? » Vous devez pouvoir faire confiance au serveur DNS, car il sait quels sites Web ont été visités.
- CN: 有一个名为DNS sever的”电话簿”服务器,在加载 www.domain.com 之前,我们会联系该服务器:”哪个IP电话号码 www.domain.com?您必须能够信任DNS服务器,因为它知道访问过哪些网站。
1) tor browser bundle
https://www.torproject.org/download/
- EN: tor-browser-bundle, it is very simple to install and available for Windows, OSX and GNU Linux, it already has an alternative DNS server installed, please donate https://donate.torproject.org/ so that the project can be improved.
- DE: tor-browser-bundle nutzen, es ist sehr einfach und für Windows, OSX und GNU Linux erhältlich, tor-browser-bundle hat schon einen alternativen DNS server eingebaut, bitte spenden https://donate.torproject.org/ damit das projekt verbessert werden kann.
- RU: tor-browser-bundle, он очень прост в установке и доступен для Windows, OSX и GNU Linux, у него уже установлен альтернативный DNS-сервер, пожалуйста, пожертвуйте https://donate.torproject.org/, чтобы проект можно было улучшить.
- UA: tor-browser-bundle, він дуже простий в установці і доступний для Windows, OSX і GNU Linux, у нього вже встановлений альтернативний DNS-сервер, будь ласка, пожертвуйте https://donate.torproject.org/, щоб проект можна було вдосконалити.
- ES: tor-browser-bundle, es muy sencillo de instalar y está disponible para Windows, OSX y GNU Linux, ya tiene un servidor DNS alternativo instalado, por favor done https://donate.torproject.org/ para que el proyecto pueda ser mejorado.
- FR: tor-browser-bundle, il est très simple à installer et disponible pour Windows, OSX et GNU Linux, il a déjà un serveur DNS alternatif installé, veuillez faire un don https://donate.torproject.org/ afin que le projet puisse être amélioré.
