scroll down to: “how to access user-dev-admin’s home network boxes from anywhere via reverse-ssh-tunnel! :D”
ssh tunnel remote deviceD’s port
access a device’s port that is only available via a specific machine 😀
or in other words:
ssh-tunnel port of deviceD that is connected only to pcB to localhost:8080 of pcA
on the local lan:
-
- there is a deviceD, but it’s not ssh capable but has a web interface on port 80 for example a printer
- the deviceD is only accessible via pcB because they are both behind a firewall-router (also deviceD is very old and explosing ports of devices that are very old (EoL = out of security update maintenance) ain’t a good idea)
solution:
- in this UseCase pcB is the proxy to deviceD
- open a TCP port on firewall-router to forward this to pcB
- pcA establishes a ssh connection to pcB that effectively tunnels port 80 of deviceD to localhost:8080 of pcA
- allowing direct access of deviceD:80 via localhost:8080 of pcA
sounds like magic?
let’s go:
# step1 on pcA) connect through firewall-router to pcB ssh -L 8080:ip.of.deviceD:80 user@ip.of.firewall.router # or if there is no firewall-router ssh -L 8080:ip.of.deviceD:80 user@ip.of.pcB # leave terminal open
# step2 also on pcA) open browser and go to http://localhost:8080 fox http://localhost:8080 # the web interface of deviceD should show up :)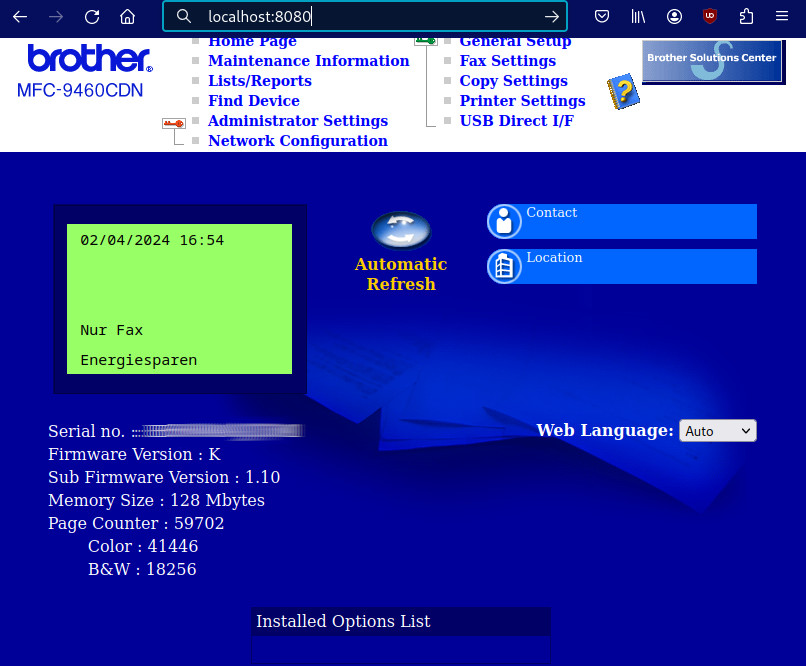
more crazy ssh magic: how to access user-dev-admin’s home network boxes from anywhere via reverse-ssh-tunnel! 😀
- pcA and pcB are connected to the internet
- but there is no open ports on any firewall-router and for security reasons there shall not be any open ports
- but there is a normal OpenSSH enabled SRVER (SRV) somewhere on the internet
