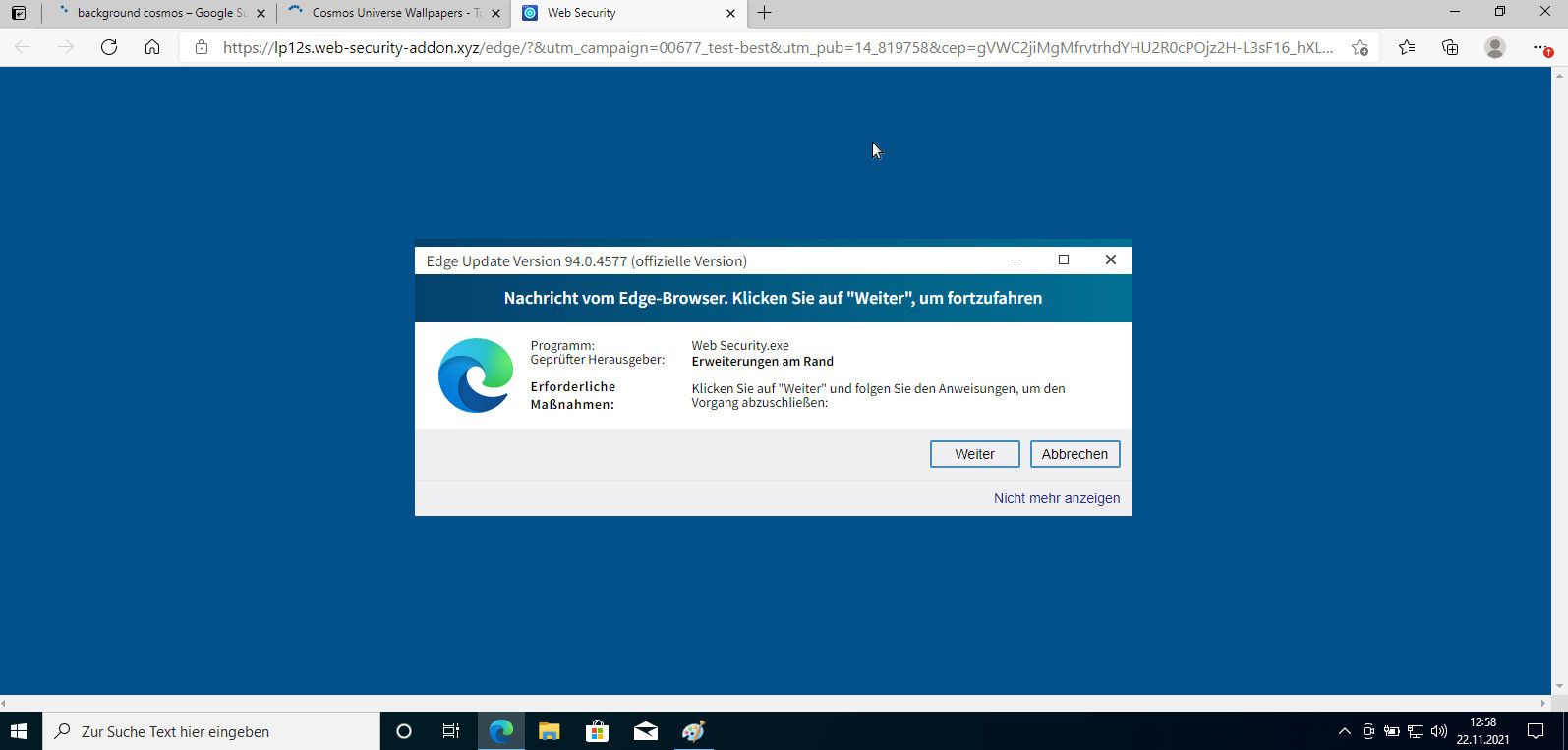
just for info: this is NOT my PC, not using Windows 10 (Windows 7 only for gaming X-D) what the user sees is a perfectly windows fake update message, that says “Edge Update Version 94.0.4577 (official Version)” so the user […]
warning: no guarantee of completeness! contains ads! (but owner of blog get’s nothing, maybe source of source does) Are the odds against the (itsec) defenders? It certainly feels that way, because no human can ever find all bugs, so Fuzzing […]
affected CPUs: (src: intel.com) Intel® Processors supporting SGX2: Code Name Product Collection Ice Lake Xeon-SP (HCC, XCC) 3rd Gen Intel® Xeon® Scalable processor family Ice Lake 10th Generation Intel® Core™ Processor Family Gemini Lake Intel® Pentium® Processor Silver Series, Intel® […]
the wiki: https://en.wikipedia.org/wiki/OWASP the top 10: https://owasp.org/www-project-top-ten/2017/Top_10.html the ebook: https://github.com/OWASP/owasp-mstg/releases/download/v1.2/OWASP_MSTG-1.2.pdf the text: https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/02-Configuration_and_Deployment_Management_Testing/01-Test_Network_Infrastructure_Configuration the conferences: https://owasp.org/www-board/ https://www.blackhat.com/us-21/ the costs: https://training.owasp.org/ 2-part Training: $505 Member 2-part Training: $455 * For member discount code contact events ÄT owasp DOOOT com https://www.udemy.com/course/intro-to-bug-bounty-by-nahamsec/ it’s […]
updates are a bless (fixes to problems, keep system secure from hackerz) but also a curse (it might break things) on systems that follow the UNIX K.I.S.S principle, they should “just work”, to the extreme of (kernel) live patching (currently […]
