SecurityLab, [02.11.20 11:52]
The 50-year-old businessman (Hunter Biden?) in April 2019 brought his device to the IT store Mac Shop in Delaware for repair, but never returned to pick it up.
The device was soon seized by the FBI.
According to IT expert Chris Greany, the laptop contained a “national security nightmare” and “classic blackmail material,” and was protected by a simple Hunter02 password.
The information on the device was not password protected and included:
Joe Biden’s personal mobile phone number and three personal email addresses, as well as the names of his secret service agents;
Mobile numbers of former President Bill Clinton, his wife Hillary, and almost all members of former President Barack Obama’s Cabinet;
A database of contacts of 1.5 thousand people, including actress Gwyneth Paltrow, Coldplay frontman Chris Martin, former presidential candidate John Kerry and former FBI chief Louis Freeh);
Personal documents, including hunter Biden’s passport, driver’s license, social security card, credit cards, and Bank statements;
https://www.securitylab.ru/news/513655.php
SecurityLab, [02.11.20 13:04]
What says the “Quran” about Privacy of the individual?
The right to a vehicle as a derivative of the right to privacy (privacy) is determined not so much by logic as by the traditions of Western individualism.
These traditions came to Russia from outside and have not yet taken root very well.
It is unlikely that the Russian mentality will change in the near future.
The constitutional right of citizens to privacy of communication was invented long before the Internet appeared.
It does not know such concepts as” logs”,” hash function “and”virus”.
New information technologies and related new social phenomena need to be reconciled with old, but “inviolable” human rights.
And the violation of these in the management of modern computer networks is widespread, but, fortunately, unintentional.
The gap between techies and lawyers is constantly widening – law is not keeping up with the development of information technology, and information technology is not keeping up with the emergence of new rights and obligations of citizens.
Accordingly, new risks appear in the work of Telecom operators (providers), as well as enterprises that independently operate information resources.
This paper is devoted to the analysis of one such new group of risks.
The risks associated with the secrecy of telecommunication messages and privacy are considered.
O you who believe, do not enter houses other than your own until you ask permission and wish peace to their inhabitants.
If you don’t find anyone there, don’t go in until they let you.
And if they say, “Go away!” then go away.
The Koran, Sura 24 “Light”, verses 27-28
(the oldest known normative document establishing the right to privacy)
https://www.securitylab.ru/analytics/267646.php
SecurityLab, [02.11.20 14:30]
Information security, courses, books, collections of useful material for IT specialists
https://t.me/Social_engineering
SecurityLab, [03.11.20 07:55]
Google has released a security update for its Chrome browser that fixes a number of vulnerabilities, including a zero-day vulnerability actively exploited by hackers.
https://www.securitylab.ru/news/513732.php
SecurityLab, [03.11.20 12:25]
The Russian authorities have submitted to the State Duma a bill providing for the introduction of fines for violating the IT security of systems of significant critical information infrastructure objects (CII) on the territory of the Russian Federation.
https://www.securitylab.ru/news/513744.php
SecurityLab, [03.11.20 15:55]
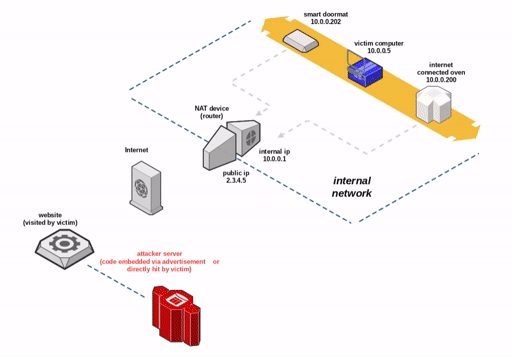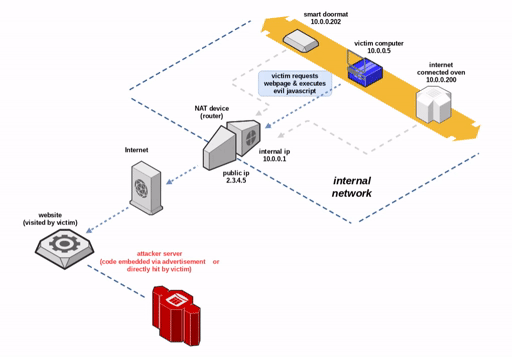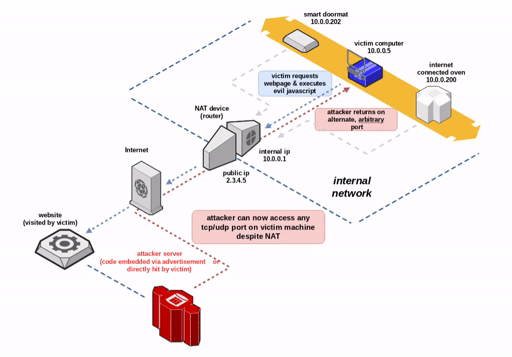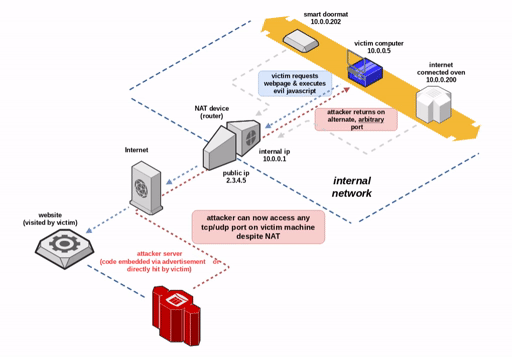
Security researcher Samy Kamkar introduced a new method to bypass the Network Address Translation (NAT) mechanism and firewalls, allowing remote access to TCP/UDP services on the victim’s internal network.
NAT Slipstreaming allows an attacker to remotely access any TCP/UDP service bound to a victim machine, bypassing the victim’s NAT/firewall (arbitrary firewall pinhole control), just by the victim visiting a website.
Developed by: @SamyKamkar // https://samy.pl
Released: October 31 👻 2020
Details:
- The NAT Slipstreaming (git repo) attack is based on using a mechanism to track ALG connections.
- Security researcher Samy Kamkar introduced a new method of bypassing the Network Address Translation (NAT) mechanism and firewalls, allowing remote access to TCP/UDP services in the victim’s internal network.The attack, dubbed NAT Slipstreaming, uses the browser and Application Level Gateway (ALG) mechanism for tracking connections used in firewalls, NATS, and routers.According to kamkar, the method presented by Him involves the use of techniques such as extracting internal IP addresses using a time attack or WebRTC, automated remote detection of MTU and IP fragmentation, compression of TCP packets, misuse of TURN authentication, precise control of packet boundaries, and creating Protocol confusion in the browser.
Since the destination port is opened by a NAT or firewall, the attack allows you to bypass the restrictions on port access implemented in the browser. All major modern browsers are vulnerable to this attack, which is a new variant of the NAT Pinning attack introduced by Kamkar ten years ago. The attack is based on support for ALG in NAT / firewalls – a mandatory feature for multi-port protocols such as FTP, IRC DCC, SIP, H323 (VoIP), and so on.
NAT distinguishes between connections that internal hosts try to establish with the same addresses/ports by overwriting the source ports. Using ALG, the NAT engine can track multiport protocols, ensuring that the required data is delivered to the requesting computer. Kamkar found out that it is possible to ” bypass the victim’s NAT and connect directly to any port on her computer, revealing previously protected / hidden services.”
Подробнее: https://z5h64q92x9.net/proxy_u/ru-en.en/https/www.securitylab.ru/news/513749.php
https://www.securitylab.ru/news/513749.php
SecurityLab, [03.11.20 17:20]
The government proposes to make it mandatory to include genomic data of absolutely all criminals (convicted and accused) who are on trial as suspects and even taken under administrative arrest.
According to the authors of the bill, its adoption will increase the efficiency of law enforcement agencies, allowing them to use biometric data of possible criminals in their operational activities.
According to preliminary calculations of the Cabinet of Ministers, the entry into force of this bill will lead to a significant increase in the amount of data related to genomic information, which can expand the available database to 5.2 million relevant records.
The explanatory note States that the increase in the DNA database will contribute to the level of crime detection.
Such databases, according to the note, are effective only if they contain material from more than 1% of the country’s population.
These proposals will bring this figure in Russia to 3.5% of the population.
https://www.securitylab.ru/news/513750.php
SecurityLab, [05.11.20 09:30]
Cisco has revealed details about a vulnerability in its AnyConnect Secure Mobility Client that allows remote code execution.
A PoC exploit is already available for the vulnerability, but Cisco is still working on fixing it.
According to the Cisco Product Security Incident Response Team, cybercriminals do not yet use the vulnerability in their attacks.
https://www.securitylab.ru/news/513772.php
SecurityLab, [05.11.20 15:20]
In 2019, Maze ransomware operators began using a new double-extortion tactic, in which attackers steal unencrypted files and then threaten to publish them if a ransom is not paid.
Many groups have adopted a similar strategy, but according to experts from Coveware, not all extortionists keep their promises to delete stolen data after paying a ransom.
https://www.securitylab.ru/news/513796.php
SecurityLab, [05.11.20 15:45]
Check Point Research experts have lifted the veil over the current cyber fraud operation conducted by Palestinian and Egyptian hackers.
During the operation, over 12 months, attackers compromised VoIP servers of more than 1.2 thousand organizations in 60 countries.
Hackers attacked Sangoma PBX, an open source user interface for managing Asterisk VoIP telephony systems, in particular Session Initiation Protocol (SIP) servers.
https://www.securitylab.ru/news/513801.php
SecurityLab, [05.11.20 20:25]
According to a report from cryptanalytic company CipherTrace on November 3, the recent movement involving two transactions worth up to 69,370 bitcoins (BTC) – or more than $ 960 million at the time of publication – originated from an address associated with the Silk Road trading platform.
The cryptocurrency user first sent 1 BTC, probably as a test transaction, before moving most of the coins.
https://www.securitylab.ru/news/513804.php
SecurityLab, [05.11.20 21:45]
Any individual chat participant can enable or disable disappearing messages mode.
However, the administrator can do this in group settings.
For WhatsApp users worldwide, This feature will be available during November.
https://www.securitylab.ru/news/513805.php
SecurityLab, [06.11.20 08:23]
On November 10, at 16.00, the webinar “Containers vs Compliance. Or how to meet the requirements of GOST R 57580.1-2017 for containerization environments.”
At the online event, jet Infosystems experts will review the terminology of containerization environments and analyze groups of regulatory requirements to assess their applicability to container environments, namely:
📍 event registration
📍 access control
📍 to segment the network
📍 integrity monitoring
📍 vulnerability management
You will learn about possible ways to implement regulatory requirements using the mechanisms available in container environments, taking into account the restrictions they impose. At the end of the online event, you will find examples of answers from the Central Bank of the Russian Federation to the question “is the container a virtual machine?»
It will be useful for organizations for which the GOST R 57580.1-2017 standard is a mandatory requirement, as well as for information security specialists who need to build protection for containerization environments.
