- update: 2024-06: ed25519 is currently “the way to go”
- ssh can be regarded as “critical core infrastructure”
- time spend on it’s security is time well spend
- time + money well invested:
- https://www.openssh.com
- https://github.com/openssh
- current manpage: ssh.man.txt
- WARNING: this howto guide IS MOST LIKELY INCOMPLETE!
- WARNING! WHEN RUNNING THE SCRIPT: BE PATIENT! REGENERATING SSH KEYS (DEPENDING ON CPU SPEED) CAN TAKE UP TO 10MIN!
- WARNING! ALL RUNNING SSH SESSIONS MIGHT GET DISCONNECTED!
- as cyber security is constantly in motion and new attacks, threats, exploits being developed daily (thanks to AI even faster)
- please search the net for howtos and guides and apply those and publish the findings 😀 (does it work, does it not work?
- interesting find also here
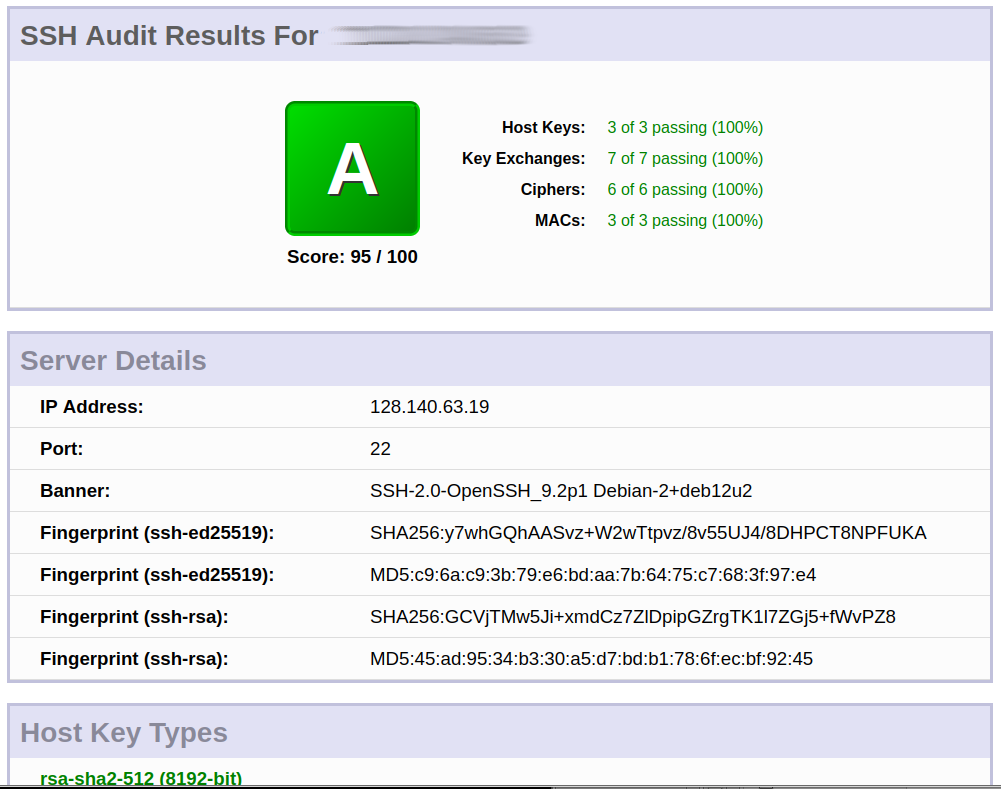
- do audits: of the ssh server
- sshaudit.com
- it keeps displaying “failed”
- so incorporated it’s guide in the below script that can be run line by line and restart ssh to see if everything is still okay :
- ubuntu’s netplan has a nice feature: when the connection is lost, restore last settings
- have an alternative way to restart ssh or the server (“hardware console”) before trying this!
- server passes the “standard” test
- but fails on sshaudit.com hardened hardened OpenSSH 9.2 test
- sshaudit.com
- it is recommended to move the port away from 22
- because it’s the first port that will be scanned for sshd
public+private key auth is better than strong passwords
but strong passwords are better than weak passwords. the reader of this blog won’t believe how many ssh servers get compromised because of brute-force password attacks (the faster the server and the faster the bandwidth of the server and the more lose the ssh settings the faster a weak password can be brute-force cracked: Avocado123 is not a strong password)
- use at least 10 digit password with a combination of:
- that includes lowercase letters
- UPPERCASE LETTERS
- Special chars: *’!”§?_- (of the native langauge? 😀 like ü?)