in short: humans per default, without an education might just be “better” apes. Some parts of mankind behave very primitive and clearly show no signs of higher intelligence or education. The troubles start, when the tools become more and more […]
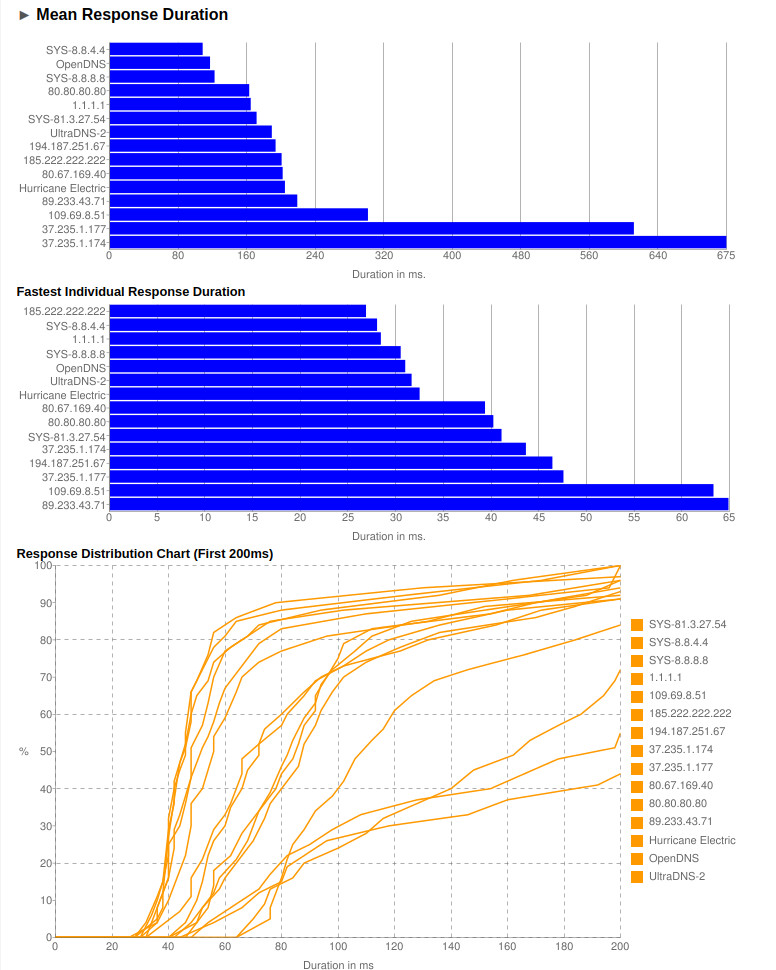
every user want’s a fast & responsive internet. BIND and DNS – the Phonebook of the internet – Berkeley Internet Name Domain – how to benchmark dns servers (find fastest) – LibreDNS There is nothing more anoying than slow loading […]
Yes! What RSS does NOT stand for “Rashtriya Swayamsevak Sangh” , “Nathuram Godse, who assassinated Gandhi, on January 30, 1948, was a member of the Rashtriya Swayamsevak Sangh, or R.S.S., a violent right-wing organization that promotes Hindu supremacy.” (src: HolyCow!) […]
“In 2019, spending in the cybersecurity industry reached around $40.8 billion, with forecasts suggesting that the market will eclipse 54 billion U.S. dollars by 2021 as the best-case scenario, taking into account the coronavirus (COVID-19) impact. As many organizations around […]
SecurityLab, [12.01.21 15:23] The developer of the Salaat First (Prayer Times) app, which reminds Muslims when to pray, recorded and sold detailed information about their location to a data broker without the users ‘ knowledge, who in turn sold the […]
why are those data leaks problematic? because scammers and spammers will use this data to even better scam (social engineer) the affected users that is why it is essential to give those platforms (if the user needs them) as little […]
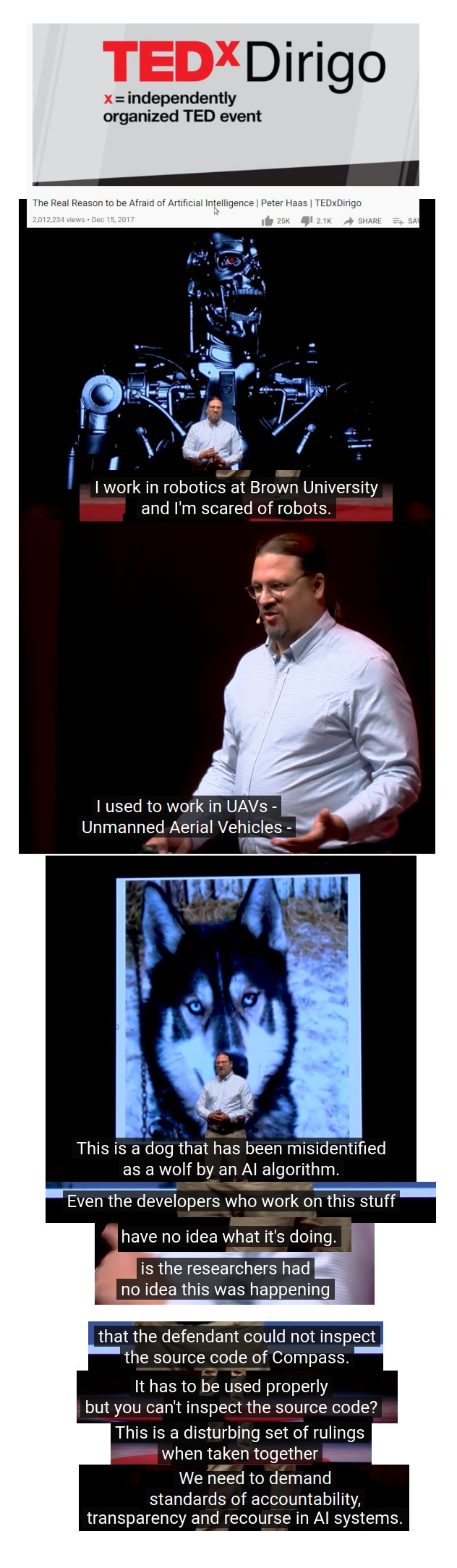
