warning: no guarantee of completeness! contains ads! (but owner of blog get’s nothing, maybe source of source does)
Are the odds against the (itsec) defenders?
It certainly feels that way, because no human can ever find all bugs, so Fuzzing and AI is employed… there is and never was and never will be 100% it security.
Up to now, the “problems” could be mitigated in the sense of: the essential (internet) based services civilization partly but ever increasingly depends on, kept running (thus it would be UTTER STUPIDITY to give up “offline” for “online” aka cash for e-Dollars and e-Euros and e-Somethings, without any paper-fallback-backup)
What this means: companies need to be able to also work offline and even test that scenario of pulling “the internet” plug for a week, provide alternative ways (send (encrypted?) CD-R and usb stick per postal?, a fax machine?) of conducting business and meassure those fallback-tests to see what happens: are parts of the company completely incapable of operating and how to fix it?
worst case: AI finds and exploits security holes faster than anyone can fix ’em
AI amok: how AIs almost crashed wallstreet
“In 2010” “70% of all trading activity was completely automated”
“May 6, 2010” “In just 15 minutes from 2:45 pm, the Dow Jones plunged by almost -9%”
“Hundreds of billions of dollars were wiped off the face value of famous companies in the S&P 500. Stocks in some companies were trading for a single cent.
Almost as soon as the sleepless Wall Street traders had time to adjust to the nightmare scenario unfolding in front of them, the market began to rebound. Within another fifteen minutes, almost all of the losses had been recovered.”
“Nothing of value was created or destroyed in the what became known as the ‘flash crash'”
“how vulnerable and chaotic the (financial) system is”
“sheer density of automated traders and algorithms that control these financial markets”
(“control” or “out of control”? in the end: those AIs shall not be allowed to operate without strict human (!) supervision)
(everyone should now, that the root cause of the economically devastating 1929 god damn wall street (banks!) crash was “fanatic” believe that stocks will rise forever and thus too much speculation was done by basically everyone, consequences of that greed: massive unemployment = massive riots unrest and problems. private sector screws up and expects the gov to fix it (many many times))
(src: singularityhub.com)
“The crash followed a speculative boom that had taken hold in the late 1920s. During the latter half of the 1920s, steel production, building construction, retail turnover, automobiles registered, and even railway receipts advanced from record to record.” “led hundreds of thousands of Americans to invest heavily in the stock market. A significant number of them were borrowing money to buy more stocks” (src: wikipedia.org)
So just as in it-systems, financial systems SHOULD have security and stability (!) meassures in place (what about financial “firewalls” and “backups”? (cash & bitcoin?), only heard of financial “bazookas” that get fired at financial problems on almost a regular basis).
sometimes the warnings in scifi are true:
back to itsec:
SecurityLab, [01.02.21 14:08]
Inventor and businessman Elon Musk spoke about the successful implantation of the Neuralink chip into the brain of a live monkey, Bloomberg reports.
The Neuralink project has a monkey with a wireless implant in the skull with small wires. The primate is able to play video games with the help of his mind. As Musk noted, the animal feels great and is “happy.”
https://www.securitylab.ru/news/516112.php
comment: … yes that is true, but all the monkey (currently) “only” can do, is move a mouse cursor and play pong
for further integration (not only muscle sensors), there will have to be significant more science to be done aka “connect the internet to the brain”.
well right now all that is possible is move the mouse pointer… that’s about it.
SecurityLab, [01.02.21 16:25]
Students of the Canadian State Research University McMaster opposed the use of a remote control system for exams based on artificial intelligence.
In their opinion, the control system to ensure that students do not cheat on online exams violates the confidentiality of their data.
We are talking about the systems used by the American company Respondus, which evaluates the quality of education.
Last September, McMaster University signed a one-year contract with Respondus.
The company uses two different programs to analyze anomalies in biometric data sets and create so-called “suspicion reports”.
These reports are subsequently transmitted to the university, and with their help, the administration of the educational institution can identify possible cases of academic fraud.
https://www.securitylab.ru/news/516120.php
SecurityLab, [01.02.21 17:46]
Editor-in-Chief Securitylab.ru Alexander Antipov studies important IT news every week, which helps to better understand current trends and prepare for current threats.
In this issue:
Hackers were able to attack the IB vendor SonicWall through a 0-day vulnerability in its own VPN products
North Korean hackers pose as information security experts in social networks and spread malware
The company’s home security specialist spied on customers through hacked video cameras
Apple fixed three zero-day vulnerabilities in iOS, iPadOS and tvOS – they allowed for attacks like watering hole.
SecurityLab, [02.02.21 06:05]
The antivirus company ESET announced the disclosure by its experts of a new attack on the supply chain, the object of which was the mechanism for updating the popular application for gamers NoxPlayer. (run Android Apps on PC)
NoxPlayer is developed by BigNox from Hong Kong and is designed to run Android applications on computers running Windows and Mac operating systems.
The number of emulator users worldwide exceeds 150 million people.
“According to ESET telemetry, the first signs of compromise were recorded in September 2020.”
“Malicious activity continued until the moment of detection last week, which was also warned by BigNox,”
the company quoted ESET researcher Ignacio Sanmillan as saying.
https://www.securitylab.ru/news/516123.php
SecurityLab, [02.02.21 07:49]
[Forwarded from Announcements of the best IB events]
Positive Technologies invites you to the webinar “Increasing privileges in the system: detecting techniques using the example of PT Sandbox”
The webinar will take place on February 11 at 14:00.
Positive Technologies invites you to take part in the webinar “Increasing privileges in the system: detecting techniques using the example of PT Sandbox”, which will be held on February 11 from 14:00 to 15:00
(Moscow time).
In a cyberattack, executing malicious code is only half the battle. After successfully infecting the victim, the attackers still need to commit destructive actions and disguise themselves. There are not always rights to this.
Therefore, in the process of implementation into the infrastructure, attackers seek to increase privileges in the system. After all, the more opportunities there are, the easier it is to stay at the point of penetration and move further along the network.
Positive Technologies experts will tell you about the most interesting and common techniques for obtaining full control over the system in targeted attacks.
They will consider techniques for impersonating another user (impersonation), techniques for bypassing the Account Control component (UAC) and executing arbitrary code with maximum rights.
And most importantly, they will show you how to detect these actions in the PT Sandbox.
The webinar is useful for SOC practitioners, malware researchers, and PT Sandbox users.
Registration ends on February 11 at 12:00. The link for viewing will be sent half an hour before the start of the webinar to all registered participants.
SecurityLab, [02.02.21 08:25]
The manufacturer of firewalls and VPN solutions SonicWall confirmed the presence of a zero-day vulnerability in the SMA 100 series 10.x product code, while the company stated that firmware versions up to release 10 do not contain the vulnerability.
https://www.securitylab.ru/news/516129.php
SecurityLab, [02.02.21 09:25]
The confrontation between Facebook and Apple on the issue of collecting user data has received a new round.
The social network said that from now on it will specifically ask users to allow it to track their activity for advertising.
According to an updated Facebook blog post, for this purpose, a whole message will be displayed on the screens of users’ devices, in which the company will explain to them why it is so important to give it permission to collect data.
https://www.securitylab.ru/news/516131.php
SecurityLab, [02.02.21 10:25]
An unknown hacker hacked digital road signs in the British city of Burton-upon-Trent and posted a message on it so that all “idiots” would stay at home during quarantine.
https://www.securitylab.ru/news/516136.php
comment: X-D !!!
SecurityLab, [02.02.21 14:55]
Google has released a beta version of Chrome 89, which has received even more APIs for interacting with hardware, many of which Mozilla and Apple consider dangerous.
https://www.securitylab.ru/news/516141.php
SecurityLab, [02.02.21 15:25]
Russian President Vladimir Putin at a meeting via video link with the winners of the All-Russian competition “Teacher of the Year” said that he was extremely concerned about social networks.
https://www.securitylab.ru/news/516169.php
SecurityLab, [02.02.21 21:15]
Kobalos is interesting for several reasons.
Its codebase is very small, but complex enough to attack GNU Linux, BSD and Solaris.
Moreover, such complex code is a rarity for malware created under GNU Linux.
According to experts, Kobalos may also be suitable for attacks on AIX and Microsoft Windows.
Together with the computer security team of the European Organization for Nuclear Research (CERN),
ESET researchers have found that “unique multiplatform” malware attacks computing clusters (HPC).
In some cases, additional malware intercepted the SSH connection of the server in order to steal credentials with which attackers gained access to the HPC and deployed Kobalos.
The use of this infostiler partially explains how the malware spreads.
https://www.securitylab.ru/news/516170.php
“While the Kobalos design is complex, its functionalities are limited and almost entirely related to covert backdoor access. Once fully deployed, the malware gives access to the file system of the compromised system and enables access to a remote terminal that gives the attackers the ability to run arbitrary commands.”
SecurityLab, [03.02.21 07:30]
“Neuralink makes every effort to ensure the safety of implants, and is in close contact with the FDA (FDA).
If everything goes well, we will be able to conduct the first human trials at the end of this year,” Elon Musk said in response to a message from a user who proposed his candidacy for clinical trials of the implant.
https://www.securitylab.ru/news/516175.php
SecurityLab, [03.02.21 09:25]
90% of British and American office workers share personal and confidential information on social networks,
potentially exposing themselves and their organization to the risks of online fraud,
phishing and other cyber threats.
https://www.securitylab.ru/news/516179.php
SecurityLab, [03.02.21 10:35]
A hacker group, presumably from China, compromised the computer systems of a number of US agencies, using another vulnerability in the SolarWinds software, the Reuters news agency reported, citing anonymous sources.
https://www.securitylab.ru/news/516182.php
SecurityLab, [03.02.21 13:59]
[Forwarded from Announcements of the best IB events]
Where can I get practical skills in the field of cybersecurity in 2021?
At the intensive course “Cybersecurity: Level 0” (https://edu.hackeru.pro/cyberprof-intensiv-new?utm_source=seclab&utm_medium=promo&utm_campaign=int_cyber&utm_term=february) from HackerU, you will get the first knowledge about network attacks and real experience in preventing them, as well as understand the basic principles of building a protection system.
How is the training going?
