in short: humans per default, without an education might just be “better” apes. Some parts of mankind behave very primitive and clearly show no signs of higher intelligence or education. The troubles start, when the tools become more and more […]
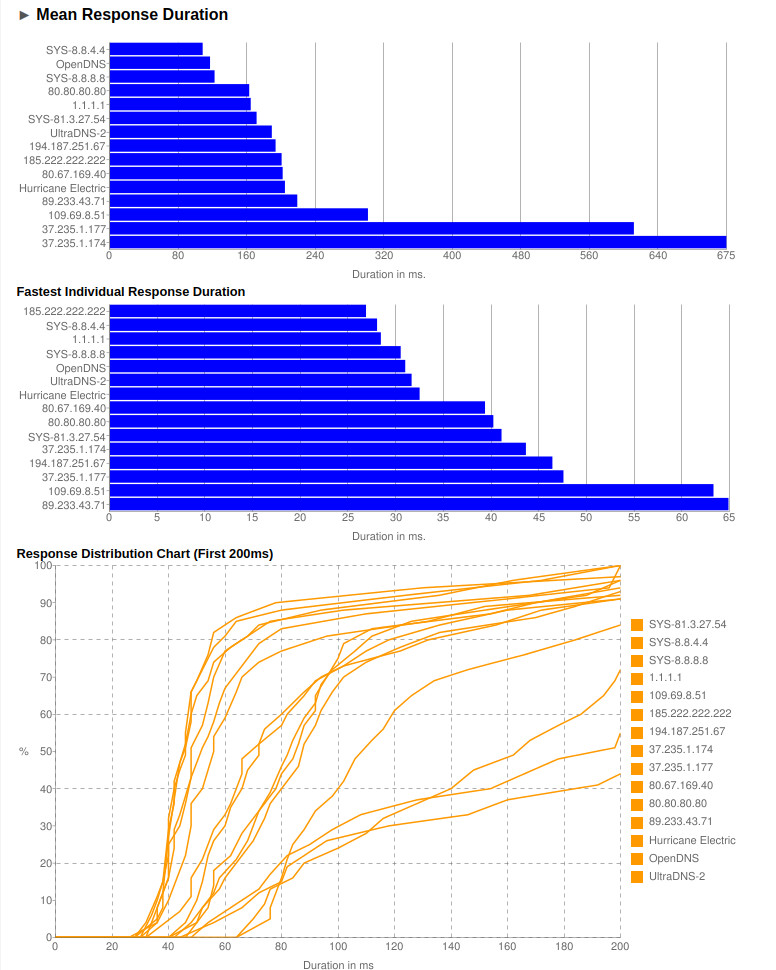
every user want’s a fast & responsive internet. BIND and DNS – the Phonebook of the internet – Berkeley Internet Name Domain – how to benchmark dns servers (find fastest) – LibreDNS There is nothing more anoying than slow loading […]
harddisk encryption is important from critical data to get physically stolen (can’t do much about data that get’s stolen while DEcrypted) (except: to not have any physical network connection while the data is in DEcrypted state?) hostnamectl; # tested on […]
Yes! What RSS does NOT stand for “Rashtriya Swayamsevak Sangh” , “Nathuram Godse, who assassinated Gandhi, on January 30, 1948, was a member of the Rashtriya Swayamsevak Sangh, or R.S.S., a violent right-wing organization that promotes Hindu supremacy.” (src: HolyCow!) […]
Apple wants to become the new Google: BigBadBoldBigDataMothership why more developers should chose GPL to publish programs: as a once proud Apple user… (yes GNU Linux Debian 10 actually runs pretty well on the Intel-Macbook-Pros) yes they are beautiful spies… […]
why are those data leaks problematic? because scammers and spammers will use this data to even better scam (social engineer) the affected users that is why it is essential to give those platforms (if the user needs them) as little […]
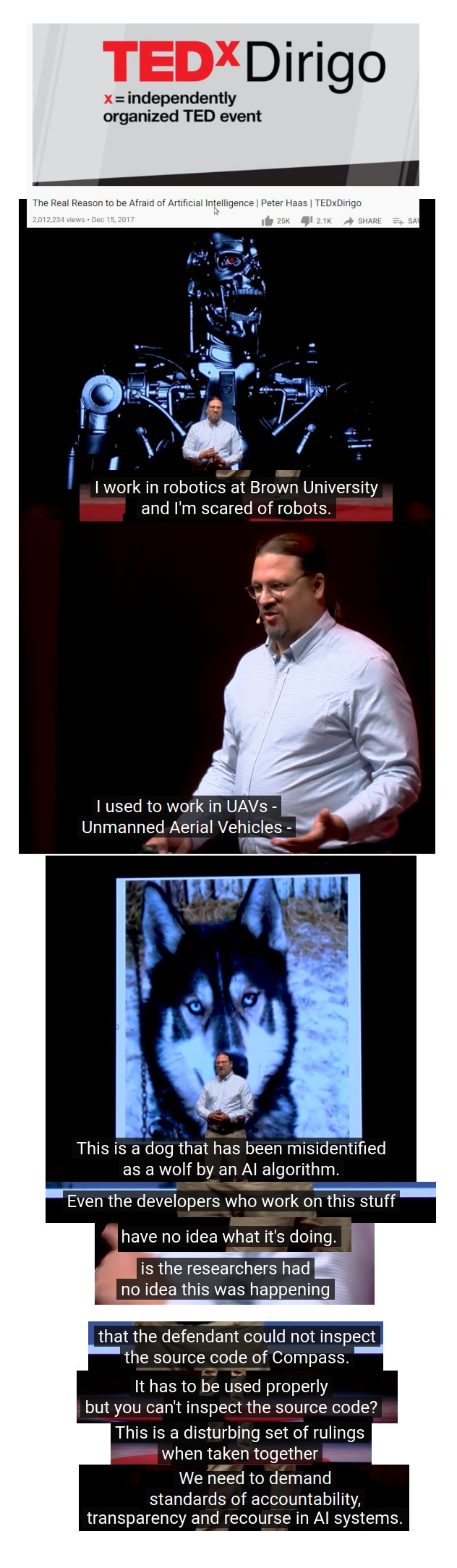
computers are no way perfect: the rise of the machines: who is scared of killer robots? who is scared of doctors, judges and police blindly trusting in AI and computer output? “we are driving in (heavy) rain right now with […]
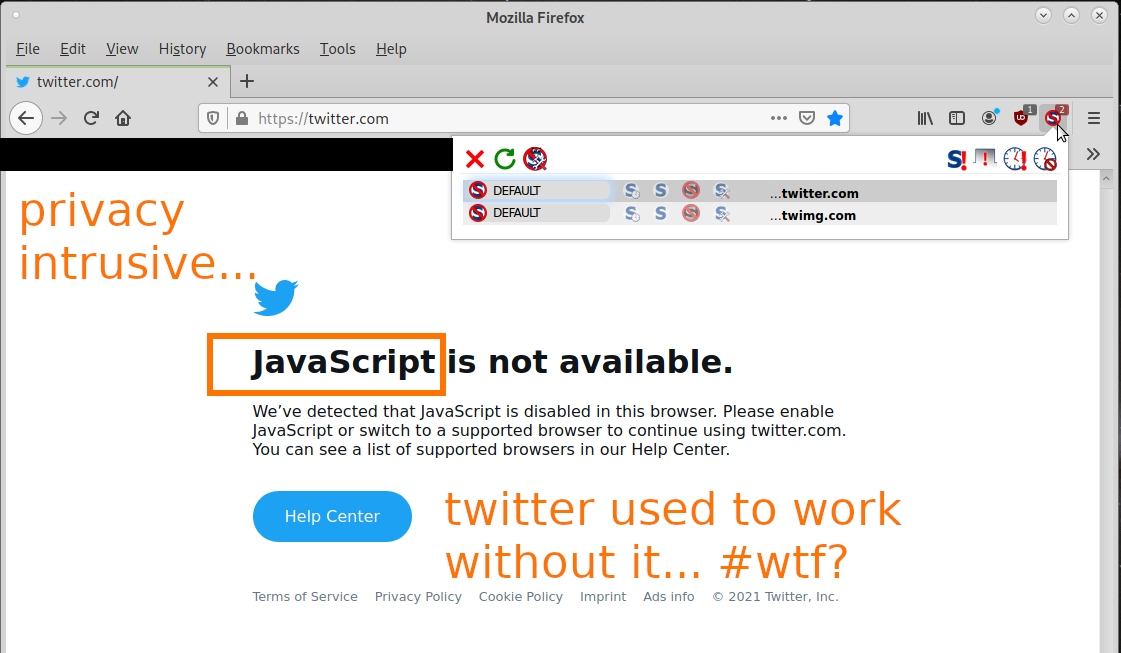
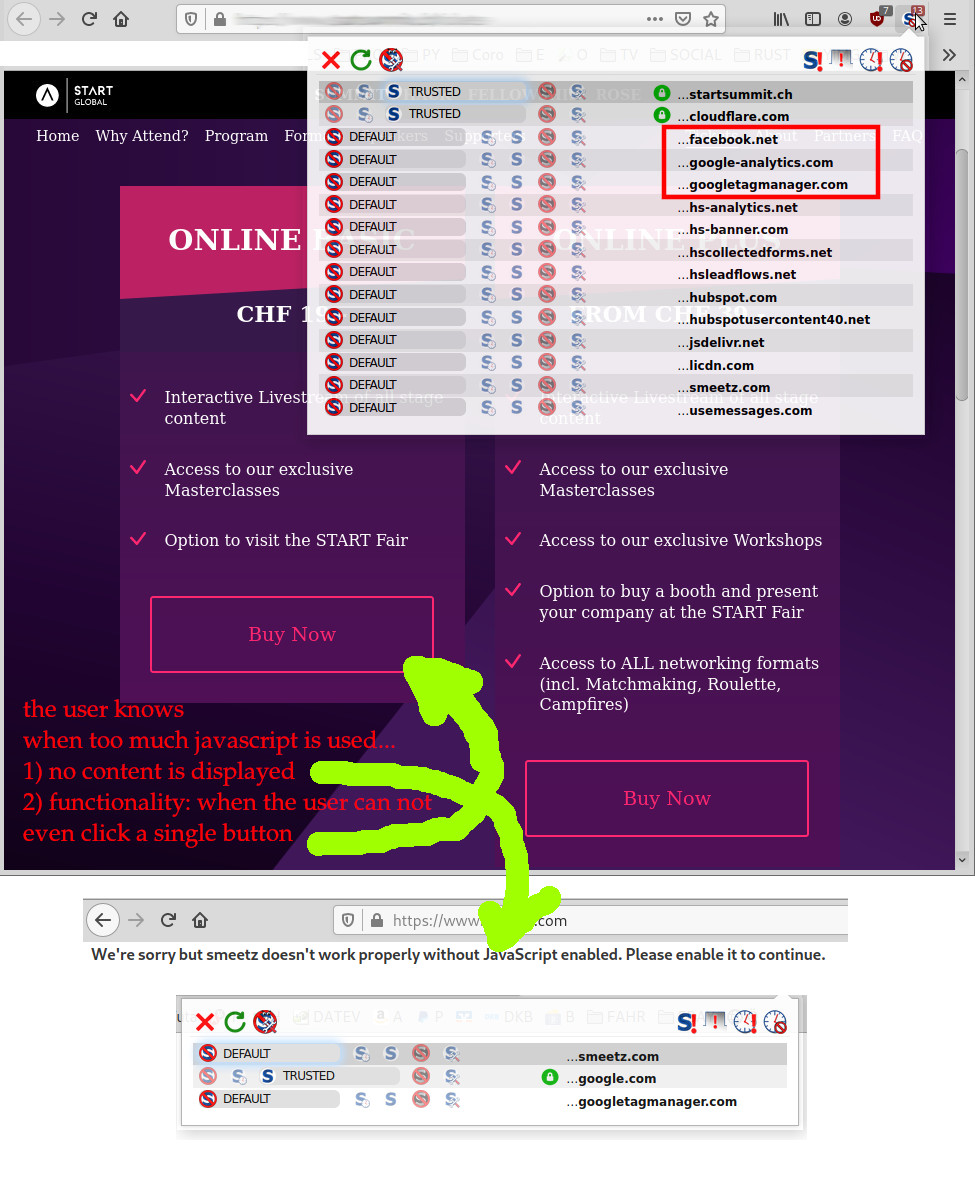
most users probably don’t care X-D twitter was updated and now, even viewing hashtags is impossible without JavaScript turned on (there used to be a functional version without javascript). JavaScript has developed from “it’s so great, the first true cross-platform […]