- CN: tor-browser-bundle,它安装非常简单,可用于Windows,OSX和GNU Linux,它已经安装了替代DNS服务器,请捐赠 https://donate.torproject.org/ 以便可以改进项目。
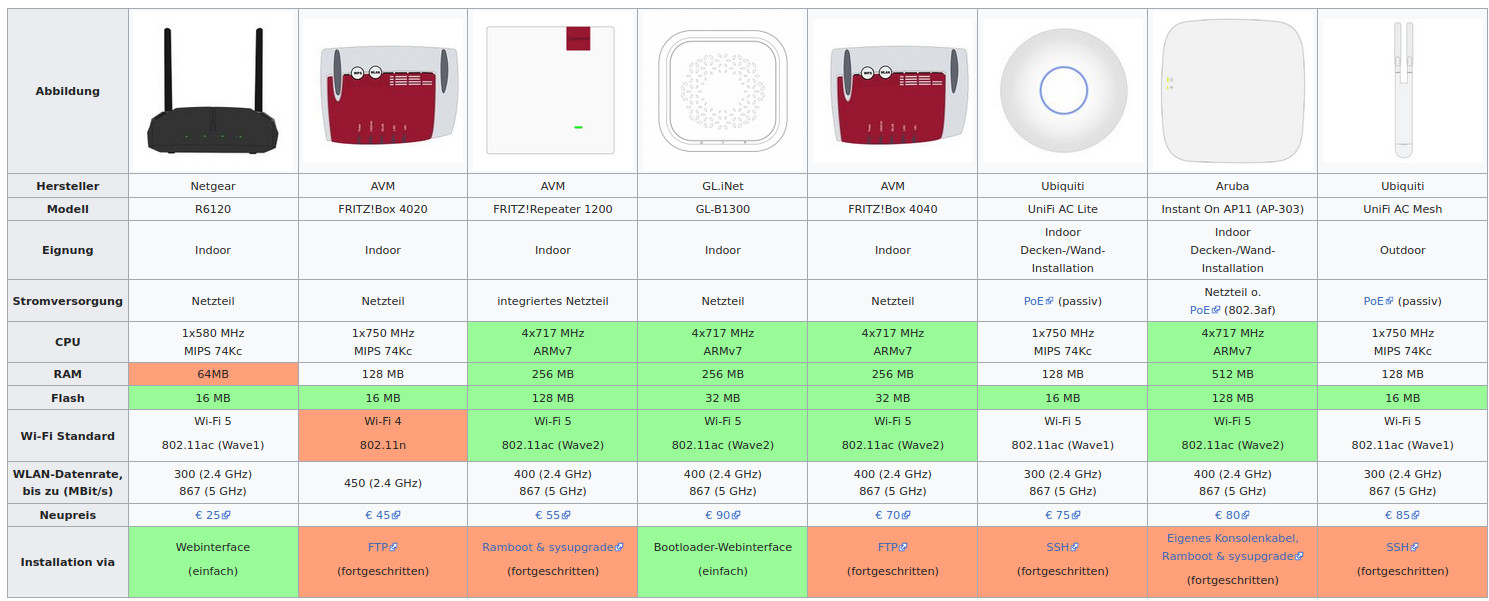
2) freifunk firmware vpn
https://firmware.freifunk-ulm.de/
- 32MBit FLASH (OPTIMAL)
- 16MBit FLASH (GOOD)
- 8MBit FLASH: (MINIMUM)
- 4MBit FLASH: NO BUY! (FIRMWARE SOON TOO BIG!)
- DE: hier updated man die firmware eines routers mit einer freifunk firmware, welche einen kostenlosen VPN tunnel entweder über Deutschland oder Schweden auf baut, man muss ein passende router modell haben (sehr günstig bei ebay).
- EN: with freifunk the user updates a router with the freifunk firmware, which has a build-in free VPN tunnel via Germany or Sweden, the user needs a compatible router model.
- RU: с freifunk пользователь обновляет маршрутизатор с прошивкой freifunk, которая имеет встроенный бесплатный VPN-туннель через Германию или Швецию, пользователю нужна совместимая модель маршрутизатора.
- UA: з freifunk користувач оновлює маршрутизатор за допомогою прошивки freifunk, яка має вбудований безкоштовний VPN-тунель через Німеччину або Швецію, користувачеві потрібна сумісна модель маршрутизатора.
- ES: con freifunk el usuario actualiza un router con el firmware freifunk, que tiene un túnel VPN gratuito incorporado a través de Alemania o Suecia, el usuario necesita un modelo de router compatible.
- FR: avec freifunk, l’utilisateur met à jour un routeur avec le firmware freifunk, qui dispose d’un tunnel VPN gratuit intégré via l’Allemagne ou la Suède, l’utilisateur a besoin d’un modèle de routeur compatible.