– 3 days and 15 ak.hours with current information security specialists, including managers and SOC specialists
– Closed video conferences and the opportunity to get recordings of classes
– Unlimited communication and feedback from experts
– Only practice and analysis of real cases
After the intensive, you will be able to create test benches for security analysis, intercept and analyze network traffic, deploy a detection system, and much more.
In addition, you will receive a certificate and bonuses upon admission to any practical courses!
Sign up for intensive and take the first step towards a career in cybersecurity!
SecurityLab, [03.02.21 15:05]
The HarmonyOS operating system, developed by the Chinese tech giant Huawei, turned out to be a fork of Android and is practically no different from Google’s mobile operating system.
According to the editor of Ars Technica, Ron Amadeo, the OS is not an alternative at all, but just a careless fork of Android 10.
https://www.securitylab.ru/news/516202.php
SecurityLab, [03.02.21 17:50]
Roskomnadzor publishes a pyramid of modern interconnected network threats caused by the use of digital technologies at seven levels of the information space.
https://www.securitylab.ru/news/516212.php
SecurityLab, [03.02.21 22:00]
A new feature will appear on the TikTok social network to combat the spread of false or inaccurate information.
This was announced by the company’s product manager Gina Hernandez, according to the application’s website.
https://www.securitylab.ru/news/516213.php
SecurityLab, [04.02.21 07:55]
The paid version of the Microsoft Defender antivirus product,
Microsoft Defender Advanced Threat Protection (ATP),
has mistaken the latest Google Chrome update for Trojan software.
According to multiple messages on Twitter, after the release of Chrome v88.0.4324.146 on Wednesday, February 3, Defender ATP began to detect many update package files as a Funvalget backdoor Trojan (PHP/Funvalget.A).
https://www.securitylab.ru/news/516224.php
SecurityLab, [04.02.21 12:23]
The Ministry of Digital Development, Communications and Mass Communications has developed amendments to Article 63 “Communication Secrecy” of the law “On Communications”, which allow security forces to access information about the location of a particular subscriber from mobile operators without a court decision.
In addition to minor changes in the wording of existing provisions, a new paragraph number 5 is also added.
“Information used in means of communication that are not user equipment (terminal equipment), and containing data on the volume,
cost of communication services rendered,
as well as information of the radio-electronic means of the communication operator,
with which the subscriber’s user equipment is connected to the mobile radio-electronic communication network,
indicating the position of the subscriber’s user equipment relative to radio-electronic means,
may be transmitted without a court decision only at the request of the bodies carrying out operational investigative activities”, — it is reported in the document.
https://www.securitylab.ru/news/516235.php
SecurityLab, [04.02.21 16:15]
Hackers are trying to trick iPhone owners into installing a fake WhatsApp application in order to steal their data.
As the technical analysis of the application carried out by the specialists of Citizen Lab and Motherboard showed,
the Italian manufacturer of tools for collecting information intended for special services and law enforcement agencies is related to the creation of a malicious fake.
https://www.securitylab.ru/news/516243.php
SecurityLab, [04.02.21 19:14]
[Forwarded from SecurityLab.ru best materials]
On Friday afternoon, the buzzing of laptops is drowned out by rhythmic music from headphones connected to a smartphone. The hash found has not yet been hacked, and the computer where the whole process takes place has not been turned off since Tuesday morning. The second can of energy hit the edge of the trash can.
The ironed casual business suit that you are forced to wear begins to constrain your breathing, as disappointment arises inside. There are several hours left until the moment when you need to inform the client about the results of the work, but there is no desire to appear in the office before the task is completely solved.
Take a deep breath. It’s time to postpone work, go back to the beginning and try to look at the current situation from a new angle.
https://www.securitylab.ru/analytics/495617.php
SecurityLab, [05.02.21 07:42]
The US has begun to deploy its cyber units around the world.
They have already appeared in Montenegro, Northern Macedonia and Ukraine.
This was told by the deputy director of the National Coordination Center for Computer Incidents (NCCI) Nikolay Murashov.
“Under the pretext of protecting the elections with allied infrastructures,
American cyber units are currently being deployed around the world.
According to the official data of the military departments,
American cyber teams have deployed their specialists on the territory of Montenegro, Macedonia, Ukraine,” Murashov said.
https://www.securitylab.ru/news/516248.php
SecurityLab, [05.02.21 09:40]
The specialists of the Cisco Talos information security company managed to communicate with the LockBit ransomware operator,
who carried out all malicious operations alone.
The hacker spoke about his modus operandi (victims, tools, etc.) and what pushed him on the path of cybercrime.
In addition, he told about the difficult fate of a security researcher in his native country, which, according to Cisco Talos, is Russia.
https://www.securitylab.ru/news/516256.php
SecurityLab, [05.02.21 11:00]
The Ministry of Internal Affairs of the Russian Federation intends to make changes to its official mobile application and introduce an “Anti-fraud” module into it,
which allows users to recognize calls from fraudulent numbers.
https://www.securitylab.ru/news/516259.php
SecurityLab, [05.02.21 16:00]
Google is developing its own tracking protection feature for Android,
following Apple’s example.
Experts intend to limit data collection and tracking between applications in the OS,
but to do this is not as tough as in the case of Apple.
This was reported by Bloomberg.
https://www.securitylab.ru/news/516270.php
SecurityLab, [05.02.21 18:25]
Rajiv Kumar from India received a threatening email from a stranger on January 1.
Not understanding who he managed to cross the road to,
the man decided that professional hackers had paid attention to him,
who are now trying to blackmail him.
https://www.securitylab.ru/news/516274.php
SecurityLab, [06.02.21 07:15]
On Friday night, the Yandex.Maps service shows traffic congestion at the level of 10 points throughout Moscow.
At the same time, Google Maps has a much more familiar situation: roads are traditionally empty at night.
https://www.securitylab.ru/news/516282.php
SecurityLab, [06.02.21 10:25]
The creator of Telegram Pavel Durov asked the users of the messenger not to distribute the personal data of other people.
He also asked them not to call for violence.
“In recent weeks, we have blocked several channels that put the phone numbers and addresses of protest participants in Russia into public access,” the entrepreneur said.
https://www.securitylab.ru/news/516283.php
SecurityLab, [06.02.21 17:45]
Google has removed “The Great Suspender”, a popular Chrome extension used by millions of users (“suspending the tabs you aren’t using”)
from its Chrome online Store due to the fact that it contains malware.
Google also took the unusual step of disconnecting it from users’ computers.
https://www.securitylab.ru/news/516285.php
SecurityLab, [07.02.21 10:41]
A security researcher has discovered that a malicious extension for Chrome uses the synchronization function to communicate with a remote server of intruders.
Hackers can also steal the computer owner’s data.
“To download, read or delete these keys, the attacker only needed to log in with the same Google account,
but in a different Chrome browser (it could be a one-time account).
After that, he could interact with the Chrome browser on the victim’s network,
abusing Google’s infrastructure,” said Boyan Zdrnya at the Internet Storm Center forum.
https://www.securitylab.ru/news/516286.php
SecurityLab, [07.02.21 10:58]
The two largest Brazilian electric power companies Centrais Eletricas Brasileiras (Eletrobras) and Companhia Paranaense de Energia (Copel) have been subjected to cyber attacks using extortionate software.
Both companies are owned by the state, with Copel being the largest in the state of Paraná and Eletrobras being the largest electric power company in all of South America.
Eletrobras also owns a subsidiary of Eletronuclear, which is involved in the construction and operation of nuclear power plants.
As a result of cyber attacks, some operations of both companies were disrupted.
In addition, they had to shut down some of their systems, at least temporarily.
https://www.securitylab.ru/news/516288.php
SecurityLab, [07.02.21 14:20]
A resident of the capital appealed to law enforcement agencies after she lost a large sum of money.
This is reported by TASS, with reference to a source in the law enforcement agencies.
https://www.securitylab.ru/news/516289.php
SecurityLab, [08.02.21 07:45]
However, access to bitcoins could not be obtained, as the fraudster still refuses to provide information for accessing the wallet
https://www.securitylab.ru/news/516295.php
SecurityLab, [08.02.21 10:05]
The tension between Apple and Facebook over a new iOS feature called App Tracking Transparency is growing every day.
This feature will allow users to choose whether to allow applications to track their online activity, and Facebook is not satisfied with this state of affairs.
The social network has launched a large-scale campaign against App Tracking Transparency,
proving that the function can hit small businesses hard,
as it will make advertising (which you can’t do without anyway) less effective.
However, according to experts, Facebook deliberately misleads the public.
https://www.securitylab.ru/news/516299.php
SecurityLab, [08.02.21 10:20]
As part of a new targeted phishing campaign,
hackers have used a new tactic of obfuscation,
which consists in using Morse code to hide malicious URLs in email attachments and bypass mail gateways and filters.
A malicious campaign was reported by a Reddit user.
The phishing attack begins with sending an email disguised as an account for a company with the subject “Revenue_payment_invoice February_Wednesday 02/03/2021”.
The letter contains an attachment in HTML format with a name that looks like a company account in Excel format — “[company name] _invoice [number] ._ xlsx.hTML».
When viewing an attachment in a text editor, you can find JavaScript code that matches letters and numbers with Morse code.
For example, the letter “a” is displayed in “.-“, and the letter “b” is displayed in “-…”.
https://www.securitylab.ru/news/516297.php
SecurityLab, [08.02.21 12:04]
Elon Musk spoke about the successful implantation of the Neuralink chip into the brain of a live monkey, and the specialists of the Korean Institute announced a miniature wireless implant for controlling the brain through a smartphone.
SecurityLab Editor-in-Chief Alexandra Antipov will tell:
– when are the first chips planned to be implanted into the human brain;
– how hackers can deprive you of your intimate life;
– why it is impossible to turn off the Internet in Russia.
and the main incident of the week is how ESET discovered a new attack on the supply chain of the NoxPlayer gaming application update mechanism, which is used by 150 million users.
Read more in the issue -> https://standoff365.com/security-lab/ilon-mask-ob-uspeshnom-vzhivlenii-chipa-neuralink-v-mozg-zhivoy-obezyany-spetsialisty-koreyskogo-ins
SecurityLab, [08.02.21 16:10]
Users complained about the failure of Yandex services, according to Downdetector.com data.
