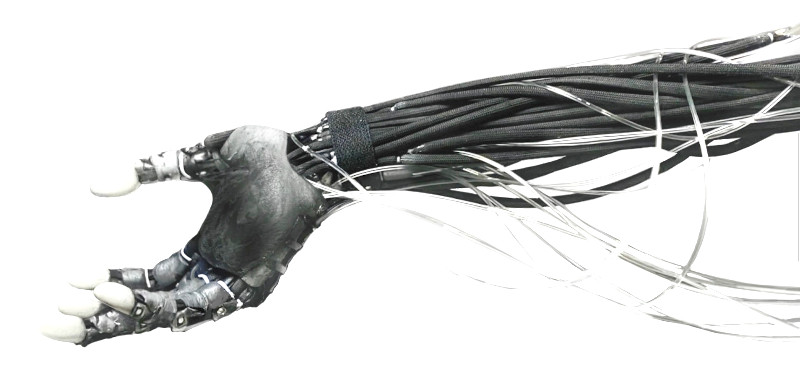
scarzy shit X-D https://www.youtube.com/watch?v=ivLbzvUjKdM https://www.youtube.com/@CloneRobotics/videos src of src https://www.clonerobotics.com/ based in Wrocław, Poland?
this blog does not get tired of testing Android ROMS that enhance privacy 🙂 (actually it would be nice, if software support for those devices is at least 10 years X-D because it is a constant tiresome race) Yes it […]
it works now! 😀 THE PENGUIN CAN NOW MEASSURE THE TEMPERATURE! thanks ALL INVOLVED 😀 TIP: it actually has 2x temp sensors 1x meassures inside usb stick 1x meassures with the metal-probe at the end of the cable WARNING! […]
want to see what’s going on in the Open Source part of Android OS? e-OS is available for many many (but not all) devices here is a detailed review of the ROM in terms of privacy. IT IS AN EXCELLENT […]
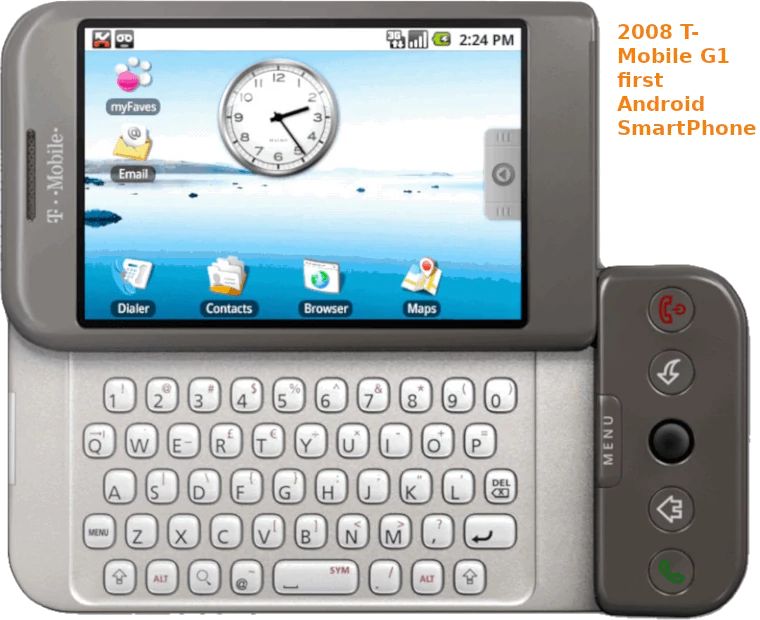
so every android user is in a hurry to update update update to Google’s latest firmware because of it’s security issues really would like to see a smart phone that can run almost unchanged GNU Linux kernel 😀 (yes would […]
https://source.android.com/docs/security/bulletin/2023-12-01?hl=en <- unfortunately does not export an RSS feed so a user needs to write a converter-aggregator https://www.heise.de/news/Patchday-Android-Android-11-12-13-und-14-fuer-Schadcode-Attacken-anfaellig-9548839.html as seen in https://www.heise.de/security/rss/alert-news-atom.xml for the news junkies – how to read news in the 21st century (APPs & RSS FEEDS) – […]
how to fix sim card not working: PLEASE WITH SIM CARD INSERTED BOOT STOCK ROM AT LEAST ONCE! while still in stock rom insert sim card and TEST & CONFIRM that CALLING and INTERNET (LTE) are working (test if stock […]
Let me be frank. Once upon the time, was a Windows user. Then was happy to have to use OSX for a transition to GNU Linux. But once on GNU Linux (Debian) do not miss neither Windows nor OSX at […]
No matter if docker repository called “hub”, Google’s App Store “PlayStore” or Apple’s App Store they are ALL facing the same security problems: https://www.bleepingcomputer.com/news/security/google-explains-how-android-malware-slips-onto-google-play-store/ plus: https://www.bleepingcomputer.com/news/security/thousands-of-android-apks-use-compression-trick-to-thwart-analysis/ what if… a malicious actor uploads an App or docker container that is totaly […]
“Von der Leyen under pressure: The head of the EU Commission refuses to release text messages about the expensive vaccine deal with Pfizer. She is accused of lack of transparency.” (src) (here is the full New York Times article on […]
both are centralized Messengers meaning: the user is in control of the device + software (to the extend that the user can understand the src) Android-Client “the client” 100% Open Source (Java 70.8% Kotlin 29.1%) iOS-Client 100% Open Source (Swift […]
“know in some countries they believe Telegram is safe. I will show you how safe it is,” he said, before showing a screen in which he appeared to scroll through the Telegram contacts of one Kenyan strategist https://www.theguardian.com/world/2023/feb/15/revealed-disinformation-team-jorge-claim-meddling-elections-tal-hanan
mekotronicsplz note: “the-best-technology-does-nothing-without-a-good-human-culture” Yes! Read that correctly, modern SmartPhones are actually full blown computers, so why not use them as such? Now that they have enough (RISC) based computational power that they can replace Desktop and Notebooks, problem: they can […]
check this out: When will Intel & AMD release their first ARM based SoC? “Intel is working on a new SoC (system on a chip) that will compete with the ARM-based designs that have dominated the mobile market for several […]
the risks of all digital (no cash) payment systems & amok AI: “This happens quite often with customers of the Cashgroup banks (@DeutscheBank / @Postbank / @Commerzbank / @Comdirect) as soon as their algorithms hit your account is directly without […]