- CN: 使用freifunk,用户使用freifunk固件更新路由器,该固件具有通过德国或瑞典的内置免费VPN隧道,用户需要兼容的路由器型号。
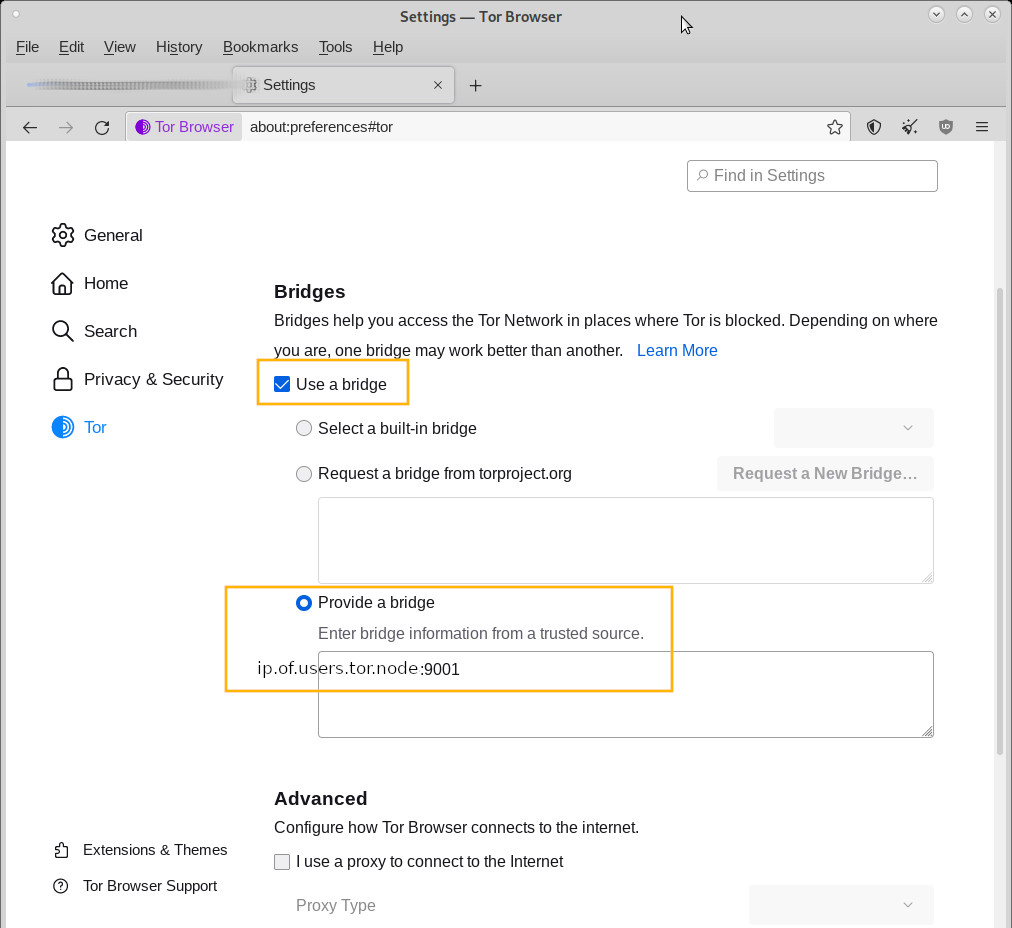
3) tor server node
https://community.torproject.org/relay/setup/bridge/debian-ubuntu/
- EN: here user has to be technically savvy and also spend a little money (for a VPS, VirtualPrivateServer i.e. a virtual server running in a data center) Advantage of your own tor server: it also helps others (tor always connects via several servers) but the tor-browser-bundle can be configured to use that specific server as a start server
- DE: hier muss man technisch schon etwas versiert sein und auch Geld ausgeben (für einen VPS, VirtualPrivateServer d.h. eine virtuellen Server der in einem Rechenzentrum läuft)
- vorteil eines eigenen tor servers: man hilft nicht nur anderen (tor verbindet sich immer über mehrere server) sondern kann den eigenen TOR server node als start node im tor-bundle-browser eintragen:
- RU: здесь пользователь должен быть технически подкованным, а также тратить немного денег (для VPS, VirtualPrivateServer, т.е. виртуального сервера, работающего в центре обработки данных) Преимущество собственного сервера tor: он также помогает другим (tor всегда подключается через несколько серверов), но tor-browser-bundle можно настроить на использование этого конкретного сервера в качестве стартового сервера
- UA: тут користувач повинен бути технічно підкованим, а також витратити трохи грошей (для VPS, VirtualPrivateServer, тобто віртуального сервера, що працює в центрі обробки даних) Перевага вашого власного сервера tor: він також допомагає іншим (tor завжди підключається через кілька серверів), але tor-браузер-пакет може бути налаштований на використання цього конкретного сервера в якості стартового сервера
- ES: aquí el usuario tiene que ser técnicamente inteligente y también gastar un poco de dinero (para un VPS, VirtualPrivateServer, es decir, un servidor virtual que se ejecuta en un centro de datos) Ventaja de su propio servidor tor: también ayuda a otros (tor siempre se conecta a través de varios servidores) pero el paquete tor-browser se puede configurar para usar ese servidor específico como servidor de inicio
- FR: ici, l’utilisateur doit être techniquement averti et aussi dépenser un peu d’argent (pour un VPS, VirtualPrivateServer, c’est-à-dire un serveur virtuel fonctionnant dans un centre de données) Avantage de votre propre serveur tor: il aide également les autres (tor se connecte toujours via plusieurs serveurs) mais le tor-browser-bundle peut être configuré pour utiliser ce serveur spécifique comme serveur de démarrage
- CN: 在这里,用户必须精通技术,并且还要花一点钱(对于VPS,VirtualPrivateServer,即在数据中心运行的虚拟服务器)您自己的tor服务器的优势:它还可以帮助其他人(tor始终通过多个服务器连接),但tor-browser-bundle可以配置为使用该特定服务器作为启动服务器
3.1) auto updates
- EN: there should be as few other services as possible running on the vps, the more software is installed, the more problems there could be with automatic updates.