The problems were reported by residents of Moscow, St. Petersburg, Nizhny Novgorod, Krasnodar and other cities.
https://www.securitylab.ru/news/516328.php
SecurityLab, [09.02.21 07:33]
Users in China were denied access to the American Clubhouse voice social network after its popularity grew dramatically.
Chinese citizens used the app to circumvent censorship and discussed taboo topics there.
On February 8, thousands of Chinese users discovered that they no longer have access to the Clubhouse, TechCrunch wrote.
At the same time, the website of the voice messaging service is still working.
Since its launch last year in 2020,
Clubhouse has become the digital equivalent of the A-lister club,
most of the hype of which is associated with the requirement to give an “invite”.
Users must be invited by an existing user to access the Clubhouse.
https://www.securitylab.ru/news/516335.php
SecurityLab, [09.02.21 08:10]
An unknown hacker gained unauthorized access to the computer system of a water treatment plant in the city of Oldsmar (Florida, USA) and changed the levels of chemicals to dangerous parameters.
https://www.securitylab.ru/news/516337.php
SecurityLab, [09.02.21 10:30]
Polish computer game developer CD Projekt has become a victim of a cyberattack using extortionate software.
The attackers managed to gain access to his internal computer network, encrypt some devices and steal “certain data”.
https://www.securitylab.ru/news/516344.php
SecurityLab, [09.02.21 19:10]
North Korean hackers have stolen more than $300 million to finance the country’s nuclear and ballistic missile programs.
This is stated in a confidential report of UN experts on North Korea, which was received by CNN through a diplomatic source in the UN Security Council.
https://www.securitylab.ru/news/516365.php
SecurityLab, [10.02.21 08:10]
Microsoft specialists have warned enterprises about a new type of attack called “dependency confusion” or “substitution attack”,
the essence of which is interference in the application development process in a corporate environment.
https://www.securitylab.ru/news/516423.php
SecurityLab, [10.02.21 11:50]
German software developer Jonas Strehle has published on GitHub an implementation of a new technique for binding an identifier to a specific browser instance.
The method is based on the features of Favicon image processing,
for which a separate cache is used, acting as a Supercookie.
https://www.securitylab.ru/news/516436.php
SecurityLab, [10.02.21 15:00]
Forescout specialists have discovered several vulnerabilities in a number of TCP/IP stacks associated with incorrect generation of ISN numbers,
which entails a risk for millions of devices from the Internet of Things. (IoT)
https://www.securitylab.ru/news/516461.php
Forescout researchers have discovered vulnerabilities in multiple TCP/IP stacks in which ISNs (Initial Sequence Numbers within TCP connections) are improperly generated, leaving TCP connections of a device open to attacks. Forescout researchers analyzed 11 total stacks: uIP, FNET, picoTCP, Nut/Net, lwIP, cycloneTCP, uC/TCP-IP, MPLAB Net, TI-NDKTCPIP, Nanostack, and Nucleus NET.
We found improperly generated ISNs in 9 of the 11 stacks analyzed.
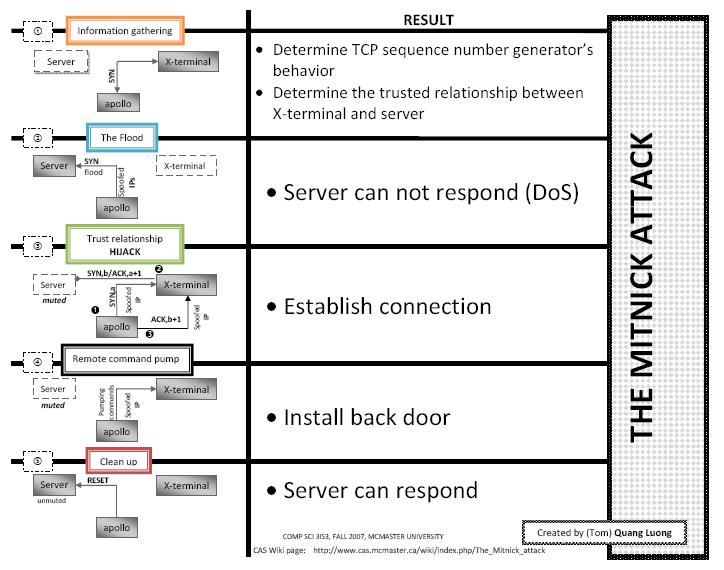
This type of vulnerability has been used historically to break into general-purpose computers (notoriously by Kevin Mitnick, which led it to be known as the “Mitnick attack”).
What makes this finding different is the stacks are primarily used in embedded devices, potentially widening their impact.
ISNs ensure that every TCP connection between two devices is unique and that there are no collisions, so that third parties cannot interfere with an ongoing connection. To guarantee these properties, ISNs must be randomly generated so that an attacker cannot guess an ISN and hijack an ongoing connection or spoof a new one.
Here’s a recap of our findings (lwIP and Nanostack are not mentioned as they were not found vulnerable):
[su_table responsive=”yes” alternate=”no”]
| CVE ID | CVSSv3 Score | TCP/IP Stack analyzed | Description | Fix |
|---|---|---|---|---|
| CVE-2020-27213 | 7.5 | Nut/Net 5.1 | ISN generator relies on a highly predictable source (system timer) and has constant increments. | Patch in progress. |
| CVE-2020-27630 | 7.5 | uC/TCP-IP 3.6.0 | ISN generator relies on LCG, which is reversible from observed output streams. The algorithm is seeded with publicly recoverable information (i.e., system timer count). | uC/TCP-IP is no longer supported. Patched in the latest version of Micrium OS (successor project). |
| CVE-2020-27631 | 7.5 | CycloneTCP 1.9.6 | ISN generator relies on LCG, which is reversible from observed output streams. The algorithm is initially seeded with a publicly observable CRC value. | Patched in version 2.0.0. |
| CVE-2020-27632 | 7.5 | NDKTCPIP 2.25 | ISN generator is initialized with a constant value and has constant increments. | Patched in version 7.02 of Processor SDK. |
| CVE-2020-27633 | 7.5 | FNET 4.6.3 | ISN generator is initialized with a constant value and has constant increments. | Documentation updated to warn users and recommend implement-ing their own PRNG. |
| CVE-2020-27634 | 7.5 | uIP 1.0 Contiki-OS 3.0 Contiki-NG 4.5 |
ISN generator is initialized with a constant value and has constant increments. | No response from maintainers. |
| CVE-2020-27635 | 7.5 | PicoTCP 1.7.0 PicoTCP-NG |
ISN generator relies on LCG, which is reversible from observed output streams. The algorithm is seeded with publicly recoverable information (i.e., system timer count). | Version 2.1 removes the default (vulnerable) implementation and recommends users implement their own PRNG. |
| CVE-2020-27636 | 7.5 | MPLAB Net 3.6.1 | ISN generator relies on LCG, which is reversible from observed output streams. The algorithm is seeded with a static value. | Patched in version 3.6.4. |
| CVE-2020-28388 | 6.5 | Nucleus NET 4.3 | ISN generator relies on a combination of values that can be inferred from a network capture (MAC address of an endpoint and a value derived from the system clock). | Patched in Nucleus NET 5.2 and Nucleus ReadyStart v2012.12 |
[/su_table]
These vulnerabilities were discovered and disclosed to the affected vendors and maintainers in October 2020. Most vendors have already issued patches and/or mitigation recommendations to users. The developers of Nut/Net are working on a solution, and Forescout has not received a response from the uIP developers.
The vulnerabilities found (except CVE-2020-28388) have a common CVSSv3 score and vector of 7.5 and AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N, respectively. Siemens has assigned a score of 6.5 to CVE-2020-28388 with the vector AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:L. However, the actual severity on a particular device and TCP connection may vary depending on, for example, the use of encrypted sessions and the sensitivity of data exchanged.
Impact
The popularity and some use cases of the vulnerable stacks is extensive. As we outlined in our AMNESIA:33 report, uIP, FNET, picoTCP and Nut/Net are used by millions of devices, including everything from IT file servers to IoT embedded components. We believe that CycloneTCP, uC/TCP-IP, NDKTCPIP, MPLAB Net and Nucleus NET are equally popular and widespread.
In this research, Forescout has not tried to identify affected devices or device manufacturers. Still, there are several notable public use cases of some of the stacks, such as medical devices, wind turbine monitoring systems, remote terminal units (RTUs) and IT storage systems.
Recommended Mitigation
Identifying and patching devices running the vulnerable stacks is challenging because it is often unknown which devices run a particular stack, and embedded devices are notoriously difficult to manage and update.
That’s why we recommend this mitigation strategy:
- Discover and inventory devices that run a vulnerable TCP/IP stack. Forescout Research Labs has released an open-source script that uses active fingerprinting to detect devices running the affected stacks. The script is updated constantly with new signatures. Additionally, Nmap allows the collection of ISN metrics and performs statistical analyses to understand whether a target device suffers from weak ISN generation.
- Patch when possible. Monitor progressive patches released by affected device vendors and devise a remediation plan for your vulnerable asset inventory. Forescout can help orchestrate remediation workflows with other IT and security tools for devices that have available patches and can be patched outside of maintenance windows.
- Segment to mitigate risk. For vulnerable IoT and OT devices, use segmentation to minimize network exposure and the likelihood of compromise without impacting mission-critical functions or business operations. Segmentation and zoning can also limit the blast radius and business impact if a device is compromised. Forescout eyeSegment can help to restrict external communication paths and isolate or contain vulnerable devices in zones.
- Deploy IPsec. End-to-end cryptographic solutions built on top of the Network layer (IPsec) do not require any modifications to a TCP/IP stack in use while allowing to defend against TCP spoofing and connection reset attacks. Unfortunately, this comes at the cost of network bandwidth.
Phase Two of Project Memoria
In 2020 Forescout Research Labs started Project Memoria, an initiative that seeks to provide the cybersecurity community with the largest study on the security of TCP/IP stacks. The first outcome of the project was AMNESIA:33 – a set of 33 vulnerabilities affecting four open source TCP/IP stacks.
