- all internet connected devices need regular maintenance and security updates (especially those directly accessible to the internet (without proxy (hopefully that proxy gets regular security updates))
- it is a good idea to 1) backup then 2) update, in case user needs to roll back, if update breaks things / brings about new dysfunctionalities
- all devices / services / applications sending & receiving messages (fax, sms, mail, instant…) need regular maintenance and security updates
- software minimalism is key
- strictly separate work-devices from private-play-and-surf-and-install-the-latest-stuff devices
- a banking application should NEVER be installed on a device that also does mail and games
- even physically separated networks (gaming network, banking network, mail network) recommended
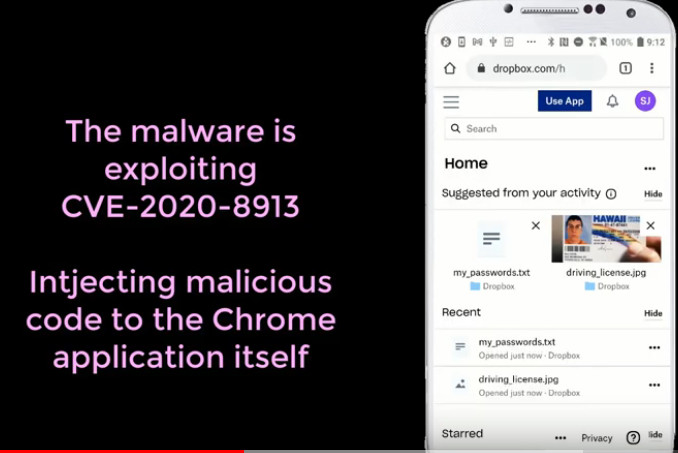
the exploit/attack vector:
| ID | CVE-2020-8913 |
| Summary | A local, arbitrary code execution vulnerability exists in the SplitCompat.install endpoint in Android’s Play Core Library versions prior to 1.7.2. A malicious attacker could create an apk which targets a specific application, and if a victim were to install this apk, the attacker could perform a directory traversal, execute code as the targeted application and access the targeted application’s data on the Android device. We recommend all users update Play Core to version 1.7.2 or later. |
src: https://cve.circl.lu/cve/CVE-2020-8913
“If a malicious application exploits this vulnerability, it can gain code execution inside popular applications and have the same access as the vulnerable application.
The possibilities are limited only by our creativity. Here are just a few examples:
- Inject code into banking applications to grab credentials, and at the same time have SMS permissions to steal the Two-Factor Authentication (2FA) codes.
- Inject code into Enterprise applications to gain access to corporate resources.
- Inject code into social media applications to spy on the victim, and use location access to track the device.
- Inject code into IM apps to grab all messages, and possibly send messages on the victim’s behalf.”
imho: design flaw
reusable libraries should NEVER be compiled into Applications
reusable libraries should be part of the OS that get’s regular updates / security updates with the OS
different versions of the libraries required by different applications can reside on the same OS installation next to each other (as long updates fixes security problems also in older versions… otherwise older version needs to be retired = Apps that do not want to use newer versions of the Library will become dysfunct, but security is saved)
Links:
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!