SecurityLab, [06.11.20 11:50]
Apple has released fixes for three zero-day vulnerabilities in iOS and macOS that are already being exploited in attacks on users.
https://www.securitylab.ru/news/513806.php
SecurityLab, [06.11.20 11:55]
The administration of the service for hosting IT projects and their joint development GitHub is forced to convince its users that the rumors about hacking the service have no basis.
https://www.securitylab.ru/news/513809.php
SecurityLab, [06.11.20 20:45]
The Russian state Corporation Roscosmos is asking the government for 1.5 trillion rubles to create the Sphere satellite system.
https://www.securitylab.ru/news/513831.php
SecurityLab, [07.11.20 13:37]
The incident does not threaten the safety of users ‘personal data, as well as points on customer accounts,” Russian Railways said on Saturday.
Yesterday at 15: 50 (Moscow time), one of the Telegram channels reported that on the website of Russian Railways Bonus (rzd-bonus.ru, currently not working) the MySQL database dump of this site and two other files (the bash_history file and the private RSA key) are freely available.
In bash_history, in addition to the path to the database dump, there was the user’s username and password.
https://www.securitylab.ru/news/513833.php
https://www.checkpoint.com/cpx/
SecurityLab, [08.11.20 16:29]
A Russian-language cybercrime group that attacks high-income companies using ransomware Ryuk received $34 million from one of its victims for a key to recover encrypted files.
Designated as group “one” according to the identification obtained from the Trickbot botnet, which promotes the deployment of Ryuk in the networks of the attacked companies, it is very illegible in victims.
According to Vitaly Kremez, an expert at Advanced Intelligence, recent victims of the Odin group include companies in the technology and energy sectors, financial services, healthcare organizations, and government agencies.
According to an October report from the IB company Check Point, in the third quarter of 2020, the group attacked an average of 20 victims per week.
On average, the amount of ransom received by Ryuk operators is 48 bitcoins (about $ 750,000), and since 2018, they have managed to “earn” $150 million in total.
According to Kremez, cybercriminals negotiate with their victims in a strict manner and almost never show leniency.
https://www.securitylab.ru/news/513834.php
SecurityLab, [08.11.20 21:40]
The Let’s Encrypt certificate authority, which provides cryptographic certificates for TLS encryption, is switching to generating signatures using only its root certificate in January.
Because of this, 33% of Android smartphones will stop opening many sites.
On September 1, next year, the Let’s Encrypt cross-agreement with IdenTrust expires, and it will not be renewed.
This means that all browsers and operating systems without the Let’s Encrypt root certificate will no longer work with sites and services that use group certificates.
In the Android operating system up to and including version 7.1.1, the Let’s Encrypt root certificate is not trusted.
Therefore, access to sites signed with such certificates will not be possible.
https://www.securitylab.ru/news/513835.php
SecurityLab, [09.11.20 07:55]
Rostelecom-solar access management competence center launches the expert Blog Solar inRights, dedicated to popularizing the topic of access control to information systems in Russian companies https://rt-solar.ru/products/solar_inrights/blog/
The Solar inRights blog is intended for managers and specialists of information security and it departments, as well as for everyone who wants to get additional knowledge about the theory and practice of building infrastructure and building processes for managing access to company information resources.
SecurityLab, [09.11.20 08:30]
Jason Brvenik, CEO of NSS Labs, a security product testing company, gathered employees for a conference call on October 15 and suddenly announced the company’s closure.
The only public announcement of the closure was a short message on the official website: “due to the consequences related to COVID-19, NSS Labs ceased operations on October 15.”
https://www.securitylab.ru/news/513842.php
SecurityLab, [09.11.20 13:02]
In the past, some organizations used lines of code as their name as a joke, but at least one of them had to change it. According to the Guardian, the Registration chamber of great Britain forced one of the consulting companies to change its name after it became known that it can be used to carry out XSS attacks on vulnerable pages, including the Registration chamber itself. As it turned out, just by mentioning the company’s name, the regulator’s website could inadvertently compromise itself. This is not a very convenient situation for a government Agency that initially approved the problematic name.
<SCRIPT SRC=HTTPS://MJT.XSS.HT> LTD
dangerous for sites that can’t handle HTML formatting properly. These sites may decide that the company name field is empty and run the script from the XS Hunter site.
This script is quite harmless and just displays a warning, but the Registration chamber thought this was enough to oblige the company to change its name.
Now it is called ” THAT COMPANY WHOSE NAME USED to CONTAIN HTML SCRIPT TAGS LTD” (“THE same COMPANY whose NAME used to CONTAIN HTML script TAGS LTD”). According to representatives of the Registration chamber, they have taken measures to prevent similar situations in the future.
https://www.securitylab.ru/news/513846.php
SecurityLab, [09.11.20 13:40]
Join the Trend Micro CLOUDSEC 2020 online conference
this year, the cloudsec trend micro conference will be held online for the first time, including in the middle east and africa. we want to make this event as useful as possible, and it is important for us to know your opinion. cloudsec 2020 virtual is held under the motto transformation your way (“your way to transformation”), and therefore we invite you to contribute to the preparation of the conference and tell us what you want to see it.
Watch THE cloudsec 2020 announcement (https://www.cloudsec.com/).
Find out what’s waiting for you at the leading conference on cloud technologies and cybersecurity.
SecurityLab, [09.11.20 14:01]
Security researchers at Juniper Threat Labs have discovered a new botnet called Gitpaste-12.
The malware uses the github and Pastebin platforms to host component code and uses 12 different methods to compromise systems.
Experts recorded the first gitpaste-12 attacks on October 15, 2020,
but the malware itself was detected on the GitHub platform on July 9.
Gitpaste-12 operators mainly attack Linux-based x86 servers and IOT devices based on Linux ARM and MIPS processors.
In the first stage of the attack, Gitpaste-12 tries to use known exploits to break into systems and may attempt a brute force attack.
After the hack, the malware loads a script from Pastebin, which is re-run every minute.
Experts suggest that this is how the botnet is updated.
The main shell script loaded on the victim’s device during the attack starts downloading and executing components from GitHub.
The malware then prepares the target environment by eliminating system defenses such as firewall rules and standard software for preventing and monitoring cyber threats.
The researchers found that the script that contains comments on the Chinese language and the commands to disable some security tools.
In one case, teams disabled cloud security agents, indicating that cybercriminals intended to attack the public cloud infrastructure provided by Alibaba Cloud and Tencent.
https://www.securitylab.ru/news/513852.php
SecurityLab, [09.11.20 15:53]
There is only one channel in Telegram (https://t.me/true_secator), which reviews hacker groups (APT) working for the security services, analyzes their attacks and spyware Trojans.
And also studies the activity of ransomware, posts InfoSec humor and, of course, does not forget about news from the information security industry.
This is the SecAtor channel (https://t.me/true_secator).
On the channel you can find reviews of the American APT Equation (https://t.me/true_secator/581), North Korean Lazarus (https://t.me/true_secator/674), Vietnamese Ocean Lotus (https://t.me/true_secator/791), Indian Patchwork (https://t.me/true_secator/485), Taiwanese PoisonVine (https://t.me/true_secator/842) and many others.
Subscribe to the SecAtor channel (https://t.me/true_secator) and you will learn this and more!
SecurityLab, [09.11.20 20:29]
The EU Council of Ministers decided to oblige operators of platforms such as WhatsApp, Signal and others to create master keys for monitoring chats and messages with end-to-end encryption.
The reason for this resolution was the terrorist attack in Vienna.
The decision has already passed the necessary stages of approval and can be adopted at a video conference of the EU interior and justice Ministers in early December this year.
In addition, EU Council President Charles Michel is scheduled to visit Vienna to hold talks with
Austrian Federal Chancellor Sebastian Kurz.
On November 19, the decision will be approved by the working group of the Council for national security cooperation, and on November 25, it is planned to submit it to the Council of permanent representatives of the EU member States.
After the adoption of the draft, an order of the Council of Ministers of the EU Commission on the development of a regulation will follow.
https://www.securitylab.ru/news/513862.php
SecurityLab, [09.11.20 21:25]
During Bug Bounty practical classes, cyber specialists will study methods for assessing the security of computer systems of critical infrastructure facilities in Ukraine, the press service of the national security Council of Ukraine reports.
On November 9, Bug Bounty exercises began in Kiev, organized by The national cybersecurity coordination center under the national security and defense Council of Ukraine with the support of the us civil research and development Foundation (CRDF Global).
This is reported by the press service of the national security Council of Ukraine.
“Representatives of the main subjects of ensuring cybersecurity in Ukraine and employees of critical infrastructure will receive skills for five days to conduct a pentest of critical infrastructure objects, create a comprehensive system for protecting such objects and strengthen their own technical capabilities,” the report says.
https://www.securitylab.ru/news/513865.php
SecurityLab, [10.11.20 08:10]
The European Union Agency for Cybersecurity (ENISA) has presented a guide to supply chain security for the Internet of things (IOT).
https://www.securitylab.ru/news/513871.php
SecurityLab, [10.11.20 15:10]
Sonatype researchers have discovered an npm package (a JavaScript library) containing malicious code designed to steal confidential files from the user’s browser and Discord app.
https://www.securitylab.ru/news/513879.php
SecurityLab, [10.11.20 15:45]
The US Federal Trade Commission (FTC) announced a compromise agreement with Zoom after initially accusing the company of “a series of deceptive and unfair actions that undermine user security,” in particular, in the claim that the encryption it uses is more reliable than it actually was.
https://www.securitylab.ru/news/513882.php
SecurityLab, [10.11.20 16:34]
The attacking side of cybersecurity — what is it?
Take your first step on the attacking side — sign up for an intensive course at the link right now
At the intensive course “Pentesting: Level 0” you will get acquainted with typical tasks of the Red Team, in practice you will understand typical vulnerabilities and how they are exploited. You can also hack an application available on the network using an exploit from the set in the Metasploit framework, and much more!
3 days of intensive “Pentesting: Level 0” is:
— The first module of the professional program
– Practical training in CTF format
-Live communication with participants and experts
– Assessment of your strengths and career prospects in the world of information security
The intensive expert is Yegor Bogomolov, who has 200+ security analysis projects, BugBounty Yandex and HackerOne in his case, as well as a number of certifications, including OSCP
This week alone, the participation fee is 2,300 rubles. 20 seats left!
Take your first step on the attacking side — sign up for an intensive course at the link right now:
SecurityLab, [10.11.20 20:05]
The Ministry of internal Affairs this year placed 44 public procurement orders for the supply of funds that are designed to gain access to smartphone information.
The police are going to purchase foreign-made systems.
On average, one agro-industrial complex costs about 1.5 million rubles, and you have to buy them abroad.
https://www.securitylab.ru/news/513885.php
SecurityLab, [11.11.20 07:27]
Webinar ” PenTera: continuous comprehensive infrastructure pentest»
Jet Infosystems invites you to the product webinar “PenTera: continuous comprehensive infrastructure pentest”
(https://events.webinar.ru/jet/pentera1211), November 12 at 16.00. This is the final online event in the series of webinars about autopentests “a New look at security analysis: focus on real security”.