These latest findings represent the second study in Project Memoria, focusing on the same seven open source embedded TCP/IP stacks from the first study (uIP, FNET, picoTCP, Nut/Net, lwIP, cycloneTCP and uC/TCP-IP), as well as four other popular stacks: Microchip’s MPLAB Net, Texas Instruments’ NDKTCPIP, ARM’s Nanostack and Siemens’ Nucleus NET.
Forescout will continue to drive impactful research into TCP/IP stacks through Project Memoria. Our goal is to raise industry awareness of the vulnerability of these stacks and the importance of a secure software supply chain.
Learn more
For a detailed analysis of ISN vulnerabilities in TCP/IP stacks, download the full report: NUMBER:JACK Weak ISN Generation in Embedded TCP/IP Stacks.
SecurityLab, [10.02.21 17:43]
The Department of Sanitary Supervision of Rospotrebnadzor has introduced new requirements for the use of mobile devices in education.
According to the new rules, children can carry smartphones to school to communicate with their parents or communicate, but only computers, tablets, candy bars or interactive whiteboards should be used for training.
“Requirements for electronic learning tools have been introduced.”
“A ban on the use of mobile communications for educational purposes has been introduced.”
“You cannot use personal mobile phones to conduct an educational program,”
said Irina Shevkun, head of the Sanitary Supervision Department of Rospotrebnadzor.
https://www.securitylab.ru/news/516464.php
SecurityLab, [10.02.21 20:20]
Developer Gustave Monce told about this on his Twitter.
Windows 10: “After integrating the mentioned feature, a new video camera icon will appear on the taskbar. By hovering the mouse cursor over it, you can see which applications use the camera. If there are several such apps, their number will be displayed directly on the icon. The new feature is designed to increase the level of privacy and will certainly be in demand, especially among people who are worried that certain applications may be monitoring them.
In 2016, Kaspersky Lab published the results of a survey among Internet users regarding personal security in cyberspace.
According to the survey, 23% of Russians stick cameras on their laptops to avoid surveillance. 14% of respondents intentionally do not use social networks, and 15% of users do not store the history of page visits and data for auto-filling forms in browsers. However, such actions, according to experts, do not give much, since almost all Internet services store data about users of their resources.”
https://www.securitylab.ru/news/516467.php
SecurityLab, [11.02.21 08:10]
Cybercriminals have put up for auction the alleged source code of popular computer games from CD Projekt, including The Witcher 3, Thronebreaker and Cyberpunk 2077.
https://www.securitylab.ru/news/516491.php
SecurityLab, [11.02.21 09:45]
Universities, organizations and technology giants such as Microsoft and Facebook are working on tools to detect deepfakes,
which are designed to prevent their use for disinformation and the spread of malicious media.
However, a team of scientists from the University of California at San Diego at the WACV 2021 conference reported that deepfake detectors can still be deceived by embedding input data (adversarial examples) into each video frame.
https://www.securitylab.ru/news/516493.php
SecurityLab, [11.02.21 12:10]
The Ministry of Digital Development, Communications and Mass Media of the Russian Federation has submitted revised requirements for software developers who want their products to be included in the register of domestic programs.
According to these requirements, all the technical means necessary for the software release, the source text and the object code must be located on the territory of the Russian Federation.
https://www.securitylab.ru/news/516498.php
SecurityLab, [11.02.21 15:06]
The implementation of a comprehensive access management solution in the company’s systems,
if you use the maximum of its capabilities,
is usually a long and expensive project.
Often, customers, having learned about the cost of owning a system, are perplexed: there are many stages, each of them has to pay a lot of money – is it necessary? But is it really that scary?
The implementation of the IGA system is not only the purchase of software and licenses.
This is a set of measures and processes that work to optimize access control.
At the same time, not every organization needs a complex and expensive solution.
One company may already have its own system for submitting applications for access to resources – here you just need to complete the scheme by implementing automation of granting rights and executing applications.
And in another case, you first need to conduct an audit: identify unauthorized accounts, check the legitimacy of the granted access rights, etc. There is still a long way to fully automate access control processes.
https://www.securitylab.ru/news/516515.php
SecurityLab, [11.02.21 17:13]
Europol has arrested 10 cybercriminals in the UK, Belgium and Malta on charges of hacking the mobile phones of celebrities, sports stars and musicians in order to steal personal information and millions of dollars in cryptocurrency.
A cybercrime group stole more than $100 million in cryptocurrency using the SIM-swapping technique.
This technique involves deactivating the SIM card of the victim’s mobile phone by deceiving the phone company or using a bribed insider so that the number can be transferred to another card under the control of criminals.
https://www.securitylab.ru/news/516520.php
SecurityLab, [12.02.21 07:55]
It is necessary for foreign social networks to open their representative offices in Russia,
and for this it is necessary to think over the appropriate regulation that would force them to do this,
according to the deputy head of Roskomnadzor Milos Wagner.
https://www.securitylab.ru/news/516529.php
SecurityLab, [12.02.21 08:10]
The Federal Service for Technical and Export Control (FSTEC) intends to create a research center for testing the security of operating systems based on the (GNU) Linux kernel.
FSTEC announced a tender worth 300 million rubles on the public procurement portal, to create this institution.
https://www.securitylab.ru/news/516530.php
SecurityLab, [12.02.21 10:20]
Researchers from Data61, a member of the State Association of Scientific and Applied Research (CSIRO) of Australia,
in collaboration with the Australian National University and experts from Germany reported that artificial intelligence can influence human decision-making.
“Although the study was theoretical,”
“it allows us to better understand how people make choices.”
“This knowledge is valuable because it allows us to reduce our vulnerabilities so that we can better identify and avoid erroneous choices as a result of potential AI abuse,” the experts noted.
https://www.securitylab.ru/news/516531.php
SecurityLab, [12.02.21 15:15]
The Yandex security service has discovered an internal information leak.
According to the results of the investigation, it became known that one of the company’s employees provided unauthorized access to users’ mailboxes.
The attacker turned out to be one of three system administrators who had access rights to perform work tasks to provide technical support for the service.
As a result of his actions, 4887 mailboxes were compromised.
“Unauthorized access to compromised mailboxes has already been blocked.”
“Their owners received a notification about the need to change the password from their account,” the press service of Yandex reported.
https://www.securitylab.ru/news/516543.php
SecurityLab, [12.02.21 20:05]
A vulnerability in the macOS version of the program that violates user privacy has been discovered in the popular Telegram messaging application. The problem was identified by security researcher Dhiraj Mishra in the Telegram application version 7.3. Its operation allowed access to self-destructing audio and video messages long after they disappeared from secret chats.
Unlike Signal or WhatsApp, Telegram conversations are not encrypted by default, except when users use secret chats that store data encrypted even on Telegram servers. Also in secret chats, the ability to send self-destructing messages is available.
According to the researcher, when a user records and sends an audio or video message via a regular chat, the application transmits the exact path by which the recorded message is stored in the “.mp4” format. When the secret chat option is enabled, the path information is not transmitted, but the recorded message is still stored in the same place.
https://www.securitylab.ru/news/516546.php
the biometric airport: open the gates without a boarding pass and passport?
how much privacy and data are users willing to give up for a little gain in efficiency?
SecurityLab, [13.02.21 08:00]
The modernization involves the installation of video cameras on all automated turnstiles (eGate) in Domodedovo, namely in the customs control zone, the departure gallery of international flights and all boarding gates.
This is done for the convenience of passengers, increasing airport profits and speeding up pre-flight procedures.
They become fully automatic, without the participation of people and without presenting a passport – from the moment of registration to boarding the plane.
The biometric data processing system will allow to fully automate the passage of pre-flight procedures,
from the moment of registration to boarding the plane, minimizing human participation, representatives of Domodedovo believe.
To get such an opportunity, a Russian citizen will need to submit data to the Unified Biometric System (EBS) in one of the bank branches,
as well as consent to the use of biometrics for specific purposes.
Thanks to facial recognition, you can identify a passenger once, and then read the data and open the gates without a boarding pass and passport.
https://www.securitylab.ru/news/516547.php
SecurityLab, [13.02.21 14:12]
Birsan successfully injected malicious code into repositories such as npm, PyPI, and RubyGems, from which his software was subsequently distributed further down the update delivery chain:
Over the past week, more than two hundred new packages have appeared in the NPM repository,
simulating the PoC of a researcher who managed to hack more than 35 large technology companies.
We are talking about a new type of attack on the supply chain called “mismatch of used dependencies” or “substitution attack” (dependency confusion),
previously described by information security expert Alex Birsan (Alex Birsan) and separately Microsoft.
With this attack, the researcher was able to run malicious code on the systems of dozens of large technology companies, including Microsoft, Apple, PayPal, Tesla, Uber, Yelp and Shopify.
Details: The method involves exploiting a design flaw in the security of open source repositories to replace private dependencies used by large companies.
By registering the names of internal libraries in public directories of open source packages, Birsan successfully injected malicious code into repositories such as npm, PyPI, and RubyGems, from which his software was subsequently distributed further down the update delivery chain.
According to Sonatype specialists, 48 hours after the publication of Birsan’s research, the NPM repository was flooded with packages that mimic the expert’s PoC, marked “for research purposes only”.
Experts believe that in this way copycats are trying to get rewards in the framework of vulnerability search programs.
“It is quite expected that other” vulnerability hunters” or even attackers will start downloading packages, and I cannot influence their actions,” Birsan explained in a conversation with Bleeping Computer.
According to Sonatype experts, most of the published simulator packages contain identical code that sends DNS queries to the Birsan server, have the same structure, version names, and comments in the code.
Although the researchers did not detect malicious packages, they warned that attackers may well take advantage of the situation, and if open repository administrators do not implement reliable verification mechanisms when publishing packages, “wildcard attacks” will become a serious tool for more complex malware campaigns.
https://www.securitylab.ru/news/516548.php
Sometimes, depending on the purpose, applications may also contain proprietary or sensitive code.
Such programs usually use private libraries stored in private (internal) repositories within the company’s own networks.
In the process of creating them, developers combine private libraries with public ones downloaded from open portals with packages, such as PyPI, NuGe, and so on.
According to Microsoft experts, cybercriminals can take advantage of such a mixed development environment in large corporations by performing the “mismatch of used dependencies” attack.