- DE: es sollte auf der vps möglichst keine/wenig andere services laufen, umso mehr software installiert ist, umso mehr probleme könnte es bei automatischen updates geben.
- RU: на vps должно быть как можно меньше других сервисов, чем больше программного обеспечения установлено, тем больше проблем может быть с автоматическими обновлениями.
- UA: на vps має працювати якомога менше інших сервісів, чим більше програмного забезпечення встановлено, тим більше проблем може бути з автоматичними оновленнями.
- ES: debería haber la menor cantidad posible de otros servicios ejecutándose en el vps, cuanto más software se instale, más problemas podría haber con las actualizaciones automáticas.
- FR: il devrait y avoir le moins d’autres services possible fonctionnant sur les vps, plus il y a de logiciels installés, plus il pourrait y avoir de problèmes avec les mises à jour automatiques.
- CN: vps上运行的其他服务应该尽可能少,安装的软件越多,自动更新的问题就越多。
crontab:
lsb_release -a; # tested Description: Debian GNU/Linux 11 (bullseye) su - root crontab -e; # will run the update process every night at 3:00 am 0 3 * * * /scripts/update.sh
update script:
vim /scripts/update.sh #!/bin/bash echo "=== attempting automatic daily update on $(date '+%Y-%m-%d-%H:%M:%S') ===" | tee -a /scripts/update.sh.log apt update 2>&1 | tee -a /scripts/update.sh.log apt -y upgrade 2>&1 | tee -a /scripts/update.sh.log echo "=== automatically removing un-needed packages (and old kernels) ===" # keeping too many old kernel versions might fill up boot partition apt -y autoremove | tee -a /scripts/update.sh.log echo "=== fine ===" | tee -a /scripts/update.sh.log echo "" | tee -a /scripts/update.sh.log
- eine mögliche tor config file könnte so aussehen:
- sample config:
- vim /etc/tor/torrc
- when a Nickname is specified, it is possible to search for the node via
- https://atlas.torproject.org/rs.html
- so this and the contact info is publicly available, so rather chose something anonymous 😀
- vim /etc/tor/torrc
- sample config:
vim /etc/tor/torrc ## Configuration file for a typical Tor user ## Last updated 9 October 2013 for Tor 0.2.5.2-alpha. ## (may or may not work for much older or much newer versions of Tor.) ## ## Lines that begin with "## " try to explain what's going on. Lines ## that begin with just "#" are disabled commands: you can enable them ## by removing the "#" symbol. ## ## See 'man tor', or https://www.torproject.org/docs/tor-manual.html, ## for more options you can use in this file. ## ## Tor will look for this file in various places based on your platform: ## https://www.torproject.org/docs/faq#torrc ## Tor opens a socks proxy on port 9050 by default -- even if you don't ## configure one below. Set "SocksPort 0" if you plan to run Tor only ## as a relay, and not make any local application connections yourself. SocksPort 0 #SocksPort 9050 # Default: Bind to localhost:9050 for local connections. #SocksPort 192.168.0.1:9100 # Bind to this address:port too. ## Entry policies to allow/deny SOCKS requests based on IP address. ## First entry that matches wins. If no SocksPolicy is set, we accept ## all (and only) requests that reach a SocksPort. Untrusted users who ## can access your SocksPort may be able to learn about the connections ## you make. #SocksPolicy accept 192.168.0.0/16 #SocksPolicy reject * ## Logs go to stdout at level "notice" unless redirected by something ## else, like one of the below lines. You can have as many Log lines as ## you want. ## ## We advise using "notice" in most cases, since anything more verbose ## may provide sensitive information to an attacker who obtains the logs. ## ## Send all messages of level 'notice' or higher to /var/log/tor/notices.log Log notice file /var/log/tor/notices.log ## Send every possible message to /var/log/tor/debug.log # Log debug file /var/log/tor/debug.log ## Use the system log instead of Tor's logfiles #Log notice syslog ## To send all messages to stderr: #Log debug stderr ## Uncomment this to start the process in the background... or use ## --runasdaemon 1 on the command line. This is ignored on Windows; ## see the FAQ entry if you want Tor to run as an NT service. #RunAsDaemon 1 ## The directory for keeping all the keys/etc. By default, we store ## things in $HOME/.tor on Unix, and in Application Data\tor on Windows. #DataDirectory /var/lib/tor ## The port on which Tor will listen for local connections from Tor ## controller applications, as documented in control-spec.txt. #ControlPort 9051 ## If you enable the controlport, be sure to enable one of these ## authentication methods, to prevent attackers from accessing it. #HashedControlPassword 16:872860B76453A77D60CA2BB8C1A7042072093276A3D701AD684053EC4C #CookieAuthentication 1 ############### This section is just for location-hidden services ### ## Once you have configured a hidden service, you can look at the ## contents of the file ".../hidden_service/hostname" for the address ## to tell people. ## ## HiddenServicePort x y:z says to redirect requests on port x to the ## address y:z. #HiddenServiceDir /var/lib/tor/hidden_service/ #HiddenServicePort 80 127.0.0.1:80 #HiddenServiceDir /var/lib/tor/other_hidden_service/ #HiddenServicePort 80 127.0.0.1:80 #HiddenServicePort 22 127.0.0.1:22 ################ This section is just for relays ##################### # ## See https://www.torproject.org/docs/tor-doc-relay for details. ## Required: what port to advertise for incoming Tor connections. ORPort 9001 ## If you want to listen on a port other than the one advertised in ## ORPort (e.g. to advertise 443 but bind to 9090), you can do it as ## follows. You'll need to do ipchains or other port forwarding ## yourself to make this work. #ORPort 443 NoListen #ORPort 127.0.0.1:9090 NoAdvertise ## The IP address or full DNS name for incoming connections to your ## relay. Leave commented out and Tor will guess. #Address noname.example.com ## If you have multiple network interfaces, you can specify one for ## outgoing traffic to use. # OutboundBindAddress 10.0.0.5 ## A handle for your relay, so people don't have to refer to it by key. Nickname NICKNAMEOFTHETORNODE ## Define these to limit how much relayed traffic you will allow. Your ## own traffic is still unthrottled. Note that RelayBandwidthRate must ## be at least 20 KB. ## Note that units for these config options are bytes per second, not bits ## per second, and that prefixes are binary prefixes, i.e. 2^10, 2^20, etc. RelayBandwidthRate 5000 KB # Throttle traffic to 100KB/s (800Kbps) RelayBandwidthBurst 7000 KB # But allow bursts up to 200KB/s (1600Kbps) ## Use these to restrict the maximum traffic per day, week, or month. ## Note that this threshold applies separately to sent and received bytes, ## not to their sum: setting "4 GB" may allow up to 8 GB total before ## hibernating. ## ## Set a maximum of 4 gigabytes each way per period. AccountingMax 400 GB ## Each period starts daily at midnight (AccountingMax is per day) AccountingStart day 00:00 ## Each period starts on the 3rd of the month at 15:00 (AccountingMax ## is per month) #AccountingStart month 3 15:00 ## Administrative contact information for this relay or bridge. This line ## can be used to contact you if your relay or bridge is misconfigured or ## something else goes wrong. Note that we archive and publish all ## descriptors containing these lines and that Google indexes them, so ## spammers might also collect them. You may want to obscure the fact that ## it's an email