Musk grabbed deeply into the Toilet, by wasting Billions on it’s twitter buy, he could have build 100x Twitters from scratch, with this amount of money. Understanding Elon Musk – (the day Elon almost destroyed Tesla by accident) – good […]
“WASHINGTON — Lockheed Martin and Verizon are experimenting with 5G-enabled drones and intelligence, surveillance and reconnaissance payloads in an effort that could ultimately enhance U.S. military command and control and in-the-field targeting abilities. The two companies on Sept. 28 said […]
“the internet”, “wifi”, all “electronic communication via air and wires” As with all new technologies, Einstein was hopeful, that this new technology will be used for good to bring peace by better understanding between nations and individuals alike. Of course […]
0) for security: keep all internet connected devices as up to date as possible! “Freifunk updates its router firmware and closes a critical security vulnerability that could allow attackers to install their own firmware on the devices” (src: heise.de) Also […]
criminals abusing tor for malicous behavior should be blocked, right? “50% of the attacks are leveraging the Tor anonymity service to mask their true origins” https://thehackernews.com/2021/12/new-local-attack-vector-expands-attack.html this could destroy the “honest” part of the network that truly exists, because it […]
the positive vision (always start with something positive) if big data about every keystroke every step we make (the police: every step you make) algorithms determine how mankind will live and thus: technology is “neutral” until it is used for […]
in short: humans per default, without an education might just be “better” apes. Some parts of mankind behave very primitive and clearly show no signs of higher intelligence or education. The troubles start, when the tools become more and more […]
Yes! What RSS does NOT stand for “Rashtriya Swayamsevak Sangh” , “Nathuram Godse, who assassinated Gandhi, on January 30, 1948, was a member of the Rashtriya Swayamsevak Sangh, or R.S.S., a violent right-wing organization that promotes Hindu supremacy.” (src: HolyCow!) […]
long story… good alternative? https://minidvblinux.de/ having had various frustrating experiences with the topic: TV + PC (even tried a cheap DreamBox 520 HD from eBay… which are probably good devices, but this one turned out to be faulty/unstable) now… in […]
I once asked Rupert Murdoch why he was so opposed to the European Union. ‘That’s easy,’ he replied. ‘When I go into Downing Street they do what I say; when I go to Brussels they take no notice.’ https://www.indy100.com/people/this-terrifying-rupert-murdoch-quote-is-possibly-the-best-reason-to-stay-in-the-eu-yet-7291931 src […]