As experts explained, after learning the names of private libraries used in the development of corporate applications, attackers can register them in open package repositories and download public libraries with malicious code.
The “dependency mismatch” attack occurs when developers create their applications in an enterprise environment, and their package managers prioritize malicious libraries from public repositories instead of internal libraries with the same names.
To test their assumption, the researchers decided to identify situations where large technology companies accidentally revealed the names of various internal libraries, and register these libraries in package repositories like npm, RubyGems, and PyPI.
As a result, they were able to upload their code (not malicious) to applications used by 35 large companies, including Apple, Microsoft, PayPal, Shopify, Netflix, Yelp, Uber, and others.
In addition to RubyGems and PyPI, the issue also affects other package managers, such as JFrog, Maven Central, and NuGet.
The researchers notified all affected companies and the creators of package managers about it.
https://www.securitylab.ru/news/516423.php
SecurityLab, [14.02.21 07:45]
With the help of the watch, users will be able to send messages via Facebook services, monitor their health using special applications and use fitness functions.
Also, owners of smart watches will have access to fitness applications and utilities that allow them to monitor their health status.
According to the Verge, the watch will run on the Android operating system.
At the same time, according to preliminary data, Facebook is developing its own system that will function on the next models of smart watches.
The Information reports that the smartwatch from Facebook will work via cellular communication, regardless of the smartphone.
Earlier, Facebook was sued for spying on users.
The company was accused of illegally spying on Instagram users through their smartphone cameras.
https://www.securitylab.ru/news/516550.php
SecurityLab, [14.02.21 10:25]
Law enforcement officers, as well as specialists in the field of computer security, identified Fedorov Alain Evgenievich, who, according to the investigation, was engaged in the sale of personal personal data of Russians: copies of their passports, bank statements and other documents of the victims.
He was charged with committing a crime under part 4 of Article 272 of the Criminal Code of the Russian Federation (“Unlawful access to computer information that caused major damage committed by an organized group and created a threat of serious consequences”).
https://www.securitylab.ru/news/516551.php
SecurityLab, [14.02.21 19:32]
The administration of the social network Instagram reported that from now on accounts that send hostile statements in personal messages will be blocked.
Previously, a preventive measure in the issue of insults and discrimination on Instagram was a temporary ban on personal correspondence.
https://www.securitylab.ru/news/516556.php
SecurityLab, [15.02.21 08:40]
Earlier this month, the Clubhouse audio communication app rapidly gained popularity among Chinese users.
Stanford University specialists decided to find out how Clubhouse protects its users’ data and explain why this is important using the example of the application.
https://www.securitylab.ru/news/516562.php
SecurityLab, [15.02.21 14:40]
Illegal copies of a number of well-known computer games were revealed in the Microsoft Edge extension store, including Mario Kart 64, Super Mario Bros., Sonic the Hedgehog 2, Pac-Man, Tetris, Cut The Rope and Minecraft.
https://www.securitylab.ru/news/516597.php
SecurityLab, [15.02.21 15:25]
The FBI supposedly has a tool at its disposal to access private messages in the Signal messenger on the iPhone.
This is evidenced by court documents related to the case of arms trafficking in New York.
https://www.securitylab.ru/news/516603.php
SecurityLab, [15.02.21 16:38]
The main news of the information security industry in the review from the editor-in-chief of SecurityLab Alexander Antipov:
Critical infrastructure facilities are increasingly being attacked by intruders: an attempt to arrange a man-made disaster was stopped in Brazil and the US state of Florida
What is GPS spoofing and how it can ruin your trip
How to protect your bank accounts? We learn from the mistakes of a girl who lost 2 million rubles by leaving her phone in a taxi
❗️ And the main incident of the week: how the cryptocurrency extracted by cyberattacks helps in financing the nuclear program
https://www.youtube.com/watch?v=2sZuUbDMms8
SecurityLab, [15.02.21 20:20]
Sberbank from April 2021 will introduce through the Sberbank Online mobile application a service for determining the numbers of incoming calls from fraudsters, Kirill Tsarev, deputy chairman of the board of the credit institution, told reporters.
https://www.securitylab.ru/news/516610.php
SecurityLab, [02/16/2011 07:00]
“According to the data for the third quarter, the “average check” is more than 10,000 rubles,” Sychev said in response to the question of how much on average phone scammers steal from Russians in one call.
According to him, earlier scammers simply called citizens en masse.
Then most of the people learned to identify them, so the attackers changed their approach.
Now they use substitution numbers, which is why many lose their vigilance, Sychev added.
https://www.securitylab.ru/news/516614.php
SecurityLab, [16.02.21 10:25]
Cybersecurity researchers have revealed details about a fixed vulnerability in the Telegram messaging application, the operation of which allowed remote attackers to access messages, photos and videos in users’ secret chats.
Details:
Exploiting the problem allowed remote attackers to gain access to messages, photos, and videos in users ‘ secret chats.
Cybersecurity researchers have revealed details about a patched vulnerability in the Telegram messaging app that allowed remote attackers to access messages, photos, and videos in users ‘ secret chats.
The problem was discovered by the Italian company Shielder in the app’s iOS, Android, and macOS versions.
The vulnerabilities are related to the secret chat function and the app’s handling of animated stickers.
Attackers can send modified stickers to unsuspecting users and gain access to messages, photos, and videos in regular and secret chats.
Exploiting the vulnerability is not easy, because it requires linking the problem to at least one additional vulnerability in order to bypass security protections in modern devices.
It is worth noting that this is the second problem this month discovered in the Telegram secret chat function.
Last week, a vulnerability was discovered in the macOS version of the program that violates user privacy.
Its exploitation allowed access to self-destructing audio and video messages long after they disappeared from secret chats.
https://www.securitylab.ru/news/516622.php
SecurityLab, [16.02.21 11:25]
The French authorities insist on changing future EU rules regarding tech giants such as Apple, Google, Facebook and Amazon so that member states can have more powers to punish violations of the law.
This was reported by the Financial Times.
https://www.securitylab.ru/news/516642.php
SecurityLab, [16.02.21 15:15]
Journalist Brian Krebs spoke about the new Bluetooth skimmers for payment terminals, which the attackers began to use in US stores.
A distinctive feature of these devices is the ability to interact with the function of terminals for reading payment card chips.
Skimmers block the ability to read chips, and buyers have to use less secure magnetic tape.
https://www.securitylab.ru/news/516618.php
SecurityLab, [16.02.21 18:10]
The State Duma in the second reading adopted a package of bills concerning elections and referendums.
They were developed by the United Russia faction with the participation of Sergei Boyarsky and Alexander Khinstein, who have already distinguished themselves in their zeal to regulate the Runet.
The owner of the resource, after he receives the notification, will have only a day to voluntarily remove the illegal content.
https://www.securitylab.ru/news/516659.php
SecurityLab, [17.02.21 03:25]
The State Duma in the first reading adopted a bill on extended consent to the processing of personal data.
https://www.securitylab.ru/news/516660.php
SecurityLab, [17.02.21 08:20]
Starting next month, LastPass users will no longer be able to have a free account simultaneously on mobile devices and computers.
https://www.securitylab.ru/news/516663.php
SecurityLab, [17.02.21 11:25]
Epic Games has appealed to the antitrust regulators of the European Union with a complaint against Apple, saying that the tech giant is unfairly using its iOS ecosystem to collect a tax of 30% on purchases in the App Store.
https://www.securitylab.ru/news/516674.php
SecurityLab, [17.02.21 15:50]
The Dutch police have published warnings on two major hacker forums for cybercriminals that “hosting criminal infrastructure in the Netherlands is a hopeless matter.”
https://www.securitylab.ru/news/516691.php
SecurityLab, [17.02.21 19:10]
The deputies adopted the document in the third, final reading.
It suggests that operators disconnect from service cellular numbers that are used in pre-trial detention centers and colonies by prisoners there.
The blocking will be carried out by a written decision of officials of the Federal Penitentiary Service (FSIN).
https://www.securitylab.ru/news/516697.php
SecurityLab, [17.02.21 19:40]
The press secretary of the President of Russia Dmitry Peskov considers the wording from the report of the French special services on the involvement of the Russian Federation in cyber attacks on enterprises of this country absurd.
https://www.securitylab.ru/news/516699.php
SecurityLab, [18.02.21 09:15]
Mac computers with Apple’s new M1 processors have only been on sale for a few months, but cybercriminals have already targeted them.
According to security researcher Patrick Wardle, he discovered a malicious application designed specifically for M1.
https://www.securitylab.ru/news/516712.php
SecurityLab, [18.02.21 15:10]
The collection agency Activbusinessconsult (ABC), owned by Sberbank, has started using a new technology in its call centers to analyze debtors’ votes.
The new system, which has been working on for two and a half years, is able to analyze the intonation of the caller and read his emotions.
Based on these data, the robot creates a further scenario of the dialogue, writes RBC.
https://www.securitylab.ru/news/516741.php
SecurityLab, [18.02.21 16:55]
NVIDIA announced the development of a special driver that slows down the GeForce RTX 3060 graphics card twice in case of detection of cryptocurrency mining algorithms, according to the company’s blog.
This will make GeForce adapters less attractive to cryptocurrency miners.
It is not specified whether these restrictions will affect only GeForce RTX 3060 or all Ampere gaming video cards.
https://www.securitylab.ru/news/516743.php
SecurityLab, [19.02.21 08:25]
Beverly Hills police officers (California, USA) have found a creative way to prevent the publication of videos with them on Instagram.
Since the algorithms of the service do not allow publishing videos with music protected by copyright law, entering into a dialogue with activists who will probably want to take a conversation on the phone and put it on the Network, law enforcement officers include copyrighted songs.
https://www.securitylab.ru/news/516752.php
SecurityLab, [19.02.21 13:10]
Microsoft has been closely following the SolarWinds hacking case since it discovered unusual activity in its systems last December.
MS now completed own investigation into the incident, which revealed that hackers did not gain access to user data and did not use Microsoft systems to attack other victims, including nine US federal agencies and about a hundred private companies.
https://www.securitylab.ru/news/516756.php
SecurityLab, [19.02.21 17:00]
WhatsApp plans to repeat the attempt to implement the updated privacy policy, which caused a flurry of criticism of the messenger.