- 894738971 numbers
https://bitwarden.com/password-strength/
Your password strength: strong
Estimated time to crack: 11 months
12 characters containing:
https://www.passwordmonster.com/
Time to crack your password:
2 years
the script:
to automate a wee bit: WARNING! this script will seem to “hang” but it’s not it actually takes most CPUs a long time to recalc strong ssh host keys.
hostnamectl; # tested on Operating System: Debian GNU/Linux 12 (bookworm) Kernel: Linux 6.1.0-18-amd64 Architecture: x86-64 # DEFINATELY enable ssh logging (not enabled per default on Debian) # start a screen session su - root apt update screen -S hardssh # so if current session gets disconnectd it is possible to resume like this # show running sessions screen -ls There is a screen on: 20712.hardssh (03/16/2024 09:20:36 PM) (Detached) 1 Socket in /run/screen/S-root. screen -R 20712.hardssh # after running this script during re-login user see this warning @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ # simply remove the "known" host key from client like this ssh-keygen -f "/home/user/.ssh/known_hosts" -R "[ip.of.ser.ver]:22" vim /scripts/ssh_hardening.sh #!/bin/bash echo "==== sshd hardening script v1 ====" echo "=== sshd hardening: let's make ssh a bit safer by tweaking (WARNING: root login will be disabled!) ===" echo "=== please input space separated list of users that are allowed to login: ===" read users echo "AllowUsers $users" >> /etc/ssh/sshd_config sed -i 's/[^"]*PermitRootLogin[^"]*/PermitRootLogin no/g' /etc/ssh/sshd_config sed -i 's/[^"]*SyslogFacility[^"]*/SyslogFacility AUTH/g' /etc/ssh/sshd_config sed -i 's/[^"]*LogLevel[^"]*/LogLevel INFO/g' /etc/ssh/sshd_config sed -i 's/[^"]*LoginGraceTime[^"]*/LoginGraceTime 3m/g' /etc/ssh/sshd_config sed -i 's/[^"]*StrictModes[^"]*/StrictModes yes/g' /etc/ssh/sshd_config sed -i 's/[^"]*MaxAuthTries[^"]*/MaxAuthTries 3/g' /etc/ssh/sshd_config sed -i 's/[^"]*ChallengeResponseAuthentication[^"]*/ChallengeResponseAuthentication no/g' /etc/ssh/sshd_config sed -i 's/[^"]*PasswordAuthentication[^"]*/PasswordAuthentication no/g' /etc/ssh/sshd_config sed -i 's/[^"]*UsePAM[^"]*/UsePAM no/g' /etc/ssh/sshd_config sed -i 's/[^"]*PubkeyAuthentication [^"]*/PubkeyAuthentication yes/g' /etc/ssh/sshd_config sed -i 's/[^"]*PrintMotd [^"]*/PrintMotd no/g' /etc/ssh/sshd_config sed -i 's/[^"]*X11Forwarding[^"]*/X11Forwarding no/g' /etc/ssh/sshd_config sed -i 's/[^"]*Subsystem\s\+sftp\s\+\/usr\/lib\/openssh\/sftp-server/# &/g' /etc/ssh/sshd_config echo "ChallengeResponseAuthentication no" >> /etc/ssh/sshd_config echo "# disable SSH protocol version 1, which has known security vulnerabilities" >> /etc/ssh/sshd_config echo "Protocol 2" >> /etc/ssh/sshd_config echo "# set idle timeout interval: automatically disconnect idle ssh sessions after a certain period of inactivity" >> /etc/ssh/sshd_config echo "ClientAliveInterval 300" >> /etc/ssh/sshd_config echo "ClientAliveCountMax 2" >> /etc/ssh/sshd_config echo "PermitEmptyPasswords no" >> /etc/ssh/sshd_config # re-generate the RSA and ED25519 keys rm -fv /etc/ssh/ssh_host_* echo "=== sshd-hardening: regenerating host keys: WARNING! THIS WILL TAKE A WHILE! PLEASE BE PATIENT :) [y,n] ===" read input if [[ $input == "Y" || $input == "y" ]]; then ssh-keygen -t rsa -b 8192 -f /etc/ssh/ssh_host_rsa_key -N "" ssh-keygen -t ed25519 -f /etc/ssh/ssh_host_ed25519_key -N "" fi echo "... remove small diffie-hellman moduli" awk '$5 >= 3071' /etc/ssh/moduli > /etc/ssh/moduli.safe mv -v /etc/ssh/moduli.safe /etc/ssh/moduli echo "...restrict supported key exchange, cipher, and mac algorithms" echo -e "# restrict