At the webinar, you can get acquainted with the Pcysys PenTera platform, learn about its advantages over other security analysis methods, and see the system in action. The pentest automation platform automatically finds and performs ethical exploitation of vulnerabilities, builds and visualizes full attack vectors, and provides recommendations on how to eliminate identified deficiencies to improve protection.
The webinar will be useful for managers of information security services and information security specialists who are thinking about improving real security, and penetration testing specialists who can learn how to use autopentests to minimize routine tasks.
SecurityLab, [11.11.20 08:10]
On Tuesday, November 10, Microsoft released planned monthly security updates in its products.
The updates fix 112 vulnerabilities in various products, ranging from Microsoft Edge to Windows WalletService.
24 vulnerabilities are critical because they allow attackers to remotely execute code on the victim’s system.
https://www.securitylab.ru/news/513954.php
SecurityLab, [11.11.20 10:30]
The authorities of the European Union have tightened the rules governing the sale and export of technologies for cyber tracking.
European legislators and the European Council have reached a preliminary agreement to update the rules governing the circulation of dual-use goods, such as facial recognition technologies and spyware, to prevent their use for the purpose of violating human rights.
https://www.securitylab.ru/news/513964.php
SecurityLab, [11.11.20 15:05]
Attackers stole access to one of the major Russian-language Telegram channels dedicated to the Internet resource Reddit.
The editorial Board of the “Durov Code” found out the details of the incident from the channel administrator.
https://www.securitylab.ru/news/513992.php
SecurityLab, [11.11.20 19:42]
Cyberbitva and online conference on information security the Standoff starts tomorrow (https://youtu.be/js3gcY61Kvs).
The program includes Russian and foreign speakers, including:
•Robert Lipovsky, ESET
* Cesar Cerrudo, IOActive Labs
* Arun Magesh, IoT security researcher
* Roman Ladutko, malware researcher
* Danila Parnishchev, independent researcher
* Sergey Gordeychik, information security expert
* Lawrence Emer, DarkLab (PwC)
* Krasimir Tsvetanov, Purdue University
* Vladimir Kropotov and Fyodor Yarochkin, Trend Micro
* Dmitry Sklyarov, Positive Technologies
• and other.
In addition to the conference, the platform will host a cyber battle of 29 teams of attackers and 6 teams of defenders, who will compete for the resources of the virtual metropolis.
SecurityLab, [11.11.20 20:20]
Czech military intelligence says: Cyber attacks can become the reason for the beginning of the 3rd world war
A published report for 2019 says that a fantasy scenario could soon become a scary reality.
The Czech information portal Lidovky, which reviewed the 14-page study, writes about the “first stage of preparation” for a new world conflict.
“A possible global conflict, which the world is currently moving towards, is at the first stage of its preparation.
The minds of those who can and will actively participate in it are being formed, and technological tools are gradually being determined.
If we are not able to assess the consequences of our own actions, then an erroneous instruction or command can initiate processes leading to mutual destruction.”
Details: Czech intelligence officers specifically warned about the dangers of advanced technologies.
More precisely, about their abuse.The likely cause of the global conflict may be the rivalry between Russia, China and the United States.
Czech military experts suggest that a large-scale confrontation may unfold in the air and cyberspace.
https://www.securitylab.ru/news/513997.php
SecurityLab, [12.11.20 08:05]
False triggering of the face recognition system used in the Moscow “Auchan” cost the buyer 15 thousand rubles and more than eight hours of hassle.
https://www.securitylab.ru/news/514003.php
SecurityLab, [12.11.20 11:15]
The Ministry of Finance of the Russian Federation has prepared a package of bills on digital currency, which proposes to deprive the owners of undeclared cryptocurrencies of their freedom.
According to the developed amendments on digital financial assets (CFA), owners of digital currencies can be imprisoned for up to three years if they have not reported to the tax authorities at least twice in three years on these transactions in the amount of 45 million rubles or more.
https://www.securitylab.ru/news/514015.php
SecurityLab, [12.11.20 15:15]
EU funds police training on iPhone hacking and Facebook surveillance
Experts from the non-profit organization Privacy International told how police officers around the world are trained by a little-known Agency of the European Union to carry out surveillance on Facebook and hack Apple iPhone.
Details:
Specialists of the non-profit organization Privacy International told how police officers around the world are being trained in a little-known Agency of the European Union to carry out surveillance on Facebook and hack Apple iPhones.
According to the documents, the European police College (CEPOL) for law enforcement training instructed officers around the world how to properly use malware and other tools to gain access to citizens’ phones and monitor social networks.
In some cases, training was funded from the EU Treasury and conducted in countries with a history of human rights violations.
CEPOL conducts training in various areas and is funded by EU programs.
Some initiatives took place as part of counter-terrorism programs, while others, such as a $13.6 million drone, a surveillance camera and wiretapping project in Niger, were sponsored from the EU trust Fund for Africa.
According to the CEPOL representative, the training was conducted in accordance with EU law and European Union policy, and the exchange of best practices and techniques, including those related to digital forensics and monitoring of social networks, is important for building the capacity of third countries to deal more effectively with terrible crimes.
Among the hundreds of training slides obtained by Privacy International, some talk about iPhone hacking tools such as GrayKey.
In a training slide for a session in Morocco, CEPOL informs participants that a key advantage of using GrayKey with the Axiom tool, created by canadian police partner Magnet Forensics, is to intercept Apple keys in iPhones, giving access to the user’s apps and data.
As for another way to hack iPhones or other smartphones, the Spanish Policia Nacional, a partner of CEPOL, has trained the authorities of Bosnia and Herzegovina to use malware to remotely control infected devices.
On the same slide was just written: “Malware is the future.”
CEPOL and the European police encourage foreign governments to spy on social networks.
One slide for Morocco’s national security Agency described the use of fake accounts and the purchase of social media analysis tools used to visualize relationships between targets of interest.
https://www.securitylab.ru/news/514037.php
SecurityLab, [13.11.20 07:12]
[Forwarded from the Announcements of the best information security events]
New solutions for protecting ViPNet EndPoint Protection workstations from Infotex»
We invite You to take part in the webinar (https://cybersecurity.axoft.ru/endpoint?utm_source=securitylab), dedicated to the new Infotex software package “ViPNet EndPoint Protection-review of a new product for protecting workstations”, which will be held on November 19 at 10.00 (Moscow time).
The complex is designed to ensure information security of end devices, prevent “file” and network attacks, detect malicious actions and respond to these actions.
The webinar will cover the following topics
• * product Composition and functionality;
* Key usage and application scenarios;
• Plans for certification;
* Development prospects.
Event (https://cybersecurity.axoft.ru/endpoint?utm_source=securitylab) will be most interesting for information security managers of medium and large companies.
We are waiting for you at the online event on November 19 (Thursday) at 10.00! The link to participate will be announced to registered participants.
Pre-registration is required.
SecurityLab, [13.11.20 13:00]
Few people will like derogatory taunts in his address, especially cybercriminals.
This is the tactic that the US Cyber Command decided to use against “Russian hackers” – to publicly ridicule them, exposing them as clumsy and harmless cartoons.
https://www.securitylab.ru/news/514054.php
SecurityLab, [13.11.20 16:05]
In 2020, the number of registered cyber attacks on manufacturing enterprises using extortionate SOFTWARE has increased dramatically, as cybercriminals have learned to disrupt production processes by attacking both the company’s IT networks and the SOFTWARE used in production.
https://www.securitylab.ru/news/514061.php
SecurityLab, [13.11.20 20:25]
The US company Microsoft has recorded cyber attacks by Russian and North Korean hackers on seven companies that develop vaccines and medicines for coronavirus.
This is stated in a statement by Microsoft Vice President of security Tom Burt.
https://www.securitylab.ru/news/514063.php
SecurityLab, [14.11.20 06:28]
Members of the Swiss Parliament have published a report on the investigation into the use of Crypto AG by US intelligence agencies.
The CIA and German intelligence have undermined Switzerland’s reputation as a historically neutral state by using one of its companies as a platform for espionage operations around the world for decades.
This is reported in a new report by members of the Swiss Parliament, writes the Washington Post.
The experts who conducted the investigation concluded that the Swiss government not only knew, but also participated (albeit indirectly) in the espionage operations conducted by the Swiss company Crypto AG.
https://www.securitylab.ru/news/514053.php
SecurityLab, [14.11.20 08:32]
[Forwarded from the Announcements of the best information security events]
Positive Technologies invites you to the webinar ” how malware bypasses sandboxes: the evolution of methods»
The webinar will be held on November 19 at 14: 00.
Positive Technologies invites you to take part in the webinar “how malware bypasses sandboxes: the evolution of methods”, which will be held on November 19 from 14:00 to 15:00 (Moscow time).
Attackers regularly make changes to malware TO avoid detection for as long as possible. APT groups have been particularly successful in this. When collecting information about the company’s infrastructure, criminals try to use malware that can detect and bypass virtualization and code analysis tools.
Positive Technologies experts will tell you how techniques for bypassing isolated environments for software research have changed over the past 10 years, and discuss detecting these techniques using the example of PT Sandbox.
The webinar will be of interest to SOC employees, malware researchers, PT Sandbox users, and anyone interested in information security issues.
To participate, you need to register (https://www.ptsecurity.com/ru-ru/research/webinar/kak-vredonosnoe-po-obhodit-pesochnicy-ehvolyuciya-metodov/?utm_source=SecLab&utm_medium=news&utm_campaign=webinar19112020). Registration ends on November 19 at 12: 00. The viewing link will be sent to all registered participants half an hour before the start of the webinar.
SecurityLab, [14.11.20 10:57]
In the first two days of the event, more than 30 presentations by information security experts were also held, which were watched by more than 13 thousand viewers from different countries.
Is it possible to arrange a blackout in a megacity the size of Moscow or new York? Many information security researchers believe that a few days will be enough for such a diversion. On the cyber range to The Standoff is possible to verify these claims. During the six-day marathon, hackers look for weaknesses in the power system of a digital copy of the city, try to derail a train or disrupt the operation of the airport.
A third of the event has already been completed. The attackers damaged the technological systems of the oil field, petrochemical plant, airport and business center. In parallel, information security experts made presentations on how to hack a smartphone with a lighter, install a game on a trading terminal, and so on.
https://www.securitylab.ru/standoff/514066.php
SecurityLab, [15.11.20 08:24]
The cost of the program to develop a modern f-35 fighter jet has increased significantly after the PRC compromised the software manufacturer in the Lockheed Martin supply chain, which led to the need to rewrite a potentially vulnerable system from scratch. This was stated by a specialist at the Center for strategic and international studies, James Lewis, during a meeting on cyber defense of the British army.