“In the coming weeks,” the company will begin sending out appropriate notifications to users and provide more information before requiring users to agree to the new terms of use.
https://www.securitylab.ru/news/516773.php
SecurityLab, [20.02.21 09:30]
The Tor mode in the Brave browser allows users to access sites .onion in a private window without the need to install Tor separately.
However, as it turned out, onion addresses leave their traces in the DNS traffic of the browser.
https://www.securitylab.ru/news/516776.php
SecurityLab, [20.02.21 11:25]
Cybersecurity researchers have told about a new attack that allows attackers to trick payment terminals into performing operations with a contactless Mastercard card, passing it off as a Visa card.
https://www.securitylab.ru/news/516782.php
SecurityLab, [20.02.21 14:45]
The Federal Financial Monitoring Service of the Russian Federation (Rosfinmonitoring) has developed a digital service that allows you to analyze transactions related to cryptocurrency in order to detect crimes.
https://www.securitylab.ru/news/516786.php
SecurityLab, [22.02.21 07:32]
Please share the most interesting resources for you (podcasts, YouTube channels, telegram channels, blogs): https://ru.surveymonkey.com/r/92FJYG5
SecurityLab, [22.02.21 07:50]
The US threatens Russia to respond to an attack allegedly by Russian hackers of the US government.
Joe Biden’s national security adviser, Jake Sullivan, promised that he would make sure that “Russia understands where the United States draws the line” on the issue of cyber attacks.
According to the official, the response will include not only sanctions, the influence will be exerted through “visible and invisible tools.”
https://www.securitylab.ru/news/516797.php
SecurityLab, [22.02.21 15:50]
Hardware and software complexes will be used to extract various information from smartphones, including correspondence in Skype and WhatsApp messengers, as well as in the Facebook social network.
Interior Ministry units will spend tens of millions of rubles on this.
Now purchases have become especially large.
That is, earlier the Interior Ministry departments have already purchased similar equipment, but in smaller volumes
https://www.securitylab.ru/news/516799.php
SecurityLab, [22.02.21 18:39]
Users will be able to receive calls and notifications.
However, you will not be able to read and send messages.
Inactive accounts will be deleted later.
Confirmation of consent to the transition to the new rules must occur before May 15.
Until the policy is adopted, the user will not be able to read and send messages in the application.
At the same time, he will have the opportunity to receive calls and notifications for a short period of time.
Details:
All “dissenters” will be able to receive calls and notifications for the next two weeks, but will not be able to read or send messages from the messenger.
Users will be able to receive calls and notifications. However, you won’t be able to read or send messages. Inactive accounts will be deleted later.
Confirmation of consent to the transition to the new rules must take place before May 15.
However, they will still be able to receive calls and notifications for a short period of time.
The online publication TechCrunch clarified with reference to a letter from the messenger management sent to one of the partners that after May 15, the messenger will “slowly ask” users who did not agree to the new terms to accept them.
If users do not accept the new policy, their account will be deleted after 120 days of inactivity.
The new terms will allow Facebook and WhatsApp to share data about user payments and transactions.
Earlier it was reported that the popular WhatsApp messenger threatens users with account blocking for refusing to accept the new terms of use of the application.
https://www.securitylab.ru/news/516798.php
SecurityLab, [23.02.21 11:34]
Hundreds of inmates in Arizona are serving their prison sentences longer than they should because of outdated versions of prison management software.
Employees of the Arizona Department of Corrections have been aware of this problem since 2019, according to radio station KJZZ.
Arizona has one of the highest incarceration rates in the United States.
As part of the amendment to the Arizona State law of June 2019, a special program was created through which prisoners can be eligible for early release.
https://www.securitylab.ru/news/516846.php
SecurityLab, [23.02.21 13:41]
The Clubhouse social network announced the leakage of conversations of some users who were in a closed room.
The reason for this was a hacker attack that was launched on February 20.
An unknown user was able to circumvent the security restrictions of the social network and transfer users’ audio files to a third-party website on the Internet, explained Clubhouse spokeswoman Rima Banasi.
Details of the hack are not reported, but the company announced that the user has already been blocked and the necessary data protection measures have been taken.
At the same time, experts say that it is impossible to ensure complete confidentiality of information.
Learn more: https://www.securitylab.ru/news/516848.php
SecurityLab, [24.02.21 09:30]
Microsoft has stated that it has “solid evidence” of Russia’s involvement in the sensational wave of cyber attacks on at least nine US federal agencies and dozens of private companies.
In identifying the source of cyber attacks, Microsoft has moved much further than the American government, CNN writes.
As Microsoft President Brad Smith noted, speaking before the US Senate Intelligence Committee, the government will probably need time to formally come to the same conclusion.
https://www.securitylab.ru/news/516877.php
SecurityLab, [2/24/21 9:50 AM]
The coronavirus pandemic has led to the penetration of digital platforms into people’s lives, UN Secretary-General Antonio Guterres said at the opening of the 46th session of the UN Human Rights Council.
https://www.securitylab.ru/news/516881.php
SecurityLab, [2/24/21 10:25 AM]
Mozilla has implemented the full Cookie Protection feature in the new version of its Firefox 86 browser.
A new protection feature is built into the Enhanced Tracking Protection mode (“Advanced Tracking Protection”), added to the browser in 2019.
https://www.securitylab.ru/news/516886.php
SecurityLab, [2/24/21 11:54 AM]
The fifth issue of security news with Alexander Antipov, Editor-in-chief Securitylab.ru
In this issue:
▪️ How big can groups attacking global corporations be?
▪️ Why does celebrity status not save from cyberattacks?
▪️ How are protected chats not so protected?
Keep up to date with the main news of the IT world, current threats and events that affect each of us.
https://www.youtube.com/watch?v=-slHkzWm5AI
SecurityLab, [2/24/21 2:40 PM]
At the request of the BBC, the specialists of the Hey mail service analyzed their traffic and found that about two-thirds of emails sent to users’ personal email accounts contain so-called “spy pixels”.
https://www.securitylab.ru/news/516903.php
instead of general forbidding huawai 5G, the Russians say: “5G okay, but only with our home grown end-to-end encryption” smort!
but still: if there are backdoors in 5G hardware, the also important meta-data (who called who, what ip connected to what ip) will probably stay unencrypted (!?)
SecurityLab, [2/25/21 7:55 AM]
The Moscow structure has developed the TDM Messenger service — a “full-fledged replacement” for Telegram and Skype.
He must ensure secure communication, first of all, between officials.
Conventional services rarely meet the requirements of government agencies.
https://www.securitylab.ru/news/516916.php
SecurityLab, [2/25/21 9:40 AM]
The Central Research Institute of Communications (TSNIIS), commissioned by Rossvyaz, will consider the possibility of introducing in the Russian Federation a special system for identifying users of Internet services and virtual telephony using a telephone number and domain name matching system.
The cost of implementing such a system will be 32.7 million rubles.
Details:
This is a protocol for transferring phone numbers to the Internet domain name system ENUM (Electronic Number Mapping System). The phone number can be converted to a domain so that any user can “seamlessly” make calls from the Internet to regular phones and vice versa. To convert a phone number to an ENUM, you need to reverse the order of digits in it and add “at the end.e164.arpa” — a phone domain owned by the RIPE Internet Coordination Center in Europe.
The ENUM protocol is already used by some mobile operators in Russia to provide calls over the Internet protocol (VoIP).
According to some experts, the introduction of additional identification of users of Internet services by phone number implies total control, because currently the Unified Identification and Authentication System (USIA) is already used for users of public services.
https://www.securitylab.ru/news/516922.php
Why easy reliable backup, updates, test, restore are necessary:
SecurityLab, [2/25/21 3:40 PM]
According to Shodan, more than 6,700 VMware vCenter servers accessible via the Internet are vulnerable to a new attack that allows attackers to seize control of non-updated devices and, as a result, over the internal networks of organizations.
https://www.securitylab.ru/news/516945.php
SecurityLab, [2/25/21 5:40 PM]
According to the documentation, the screens will have to broadcast advertisements, metro messages and observe passengers. The winner of the tender will be chosen on March 4, he will have to finish the work in December.
https://www.securitylab.ru/news/516953.php
SecurityLab, [2/25/21 6:12 PM]
Attention contest!
Help us make Security News releases even better by participating in the contest!
100 participants who left motivated answers will receive a prize – an electronic Ozone certificate in the amount of 1000 rubles!
Rules of participation:
– have time to become one of the 100 lucky ones
– share your vision of what should be improved/added to the security news releases from Alexander Antipov
– don’t be afraid to share bold ideas – we appreciate the creative approach!
– 1 user = 1 prize!
Information about the contest under our video https://www.youtube.com/watch?v=-slHkzWm5AI
SecurityLab, [2/26/21 3:30 AM]
The special services of the Netherlands have made accusations against Russia and China due to daily cyber attacks on educational institutions and local companies.
https://www.securitylab.ru/news/516954.php
SecurityLab, [2/26/21 8:12 AM]
[Forwarded from Announcements of the best IB events (webinars)]
Do you want to use reverse engineering in your work?
March 9 at the demo lesson “Exploiting vulnerabilities in the driver” (https://otus.pw/hs80 /)you will understand the overflow vulnerabilities in the drivers. Lecturer Artur Pakulov will analyze an example of a classic buffer overflow vulnerability, integer type overflow vulnerability and features of exploits development in kernel mode.
Demo lesson is an opportunity to try the online course “Reverse-Engineering. Basic” and meet an expert. The basic level of the program will introduce you to the key features of reverse engineering. To register for a class, take the entrance test https://otus.pw/hs80 /.
SecurityLab, [2/26/21 9:30 AM]
A group of scientists from the USA and Germany analyzed the security mechanisms implemented in Amazon’s Alexa voice assistant ecosystem and recognized them as insufficiently effective.
(https://t.me/iv?url=https://www.securitylab.ru/news/516965.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/516965.php
SecurityLab, [2/26/21 3:55 PM]
Tech giant Facebook is considering the possibility of introducing a facial recognition system into its new “smart” glasses, the release of which is scheduled for this year. The company discusses ethical issues that may arise due to the use of this technology. In addition, Facebook has also started developing its own smartwatch.