v1.6 https://dwaves.de/software/familypicshare.de_v1.6.tar.gz https://dwaves.de/software/familypicshare.de_v1.6.tar.gz.sha512sum.txt released: improvements: thumbnail generator thanks to ImageMagick PHP extension can now also resize large image files (10MBytes and more) for slideshow it now uses resized versions of 1024px instead of the original file (which might be too […]
it is remarkable, that even the most simple tool, like exiftool seems to have (had?) a serious security problem: “Improper neutralization of user data in the DjVu file format in ExifTool versions 7.44 and up allows arbitrary code execution when […]
Update: 2021-05: https://www.golem.de/news/irland-erste-patientendaten-im-netz-aufgetaucht-2105-156599.html Drei Krankheiten: erfolgreich kaputt gespart: schlechte Bezahlung: im Vergleich mit anderen EU-Ländern und auch USA steht Deutschland schlecht da was die Entlohnung von Ärzte an geht auch schlechter als Japan und gar Italien (!) das ist vermutlich […]
BeyondCorp Google’s new Approach to Security – we need to know EVERYTHING about the user – in order to trust the user – The Age of Surveillance Capitalism first of… the good about JavaScript is (always say something positive […]
update: 2024-04: having problem connecting to camera with vlc? (rstp not well documented or not working at all? try this: easy camera stream identification with ONVIF: it is a DAMN hussle, because EVERY camera vendor does it’s own rstp://user:password:ip.ad.dr.ess:/some/url/stream and […]
“Better Than Nothing” Starlink-Beta started across the US & Canada Starlink: amazing but and also a bit “crazy” “On 15 October 2019, the United States Federal Communications Commission submitted filings to the International Telecommunication Union on SpaceX’s behalf to […]
contains advertisement. to be honest, it is hard to keep up the speed at which cyber incidents are reported. here is the latest take on “Russian IT Sec Updates”. have phun! SecurityLab, [28.09.20 08:20] Last month, TikTok developers rolled […]