According to Lewis, China compromised the systems of a subcontractor involved in the development of the F-35 and allegedly infected software designed for the fighter. The specialist did not specify what kind of software was in question, and whether it was possible to prevent infection.
“Lockheed Martin has done an excellent job of protecting its systems [ … ], but going lower down the chain, not everyone provides the level of security you need. So this is an allegation-through a subcontractor, China was able to access [the systems]. We don’t know what they could have done, the vulnerability was closed, and the software was mostly rewritten from scratch,” the Register quoted Lewis as saying.
In the past, Lewis has referred to this incident as a rumor, partly explaining the high cost of the F-35. Apparently, this attack is not related to the 2017 incident, when attackers penetrated the computer network of the US air force and stole materials related to the F-35, including several gigabytes of data related to the design and electronic systems of the fighter.
https://www.securitylab.ru/news/514065.php
SecurityLab, [15.11.20 08:36]
[Forwarded from the Announcements of the best information security events]
[ Photo ]
On November 16, at 13:00, Positive Technologies specialists will conduct a preview of a new product — the next-generation vulnerability management system MaxPatrol VM.
The program includes substantive conversations on how to properly build processes, which vulnerabilities to fix in the first place, and, of course, a demo of the MaxPatrol VM itself.
The discussion and presentation will take place at the Standoff global conference and cyber battle at 13:00.
Registration for the event (https://www.ptsecurity.com/ru-ru/products/mpvm/?utm_source=telegram&utm_medium=seclab&utm_campaign=mpvm_launch)
SecurityLab, [16.11.20 08:04]
The network hosts many daily paid and free events, courses and webinars on information security. The @secwebinars channel will help you make your choice. it offers only the most relevant and popular events for both information security professionals and those who are just starting their career. Most events are free.
Subscribe to the channel @secwebinars
SecurityLab, [16.11.20 08:15]
Microsoft intends to suspend the release of additional preliminary updates for Windows 10 in December 2020 and make a short pause in the work.
https://www.securitylab.ru/news/514071.php
SecurityLab, [16.11.20 08:20]
Users sued Google, accusing the company of using mobile Internet traffic on their Android devices without permission.
The lawsuit “Taylor et al. V. Google” was filed in the Federal district court of San Jose (California, USA) on behalf of four citizens living in Illinois, Wisconsin and Iowa.
The plaintiffs hope that the claim will get the status of a collective one.
https://www.securitylab.ru/news/514072.php
SecurityLab, [16.11.20 11:25]
The US national security Agency (NSA), with the participation of the Danish intelligence service, spied on Danish and Swedish defense enterprises.
According to the Danish public broadcaster Danmarks Radio, the operation lasted from 2012 to 2014, when Denmark purchased new combat aircraft.
https://www.securitylab.ru/news/514081.php
SecurityLab, [16.11.20 12:33]
Over the past two days, 15 reports of information security experts were also held.
At the Standoff CyberPolygon, attackers were able to transfer money from Virtual City Bank cards to their own account, stopped production at a chemical plant and oil production, and caused a failure in the airport’s technological systems.
By the end of the fourth day, 13 unique business risks were implemented.
The speakers, meanwhile, discussed threats to information security, a large part of which is related to COVID-19.
These include vulnerabilities in medical image recognition systems, problems with IP telephony and video conferencing products, and attempts to hack VPNs.
https://www.securitylab.ru/standoff/514086.php
SecurityLab, [16.11.20 15:20]
The unique IDFA (The Identifier for Advertisers) number that Apple assigns to each device allows the tech giant and all applications on the phone to track the user and collect information about their actions on the Internet and on mobile devices.
As with cookies, this requires the consent of users under EU law, but Apple implements these tracking codes without the device owners ‘ knowledge.
In this regard, the non-profit organization NOYB (“none of your business”) filed a complaint against the company.
https://www.securitylab.ru/news/514105.php
SecurityLab, [16.11.20 15:34]
[Forwarded from the Announcements of the best information security events]
IB of cloud environments: from denial to confident use
On November 18, at 16: 00, we invite you to the first online event in a series of webinars about Cloud Security “IB of cloud environments: from denial to confident use”.
(https://redirect.jet.su/?url=https://events.webinar.ru/jet/cloudsecurity1811)The event will focus on the overall picture of information security in the cloud and how to take advantage of the cloud when implementing security measures. Jet INFOSYSTEM experts will review the most common threats in the cloud, key controls for protecting cloud environments, as well as tools available in the cloud and their use for information security.
Who will benefit:
🔺 Information security specialists who want to understand the features of the cloud and approaches to its protection
🔺 For those who want to understand the information security tools available in the cloud
🔺 It professionals who are planning to move to the cloud
SecurityLab, [17.11.20 07:28]
[Forwarded from the Announcements of the best information security events]
Automated response to information security incidents
How can I increase the speed of incident response? How to automate the process correctly?
Which SOAR should I choose?
We invite you to the online event “Security Stand Up: automated response to information security incidents” (https://cybersecurity.axoft.ru/soar?utm_source=securitylab) November 24 at 10 (Moscow time):
– get acquainted with soar solutions from leading manufacturers: Palo Alto Networks, Siemplify, R-Vision
– learn about the main trends in the SOAR solutions market
– understand which criteria are the main and important when choosing SOAR
– choose the perfect solution for you
3 leading manufacturers, 3 pitches and unlimited options for choosing your” own ” SOAR.
SecurityLab, [17.11.20 07:38]
The global Commission on the Stability of Cyberspace (GCSC) has presented its final report outlining its vision of how the world’s countries should behave on the Internet.
GCSC is an organization that develops policies that countries around the world can follow to ensure the stability and security of the global Network.
The GCSC exists because the organization’s founders and stakeholders believe that the Internet is vital, but not protected by any agreements or regulations.
The organization is pragmatic enough to understand that some countries will never sign up to such norms, since they will not tolerate any restrictions for their offensive cyber operations.
However, according to GCSC management, if the Commission can create norms and get them adopted by countries and multilateral organizations, it will be possible to present those who use the Network as a weapon as operating outside acceptable standards of behavior.
https://www.securitylab.ru/news/514107.php
SecurityLab, [17.11.20 08:15]
Services of technology companies that do not comply with the requirements of the EU legislation will not be allowed to enter the European market.
European Commissioner for internal market Affairs Thierry Breton told the German weekly Welt am Sonntag that the European Commission is already finalizing new rules for Internet companies.
Together with European Commissioner for competition Margrethe Vestager, Breton will present two new bills called “the law on digital services” and “the law on digital markets” on December 2 this year.
https://www.securitylab.ru/news/514115.php
SecurityLab, [17.11.20 09:15]
Cybercrime groups operating under the Ransomware-as-a-service (RaaS) business model are actively looking for partners to divide the profits generated from cyber attacks using ransomware INTO public and private organizations.
https://www.securitylab.ru/news/514116.php
SecurityLab, [17.11.20 12:15]
Although all companies attacked by ransomware are different, they can still learn from each other’s experience.
A step-by-step examination of a ransomware attack can help organizations realize that they may also be vulnerable to such attacks, and explain what steps should be taken to avoid these attacks.
https://www.securitylab.ru/news/514117.php
SecurityLab, [17.11.20 15:05]
The Ministry of digital development, communications and mass communications of the Russian Federation is developing a mobile application to combat the spread of coronavirus infection (COVID-19) – “Stopcoronavirus. My contacts”.
The program is based on technology from Apple and Google and will be used to monitor social contacts.
https://www.securitylab.ru/news/514127.php
SecurityLab, [17.11.20 15:45]
A team of specialists from the University of Birmingham has developed a new attack that can undermine the confidentiality and integrity of the Intel Software Guard Extensions (SGX) CPU instruction set by manipulating the supply of electrical voltage to the CPU core.
https://www.securitylab.ru/news/514128.php
SecurityLab, [17.11.20 19:10]
The American Corporation Twitter Inc has hired one of the hackers Payter Zatko, previously known under the network alias Mudge, as the head of the security service.
Zatko will report directly to CEO Jack Dorsey.
It is planned that it will take over the management of key security functions.
In an interview with NBC, the former hacker said that he will study “information security, site integrity, physical security, platform integrity, and anything that may relate to third-party manipulation of the platform as a whole.”
https://www.securitylab.ru/news/514134.php
SecurityLab, [18.11.20 06:28]
[Forwarded from the Announcements of the best information security events]
On November 19, at 16:00, jet Infosystems and R-Vision will hold an online event “how to avoid drowning in the flow of compliance checks and free up resources for solving information security problems”, where experts will tell you how to organize the audit/self-assessment process so that it is transparent and contains a minimum of pitfalls at each stage.
It will be useful for information security specialists, heads of information security services, employees who support internal information security audits, and internal control services.
Questions for discussion at the online event:
Лав avalanche of compliance that falls on the IB specialist. What checks does it consist of?
📍 How do I prepare for the audit?
📍 How to organize your collection of documents?
📍 How to minimize labor costs when calculating final indicators and preparing reports?
📍 How do I process comments and create a single list of corrective actions?
SecurityLab, [18.11.20 10:20]
Rapid7 specialists reported on the risks associated with connecting the Tesla Backup Gateway to the Internet, and described how open connections can be used by hackers to violate the privacy and security of users.
https://www.securitylab.ru/news/514143.php
SecurityLab, [18.11.20 10:25]
Last week, the police Department of a suburban Florida city received a phone call from a man who confessed to killing his wife.
According to him, he laid explosives after learning about the betrayal of his wife.
However, there was no actual crime, and the caller turned out to be a hacker who hacked someone else’s ring security camera.
https://www.securitylab.ru/news/514148.php
SecurityLab, [18.11.20 14:04]
[Forwarded from the Announcements of the best information security events]
Define your path in the world of cybersecurity at the “CyberSecurity: Level 0” intensive course»
3 days of video conferences with practicing information security experts, together with whom you:
— Understand the typical tasks of the Blue Team and Red Team
— Learn how to scan the network and take a comprehensive approach to the network device
– Gain skills in working with virtual environments, intrusion detection and prevention systems (IDS/IPS)
— Conduct your first attacks on the network layer, in order to investigate potentially malicious nodes
– Pass the first module of the professional program
Special offer for those who are not used to delay useful decisions!
For the next week, the cost of participation in the intensive course is only 2300 RUB
SecurityLab, [18.11.20 14:20]
Anton Gorelkin, a member of the state Duma Committee on information policy, introduced a bill prohibiting the use of publicly available personal data without the owner’s consent. According to the document, Russians are also granted the right to demand their removal from the operator.
https://www.securitylab.ru/news/514145.php
SecurityLab, [18.11.20 14:30]
On Wednesday, November 18, US President Donald Trump dismissed the head of the US cybersecurity and Infrastructure Security Agency (CISA), a structure formed by his administration specifically to protect American computer networks from hackers.
https://www.securitylab.ru/news/514160.php
SecurityLab, [18.11.20 15:47]
By the end of the last day at the Standoff CyberPolygon, attackers had broken into the perimeter of all six organizations and gained a foothold in corporate networks. However, it was more difficult to implement business risks: hackers were confronted by experienced teams of security specialists. The airport, amusement Park, gas distribution station, oil company and power plant systems were disabled. The Bank and the business center suffered losses. The hackers could display anything on the advertising screens. But the seaport and the railway persisted.