why are those data leaks problematic? because scammers and spammers will use this data to even better scam (social engineer) the affected users that is why it is essential to give those platforms (if the user needs them) as little […]
SecurityLab, [22.12.20 10:00] Google has explained the reasons for the massive failure of its services that took place last week. Recall that on December 14 of this year, users around the world for 47 minutes could not access Gmail, YouTube […]
DNS servers are the “yellow pages” “phone book” of the internet. whoever is running DNS servers get’s to know all queries send (what client is requesting and probably connecting to what address… basically: what websites the user have visited, this […]
Overview Recent 360Netlab unknown threat detection system to capture to a group of unknown malicious families of the sample, which a number of samples supported CPU architectures are x86(32/64), ARM(32/64), MIPS(MIPS32/MIPS-III) as well as PPC, after our analysis, which is […]
contains advertisement. to be honest, it is hard to keep up the speed at which cyber incidents are reported. here is the latest take on “Russian IT Sec Updates”. have phun! SecurityLab, [28.09.20 08:20] Last month, TikTok developers rolled […]
SecurityLab, [14.07.20 15:35] The Electronic Frontier Foundation (EFF) has unveiled a new database demonstrating how and where us law enforcement agencies use tracking technologies. A map of the use of tracking technologies in the United States is presented (https://www.securitylab.ru/news/510018.php) SecurityLab, […]
All SmartPhones are spies! that’s why Merkel keeps the Nokia from 1995 (even if that device is spied on as well, because it can not end2end encrypt sms or phone calls (*FAIL*! X-D)) Putin does not have a mobile phone […]
The Age of Surveillance Capitalism: “be careful what you reveal to your friend” (the internet) https://irlpodcast.org/season4/episode5/ “where it has gone from defending America to controlling it” data google tries to collect from users: (it is probably only the tip of […]
The Great A.I. Awakening: A Conversation with Eric Schmidt Feb 23, 2017 as user might have noticed, the battle Amazon vs Microsoft who will get the $10Billion DoD cloud computing contract is still hot. And maybe the contract is split. […]
this age of mass surveillance… … who is observing “the observers”? guess with it-security and internet-security (internet = roads, cars = computers that users use every day) it is like with real-life-security – there is no 100% security. all users […]
