affected CPUs: (src: intel.com)
Intel® Processors supporting SGX2:
| Code Name | Product Collection |
| Ice Lake Xeon-SP (HCC, XCC) | 3rd Gen Intel® Xeon® Scalable processor family |
| Ice Lake | 10th Generation Intel® Core™ Processor Family |
| Gemini Lake | Intel® Pentium® Processor Silver Series, Intel® Celeron® Processor J Series, Intel® Celeron® Processor N Series |
“But when the enclave is also handling in-enclave exceptions (e.g., timer interrupt or division-by-zero), the vulnerability provides a brief window for a local attacker to hijack the control flow of execution by injecting an asynchronous exception immediately after the enclave is entered.
Armed with this capability, the adversary can then corrupt the in-enclave memory to leak sensitive data such as RSA private keys or execute malicious code.”
src: https://thehackernews.com/2021/10/researchers-break-intel-sgx-with-new.html
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00548.html
https://github.com/lsds/spectre-attack-sgx
Cui J, Zhijingcheng Yu J, Shinde S, Saxena P, Cai Z SmashEx: Smashing SGX Enclaves Using Exceptions. Proceedings of the ACM Conference on Computer and Communications Security (CCS) November 2021 doi: 10.1145/3460120.3484821 (Publication still pending. Link to the list of papers to be presented). (src: sciena.ch)
- “It demonstrates the importance of a fundamental property of safe atomic execution that is required on this interface.”
- “In the absence of atomicity, we show that asynchronous exception handling in SGX enclaves is complicated and prone to re-entrancy vulnerabilities.”
- “Our attacks do not assume any memory errors in the enclave code, side channels, or application-specific logic flaws.”
- “We concretely demonstrate exploits that cause arbitrary disclosure of enclave private memory and code-reuse (ROP) attacks in the enclave.”
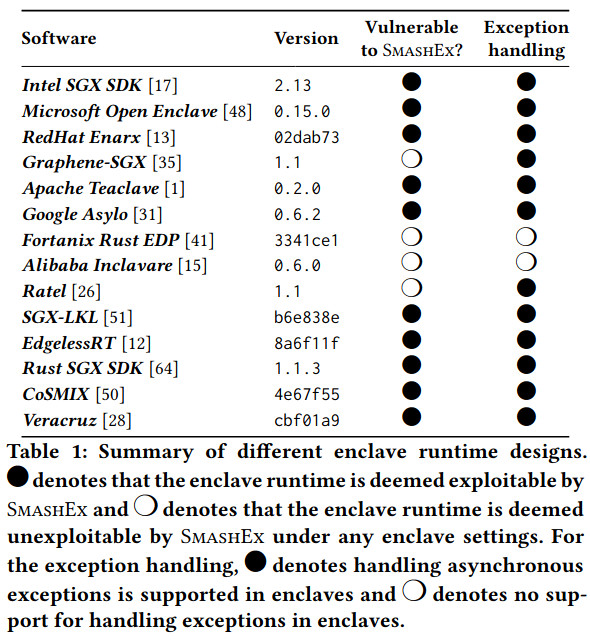
- “We show reliable exploits on two widely-used SGX runtimes, Intel SGX SDK and Microsoft Open Enclave, running OpenSSL and cURL libraries respectively. We tested a total of 14 frameworks, including Intel SGX SDK and Microsoft Open Enclave, 10 of which are vulnerable.”
- “We discuss how the vulnerability manifests on both SGX1-based and SGX2-based platforms”
the whitepaper: https://arxiv.org/pdf/2110.06657.pdf
https://www.sigsac.org/ccs/CCS2021/index.html
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!