(https://t.me/iv?url=https://www.securitylab.ru/news/516972.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/516972.php
SecurityLab, [2/27/21 8:55 AM]
[Forwarded from Announcements of the best IB events]
Positive Technologies invites you to the webinar “MaxPatrol SIEM 6.1: overview of new features”
The webinar will take place on March 4 at 14:00.
Positive Technologies invites you to take part in the webinar (https://ptsecurity.zoom.us/webinar/register/2316134020029/WN_PyNU1yT0Qc-pZwm6psu0-A ) “MaxPatrol SIEM 6.1: overview of new features”, which will be held on March 4 from 14:00 to 15:00 (Moscow time).
A new version of MaxPatrol SIEM was released in February. It allows you to quickly find and update IT assets with outdated data, monitor the load of the correlator and configure data collection profiles via the web interface. Dashboards can now be created without restrictions on the number of widgets, save them as templates and share with colleagues. New event fields have appeared in the taxonomy — they are needed for normalization and correlation rules.
Positive Technologies experts will show you how to work with new features and tell you about upcoming changes in the normalization and correlation rules.
The webinar will be useful for information security specialists and Positive Technologies partners.
SecurityLab, [2/27/21 3:39 PM]
The problem will also affect Russian government agencies, which are switching to domestic Linux-based operating systems as part of import substitution, experts say. Entrepreneurs who, against the background of the coronavirus pandemic, have begun to actively use the clouds, face increased costs: hackers can hack cloud environments and use them for mining cryptocurrencies, as well as DDoS attacks.
In 2020 alone, hackers created 56 categories of viruses under Linux, which is 40% more than a year earlier. Viruses will also affect Russian users. This was told by Oleg Bakshinsky, IBM’s leading information security adviser in Russia.
Learn more: https://www.securitylab.ru/news/516977.php
SecurityLab, [2/27/21 6:32 PM]
In their report, experts warn of the emergence of “cybercrime-as-a-service” schemes, thanks to which government hackers can work with third-party groups as part of the implementation of various kinds of campaigns. Such campaigns typically involve phishing and the introduction of malicious software into target networks.
As a result, hackers receive a financial reward, and the authorities of the customer country receive the data of interest or access to hacked networks. Since hackers use their own infrastructure and methods to conduct a malicious campaign, it is extremely difficult to link such an attack with the customer country.
https://www.securitylab.ru/news/516976.php
SecurityLab, [2/28/21 7:13 AM]
In the last few years, experts have observed a trend of gradual transition of virus writers from C and C++ languages to the Go language, developed and launched by Google in 2007. While the first malware written in Go was noticed back in 2012, they became a common phenomenon only a few years later – starting in 2019. At the same time, such malware uses both APT groups, for example, APT28 (a version of the Zebrocy Trojan written in Go), APT29 (Wellmess), Mustang Panda APT (Go Loader), and cybercrime groups such as Carbanak (GOSH RAT). In addition, new types of extortionate software (RobbinHood, Nefilim, EKANS) are also written in the Go language.
https://www.securitylab.ru/news/516978.php
SecurityLab, [2/28/21 10:20 AM]
The user databases of three popular Android VPN services have been hacked, and now millions of user records are for sale on the Internet.
(https://t.me/iv?url=https://www.securitylab.ru/news/516980.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/516980.php
SecurityLab, [2/28/21 8:24 PM]
A team of hackers of the Apple mobile platform with Unc0ver experience has released a jailbreak that works on iOS from version 14 to 14.3 with support for all iPhone models with this OS version – from the “ancient” iPhone 6s to the newest iPhone 12.
https://www.securitylab.ru/news/516989.php
SecurityLab, [3/1/21 7:55 AM]
In addition to the information of the Public Chamber of the Russian Federation on Twitter’s anti-leadership in the dissemination of prohibited information, we inform you that since 2017, the social network Twitter has not deleted 2,862 materials with prohibited information:
(https://t.me/iv?url=https://www.securitylab.ru/news/516994.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/516994.php
SecurityLab, [3/1/21 9:25 AM]
A resident of Pennsylvania, Donna Francis, became a victim of a hacker who intercepted her phone call to Apple’s technical support service. According to the victim, the attacker remotely installed applications on her iPhone and transferred money from her bank account. (https://t.me/iv?url=https://www.securitylab.ru/news/517000.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/517000.php
SecurityLab, [3/1/21 2:08 PM]
To recover from a hacker attack, the company may need more than a year!
We will tell and discuss cybersecurity news with SecurityLab Editor-in-Chief Alexander Antipov:
– how bugs in prison software interfere with the early release of prisoners
– how the police use Beatles songs
– how did Silver Sparrow manage to infect more than 30 thousand Mac devices
and the main incidents of the week:
– how has the number of ransomware attacks increased in 2021
– how SEPA is restored after hacking in 2020
– how do SunCrypt operators deceive their victims
SecurityLab, [3/1/21 4:25 PM]
Some people think that the attack on SolarWinds is a story about Russian or Chinese hackers, but in fact, it is a story about a huge security hole that increases as new details about the attack become available. And now an extreme – inexperienced intern who used an unreliable password has been discovered in this story, CNN writes.
(https://t.me/iv?url=https://www.securitylab.ru/news/517029.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/517029.php
SecurityLab, [3/1/21 5:32 PM]
Scientists at the University of Chicago have made a real breakthrough in quantum computing by sending entangled states of qubits through a cable connecting one node of a quantum network to another. Specialists of the Pritzker University School of Molecular Engineering also managed to strengthen the entangled state using the same cable. First they used a cable to entangle two qubits on each of the two nodes, and then further entangled the qubits with other qubits on the nodes. This research will help make quantum computing more feasible and lay the foundation for future quantum communication networks.
https://www.securitylab.ru/news/517033.php
SecurityLab, [3/1/21 7:25 PM]
This study included approximately 5.1 billion unique login/password pairs. The login in this case is the email address.
(https://t.me/iv?url=https://www.securitylab.ru/news/517038.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/517038.php
SecurityLab, [3/2/21 3:45 AM]
On Monday, March 1, a pilot program began to issue electronic bracelets to passengers arriving in Israel as an alternative to forced quarantine in hotels.
(https://t.me/iv?url=https://www.securitylab.ru/news/517039.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/517039.php
SecurityLab, [3/2/21 7:42 AM]
[Forwarded from Announcements of the best IB events (webinars)]
Online seminar “Live-demo of advanced infrastructure protection solutions against internal and external threats”
On March 12, at 11:00 (Moscow time), an online seminar “Live-demo of advanced infrastructure protection solutions against internal and external threats” will be held
The seminar will tell you how to use Microsoft solutions to secure the IT infrastructure when solving tasks such as:
* Protection of documents and emails
* Advanced mail server protection
* Control over the organization’s mobile devices
* Remote access to applications in a local environment
* Additional access protection measures
And there will also be a demonstration of the reflection of a cyber attack on the IT infrastructure.
SecurityLab, [3/2/21 10:10 AM]
Americans may be involved in cyberattacks that will put their Internet-connected devices at risk, says Kevin Mandia, CEO of FireEye information technology company. As Mandia reported in the Axios program on HBO, a cyber war between the United States and China or Russia can affect ordinary citizens and lead to mass destabilization of everyday life.
(https://t.me/iv?url=https://www.securitylab.ru/news/517050.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/517050.php
SecurityLab, [3/5/21 9:30 AM]
As part of the implementation of the law on “self-cleaning” of social networks, Roskomnadzor presented a methodology for calculating the number of their users. (https://t.me/iv?url=https://www.securitylab.ru/news/517157.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/517157.php
SecurityLab, [3/5/21 10:12 AM]
Among the channels on the topic of information security, there is the only one about which there are many versions, but none of them is true. This is the SecAtor channel (https://t.me/true_secator ).
Meet the most mysterious authors from the world of infosec. Find out about the wars of special services in cyberspace, about the activity of ransomware and commercial hacker groups, about fresh vulnerabilities in your software that need to be fixed urgently. Well, about insiders from the information security industry, of course.
SecAtor Channel (https://t.me/true_secator ) – nobody knows us, but we know a lot of things.
SecurityLab, [3/5/21 4:13 PM]
Over the past week, several organizations have immediately reported that they were victims of a cyberattack through a vulnerability in Accellion software, extortionate software operators continued to improve their tools, the manufacturer of the coronavirus vaccine became a victim of a cyberattack, and Chinese hackers learned to hack Gmail using a browser extension. Read about these and other events in the world of information security for the period from February 27 to March 5, 2021 in our review.
https://www.securitylab.ru/news/517171.php
SecurityLab, [3/6/21 4:41 AM]
An hour before the presentation, the Williams team announced the cancellation of part of the plans for the event. They planned to show the new car using an augmented reality app for iOS and Android.
According to the press service of Williams, it will be impossible to do this due to the fact that the team’s systems were hacked by hackers the night before. As a result, Williams employees have already had to remove their app from the App Store and Google Play. https://www.securitylab.ru/news/517174.php
SecurityLab, [3/6/21 9:59 AM]
#useful
“Your message is protected by end-to-end encryption” – such a notification can be seen in the messengers that we use daily. This means that your message is encrypted before it leaves your phone and decrypted only when it is on your interlocutor’s phone.
We all know that the presence of end-to-end encryption does not mean that the correspondence is completely protected from prying eyes.
Stanislav Shakirov, Technical Director of Roskomsvoboda, explained in a short video who and how can read your messages and where data about your correspondence in messengers is stored.
➡️ https://youtu.be/0N0WDCoveMU
There is still a lot of useful information in the Roskomsvobody YouTube channel! Subscribe and protect your online communications!
SecurityLab, [3/6/21 10:00 AM]
Kravtsov did not specify how the system would work and what would be regarded as “negative information”. According to him, by the end of 2021, all schools in cities plan to connect to the Internet at a speed of at least 100 megabits per second, and schools in towns and villages – 50 megabits per second.