In hot pursuit, we tell you about everything that happened during the Standoff. During the online presentations of experts, listeners learned, for example, how to get physical access to a room, fake a voice in five seconds, decrypt data corrupted by a ransomware virus, and intercept smartphone data on the 5G network.
The winning team was Codeby (27,123 points, 12 cyber risks), with back2oaz in second place (24,463 points, 12 cyber risks), followed by DeteAct
(18,508 points, 7 cyber risks). The attackers managed to implement 47% of the inherent risks. Two of the 24 implemented cyber risks were new and not included in the competition program. In total, the jury accepted more than 50 reports on successfully completed tasks.
Defense teams were able to identify more than 200 is incidents in their infrastructures. The IZ:SOC and CT&MM teams found the most incidents. Teams conducted 21 incident investigations. On average, it took teams 11 hours and 50 minutes to investigate with the necessary completeness of the collected facts.
https://www.securitylab.ru/standoff/514163.php
SecurityLab, [18.11.20 16:58]
Israeli spyware manufacturer NSO Group is trying to avoid any legal consequences from creating and selling tools to hack WhatsApp users’ phones.
NSO Group filed a document with the U.S. court of Appeals for the 9th circuit, saying that U.S. district judge Phyllis J. Hamilton made a mistake in July this year, rejecting the application of a software developer to obtain immunity from the WhatsApp lawsuit, which accuses the company of violating the U.S. computer crimes act by using malware to spy on human rights lawyers, journalists and political dissidents on behalf of government clients.
NSO Group has called on a Federal appeals court to overturn a California judge’s July 2020 decision and protect the company from a lawsuit over hacking the phones of more than a thousand WhatsApp users.
In its brief, the company said that governments around the world are using its technology to bypass end-to-end encryption in WhatsApp to spy on suspects in serious criminal cases.
(Jeff Bezo’s iPhone was also hacked in this way)
https://www.securitylab.ru/news/514164.php
SecurityLab, [18.11.20 19:35]
Together with AMD, Intel and Qualcomm, the company introduced a “shared vision for the future of the Windows PC”, in which security features are built into the core itself, right in the CPU.
Pluton will be used to protect personal data on Windows computers.
The chip eliminates the possibility of a hacker attack by storing the user’s personal data — for example, encryption keys-in a separate segment from the system.
“None of this information can be removed from Pluton, even if an attacker installs malware or gains full physical control of the computer,” the processor’s operating principle says.
Microsoft management intends to enter into an agreement with AMD, Intel and other major processor developers in the near future so that they install a new chip in their chips before production.
It will not allow Internet users to launch pirated content or play unlicensed games.
https://www.securitylab.ru/news/514165.php
SecurityLab, [19.11.20 01:15]
Firefox 83 now uses -8% less RAM and loads pages +15% faster than Firefox 82.
Mozilla achieved this by optimizing JavaScript support, while adding a lot of other innovations to its browser.
The new version of the Mozilla Firefox 83 browser will also get a security feature called HTTPS-Only Mode.
This mode will not open unsafe sites.
https://www.securitylab.ru/news/514166.php
SecurityLab, [19.11.20 09:25]
Microsoft stopped supporting Windows 10 version 1809 (Home and Pro) last week, but the company has already released an important security update for it (other versions of Windows have not received updates).
https://www.securitylab.ru/news/514171.php
SecurityLab, [19.11.20 10:20]
Deputy Chairman of the State Duma Committee on information policy, information technologies and communications Maxim Kudryavtsev introduced a bill on remote registration of SIM cards and the ability to block lost mobile phones by IMEI (International Mobile Equipment Identity).
https://www.securitylab.ru/news/514174.php
SecurityLab, [19.11.20 11:05]
In Russia, the law may allow blocking YouTube, Facebook and other services for censorship.
The corresponding bill was introduced by Senator Alexey Pushkov and six deputies and will soon be considered by the State Duma of the Russian Federation.
https://www.securitylab.ru/news/514176.php
SecurityLab, [19.11.20 15:00]
Cisco has fixed three vulnerabilities (CVE-2020-3441, CVE-2020-3471, and CVE-2020-3419) in the Webex video conferencing application that allow attackers to join a meeting and eavesdrop on conversations as a “Ghost user” invisible to other participants.
https://www.securitylab.ru/news/514189.php
SecurityLab, [19.11.20 15:14]
⚡ This Positive Technologies shares the results of a survey (https://www.ptsecurity.com/ru-ru/research/analytics/prozrachnost-korporativnyh-setej-v-rossii-2020/) 230 Russian specialists in information security about the level of transparency of corporate networks.
In the report:
– Where traffic transparency is higher — in Russia or abroad.
– What threats Russian Isnike most commonly detected in the network.
– Transparency of the network or encryption of internal traffic that selects Isnic.
SecurityLab, [19.11.20 18:55]
After checking almost 275.7 million passwords, NordPass published a list of the most frequently used passwords for online accounts in 2020.
The first five lines were taken by such combinations as “123456789”, “picture1”, “password” and “12345678”.
The most popular password was “123456”, which was hacked more than 23 million times in 2020 alone.
The shorter password “12345” ranked first last year.
But more than 188,000 users chose it this year, putting it in eighth place.
Both passwords can be cracked in less than a second.
https://www.securitylab.ru/news/514195.php
SecurityLab, [19.11.20 20:15]
The researchers collected information from a laser navigation system in a popular vacuum cleaner robot and applied signal processing and deep learning techniques to reconstruct speech and detect TV sounds in the same room as the device.
“we welcome these devices into our homes and have no idea how they can be used,” explains Nirupam Roy, associate professor of computer science at the university of Maryland, one of the study’s authors. — but we’ve clearly shown that even though robot vacuums don’t have microphones, it’s possible to repurpose the systems they use for navigation to spy on users and potentially reveal personal information.”
https://www.securitylab.ru/news/514198.php
SecurityLab, [20.11.20 08:05]
With more than 100 million downloads, the Android instant messaging App “GO SMS Pro“ contains a vulnerability that allows outsiders to steal media files from someone else’s correspondence.
According to the specialists of the Trustwave information security company, an unauthorized attacker can get access to personal voice messages, videos and photos sent via the GO SMS Pro app.
https://www.securitylab.ru/news/514204.php
SecurityLab, [20.11.20 09:15]
Russia may introduce fines for social networks that do not delete illegal content in accordance with the requirements of Russian legislation.
Alexander Khinshtein, head of the state Duma Committee on information policy, information technologies and communications, told the TASS news Agency that the relevant draft law has already been prepared.
https://www.securitylab.ru/news/514206.php
SecurityLab, [20.11.20 09:25]
Facebook has fixed a critical vulnerability in the messaging app Facebook Messenger for Android.
Its operation allowed callers to listen to other users’ surroundings without permission before the caller on the other end answered the call.
https://www.securitylab.ru/news/514205.php
SecurityLab, [20.11.20 13:50]
According to experts of the information security company Menlo Security, although two-thirds of their customers use the latest version of Google Chrome (.86),
83% of all users of this browser work with outdated versions with uncorrected zero-day vulnerabilities recently disclosed by Google.
In this regard, we should expect an increase in the number of attacks with the exploitation of these vulnerabilities, says Vinay Pidathala, Director of security research at Menlo Security.
https://www.securitylab.ru/news/514209.php
SecurityLab, [20.11.20 15:20]
Researchers from Kenna Security teamed up with experts from the Cyentia Institute and analyzed 473 vulnerabilities discovered since 2019, the exploitation of which was recorded in real attacks.
Experts warned That when the PoC code for exploiting the vulnerability is published in the public domain, attackers get a 47-day head start to implement their goals.
https://www.securitylab.ru/news/514218.php
SecurityLab, [21.11.20 07:20]
The Frolov Interdistrict Prosecutor’s office of the Volgograd region approved a criminal charge against a 20-year-old local resident.
https://www.securitylab.ru/news/514223.php
SecurityLab, [21.11.20 08:19]
In addition, it claims that it can get databases of patients with HIV and tuberculosis from other regions.
According to the telegram channel of information leakage, on Wednesday (18.11), the seller put up for sale the data of more than 2,400 patients with HIV/AIDS, obtained, according to him, from the database of the state regional budgetary health institution “Novgorod center for the prevention and control of AIDS and infectious diseases “Helper” (GOBUZ center “Helper”).
https://www.securitylab.ru/news/514226.php
SecurityLab, [21.11.20 09:30]
The global damage from Cybercrime in 2021 may amount to about 6 trillion dollars, the President of the Russian Federation said.
https://www.securitylab.ru/news/514225.php
SecurityLab, [21.11.20 12:00]
Two tech giants Apple and Facebook have exchanged accusations about the policy of collecting user data and using it for commercial purposes.
The first dispute was initiated by Apple, which said that it does not collect detailed user information for sale to third parties, unlike Facebook, which uses a “completely different approach”.
https://www.securitylab.ru/news/514227.php
SecurityLab, [22.11.20 17:00]
35 years ago, in 1985, there was the legendary Windows 1.0.
On 20 November it started to work.
Now, after all these years, billions of devices are running on this system.
Windows 1.0 had a graphical window interface and several basic programs.
Over time, developers began to add a lot of new features that are now used by a huge number of people.
https://www.securitylab.ru/news/514233.php
SecurityLab, [22.11.20 19:02]
According to (Bill) Gates, a new disaster may hit people in 10-20 years or even earlier.
Last week, billionaire Microsoft founder Bill Gates recorded a podcast in which he discussed the coronavirus pandemic with actress Rashida Jones and US chief infectious diseases specialist Anthony Fauci, as well as changes in the world.
According to the billionaire, the world is already undergoing drastic changes.
People get used to masks, social distancing, and remote work = “the new normal”?
https://www.securitylab.ru/news/514234.php
SecurityLab, [23.11.20 07:27]
Jet Infosystems and Check Point invite you to the online event “infrastructure Protection in the public cloud from (A) zure to (Z)ndex. Cloud” on November 25 at 16.00. At the webinar, experts will discuss the main issues of information security when working with public clouds, talk about the key controls necessary for protection, and demonstrate the capabilities of Check Point Dome9, a Cloud Security Posture Management (CSPM) solution that allows you to automate the task of ensuring information security.
Points for discussion:
·How to avoid losing control over resources in the public cloud
·How to protect yourself from unauthorized changes and dangerous settings of public services
· How to safely use microservices and kubernetes without creating additional risks
Who will benefit:
* Information security specialists dealing with the issue of infrastructure protection in the public cloud
·For those who want to learn about the possibilities of automating information security controls in the public cloud
* Engineers supporting infrastructure in multicloud
SecurityLab, [23.11.20 09:10]
Security analyst Bank_Security came across a discussion thread on one of the hacker forums, in which someone under the pseudonym pumpedkicks published a list of IP addresses of 49,577 organizations with vulnerable Fortinet VPN devices.