solution:
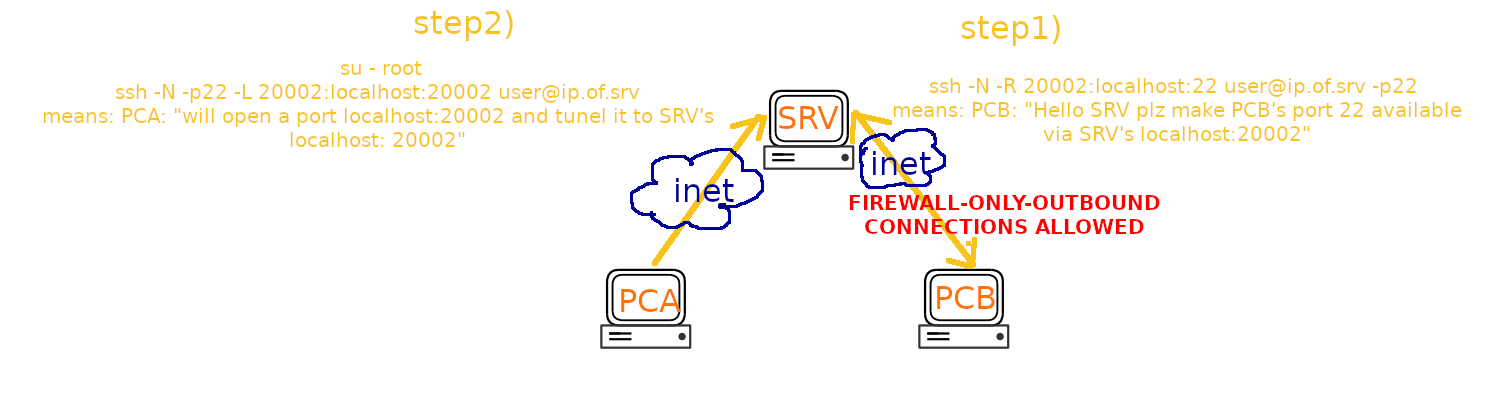
- pcA “client” will connect via SRV (proxy1) to pcB (proxy2) and even open a vnc viewer session to see pcB’s desktop
- this is basically the a bit tricky open source’s admin’s replacement for teamviewer 😀
- sounds like magic?
- get a vm server somwhere
- make sure there is “username” on pcA, pcB and SRV and ssh keys allow fast and easy login from pcA and pcB to SRV
let’s go:
-
on SRV:
- ssh into SRV and monitor what’s going on
-
while true; do netstat -tulpn; sleep 1; clear; done;
-
on pcB:
- setup vnc server
- apt install autossh
- open a terminal (1) run this and keep it open:
-
# in order to keep the connection from pcB to SRV alive # allow remote reverse-ssh access to ssh port of pcB su -c 'autossh -M 0 -o "ServerAliveInterval 30" -o "ServerAliveCountMax 3" -fN -T -R 20002:localhost:22 user@ip.of.srv -p22' user# if everything works, there will be no output # allow remote reverse-ssh access to 5900 (VNC) port of pcB su -c 'autossh -M 0 -o "ServerAliveInterval 30" -o "ServerAliveCountMax 3" -fN -T -R 20003:localhost:5900 user@ip.of.srv -p22' user -
# also here if everything works, there will be no output
- the only visible output is onSRV this should be:
-
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:20002 0.0.0.0:* LISTEN 14704/sshd: user tcp 0 0 127.0.0.1:20003 0.0.0.0:* LISTEN 14745/sshd: user
-
on pcA:
-
apt install tigervnc-viewer - open a terminal(1) run this and leave it open
-
ssh -N -p22 -L 20002:127.0.0.1:20002 user@ip.of.srv
-
- open another terminal(2)
-
ssh -p20002 user@127.0.0.1The authenticity of host ‘[127.0.0.1]:20002 ([127.0.0.1]:20002)’ can’t be established.