Kravtsov also clarified that the ministry has created its own system of secure videoconferencing for schools – “Sphere”, based on the Vkontakte network. It is already being tested in 15 regions. Also, the Ministry creates verified content verified in accordance with the standards, which a teacher can use to teach a particular subject.
https://www.securitylab.ru/news/517177.php
SecurityLab, [3/6/21 12:31 PM]
The Indian government has threatened employees of Facebook, WhatsApp and Twitter with jail in an attempt to quell political protests and expand its powers to disclose the data of users of foreign technology platforms.
According to The Wall Street Journal, the threats of the Indian government are a direct response to the unwillingness of technology companies to comply with the authorities’ demands to delete data related to the protests of Indian farmers and made headlines in international newspapers. At least several written warnings sent to companies mention specific employees from India who face arrest if the companies do not comply with the requirements of the authorities.
https://www.securitylab.ru/news/517179.php
SecurityLab, [3/7/21 7:05 AM]
Thanks to the identified vulnerability in Microsoft software, hackers were able to hack about 60 thousand organizations using Microsoft Exchange Server. “A serious vulnerability has been discovered and it can have far-reaching consequences. The US government is concerned about the large number of victims,” Psahi said.
(https://t.me/iv?url=https://www.securitylab.ru/news/517182.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/517182.php
SecurityLab, [3/7/21 10:50 AM]
The trainee of one of the German prisons will have to pay an impressive sum due to his own unreasonable actions, as a result of which the administration of the penitentiary institution was forced to replace hundreds of locks in prison cells. (https://t.me/iv?url=https://www.securitylab.ru/news/517184.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/517184.php
SecurityLab, [3/7/21 11:31 AM]
Online hackathon DemHack 2.
Participants are expected to make decisions that will help protect personal data and preserve user privacy. The organizers are RosKomSvoboda and Privacy Accelerator.
Teams can implement one of the tasks proposed on the site, for example, create an information security habits tracker or a program to detect hacking of messengers, as well as submit an application with their project.
The last day for accepting applications is March 11, 2021.
Details and registration ➡️ https://demhack.ru
SecurityLab, [3/7/21 12:00 PM]
Russian Prime Minister Mikhail Mishustin has signed a decree allowing Russian universities to remotely conduct intermediate certification using a single biometric system in the 2021-2022 academic year, the government’s press service reports.
(https://t.me/iv?url=https://www.securitylab.ru/news/517185.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/517185.php
SecurityLab, [3/8/21 12:18 PM]
Apple devices come with the Find My feature, which makes it easier for users to search for other Apple products, including iPhone, iPad, iPod touch, Apple Watch, Mac or AirPods. The location tracking function, dubbed “offline search” and introduced in 2019, transmits Bluetooth Low Energy (BLE) technology signals from Apple devices, allowing other devices in the immediate vicinity to transmit their location to the servers of the tech giant.
Offline downloading turns every mobile device into a broadcast beacon specifically designed to track movements through the use of a crowdsourcing mechanism that is anonymous and protected by end-to-end encryption. This is achieved by rotating the keys (pairs of open and closed), which are generated by each device emitting Bluetooth signals, encoding the public key together with it. The key information is subsequently synced via iCloud with all other Apple devices associated with the same user.
https://www.securitylab.ru/news/517199.php
SecurityLab, [3/10/21 10:55 AM]
A team of information security experts was able to gain access to surveillance cameras installed in Tesla, Equinox, medical clinics, prisons and banks. Experts have published images from cameras, as well as screenshots of their ability to gain superuser access to surveillance systems used at Cloudflare and at Telsa headquarters.
(https://t.me/iv?url=https://www.securitylab.ru/news/517309.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/517309.php
SecurityLab, [3/10/21 11:23 AM]
The failure occurred shortly after Roskomnadzor’s statement that the speed of the Twitter microblogging service has been slowed down in Russia since March 10 on all mobile and half of stationary devices. The decision is due to the fact that the company systematically does not comply with the requirements for the removal of content.
https://www.securitylab.ru/news/517317.php
SecurityLab, [3/10/21 4:25 PM]
The slowdown of other resources besides Twitter was discovered by a user of the service and a researcher of network locks under the pseudonym ValdikSS. At first, he noticed the restriction of access to one of the GitHub subdomains, and then came to the conclusion that Roskomnadzor automatically slowed down all sites with t.co in the domain — one of the twitter subdomains.
(https://t.me/iv?url=https://www.securitylab.ru/news/517338.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/517338.php
SecurityLab, [3/10/21 8:15 PM]
Roskomnadzor reported that the failure is not related to the actions of the department to limit the speed of access to the social network Twitter in the territory of the Russian Federation. Violations in the operation of the platforms were recorded not only in Russia, but also in Western Europe, Japan and parts of the USA.
https://www.securitylab.ru/news/517339.php
SecurityLab, [3/11/21 12:20 AM]
The law banning the use of foreign software in schools may come into force as early as December 2021, according to the department’s plan to stimulate the development of the IT industry.
(https://t.me/iv?url=https://www.securitylab.ru/news/517340.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/517340.php
SecurityLab, [3/11/21 8:15 AM]
The Ministry of Finance has proposed to more actively collect biometric data of Russians. It is planned to increase the number of records in the Unified Biometric System (UBS) from 164 thousand to 70 million in two years. This is reported by Kommersant with reference to its own sources.
(https://t.me/iv?url=https://www.securitylab.ru/news/517344.php&rhash=d7509243d58aec)
https://www.securitylab.ru/news/517344.php
SecurityLab, [3/11/21 10:45 AM]
[Forwarded from Announcements of the best IB events (webinars)]
Online seminar “Eset Design Solutions. Two-factor authentication with ESET Secure Authentication. DLP Safetica»
Text:
Axoft and Eset invite you to take part in an online seminar with a live demonstration, which will take place on March 16 at 11:00 (Moscow time).
Within the framework of the online seminar (https://event.axoftglobal.com/eset-10-03?utm_source=securitylab&utm_medium=textlink&utm_campaign=eset_webinar_16_03_2021 ) you will be able to:
* familiarize yourself with each of the solutions in detail,
* highlight the advantages of each of them,
* see all the nuances of working with solutions as part of the demonstration,
* ask all your questions and get practical advice and recommendations from experts.
Speakers:
Alexander Chirkunov, Business Development Manager, Axoft
Alexey Gorelov, Technical Specialist, Axoft
Participation in the event is free of charge, upon prior registration.
SecurityLab, [3/11/21 12:02 PM]
A Vietnamese security researcher has published the first functional PoC exploit for a group of vulnerabilities in Microsoft Exchange called ProxyLogon, which have been actively exploited by hackers of all stripes over the past week.
Over the past few days, several PoC exploits for ProxyLogon have been published on GitHub, but they were either fake or did not work as expected. However, the tool presented by the Vietnamese researcher is fully operational. The authenticity of the exploit has already been confirmed by the well-known security researcher Marcus Hutchins.
https://www.securitylab.ru/news/517349.php
SecurityLab, [3/11/21 12:05 PM]
A team of researchers from universities in Australia, the USA and Israel presented an attack via third-party channels, which is carried out using a browser and does not require the use of JavaScript.
The scientists tested the attack on a wide range of platforms, including devices with new protected M1 chips from Apple.
Details: A team of researchers from universities in Australia, the United States and Israel presented an attack via third-party channels, which is carried out using a browser and does not require the use of JavaScript. The researchers tested the attack on a wide range of platforms, including devices with Apple’s new secure M1 chips.
Prime+Probe 1, JavaScript 0: Overcoming Browser-based Side-Channel Defenses
src: https://arxiv.org/abs/2103.04952#
The researchers called their attack the first browser – based attack on third-party channels that uses only CSS and HTML and works even when JavaScript is completely disabled. It is based on the Prime+Probe method, which allows you to determine which cache sets are accessed by the attacked target, and use this information to output potentially valuable information.
The implementation of such attacks in the browser usually involves the use of JavaScript codes and time measurement. Browser vendors are actively working to protect against them, in particular by limiting or completely blocking the execution of JavaScript codes, as well as by making it more difficult for attackers to measure time. However, an international team of researchers developed a sequence of attacks in which they managed to significantly reduce their dependence on JavaScript and bypass all the security measures implemented by browser manufacturers.
The attack was successfully tested (with varying levels of success depending on the target architecture and existing security tools) in secure browser environments (Tor, Chrome Zero, DeterFox) on devices with Intel, AMD, Samsung, and Apple chips.
All affected vendors have been notified. As reported in Apple, the publication of the results of the study does not cause her any concern.
Prime+Probe-a method that allows you to determine which cache sets are accessed by the attacked program. First, the attacker must fill a certain part of the cache, and then transfer control to the attacked program, after which it can determine which part of the filled cache still belongs to it. An attacker can do this by measuring the access time to the addresses that they used to fill the cache in the first stage of the attack. Thus, if the victim program uses addresses that map to the same cache areas as the attacker, it will push the attacker’s data out of the cache, and he will be able to track this in the third stage of the attack.”
https://www.securitylab.ru/news/517347.php
SecurityLab, [3/12/21 6:42 AM]
How do you use network sandboxes?
Positive Technologies conducts research on how information security specialists use sandboxes: what tasks and how they solve with their help, which threats they identify.
If you work with a network sandbox (vendor does not matter), share your experience – answer a few questions anonymously: https://ru.surveymonkey.com/r/T6M5H9S
A report with the results of the study will be published on the Positive Technologies website.
SecurityLab, [3/12/21 9:20 AM]
Netflix is testing a new security feature that will block access to an account for users who do not live in the same house with the person to whom it belongs.
Judging by the messages on Twitter, the service began to require members of the same family using a common account, but living in different places, to register personal accounts.
https://www.securitylab.ru/news/517401.php
SecurityLab, [3/12/21 11:25 AM]
The official version of the popular 7-Zip archiving program was first released for the Linux operating system.
Linux already had support for the 7-Zip archive file format via a POSIX port called p7zip, but from another developer.
https://www.securitylab.ru/news/517404.php
Links:
SecurityLab: in social networks
Youtube channel – https://www.youtube.com/channel/UCf8Yn-puvoxLsXscTuMBrmA
Facebook – https://www.facebook.com/seclabru
Vkontakte – https://vk.com/public47494392
twitter – https://twitter.com/securitylabnews
Announcements of the best IB events – https://t.me/secwebinars
NGFW discussion – https://t.me/ngfw_russia
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!