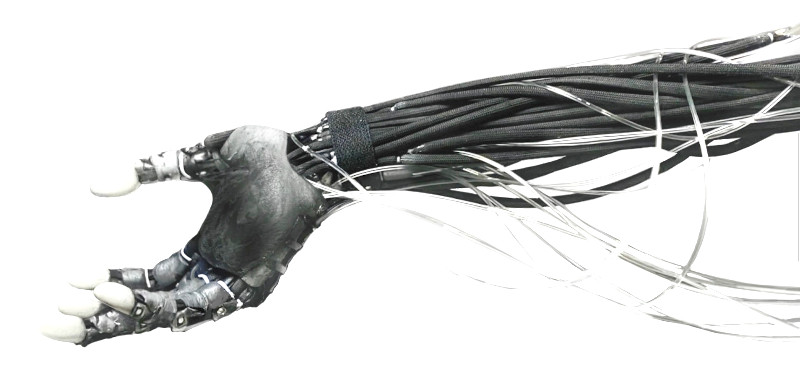
scarzy shit X-D https://www.youtube.com/watch?v=ivLbzvUjKdM https://www.youtube.com/@CloneRobotics/videos src of src https://www.clonerobotics.com/ based in Wrocław, Poland?
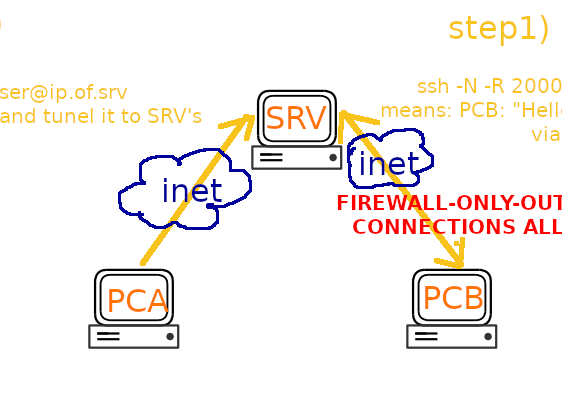
scroll down to: “how to access user-dev-admin’s home network boxes from anywhere via reverse-ssh-tunnel! :D” ssh tunnel remote deviceD’s port access a device’s port that is only available via a specific machine 😀 or in other words: ssh-tunnel port of […]
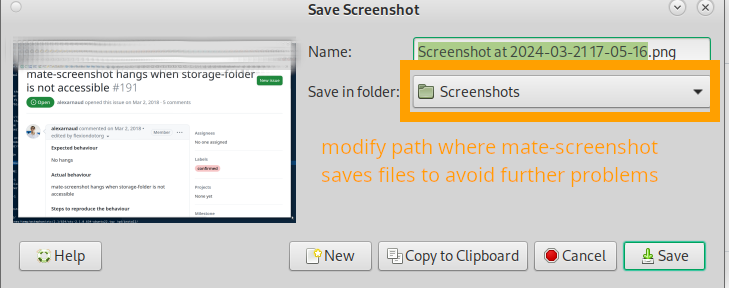
taking screenshots is important 😀 it is very useful and mate-screenshot is an easy to use screenshot tool that can be started by the simple press of the ancient otherwise useless “print” button (found on almost every keyboard) if mate-screenshot […]
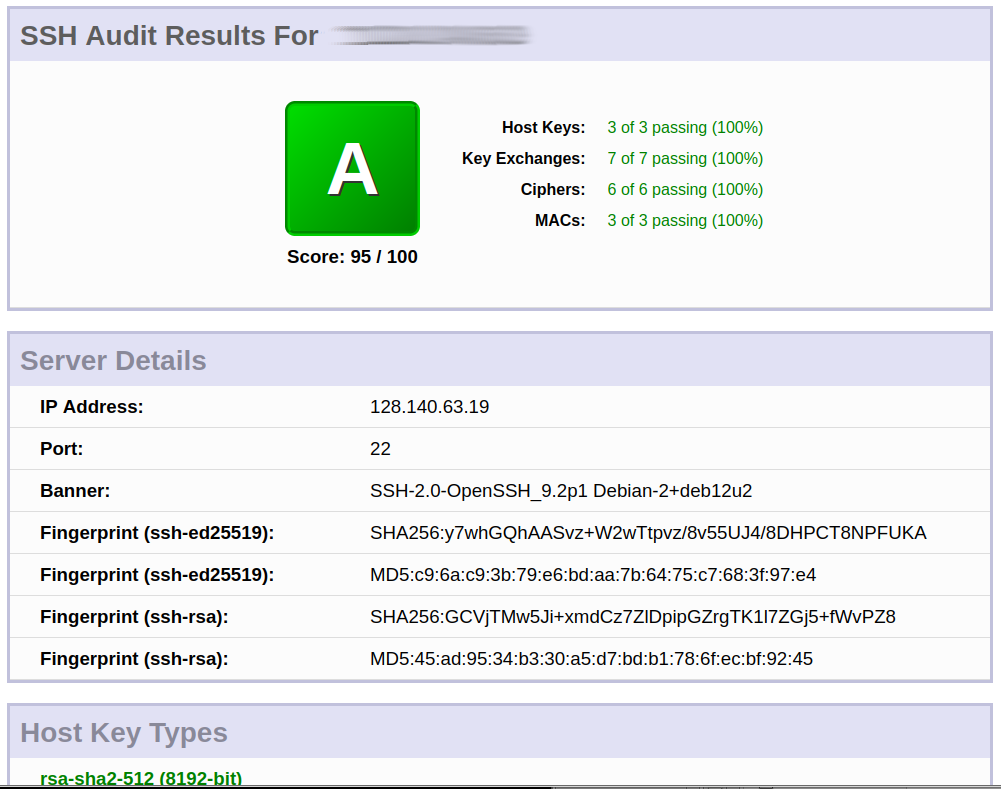
update: 2024-06: ed25519 is currently “the way to go” ssh can be regarded as “critical core infrastructure” time spend on it’s security is time well spend time + money well invested: https://www.openssh.com https://github.com/openssh current manpage: ssh.man.txt WARNING: this howto guide […]
Just as php python is a widely used easy to read and write on-the-fly interpreted language. performance? performance in the sense of data throughput or amount of prime numbers per second but it is also: how long will a user […]
variant1: the most minimalist approach works but imho it is very primitive 🙂 (but it works) variant2: a wee bit better let’s go hostnamectl; # tested with Virtualization: kvm Operating System: Ubuntu 22.04.4 LTS Kernel: Linux 5.15.0-94-generic Architecture: x86-64 # […]