According to the hacker, he also has unencrypted credentials associated with these IP addresses.
Among others, the list of potential targets includes domains owned by major banks and government organizations around the world.
https://www.securitylab.ru/news/514240.php
SecurityLab, [23.11.20 09:45]
The Ministry of internal Affairs of Russia intends to create a centralized Bank of biometric data of Russians and foreign citizens within three years.
With its help, the authorities will be able to identify people by their face image and fingerprints.
This was reported by the TASS news Agency.
https://www.securitylab.ru/news/514241.php
SecurityLab, [23.11.20 11:15]
The scammers redirected email and web traffic intended for several cryptocurrency exchanges.
As KrebsOnSecurity has learned, during the attacks, criminals carried out phishing attacks on employees of the world’s largest domain name Registrar, GoDaddy.
The attackers tricked the company’s employees into transferring ownership and / or control over the domains.
https://www.securitylab.ru/news/514247.php
SecurityLab, [23.11.20 12:55]
Positive Technologies experts analyzed 36 HPE families that have been active over the past 10 years and have features for detecting and bypassing virtualization tools (sandboxes).
The analysis showed that a quarter of all malware included in the study was active in 2019-2020, at least 23 APT groups around the world used programs from this sample in their attacks, and 69% of VPOs were used for the purpose of espionage.
https://www.securitylab.ru/news/514251.php
SecurityLab, [23.11.20 16:00]
To fix vulnerabilities and add new features to its Keyless access system in Tesla Model X vehicles, Tesla uses “over-the-air”updates.
However, according to a specialist at the Catholic University of Leuven (Belgium), Lennert Wouters, you can use this update delivery mechanism to steal a car in a matter of minutes.
https://www.securitylab.ru/news/514263.php
SecurityLab, [23.11.20 18:35]
The Ministry of Finance of Russia announces the start of accepting applications for inclusion in the list of software that is planned for pre-installation on electronic devices.
The rules for compiling and maintaining the list are set out in the Decree of the Government of the Russian Federation No. 1867 of November 18, 2020.
https://www.securitylab.ru/news/514267.php
SecurityLab, [23.11.20 23:00]
Google gives out when searching sites that access is restricted in Russia, including resources with extremist, pornographic and suicidal content, according to Roskomnadzor.
According to the Agency’s calculations, the search engine does not remove up to 30 percent of “dangerous” content from its search results.
https://www.securitylab.ru/news/514268.php
SecurityLab, [24.11.20 08:13]
[Forwarded from the Announcements of the best information security events]
Solar webProxy 3.4. Now with antivirus
Preventing malware from reaching users ‘ workstations is an important task that antivirus programs are quite successful at. But it is even more important to prevent malware from accessing the organization’s network.
Solar webProxy, a Secure Web Gateway (SWG) solution equipped with the Dr. Web antivirus module, is designed to solve this problem.
December 3 (https://solar.webex.com/solar/onstage/g.php) Olga Isaeva, a leading business analyst at Rostelecom-Solar, will talk about the features of Solar WebProxy 3.4, designed to facilitate the work of users, and together with Vasily Sevostyanov, head of the technical support department of sales at Doctor Web, will discuss the choice of an antivirus module and its advantages.
Webinar (https://solar.webex.com/solar/onstage/g.php) will be of interest to managers and specialists of information security and it departments of foiv and roiv, companies in the financial sector, as well as companies with a geographically distributed structure.
The program of the webinar:
1. New features in Solar webProxy 3.4
2.Dr. Web antivirus. Features and benefits
3. Solar webProxy. Future plan
4. Answers to questions
The total duration of the webinar is approximately 1.5 hours.
SecurityLab, [24.11.20 09:25]
Security researchers analyzed 11 low-cost video doorbells sold on online trading platforms such as Amazon and eBay, and identified many vulnerabilities in each device.
The most dangerous problem was the practice of some devices to send Wi-Fi network names, passwords, location information, photos, videos, email and other data to the manufacturer without any obvious reason.
https://www.securitylab.ru/news/514272.php
SecurityLab, [24.11.20 10:20]
Cybercriminals targeted users of the Spotify music service using credential stuffing attacks.
https://www.securitylab.ru/news/514276.php
SecurityLab, [24.11.20 10:25]
The App “public Services” is now available for download in the App Store and Google Play Store.
“COVID tracker”, which allows you to track contacts with patients with coronavirus infection (COVID-19).
https://www.securitylab.ru/news/514277.php
SecurityLab, [24.11.20 11:10]
The State Duma of the Russian Federation has introduced a bill on penalties for Telecom operators who did not use equipment for stable Internet operation on the territory of Russia.
The bill was introduced by the head of the state Duma Committee on information policy, information technologies and communications Alexander Khinshtein and his first Deputy Sergey Boyarsky.
https://www.securitylab.ru/news/514281.php
SecurityLab,[24.11.20 17:49]
The developers of the Chinese App TikTok fixed two vulnerabilities that could allow attackers to take control of accounts with a single click.
German security researcher Mohammad Taskiran discovered a vulnerability in reflected cross-site scripting (XSS) in the TikTok URL parameter, reflecting its value without proper cleaning.
The problem could also lead to data leaks during fuzzing of the company’s domains tiktok.com and m.tiktok.com.
The expert also found that the TikTok API endpoint is vulnerable to cross-site request forgery (CSRF) attacks that allow you to change the passwords of user accounts registered using third-party applications.
https://www.securitylab.ru/news/514308.php
SecurityLab, [24.11.20 18:05]
Communication between a machine and a person always happened without humor.
However, this rule will soon cease to apply.
Chinese experts have developed a new technology that will help AI (artificial intelligence) to learn to recognize sarcasm in people’s statements.
Sarcasm is one of the most difficult forms of human expression, and therefore one of the most difficult to teach systems.
Scientists were able to detect this unique human linguistic trait in spoken or written conversation.
https://www.securitylab.ru/news/514318.php
SecurityLab, [24.11.20 20:25]
The Santa Clara County, California, district attorney’s office said a Grand jury has indicted Apple Security Chief Thomas Moyer and two Sheriff’s deputies on bribery charges.
https://www.securitylab.ru/news/514322.php
SecurityLab, [24.11.20 20:52]
The Moscow mayor’s office will develop a system that will collect a detailed “digital profile” of users of all city services and will be able to study the activity of Muscovites in individual districts and “city objects”.
The “enriched profile” of the user will include data on debts and fines, information about the travel document and social card.
The system will compare this with information from public Wi-Fi access points and from operators, track “territorial bans” and “medical violations”, and also take into account data from social surveys in the context of individual districts of the city.
The announced tender implies a large-scale expansion of the ability to collect information about residents, according to the procurement documentation.
The stated goal of the revision is to “create tools for continuous monitoring of user activity in the territories and objects of the city of Moscow”, including the development of “activity profiles by activity areas”,” rapid identification of emerging trends”,” obtaining detailed Analytics and integrated indicators for various areas of user activity” and “the ability to quickly respond to changes in the situation in the city”.
As the documentation emphasizes, all collected data is depersonalized and linked to a unique profile identifier that does not contain such data as Full Name or place of birth.
The data enrichment module will provide “comparison and linking” of data from basic profiles of Muscovites with data from Wi-Fi sessions in public transport, permissions for access to territories or objects, requests and results of social surveys on health, education, housing and public transport, as well as requests related to personal vehicles and participation in city events.
https://www.securitylab.ru/news/514323.php
SecurityLab, [25.11.20 08:10]
Security researchers of the information security company Digital Defense have discovered a serious vulnerability in the cPanel site management software, which is very popular with hosting companies.
With its help, an attacker can bypass the two-factor authentication mechanism implemented in cPanel to protect accounts.
https://www.securitylab.ru/news/514325.php
SecurityLab, [25.11.20 08:25]
The Baidu Maps and Baidu Search Box apps have a problem with collecting sensitive data.
https://www.securitylab.ru/news/514326.php
SecurityLab, [25.11.20 09:50]
The Hi-Tech Crime Trends 2020-2021 report explores various aspects of the functioning of the cybercrime industry, analyzes attacks and predicts changes in the threat landscape for various sectors of the economy: financial, telecommunications, retail, manufacturing, and energy.
The authors of the report also analyze campaigns launched against critical infrastructure objects, which are increasingly becoming a target for the special services of different States.
https://www.securitylab.ru/news/514328.php
SecurityLab, [25.11.20 10:15]
During the NATO cyber exercise in Estonia on November 16-20, experts practiced catching government-funded hackers using specially placed traps.
https://www.securitylab.ru/news/514329.php
SecurityLab, [25.11.20 11:43]
[Forwarded from the Announcements of the best information security events]
Intensive workshop ” cybersecurity: Level 0»
we invite you (https://is.gd/yEa5PM) get acquainted with the work of the security team at the intensive ” cybersecurity: level 0»
In 3 days of video conferences with an experienced information security specialist, you will:
— Understand the main tasks of the Blue Team and set up your own system for detecting incidents
-Learn how to successfully apply the skills of building a security system
— Meet the experts and HackerU company
– Pass the first labs and tests, evaluating your strength for the start of a large program
The cost of an intensive course with an expert in December is only 2300 RUB
Have time to get into the group and record right now.
SecurityLab, [25.11.20 17:18]
Employees of the Moscow criminal investigation Department, together with colleagues from the Central district of the capital, stopped the activities of a group that remotely stole money from citizens’ accounts using social engineering.
As the press service of the interior Ministry, the attackers acted in the following way:
- call the clients and posing as employees of the security service of financial-credit institution
- informed them that their Bank card has been hacked
- Then the scammers offered to block it, and asked to dictate the card number and codes that came in SMS messages
- After receiving all the necessary data, the attackers registered other people’s cards in the contactless payment system on their mobile phones and used money.
- In total, the fraudsters caused damage in excess of 12 million rubles.
https://www.securitylab.ru/news/514354.php
SecurityLab, [25.11.20 17:33]
A national quantum laboratory will be built in Russia as part of a Federal project aimed at developing quantum technologies, Ruslan Yunusov, head of the project office for quantum technologies at Rosatom state Corporation, told reporters at a press conference on November 25.
The new structure will combine the efforts and resources of key universities, research centers, technology companies, financial organizations, startups and development teams in the field of creating quantum computers.
Participants of the consortium will develop the necessary infrastructure for carrying out work in the field of quantum computing, as well as provide training.
https://www.securitylab.ru/news/514355.php
SecurityLab, [26.11.20 07:22]
[Forwarded from the Announcements of the best information security events]
Solar inRights 3.0 Working with SOD conflicts
Segregation of duties (SOD) is one of the key elements of proper risk management and internal control for a business. The point of this approach is to distribute highly critical processes and functions among several individuals or departments, so that staff in the performance of their official duties will not be able to commit and hide mistakes or fraud.