computers are no way perfect: the rise of the machines: who is scared of killer robots? who is scared of doctors, judges and police blindly trusting in AI and computer output? “we are driving in (heavy) rain right now with […]
scroll down to ENGLISH “Zehntausende Mail-Server wegen Exchange-Lücke gehackt. Wegen einer vor wenigen Tagen bekanntgewordenen Sicherheitslücke sind laut US-Medienberichten Zehntausende E-Mail-Server von Unternehmen, Behörden und Bildungseinrichtungen Opfer von Hacker-Attacken geworden. “Deutsche Unternehmen sind im internationalen Vergleich besonders stark von dieser […]
SecurityLab, [22.12.20 10:00] Google has explained the reasons for the massive failure of its services that took place last week. Recall that on December 14 of this year, users around the world for 47 minutes could not access Gmail, YouTube […]
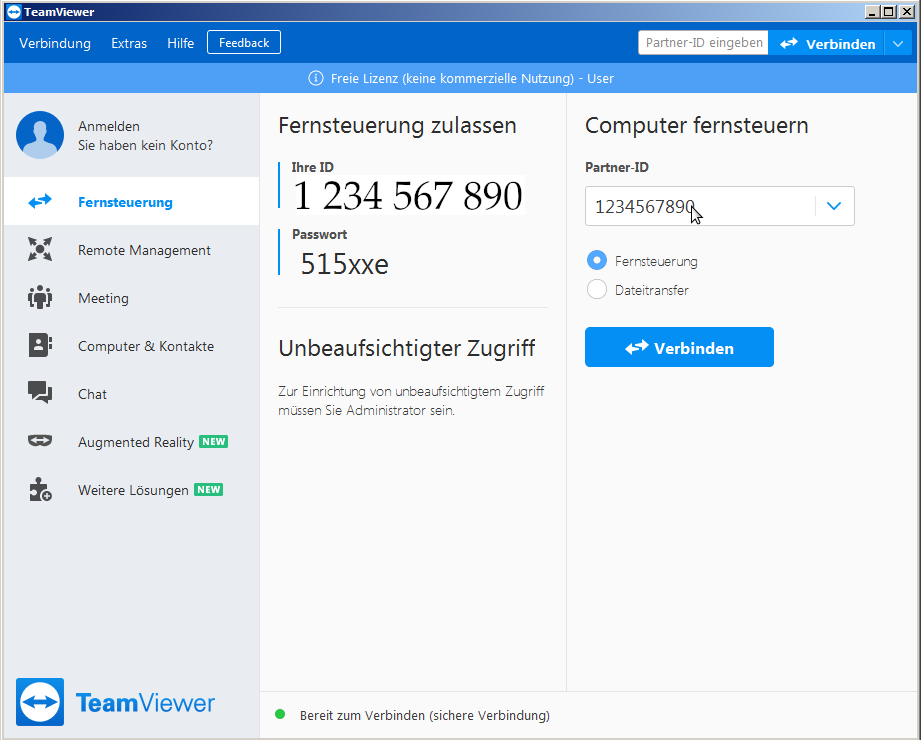
convenience vs security problem: remote support via internet in COVID19 pandemic days is basically a must for many companies, but does it have to run non-stop on computers that control sensitive machines and systems such as energy and water-supply? ABSOLUTELY […]
not sure if the news rang through… the Amazon Cloud (AWS) guy will be the new CEO of Amazon. What cloud? Amazon “cloud” Hetzner “cloud” cloud (centralized digital infrastructure) can be designed / implemented in different ways. from: the user/admin […]
SecurityLab, [03.12.20 11:15] Vulnerabilities in open source software can go undetected for more than four years before being discovered. According to the GitHub State of the Octoverse annual report, the use of open source projects, components, and libraries is more […]