ED25519 key fingerprint is SHA256:78e90f78d9f7d…
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:72: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added ‘[127.0.0.1]:20002’ (ED25519) to the list of known hosts.
user@127.0.0.1’s password: - # hurray! 🙂 response! 🙂 user dev admin shall now be able to ssh-login-to pcB from pcA via SRV 🙂
-
- open another terminal(3) run this and leave it open
-
ssh -N -p22 -L 20003:127.0.0.1:20003 user@ip.of.srv
-
- open another terminal(4)
-
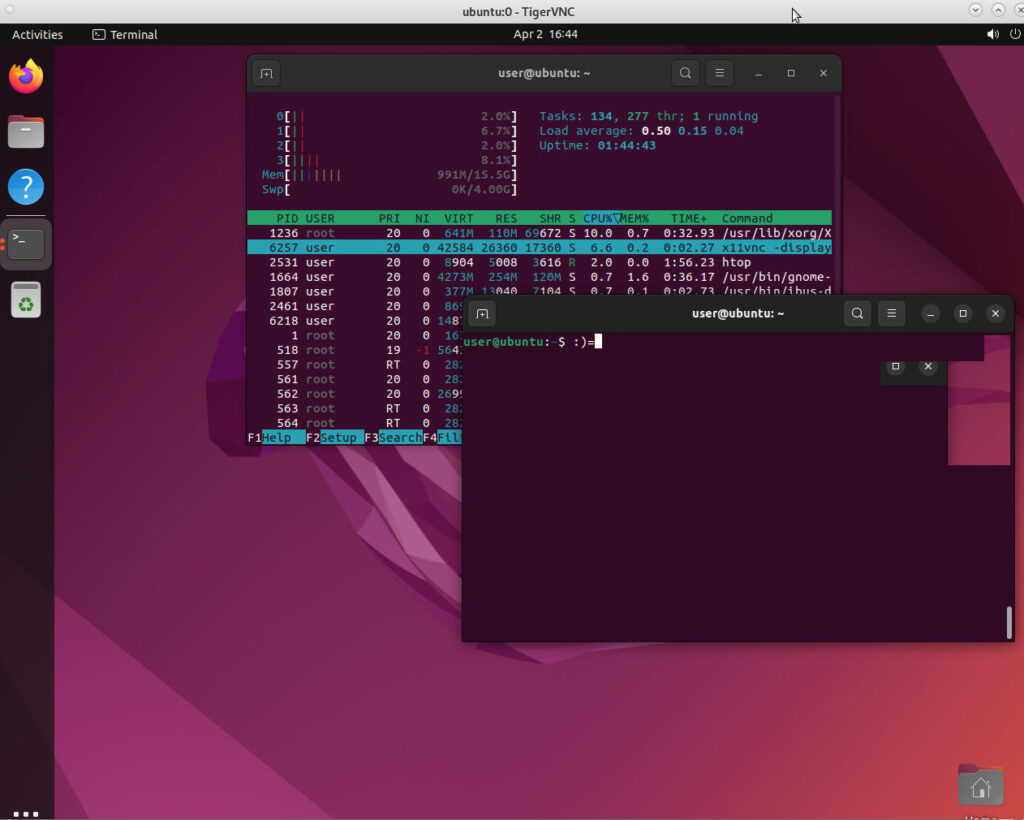
hurray it works 🙂
won’t be 100 FPS but it works 🙂
this means: access user-dev-admin’s home network boxes from anywhere! 😀
script it
vim /scripts/ssh.tunnels.sh #!/bin/bash echo "=== tunneling local port 20002 for ssh port 22 access of ubuntu ===" ssh -N -p22 -L 20002:127.0.0.1:20002 username@ip.of.srv & echo "=== tunneling local port 20003 for vnc port 5900 access of ubuntu ===" ssh -N -p22 -L 20003:127.0.0.1:20003 username@ip.of.srv & echo "... keep this terminal(1) open, open a new terminal(2)" echo "... in terminal(2) to connect to remote hosts ssh type: ssh -v -p 20002 username@127.0.0.1" echo "... and start a vnc server on port 5900" echo "... in terminal(3) to connect to remote hosts vnvserver: vncviewer localhost:20003" echo "... alternatively on headless server: install xpra on server and client and use terminal(4) like this xpra start ssh/username@127.0.0.1:20002 --start-child=firefox" echo "too start a gui program on server but show it's output on local client :) *ssh*magic*"
celebrate
but that is temporary?
in order to make pcB accessible permanently it would be required to start the autossh on boot
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!