it works now! 😀 THE PENGUIN CAN NOW MEASSURE THE TEMPERATURE! thanks ALL INVOLVED 😀 TIP: it actually has 2x temp sensors 1x meassures inside usb stick 1x meassures with the metal-probe at the end of the cable WARNING! […]
most recent version 2024-03 is https://www.python.org/downloads/ python 3.12 First released: 2023-10-02 End of support: 2028-10 Release schedule: PEP 693 python for automation: So for performance critical tasks python is actual just the “controller” that then calls C or or C++ or […]
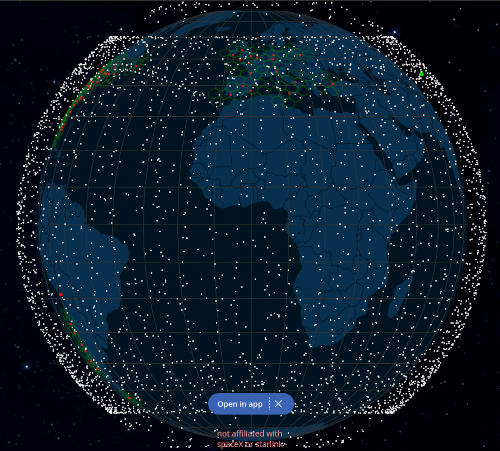
Starlink is a cost effective internet-via-satellite provider run by SpaceX at 2024-01 currently (2014-01) counts over x > 2 mio customers SpaceX plans to put 12.000 to 42.000 satellites into Low Earth Orbit (LEO). currently (2024-01) 5289 satellites (Wiki) in […]
scientists predict human leven AI by 2047 so DON’T HOLD THE BREATH What is GPT4All-J?: An Apache-2 Licensed Assistant-Style Chatbot What is Mistral Orca? https://huggingface.co/ “The AI community building the future.” “The platform where the machine learning community collaborates on […]
“wlx123 Interface doesn’t support scanning : Device or resource busy” this error occurs during manual terminal bash based scanning of wifi wlan networks: hostnamectl; # tested on Operating System: Debian GNU/Linux 12 (bookworm) Kernel: Linux 6.1.0-13-686-pae Architecture: x86 su – […]
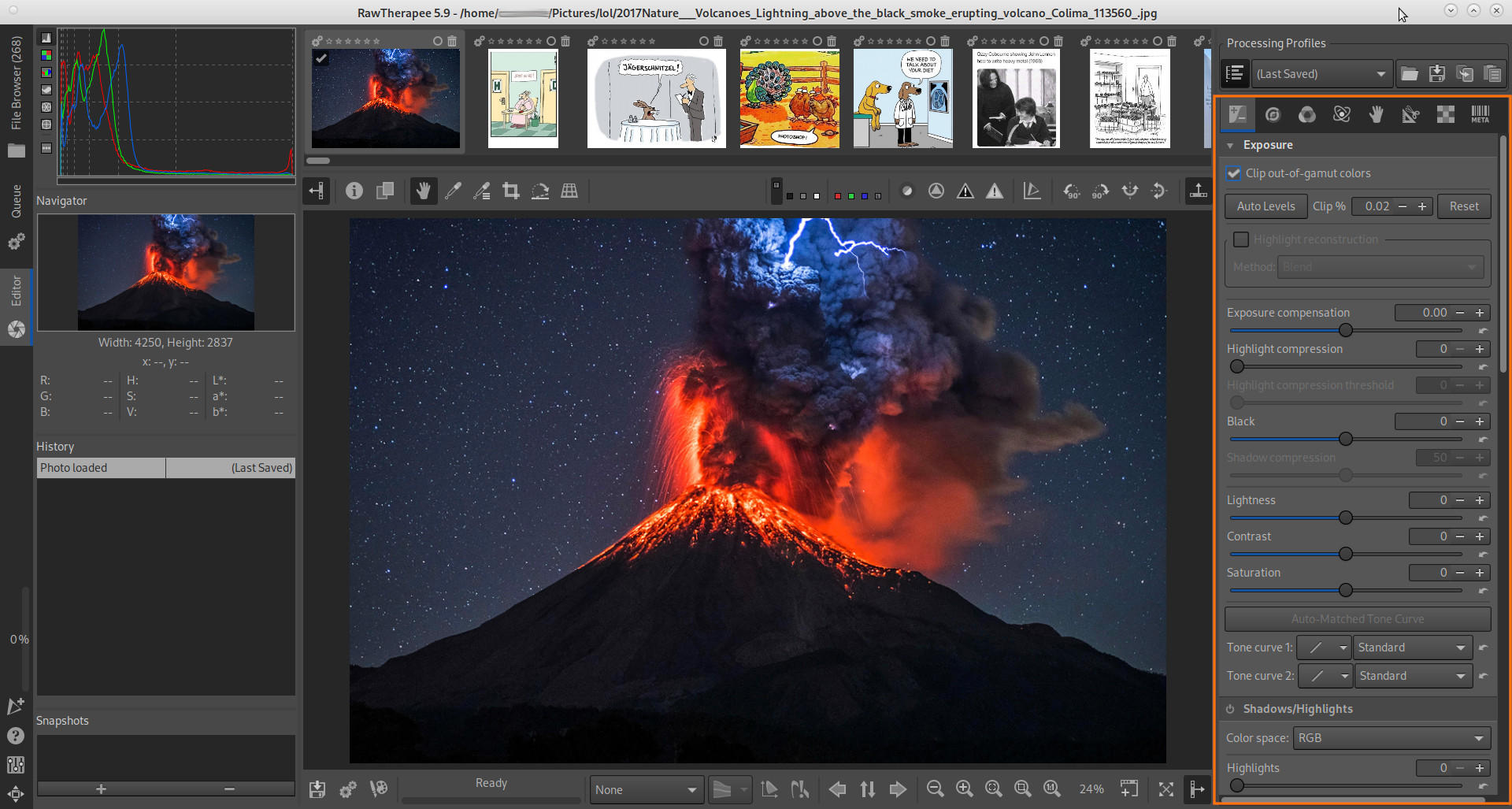