address and/or generate a new address for this purpose. #ContactInfo Random Person ## You might also include your PGP or GPG fingerprint if you have one: ContactInfo 0xFFFFFFFF user <privacy@yourdomain.com> ## Uncomment this to mirror directory information for others. Please do ## if you have enough bandwidth. #DirPort 9030 # what port to advertise for directory connections ## If you want to listen on a port other than the one advertised in ## DirPort (e.g. to advertise 80 but bind to 9091), you can do it as ## follows. below too. You'll need to do ipchains or other port ## forwarding yourself to make this work. #DirPort 80 NoListen #DirPort 127.0.0.1:9091 NoAdvertise ## Uncomment to return an arbitrary blob of html on your DirPort. Now you ## can explain what Tor is if anybody wonders why your IP address is ## contacting them. See contrib/tor-exit-notice.html in Tor's source ## distribution for a sample. #DirPortFrontPage /etc/tor/tor-exit-notice.html ## Uncomment this if you run more than one Tor relay, and add the identity ## key fingerprint of each Tor relay you control, even if they're on ## different networks. You declare it here so Tor clients can avoid ## using more than one of your relays in a single circuit. See ## https://www.torproject.org/docs/faq#MultipleRelays ## However, you should never include a bridge's fingerprint here, as it would ## break its concealability and potentionally reveal its IP/TCP address. #MyFamily $keyid,$keyid,... ## A comma-separated list of exit policies. They're considered first ## to last, and the first match wins. If you want to _replace_ ## the default exit policy, end this with either a reject *:* or an ## accept *:*. Otherwise, you're _augmenting_ (prepending to) the ## default exit policy. Leave commented to just use the default, which is ## described in the man page or at ## https://www.torproject.org/documentation.html ## ## Look at https://www.torproject.org/faq-abuse.html#TypicalAbuses ## for issues you might encounter if you use the default exit policy. ## ## If certain IPs and ports are blocked externally, e.g. by your firewall, ## you should update your exit policy to reflect this -- otherwise Tor ## users will be told that those destinations are down. ## ## For security, by default Tor rejects connections to private (local) ## networks, including to your public IP address. See the man page entry ## for ExitPolicyRejectPrivate if you want to allow "exit enclaving". ## #ExitPolicy accept *:6660-6667,reject *:* # allow irc ports but no more #ExitPolicy accept *:119 # accept nntp as well as default exit policy ExitPolicy reject *:* # no exits allowed ## Bridge relays (or "bridges") are Tor relays that aren't listed in the ## main directory. Since there is no complete public list of them, even an ## ISP that filters connections to all the known Tor relays probably ## won't be able to block all the bridges. Also, websites won't treat you ## differently because they won't know you're running Tor. If you can ## be a real relay, please do; but if not, be a bridge! BridgeRelay 1 ## By default, Tor will advertise your bridge to users through various ## mechanisms like https://bridges.torproject.org/. If you want to run ## a private bridge, for example because you'll give out your bridge ## address manually to your friends, uncomment this line: #PublishServerDescriptor 0
viel Spass!
have fun!
Веселитесь!
Розважатися!
¡Que te diviertas!
Amusez-vous!
玩得愉快!
Links:
search the user’s tor node here: (if BridgeRelay 1) https://metrics.torproject.org/rs.html
it has nice graph that shows bandwidth usage etc.
https://tb-manual.torproject.org/bridges/
https://mastodon.social/@torproject
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!