accroding to BleepingComputer: “zero-day vulnerability in their VPN products” (so not FallOut of SolarWinds-orion-auto-update-software-supply-chain) “…have information about hacking of a well-known firewall vendor and other security products by this they are silent and do not release press releases for their […]
update: 2024-04: having problem connecting to camera with vlc? (rstp not well documented or not working at all? try this: easy camera stream identification with ONVIF: it is a DAMN hussle, because EVERY camera vendor does it’s own rstp://user:password:ip.ad.dr.ess:/some/url/stream and […]
proof wrong but, sorry to say but… would it not be possible that messing with bacteria DNA that by accident scientists creates new pathogens? new deadly diseases? so it’s one thing to write a program that dos “hello world” and […]
SecurityLab, [02.11.20 11:52] The 50-year-old businessman (Hunter Biden?) in April 2019 brought his device to the IT store Mac Shop in Delaware for repair, but never returned to pick it up. The device was soon seized by the FBI. According […]
DNS servers are the “yellow pages” “phone book” of the internet. whoever is running DNS servers get’s to know all queries send (what client is requesting and probably connecting to what address… basically: what websites the user have visited, this […]
all internet connected devices need regular maintenance and security updates (especially those directly accessible to the internet (without proxy (hopefully that proxy gets regular security updates)) it is a good idea to 1) backup then 2) update, in case user […]
“Apple Wireless Direct Link (AWDL) is a key protocol in Apple’s ecosystem used by over one billion iOS and macOS devices for device-to-device communications. AWDL is a proprietary extension of the IEEE 802.11 (Wi-Fi) standard and integrates with Bluetooth Low […]