rawtherapee.com is an awesome corss OS photo-picture-post-processing program (THANKS ALL INVOLVED! :D) “raw image converter and digital photo processor” “RawTherapee is an advanced program for developing raw photos and for processing non-raw photos. It is non-destructive, makes use of OpenMP, supports […]
how to fix sim card not working: PLEASE WITH SIM CARD INSERTED BOOT STOCK ROM AT LEAST ONCE! while still in stock rom insert sim card and TEST & CONFIRM that CALLING and INTERNET (LTE) are working (test if stock […]
once upon a time… found a strange looking cable.. Double micro audio jack? WHAT ON EARTH IS THAT? It is a serial-to-usb programming radio cable for RETEVIS handheld “walkie talkie” radios, that allows to set different modes of the radio […]
always say something positive first: then the critique: follow the excellent guide: https://getcomposer.org/download/ mkdir /var/www/html/composer cd /var/www/html/composer php -r “copy(‘https://getcomposer.org/installer’, ‘composer-setup.php’);” php -r “if (hash_file(‘sha384’, ‘composer-setup.php’) === ‘THISWILLHAVECHANGEDBYNOW’) { echo ‘Installer verified’; } else { echo ‘Installer corrupt’; unlink(‘composer-setup.php’); } […]
Musk grabbed deeply into the Toilet, by wasting Billions on it’s twitter buy, he could have build 100x Twitters from scratch, with this amount of money. Understanding Elon Musk – (the day Elon almost destroyed Tesla by accident) – good […]
https://doodlejumporiginal.com/ there is also the version for xbox kinect, where the user actually is steering the doodle with user’s body (cool, but that SHOULD also be possible with a smart phone’s front cam right?) game ideas: while doodle jump […]