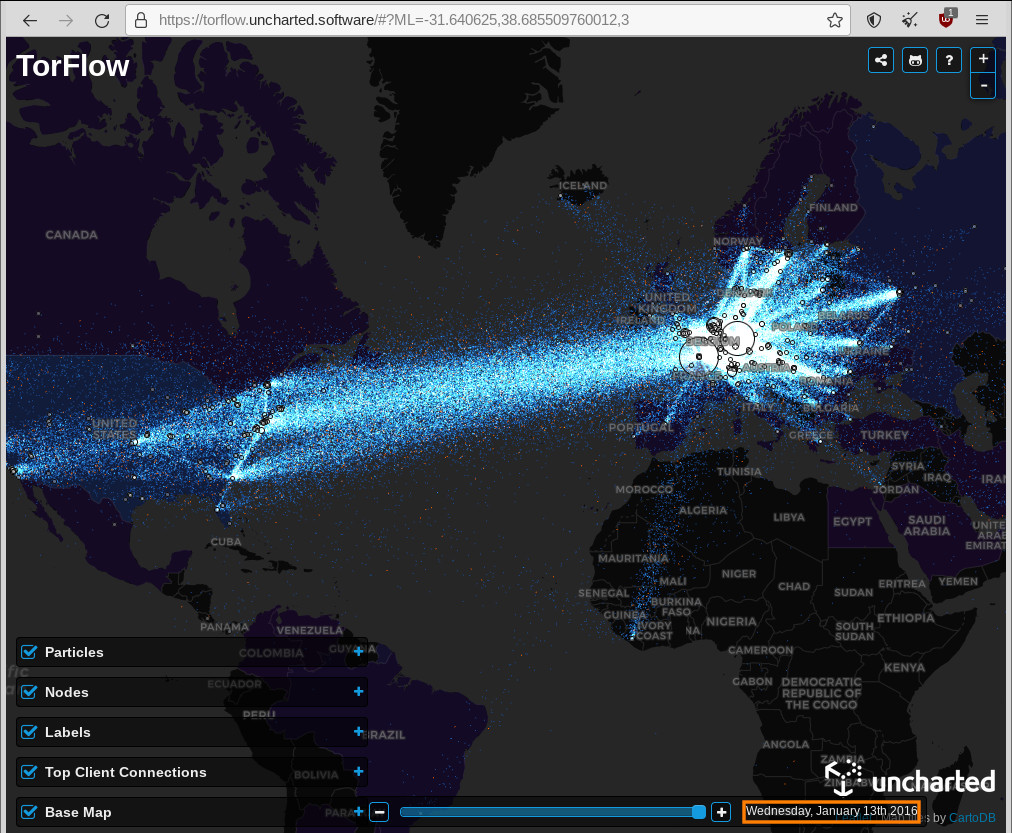
Tor is easier to use than ever superb usability! Tor is now super easy to use! (thanks all involved!) just get the tor bundle – it is tor bundled with firefox https://www.torproject.org/download/ Tor visualized: most users are legit: but criminals […]
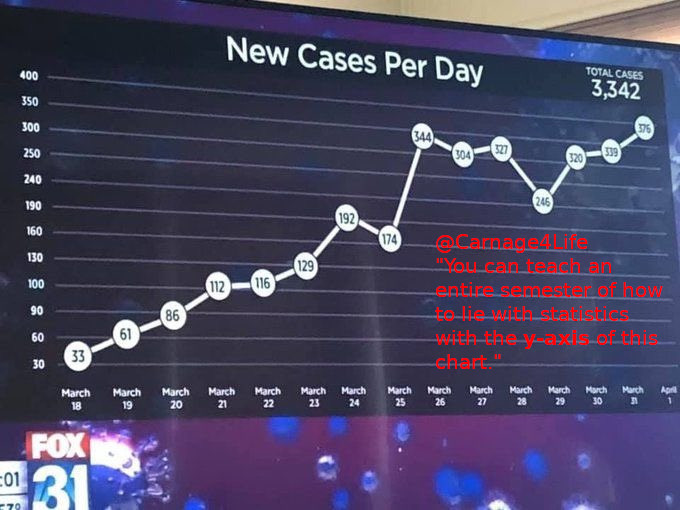
this is why high quality journalism and education are sooooo important: trust is so important & journalism should be about truth and trust context: media outlets that use numbers out of context (do those numbers apply to the US, or […]
As with all hot debated topics: Linus Torvald’s “show me the source” in this case, the source of one’s informations (always give the source!) is IMPORTANT for the information’s credibility. It is absolutely vital in science to give all sources […]
now WITH SPICY COMMENTS X-D SecurityLab, [22.12.19 12:40] A Twitter user using the alias 08Tc3wBB created tfp0-an exploit that allows you to jailbreak the latest iPhone models with IOS 13.3. The functionality of the exploit has already been confirmed by […]
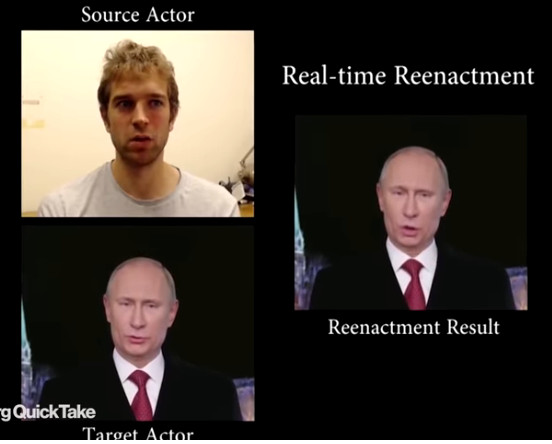
“We need to be more vigilant with what we trust from the internet” – BigBrother will use this against you! … even if Putin, Trump and Obama will die some day… his digital deep fake copy will feed you lies […]
update: “The sale was met with significant opposition since it involved the transfer of what is viewed as a public asset to a private equity investment firm.[45] In late January 2020, ICANN halted its final approval of the sale after […]
i really like virtualbox and i think it has great potential, what i do not like SOOO much is the CIA’s involvement with Oracle. “Larry Ellison Is A Billionaire Today Thanks To The CIA” (src) VirtualBox is mostly GPL 2.0 […]
new Russian IT Security updates: thanks to https://www.securitylab.ru/ and https://translate.yandex.com/ SecurityLab, [06.11.19 16:12] The Libarchive compression library, which is included by default in Debian, Ubuntu, Gentoo, Arch Linux, FreeBSD, and NetBSD distributions, contains a vulnerability that allows an attacker […]
Another reason to NOT trust EVERY human task to machines… unless one wants to get killed by a robot dressed up as dinosaur. “great” X-D “Japanese travel agent H. I. S. Group ignored warnings about a vulnerability in its Tapia […]
Update: 2021-02 “A statement from the German Federal Criminal Police Office about their participation in Operation Ladybird said prosecutors seized 17 servers in Germany that acted as Emotet controllers.” and many bars of gold and cash were seized in Ukraine… […]