it might be the biggest “cyber” story of the year 2024 already: buy this guy MANY MANY COFFEES! he spotted the problem via know how but also luck 😀
- it was a VERY VERY LONG and WILD COMPLEX and HIGHLY SOPHISTICATED (OBFUSCATED) OPERATION
- it was spotted completely by accident from am M$ developer (?) 😀 (thanks M$ for hiring such people! 🙂
- bad actor (possible a state sponsored actor) with pseudonyms “Jigar Kumar” “Jia Tan” found a burned out open source maintainer-developer and offered to help
- https://www.mail-archive.com/xz-devel@tukaani.org/msg00566.html
possible solutions:
- mankind really has to
- value the value of Open Source
- get organized to avoid such problems in the future
- the “multi eye ball” principle worked in this case but more or less by accident, because the attack was sophisticated, long-term and highly obfuscated
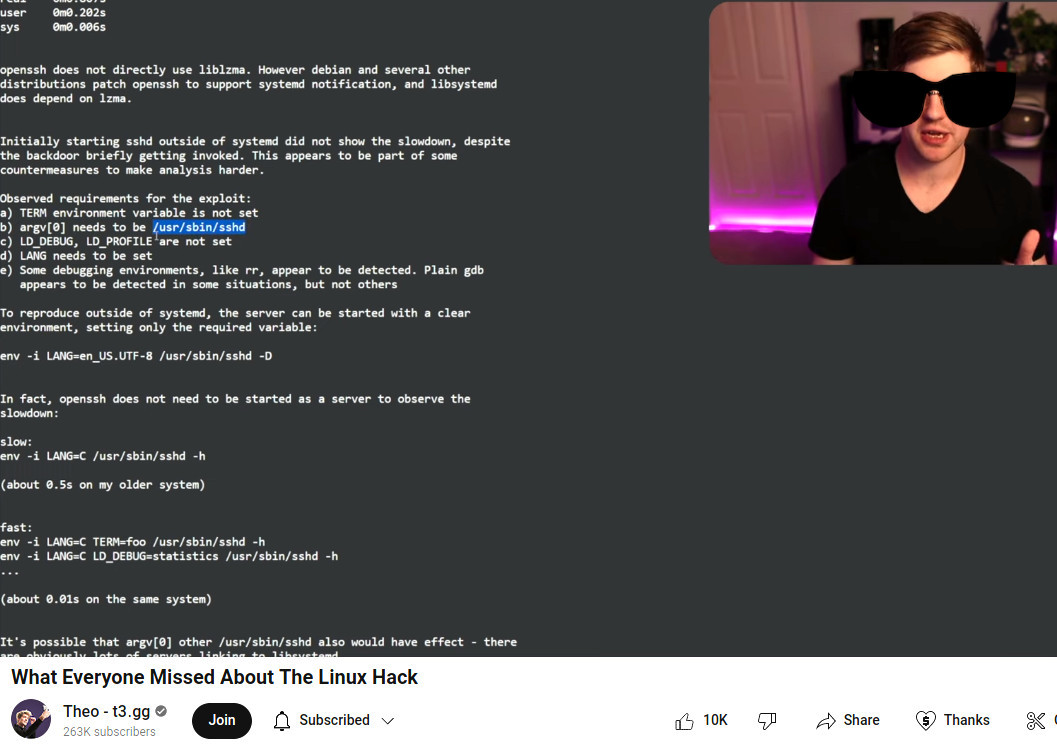
how to manually start sshd:
hostnamectl; # tested on Operating System: Debian GNU/Linux 12 (bookworm) Kernel: Linux 6.1.0-18-amd64 Architecture: x86-64 service ssh stop mkdir /run/sshd; time env -i LANG=C /usr/sbin/sshd -h /etc/ssh/ssh_host_ed25519_key; real 0m0.006s ps uax|grep ssh killall sshd mkdir /run/sshd; time env -i LANG=C TERM=bla /usr/sbin/sshd -h /etc/ssh/ssh_host_ed25519_key; real 0m0.006s ps uax|grep ssh killall sshd
Links:
“In the cybersecurity world, a database engineer inadvertently finding a backdoor in a core Linux feature is a little like a bakery worker who smells a freshly baked loaf of bread, senses something is off and correctly deduces that someone has tampered with the entire global yeast supply.”
- “Andre’s friend discovers hacker attack This Berliner (38) has saved the Internet” (src)
- very detailed info on how this backdoor “at some point an .o file is extracted and weaved into the compilation/linking process”
- the CVE-2024-3094 story is EVERYWHERE
- https://robmensching.com/blog/posts/2024/03/30/a-microcosm-of-the-interactions-in-open-source-projects/
- https://tukaani.org/xz-backdoor/
- https://git.tukaani.org
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!