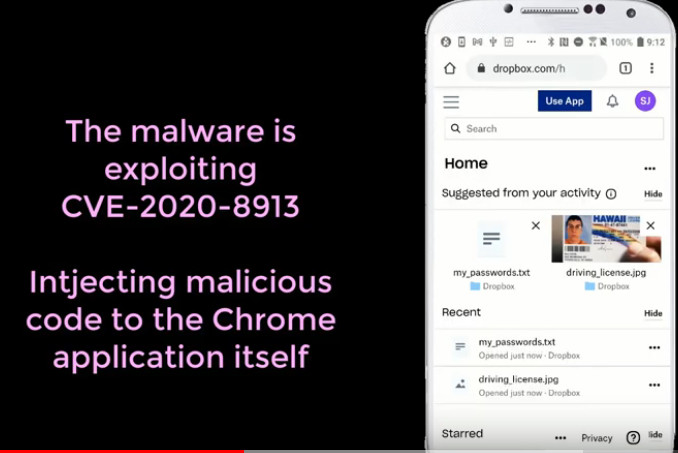
Overview Recent 360Netlab unknown threat detection system to capture to a group of unknown malicious families of the sample, which a number of samples supported CPU architectures are x86(32/64), ARM(32/64), MIPS(MIPS32/MIPS-III) as well as PPC, after our analysis, which is […]
contains advertisement. to be honest, it is hard to keep up the speed at which cyber incidents are reported. here is the latest take on “Russian IT Sec Updates”. have phun! SecurityLab, [28.09.20 08:20] Last month, TikTok developers rolled […]
SecurityLab, [14.07.20 15:35] The Electronic Frontier Foundation (EFF) has unveiled a new database demonstrating how and where us law enforcement agencies use tracking technologies. A map of the use of tracking technologies in the United States is presented (https://www.securitylab.ru/news/510018.php) SecurityLab, […]
All SmartPhones are spies! that’s why Merkel keeps the Nokia from 1995 (even if that device is spied on as well, because it can not end2end encrypt sms or phone calls (*FAIL*! X-D)) Putin does not have a mobile phone […]
The Age of Surveillance Capitalism: “be careful what you reveal to your friend” (the internet) https://irlpodcast.org/season4/episode5/ “where it has gone from defending America to controlling it” data google tries to collect from users: (it is probably only the tip of […]
SecurityLab, [04.06.20 15:05] The Chinese-language cybercrime group Cycldek (also known as Goblin Panda or Conimes) has developed the malicious tool USBCulprit to carry out attacks on physically isolated systems and steal confidential data. Cycldek APT has developed a malware for […]