However, in practice, for a number of reasons, it is not always possible to avoid conflicts of authority. in this case, mechanisms for early warning of conflicts and timely and correct response to them are especially important for the company’s sustainable operation.
On December 8, Rostelecom-Solar experts will tell and show in practice how Solar inRights controls SOD conflicts, ensuring the security of the organization’s business processes.
The webinar will be of interest to specialists of information security and it departments of companies from the industries of online retail, financial services, logistics, production, mining and processing of minerals.
The program of the webinar:
1. Overview of approaches to the division of responsibilities of employees.
2. Overview of the risks of SOD conflicts.
3. Demonstration of working with sod conflicts of the Solar inRights IGA system.
4. Answers to questions.
Your questions will be answered:
* Viktor Eremin-head of the Solar inRights implementation Department.
* Lyudmila Sevastyanova-promotion Manager for Solar inRights.
The total duration of the webinar is approximately 1 hour.
We are waiting for you at the webinar!
SecurityLab, [26.11.20 08:10]
A free temporary fix for the local privilege escalation vulnerability in Windows 7 and Server 2008 R2 is now available on the 0patch platform.
All devices that participate in the Microsoft extended Security Updates (ESU) program are vulnerable, so their administrators are recommended to install the patch from 0patch until Microsoft releases an official update.
Users who do not participate in the ESU program are also recommended to install the patch from 0patch.
https://www.securitylab.ru/news/514363.php
SecurityLab, [26.11.20 10:15]
Security researcher Joe Slovik from DomainTools called on Western information security specialists to more closely monitor cyber operations related to local conflicts in regions that usually do not attract attention in the United States and Europe.
According to the expert, this will help you better prepare for potential attacks.
https://www.securitylab.ru/news/514366.php
SecurityLab, [26.11.20 13:29]
Facebook has paid a fine of 4 million rubles for violating the law on personal data protection.
The tech giant did not provide information about the localization of databases of Russian users.
“The fine has been paid, the court has received an order to end the enforcement proceedings,” the spokeswoman said.
https://www.securitylab.ru/news/514375.php
SecurityLab, [26.11.20 13:35]
Microsoft has added new features to Office Suite 365 that allow organizations to monitor the actions of their employees.
https://www.securitylab.ru/news/514365.php
SecurityLab, [26.11.20 15:35]
In a joint operation between Interpol, Group-IB and law enforcement agencies in Nigeria, a major cybercrime group was eliminated.
In particular, three local residents were arrested on the territory of Nigeria, suspected of participating in a large organized criminal group that distributes malware, sends phishing emails and INTERNET attacks.
https://www.securitylab.ru/news/514391.php
SecurityLab, [26.11.20 19:42]
In the closed beta version of iOS, experts have discovered a feature that prompts the user to install third-party apps when the iPhone is first launched.
This option will allow Apple to meet the requirements of the law on pre-installation of Russian software for the sale of smartphones in our country.
But there is still an open question about the Mir payment system’s access to the contactless payment module in the iPhone. Apple still doesn’t allow third-party payment systems to be installed on its products. But experts believe that everything will change soon, since any foreign operator, including Apple, is interested in operating its own payment systems on the territory of the Russian Federation.
https://www.securitylab.ru/news/514393.php
SecurityLab, [27.11.20 08:10]
Last weekend, one of the hacker forums published exploits for vulnerabilities in Fortinet VPN devices (CVE-2018-13379) and IP addresses of about 50.000 vulnerable devices belonging to large banks, telecommunications companies and government organizations around the world.
At the time, the cybercriminal who published them claimed that he also had credentials for these vulnerable devices, and now he has put them in the public domain.
https://www.securitylab.ru/news/514394.php
SecurityLab, [27.11.20 08:20]
The EU has proposed new rules allowing companies to access public and personal data so they can compete with American and Asian giants.
The rules are also intended to encourage innovation in areas such as climate change and health.
Details: The European Union has proposed
“The economic and societal potential of data use is enormous: it can enable new products and services based on novel technologies, make production more efficient, and provide tools for combatting societal challenges. In the area of health for example, data contributes to providing better healthcare, improving personalised treatments and helping cure rare or chronic diseases.” (src)
(in other words: BigPharma would like to know more about “the market” and where to make most money)
new rules allowing companies to access public and personal data so that they can compete with American and Asian giants.
The rules are also designed to encourage innovation in areas such as climate change and public health.
Businesses and research organizations will be given access to data that is usually blocked due to privacy, commercial confidentiality, or intellectual property rights.
The rules of the General Data Protection Regulation (GDPR) will still apply, and companies and government agencies will need to implement technical solutions to ensure confidentiality.
For example, personal data must be kept anonymous before companies can be granted access.
According to the European Commission, providing companies with access to more data will support businesses in creating new services and products, as well as help researchers solve social problems.
Under the new proposals, companies will not be required to have their headquarters in Europe or store data in the region, but they will have to appoint local representatives to participate in the program. (wtf? as soon as data is stored outside of the EU, EU-DataProtection laws DO NOT APPLY ANYMORE!? DOES NOT MAKE ANY SENSE WHATSOEVER! making the GDPR basically a very annoying time consuming “yes you can have my cookie” joke)
https://www.securitylab.ru/news/514395.php
SecurityLab, [27.11.20 13:55]
Personal and medical data of more than 16 million Brazilians infected with COVID-19 leaked Online after a hospital employee uploaded spreadsheets with user names, passwords and access keys to the systems of the Brazilian Ministry of health to GitHub.
https://www.securitylab.ru/news/514404.php
SecurityLab, [27.11.20 15:20]
Hackers, presumably from North Korea, tried to hack the systems of the British drug manufacturer AstraZeneca, which is developing a vaccine for coronavirus infection (COVID-19).
This was reported to the Reuters news Agency by two knowledgeable sources.
https://www.securitylab.ru/news/514408.php
SecurityLab, [27.11.20 20:06]
[Forwarded from Announcements of the best is events]
” DevSecOps: implementation in the product pipeline and operation of PT Application Inspector»
The webinar will be held on December 3 at 14: 00.
Positive Technologies invites you to take part in the webinar “DevSecOps: introduction to the product pipeline and operation of PT Application Inspector”, which will be held on December 3 from 14:00 to 15:00 (Moscow time).
Positive Technologies experts will tell you how to deploy and operate the PT Application Inspector security analyzer in the Assembly line, taking into account the specifics of the corporate infrastructure.
You will learn about what PT Application Inspector can do “out of the box”, how to integrate it into development processes, and how to use the results of scanning through PT AI to improve the security of the product being developed. Experts will explain how to prepare the application Inspector Enterprise (AIE) server part and how to conveniently configure interaction with the server using the Aisa client utility.they will also give recommendations for DevSecOps engineers on working with AIE and AISA.
The webinar will be useful for CI engineers, infrastructure engineers, security specialists, and anyone interested in DevSecOps. Especially for those who are already implementing PT Application Inspector in the existing infrastructure and development processes.
To participate, you need to register (https://www.ptsecurity.com/ru-ru/research/webinar/devsecops-vnedrenie-v-produktovyj-konvejer-i-ehkspluataciya-pt-application-inspector/?utm_source=SecLab&utm_medium=news&utm_campaign=webinar03122020). Registration ends on December 3 at 12: 00. The viewing link will be sent to all registered participants half an hour before the start of the webinar.
SecurityLab, [28.11.20 13:05]
The world risks plunging into “CyberChaos” without universal agreements in the field of information security, Russian foreign Minister Sergey Lavrov said, speaking at a meeting of the boards of the ministries of foreign Affairs of the Russian Federation and Belarus.
https://www.securitylab.ru/news/514413.php
SecurityLab, [30.11.20 07:41]
[Forwarded from the Announcements of the best information security events]
December 2, 16: 00
Protect your Microsoft 365 email from complex threats
We continue our series of webinars (https://events.webinar.ru/jet/cloudsecurity0212), dedicated to the topic of Cloud Security, this time experts from jet Infosystems and Cisco will talk about the possibilities of protecting Microsoft 365 email from complex threats. At the online event, you will learn about the features of using Microsoft 365 cloud services and solutions for their protection. At the end, everyone will be waiting for a live demo of the Cisco Mailbox Defense solution.
Questions for discussion:
⁉ app The popularity and vulnerability of cloud-based e-mail. How do hacks most often start?
⁉ ️ a basic Set of built-in Microsoft 365 security tools. Enough or not?
⁉ app How to gain control over internal and external correspondence, without interrupting the delivery of messages?
Who will benefit:
📍 information security professionals who are looking for tools to improve mail security in the Microsoft 365 cloud
📍 Heads of it departments considering the use of cloud email
SecurityLab, [30.11.20 08:10]
At a closed Russian-language cybercrime forum https://Exploit.in access to hundreds of company Directors’ email accounts around the world is for sale.
According to ZDNet, combinations of usernames and passwords of Office 365 and Microsoft users are put up for sale, according to the seller, belonging to the presidents of companies, their assistants and deputies, as well as General, Executive, financial and technical Directors, accountants, etc.
The cost of access ranges from $100 to $1500 per account, depending on the size of the company and the user’s position.
https://www.securitylab.ru/news/514419.php
SecurityLab, [30.11.20 10:30]
The attackers organized a large-scale phishing campaign, in which they use Oracle and Amazon cloud services to steal the credentials of Office 365 users in the United States and Australia.
The malicious campaign has been active for more than six months and uses a network of legitimate websites that have been compromised to act as a proxy chain.
https://www.securitylab.ru/news/514425.php
SecurityLab, [30.11.20 11:25]
Representatives of the Russian Union of Industrialists and entrepreneurs (RSPP) consider it impossible to switch to domestic software from 2024, and to Russian equipment from 2025.
According to experts, the process will require a lot of money, and it is necessary to change the equipment gradually, taking into account the wear and tear of the existing one.
https://www.securitylab.ru/news/514427.php
SecurityLab, [30.11.20 12:25]
A cybercrime group that “robbed” at least 35 ATMs belonging to Italian banks has been liquidated in Italy.
With the help of the black box attack, in just seven months, the attackers stole about 800,000€.
https://www.securitylab.ru/news/514431.php
SecurityLab, [30.11.20 15:00]
Microsoft is developing a new software solution that allows you to run Android applications on the Windows 10 operating system.
The project, called “Latte”, will allow you to port Android apps to Windows 10 without any changes in the code, packaging them as MSIX, and publish them to the Microsoft Store.
This was reported by sources of the Windows Central resource.
https://www.securitylab.ru/news/514449.php
SecurityLab, [30.11.20 15:50]
On Monday, November 30, experts from the David Ben-Gurion University in the Negev (Israel) presented a new attack that can bring biological warfare methods to a new level.
Details: The attack presented by the researchers allows scientists working with DNA to inadvertently create dangerous viruses.
On Monday, November 30, specialists of the David Ben-Gurion University in the Negev (Israel) presented a new attack that can bring the methods of conducting biological warfare to a new level.