This is actually VERY usefull to find files that waste disk space. lsb_release -a; # tested on Distributor ID: Debian Description: Debian GNU/Linux 12 (bookworm) the solution: czkawka_cli install rust like this (no need to install rust as root) install […]
Year 2000 has passed, no flying cars yet but at least more faster (SSD and NVMe) disk space 😀 All sorts of resources also digital resources and bandwidth, RAM and DiskSpace space are STILL precious and should be treated as […]
#wtheseriousf? It used to “just work” “seamlessly”, now read the “HORRORS” of reinstalling a only 4 year old iMac (2019) that Apple just does not care about anymore. (just reinstalled LATEST 2023 Debian 12 on a 17 year old lenovo […]
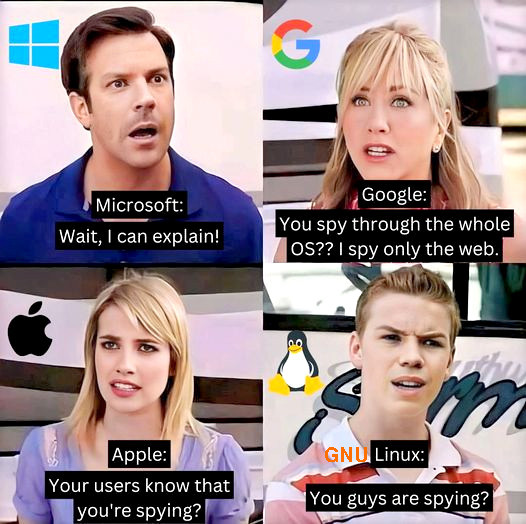
why are not more companies, schools, governments, banks using GNU Linux? Some might claim because of lack of standardization. but imho that is not true. from a biologists point of view biodiversity is actually a very good thing, as it […]
most important: use the WatchPower version that comes on CD with the solar charge controller, as newer or older versions might not be working (incompatible, changes in protocol etc) it might wise to use a galvanic isolator (even the shielding […]
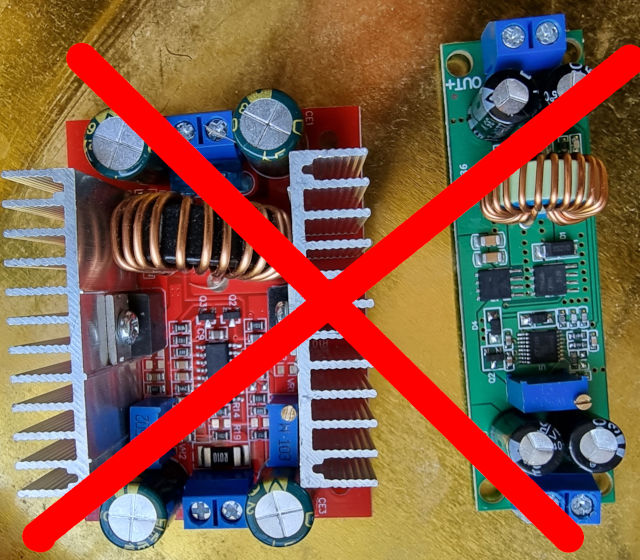
those did not: no matter the position of the poti, the output current did not change at all X-D #wtf is going on? (power source was a “12V” solar panel delivering 20V which is in the allowed input range of […]