key exchange, cipher, and mac algorithms, as per sshaudit.com\n# hardening guide\nKexAlgorithms sntrup761x25519-sha512@openssh.com,curve25519-sha256,curve25519-sha256@libssh.org,gss-curve25519-sha256-,diffie-hellman-group16-sha512,gss-group16-sha512-,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha256\n\nCiphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com,aes256-ctr,aes192-ctr,aes128-ctr\n\nMACs hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,umac-128-etm@openssh.com\n\nHostKeyAlgorithms sk-ssh-ed25519-cert-v01@openssh.com,ssh-ed25519-cert-v01@openssh.com,rsa-sha2-512-cert-v01@openssh.com,rsa-sha2-256-cert-v01@openssh.com,sk-ssh-ed25519@openssh.com,ssh-ed25519,rsa-sha2-512,rsa-sha2-256\n\nCASignatureAlgorithms sk-ssh-ed25519@openssh.com,ssh-ed25519,rsa-sha2-512,rsa-sha2-256\n\nGSSAPIKexAlgorithms gss-curve25519-sha256-,gss-group16-sha512-\n\nHostbasedAcceptedAlgorithms sk-ssh-ed25519-cert-v01@openssh.com,ssh-ed25519-cert-v01@openssh.com,sk-ssh-ed25519@openssh.com,ssh-ed25519,rsa-sha2-512-cert-v01@openssh.com,rsa-sha2-512,rsa-sha2-256-cert-v01@openssh.com,rsa-sha2-256\n\nPubkeyAcceptedAlgorithms sk-ssh-ed25519-cert-v01@openssh.com,ssh-ed25519-cert-v01@openssh.com,sk-ssh-ed25519@openssh.com,ssh-ed25519,rsa-sha2-512-cert-v01@openssh.com,rsa-sha2-512,rsa-sha2-256-cert-v01@openssh.com,rsa-sha2-256" >> /etc/ssh/sshd_config echo "... restarting ssh service" systemctl restart ssh echo "... restarting ssh service the other way" service ssh restart
self audit:
su - root
apt install ssh-audit
ssh-audit ip.of.server.audit
creditz
- STANDARDS
- S. Lehtinen and C. Lonvick, The Secure Shell (SSH) Protocol Assigned Numbers, RFC 4250, January 2006.
- T. Ylonen and C. Lonvick, The Secure Shell (SSH) Protocol Architecture, RFC 4251, January 2006.
- T. Ylonen and C. Lonvick, The Secure Shell (SSH) Authentication Protocol, RFC 4252, January 2006.
- T. Ylonen and C. Lonvick, The Secure Shell (SSH) Transport Layer Protocol, RFC 4253, January 2006.
- T. Ylonen and C. Lonvick, The Secure Shell (SSH) Connection Protocol, RFC 4254, January 2006.
- J. Schlyter and W. Griffin, Using DNS to Securely Publish Secure Shell (SSH) Key Fingerprints, RFC 4255, January 2006.
- F. Cusack and M. Forssen, Generic Message Exchange Authentication for the Secure Shell Protocol (SSH), RFC 4256, January 2006.
- J. Galbraith and P. Remaker, The Secure Shell (SSH) Session Channel Break Extension, RFC 4335, January 2006.
- M. Bellare, T. Kohno, and C. Namprempre, The Secure Shell (SSH) Transport Layer Encryption Modes, RFC 4344, January 2006.
- B. Harris, Improved Arcfour Modes for the Secure Shell (SSH) Transport Layer Protocol, RFC 4345, January 2006.
- M. Friedl, N. Provos, and W. Simpson, Diffie-Hellman Group Exchange for the Secure Shell (SSH) Transport Layer Protocol, RFC 4419, March 2006.
- J. Galbraith and R. Thayer, The Secure Shell (SSH) Public Key File Format, RFC 4716, November 2006.
- D. Stebila and J. Green, Elliptic Curve Algorithm Integration in the Secure Shell Transport Layer, RFC 5656, December 2009.
- A. Perrig and D. Song, Hash Visualization: a New Technique to improve Real-World Security, 1999, International Workshop on Cryptographic Techniques and E-Commerce (CrypTEC ’99).
- AUTHORS
- OpenSSH is a derivative of the original and free ssh 1.2.12 release by Tatu Ylonen. Aaron Campbell, Bob Beck, Markus Friedl, Niels Provos, Theo de Raadt and Dug Song removed many bugs, re-added newer features and created OpenSSH. Markus Friedl contributed the support for SSH protocol versions 1.5 and 2.0 (BSD November 28, 2022)
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!