data google tries to collect from users: BeyondCorp Google’s new Approach to Security – we need to know EVERYTHING about the user – in order to trust the user – The Age of Surveillance Capitalism (it is probably only the […]
SecurityLab, [14.07.20 15:35] The Electronic Frontier Foundation (EFF) has unveiled a new database demonstrating how and where us law enforcement agencies use tracking technologies. A map of the use of tracking technologies in the United States is presented (https://www.securitylab.ru/news/510018.php) SecurityLab, […]
All SmartPhones are spies! that’s why Merkel keeps the Nokia from 1995 (even if that device is spied on as well, because it can not end2end encrypt sms or phone calls (*FAIL*! X-D)) Putin does not have a mobile phone […]
what to do to improve online privacy? use a privacy respecting DNS server by https://www.opennic.org/ for example: 195.10.195.195 (not google’s (8.8.8.8)) use Freifunk use a VPN such as: mullvad VPN https://mullvad.net/en/help/pricing-discounts/ https://mullvad.net/en/check/ Mozilla launched it’s own VPN service https://vpn.mozilla.org/ use tor […]
The Age of Surveillance Capitalism: “be careful what you reveal to your friend” (the internet) https://irlpodcast.org/season4/episode5/ “where it has gone from defending America to controlling it” data google tries to collect from users: (it is probably only the tip of […]
Worldwide mass surveillance by Germany’s intelligence (BND) service declared unconstitutional in landmark ruling on press freedom in the digital age “The ruling, the most far-reaching in this field in the past 20 years, sends an important signal for the protection […]
this age of mass surveillance… … who is observing “the observers”? Orwell left one final warning: 1984: “don’t let it happen” (alternative version) this is a “backup of the backup” that archive.org has taken from theorwellreader.com (offline since 2019) src: […]