“Founded in 2016, the annual fair in Paris is one of Europe’s top-tier technology events, this year attracting 2,400 start-ups – double the number it hosted in its first year – and more than 2,000 investors looking to fund the […]
update: 2024 ok Apple won this round (almost) Airpods Pro (better buy new = small batteries that wear out fast 🙁 can be used with any Graphene powered Android device just fine (stop song (click on button once) works, next song […]
The Flashplayer was a (unfortunately closed source, why not release the source NOW? Adobe? 😀) runtime binary to enhance multimedial capabilites of the browser THE FIRST possibility to stream videos inside the browser (youtube once used flash, now they shifted […]
https://webmasters-fernakademie.de Wie so oft in Deutschland: Idee gut, Umsetzung mangelhaft. im Prinzip ist 100% Remote Online Fortbildung eine gute Idee, praktisch wird man mit Text-Wüsten eines sich tot-stellenden Dozenten alleine gelassen, mit welchem man nur über eine veraltete wenig inutitiven […]
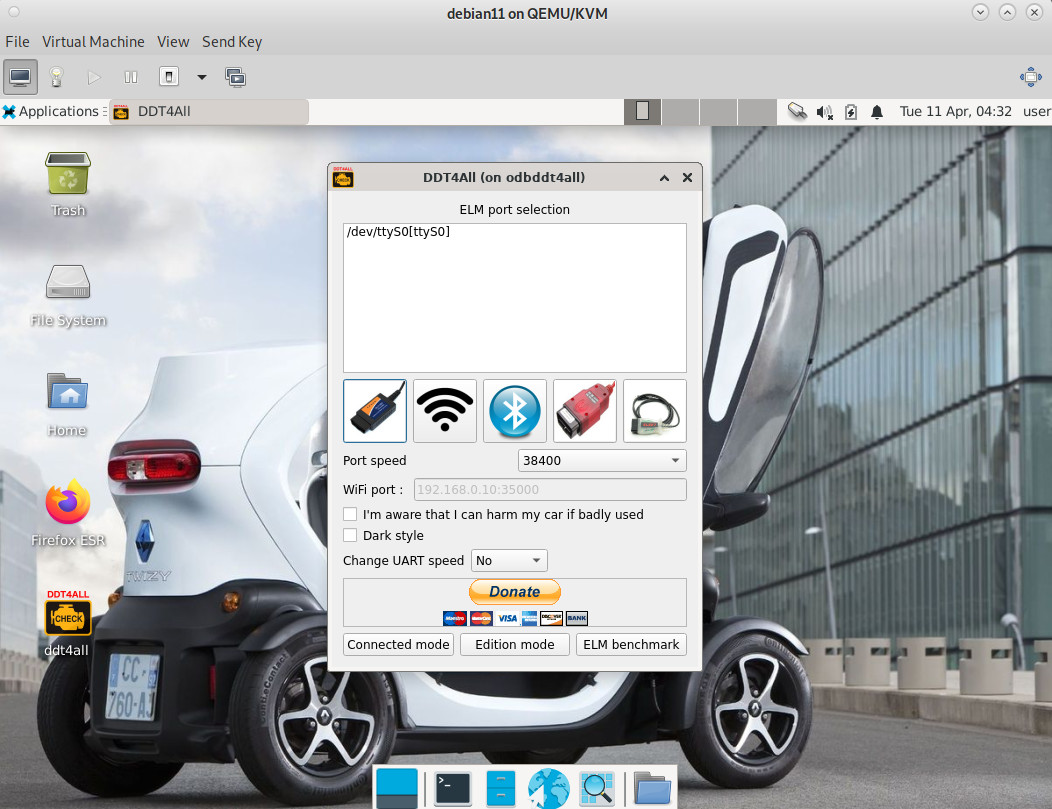
Warning!: many things can be set with DDT4ALL, theoretically also nasty things that might damage the vehicle. Warning send! it is said to work with this adapter: (at least for the ZOE the wirering needs to be modified?) (why so […]
src: https://twitter.com/elonmusk/status/1641880448061120513 btw: StarShip fully-stacked maiden flight is said to be this week. So the good part of the Science-Fiction now becomes more science als less fiction.