can smart phone cameras compete with the “big” ones with big lenses? please support this Open Source, Tech & Privacy dedicated blog 😀 by buying from Amazon Affiliated links: Get the amazing Samsung S21 Ultra 5G with 10x times optical […]
can tablets replace notebooks? no. imho most tablets are just “big mobile phones” (no matter ipad or android based) or very slow downsized notebooks (windows 10 based), but having a full speed of AMD or Intel CPUs at 16GB of […]
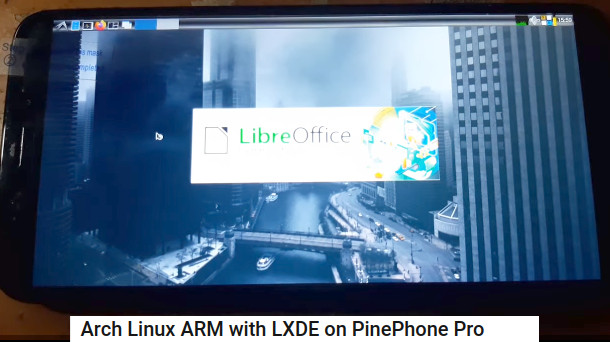
update: 2022: ah oh: Pine community in Pain? https://blog.brixit.nl/why-i-left-pine64/ “In February 2021, PINE64 announced the end of the community editions. At this moment, PINE64’s focus shifted from supporting a diverse ecosystem of distributions and software projects around the PinePhone to […]
in previous rant, it was about “trying to return a product to China and get money back? well…. does not work in 99.9% of all cases” https://dwaves.de/2021/12/13/ebay-artikel-versand-aus-china-ruckgabe-keine-chance-teuer-unzuverlassig/ this is outright fraudulent allowance of eBay to sell more fake and scam […]
Motorola, Apple, Samsung, and now even Fairphone 4: NO 3.5mm headphone jack!!! For the audio junkies among us, this is a no go. Was so looking forward to the Fairphone, but will probably use a phone with audio jack as […]
simplicity is key: what is definately great and a big plus is the “openness” of the Android (a by Google heavily modified GNU-Linux) environment. no need for extra software (itunes) to access the device a usb-c-cable will do connect it […]
update: 2022-12 wow 3 and 4nm is very very small “TSMC recently announced that it is upping its U.S. investment in Arizona to US$40 billion (NT$1.23 trillion) and will manufacture 4nm and 3nm chips there. The 4nm chips are expected […]
the user has to know, that Mozilla is very much (still) dependant on Google’s money. User Agent: Mozilla/5.0 (X11; Linux x86_64; rv:92.0) Gecko/20100101 Firefox/92.0 Hello Dear Mozilla / Dear Firefox management & DevTeam, using this rss app to stay up […]
prologue: (u can skip it) SmartPhones try to spy and collect data, that why SmartPhone games and weather-apps are usually free. Because the user pays with user data. What even fuels the paranoia are stories like these: in 2011 Rothschild […]
in short: humans per default, without an education might just be “better” apes. Some parts of mankind behave very primitive and clearly show no signs of higher intelligence or education. The troubles start, when the tools become more and more […]
short story: phase it out So it finally happened, Oracle wants to cash in on it’s $7.4 Billion investment it made in 2009. The non-Open-Source non-GPL non-Free-Software-coffee has officially gone sour. One can just pray, that this will be a […]
Yes! What RSS does NOT stand for “Rashtriya Swayamsevak Sangh” , “Nathuram Godse, who assassinated Gandhi, on January 30, 1948, was a member of the Rashtriya Swayamsevak Sangh, or R.S.S., a violent right-wing organization that promotes Hindu supremacy.” (src: HolyCow!) […]
Apple wants to become the new Google: BigBadBoldBigDataMothership why more developers should chose GPL to publish programs: as a once proud Apple user… (yes GNU Linux Debian 10 actually runs pretty well on the Intel-Macbook-Pros) yes they are beautiful spies… […]
SecurityLab, [12.01.21 15:23] The developer of the Salaat First (Prayer Times) app, which reminds Muslims when to pray, recorded and sold detailed information about their location to a data broker without the users ‘ knowledge, who in turn sold the […]
BeyondCorp Google’s new Approach to Security – we need to know EVERYTHING about the user – in order to trust the user – The Age of Surveillance Capitalism one tweet against Google… and the user’s Twitter account could look like… […]