this age of mass surveillance… … who is observing “the observers”? guess with it-security and internet-security (internet = roads, cars = computers that users use every day) it is like with real-life-security – there is no 100% security. all users […]
Tor is easier to use than ever superb usability! Tor is now super easy to use! (thanks all involved!) just get the tor bundle – it is tor bundled with firefox https://www.torproject.org/download/ Tor visualized: most users are legit: but criminals […]
home of git’s git repo: https://git-scm.com/ # to clone git’s git repo git clone https://git.kernel.org/pub/scm/git/git.git # as can be seen there, it is STILL under active development written in primarily in C, with GUI and programming scripts written in Shell […]
scroll down and behave! (slaves of digital dictatorships) short version summary of 1984: short version: 1984 needs to be avoided at any cost. because: it is evil. (Google did not drop it’s motto “don’t be evil” for nothing) in essence: […]
https://theintercept.com/2020/04/03/zooms-encryption-is-not-suited-for-secrets-and-has-surprising-links-to-china-researchers-discover/ hm…. let me think where one has seen this before: TELEGRAM! Zoom’s service is “not suited for secrets” “The researchers also found that Zoom protects video and audio content using a home-grown encryption scheme, that there is a vulnerability […]
this really raises the question: the mobile (complete computer) phone (number) as key to everything? is it a good idea to rely on smart phones (that are essentially a very small laptop and a cellular modem) and phone numbers to […]
https://youtu.be/Ag1AKIl_2GM the 4 free software freedom rules: freedom 0: The freedom to run the program as you wish, for any purpose. (computers start counting with 0, that’s why it is freedom 0) freedom 1: The freedom to study how […]
“first Benchmarks of the KX-6780A. China just developed it’s own x86 CPU with the performance of a Intel Core i7 2600 (4C/8T, 1,401 points) from 2011 the eight-core CPU-Z achieves 171 points in single-core and 1,396 points in Multi-Core comparison […]