The attack presented by the researchers allows biotechnologists working with DNA to inadvertently create dangerous viruses and toxins.
According to them, now, when the whole world is busy developing vaccines against coronavirus, attackers do not need to be near them to interact with dangerous substances and viruses.
They can create toxins or synthetic viruses by unsuspecting scientists using targeted cyberattacks.
Researchers have described how a malware on the computer of the biotechnology, the attacker can substitute the chain for DNA sequencing.
In particular, vulnerabilities in the systems “screening Guidelines for synthetic double-stranded DNA providers” and “Harmonized screening Protocol 2.0 “allow” circumventing the protocols with a common obfuscation procedure”.
According to the instructions of the US-Department of health and human services, when making a gene sequence in the process of DNA sequencing, special screening protocols must be followed to identify potentially dangerous DNA.
However, the researchers managed to circumvent these protocols by using obfuscation, resulting in 16 of the 50 obfuscated DNA images not being detected by “best match DNA screening”.
The software used to develop and manage synthetic DNA projects is also vulnerable to “human in the browser” attacks.
With these attacks, attackers can insert arbitrary strands of DNA into gene sequences – what researchers have called a “cross-cutting cyberbiological attack.”
To demonstrate the possibility of their attack, the researchers cited the remainder of the Cas9 protein, using malware to convert this sequence into active pathogens.
According to scientists, using CRISPR protocols, the Cas9 protein can be used to “deobfuscate harmful DNA in host cells.”
For an unsuspecting scientist processing the sequence, this could mean accidentally creating dangerous substances, including synthetic viruses or toxins.
https://www.securitylab.ru/news/514450.php
SecurityLab, [30.11.20 17:50]
🔥 What other security channels to read in Telegram
@Haccking – The one! About information security, hacking, protection from hacker attacks. IT technologies. Kali Linux. PC hacking / protection, WiFi hacking / protection.
Codeby reading room (https://t.me/sudolib), make yourself comfortable and let’s get started. Codebay library – books on Information security https://t.me/sudolib
Information leakage (https://t.me/dataleak) – daily analysis of leaks, monitoring the darknet. The channel that each security guard should subscribe to: https://t.me/dataleak
Hacker’s library (https://t.me/hackerlib) – a channel that contains the best books and courses on information security, programming, and ethical hacking. https://t.me/hackerlib
@vschannel (https://t.me/vschannel/903) – Dmitry Momot’s channel (aka VektorT13). He talks about the unique, antigamente, methods of tracking, anti-fraud system, the fingerprint of the browser, iron, and operating system.
SecurityLab, [01.12.20 08:05]
Codes of banking SOFTWARE used by national Central banks of different countries were published in open repositories.
As reported on the Bank Security Twitter channel dedicated to security threats in the banking sector, the leaked code was developed by CMA, a company specializing in creating SOFTWARE for banks and stock exchanges.
Details:
Codes of banking SOFTWARE used by National Central banks of different countries were published in open repositories.
As reported on the Bank Security Twitter channel dedicated to security threats in the banking sector, the leaked code was developed by CMA, a company specializing in creating SOFTWARE for banks and stock exchanges.
The dump mainly contains the code of the CMA’s DEPO/X custody solution, which, according to the description on the company’s official website, has “rich functionality that allows eliminating financial and operational risks and improving the efficiency of the capital markets infrastructure”.
The solution is used by more than 20 organizations around the world, including Central banks, Central/national depositories and stock exchanges.
According to Bank Security’s Twitter feed, more than $100 billion passes through the CMA’s software every day.
It is not specified where the codes were published or how the leak occurred.
Recall that about a month ago, the code of a popular set of tools for testing for penetration of Cobalt Strike leaked to the Network.
On the GitHub platform, a repository was created containing the source code of version Cobalt Strike 4.0.
According to the file src/main/resources/about.html, the source code was released on December 5, 2019.
https://www.securitylab.ru/news/514453.php
SecurityLab, [01.12.20 09:35]
More than fifty computer networks in North America, which had been dormant for a long time, suddenly resumed activity.
https://www.securitylab.ru/news/514461.php
SecurityLab, [01.12.20 11:55]
Credit card skimmer operators have started using an innovative technique to implement plausible PayPal frames and hack the checkout process in compromised online stores.
Hackers steal payment and personal information provided by customers on hacked e-Commerce sites and send it to remote servers under their control.
https://www.securitylab.ru/news/514462.php
SecurityLab, [01.12.20 12:00]
The British counterintelligence service MI5 hid important information from the home Secretary when it sent requests to collect phone and Internet data.
As reported by ComputerWeekly, the organizations Privacy International and Liberty accuse the security service of not providing details about serious problems with compliance with the law regarding the storage and deletion of surveillance data stored in its IT systems.
https://www.securitylab.ru/news/514472.php
SecurityLab, [01.12.20 15:30]
A member of a “hacker collective” that threatened to blow up dozens of schools in the US and UK has been sentenced to eight years in prison.
https://www.securitylab.ru/news/514488.php
SecurityLab, [01.12.20 20:23]
Can a cyber attack seriously affect the business?
We are interested to know the opinion of the IT and information security audience: is it possible to cause serious and even irreparable damage to business as a result of a cyber attack, or can this risk be considered exaggerated?
Share your opinion by answering a few questions anonymously.
https://ru.research.net/r/2G739KG
SecurityLab, [02.12.20 08:40]
Microsoft will make changes to its new Microsoft Productivity Score tool in response to recent complaints about user privacy violations.
In its blog, the company talked about the planned innovations, and at the same time explained how its new tool for collecting telemetry guarantees the privacy of users.
https://www.securitylab.ru/news/514494.php
SecurityLab, [02.12.20 09:20]
It is generally assumed that the Tor browser is used mainly for accessing the darknet, including illegal content.
However, according to a study published in the journal Proceedings of the National Academy of Sciences, things are very different:
- only a small percentage of the total time spent working with Tor is spent visiting sites on the darknet.
- Details:
- In democratic countries, Tor is more often used to access forbidden content
- and in countries with restrictions, it is used to circumvent censorship.
- It is generally assumed that the Tor browser is mainly used to access the darknet, including illegal content.
- However, according to a study published in the journal Proceedings of the National Academy of Sciences, things are quite different-only a small percentage of all the time you work with Tor is spent visiting sites on the darknet.
- For eight months, researchers tracked a small portion of users of the anonymous browser.
- Since Tor does not allow you to find out the real history of visits, these visits were divided into two categories:
- legitimate resources including social networks
- underground sites on the darknet
- As it turned out, visiting sites on the darknet accounts for only 6.7% of the total time spent in the browser. (so 93.3% of all Tor Browser users use TOR for legitimite privacy reasons during every-day tasks and research)
- It is also worth noting that not all deep-web sites contain illegal content
- According to the study, illegal resources are visited more often in democratic countries than in countries with a totalitarian regime
- For example, in democratic countries, visiting illegal resources accounts for 7.8% of all time on Tor, while in countries that restrict users’ freedom on the Internet – only 4.8%.
- In other words, residents of democratic States are more likely to use anonymizers to access prohibited content, and in countries with restrictions, users turn to Tor to circumvent censorship and visit legitimate sites that are banned in some territories (for example, Facebook in China).
- thank’s a lot. There are also legitimate usages of TOR in democracies.
https://www.securitylab.ru/news/514495.php
SecurityLab, [02.12.20 10:09]
[Forwarded from the Announcements of the best information security events]
We invite you to get acquainted with the attacking side of the IB at the intensive ” Pentesting: Level 0»
Learn how to apply pentest skills successfully in your work.
In 3 days of video conferences with an experienced pentester, you will:
— Understand the main tasks of the Red Team and conduct the first hacking of the web application
-Learn how to successfully apply the skills of pentest in your work
— Meet the experts and HackerU company
– Pass the CTF and evaluate your strength for the start of a large program
The cost of an intensive course with an expert in December is only 2300 RUB
Join the group in time and follow the link right now: https://is.gd/ypIov0
SecurityLab, [02.12.20 14:25]
More than half of the most recently uploaded images in Docker Hub contain vulnerabilities “inherited” from outdated SOFTWARE, (so not un purpose, but because the images never received updates, another massive missconception in the docker system, which is kind of a good idea, but pisses so many people off vs “real” virtualization, there needs to be some form of automatic “rebuild and publish” mechanism to keep docker images up to date)
while thousands of images are tools for attacks or other dangerous SOFTWARE.
This is the conclusion reached by the specialists of the Prevasio information security company, who analyzed 4 million images in Docker Hub.
https://www.securitylab.ru/news/514517.php
SecurityLab, [02.12.20 14:30]
Specialists of the Sonatype information security company found malicious nmp packages that install the njrat remote access Trojan on users ‘ computers.
https://www.securitylab.ru/news/514500.php
(never trust any manually downloaded packages or obscure repositories)
(it really pisses one off, that sysbench is not (anymore) in the official debian repositories)
SecurityLab, [02.12.20 15:15]
Security researchers from the Austrian company SEC Consult told about a dangerous vulnerability in the tool for deploying devices in corporate networks Microsoft Autopilot,
the operation of which allows you to intercept control over a computer system.
Representatives of Microsoft deny the existence of this problem.
(always “the best solution”, instead of addressing a problem and actually solving it, to simply ignore it until the problem is so big, that it can not be ignored anymore)
https://www.securitylab.ru/news/514522.php
SecurityLab, [02.12.20 16:08]
The bill on retaliatory sanctions for censorship against Russian media suggests blocking YouTube only as an extreme measure as an element of deterrence, but this is a poorly implemented construction, said one of the authors of the project – the head of the state Duma Committee on information policy Alexander Khinshtein.
Earlier, the state Duma introduced a bill on retaliatory sanctions against Internet platforms for censorship against Russian media.
The measures will include blocking, slowing down traffic, and administrative fines.
(so on on cyber battleground betwen hostile nations (the solution would be to end the hostilities and drink tee and make friends) hackers & lawyers profit most)
As Hinstein has already explained, the bill “theoretically allows” to block YouTube, but hopes that the situation with blocking the service on the territory of the Russian Federation will not happen. (yep that would also piss of loads of Russians (no free western music and funny videos anymore), unless all of Youtube’s content get’s mirrored regularly on a Russian-Copy-Of-Youtube, like rutube.ru)
https://www.securitylab.ru/news/514524.php
SecurityLab, [03.12.20 08:25]
NSS Labs may have ceased operations on October 15 this year, but its previously unpublished testing data will now be used in a new organization created by former CEO Vikram Phatak.
This was reported by the dark Reading resource.
https://www.securitylab.ru/news/514528.php
SecurityLab, [03.12.20 09:15]
“Positive Technologies” invites you to take part in the webinar “Following the Standoff: investigating successful attacks on the city”, which will be held on December 10 from 14:00 to 15:00 (Moscow time).
https://www.securitylab.ru/news/514529.php
(wow it took one “only” like 4hours to process all of this info… thanks for tuning in.)
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!