convenience vs security problem:
remote support via internet in COVID19 pandemic days is basically a must for many companies, but does it have to run non-stop on computers that control sensitive machines and systems such as energy and water-supply?
ABSOLUTELY NOT!
to connect those systems to the internet is asking for trouble.
Oldsmar, Florida: “Gualtieri told the media that someone (they don’t know who yet) remotely accessed a computer for the city’s water treatment system (using TeamViewer) and briefly increased the amount of sodium hydroxide (a.k.a. lye used to control acidity in the water) to 100 times the normal level.”
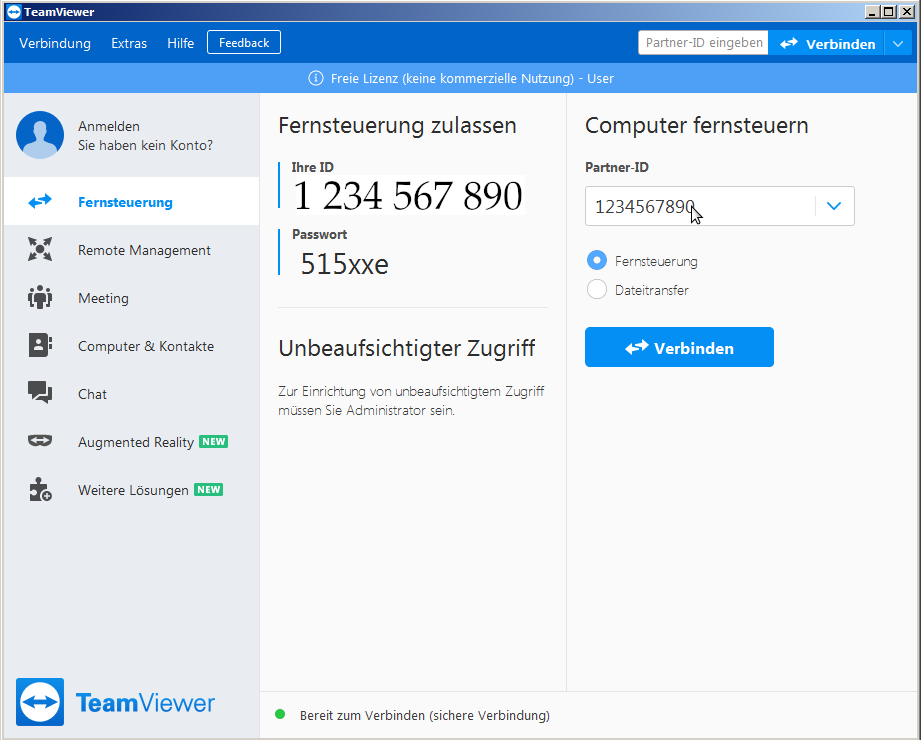
TeamViewer (now with automatic updates) generates a unique 10x digit per-device ID and also generates a password for every new session (but it is possible to also assign a fixed password (that is probably what was done in the water-treatment plant… probably with a bad too easy to guess password… because some employee wanted to remote admin that machine))
There is also a portable version, that does not need installation and will not keep running in the background as a service, but for users that want to remote-administer their machines… that aint’ suitable, is it?
about teamviewer
“The software is distributed by the German company TeamViewer AG, which was founded in Göppingen, Germany in 2005. As of 2018, TeamViewer has local representations in Australia and the United States.
Two outside investments were placed in TeamViewer since 2010. The Durham, North Carolina-based company GFI Software acquired a majority stake in TeamViewer in 2010. The London-based private equity firm Permira took over GFI’s stake in TeamViewer in 2014.[23]”
“In 2020, TeamViewer software has seen significant extra demand caused by the COVID-19 lockdown and the shift of millions of people to remote work.[24]”
“Remote service scams using TeamViewer
TeamViewer and similar services have been used to commit technical support scams via telephone calls.
People are called, either at random or from a list, by criminals claiming to represent a computer support service”
usually goes like this:
caller: “Hello this is Microsoft, you have a Virus on your computer… please do this and that”
user: “wow! Microsoft calls me, must be important…” X-D
“that has identified the victim’s computer as being infected by malware.
Most often, the criminals pretend as if they represent well known software companies.”
“They then ask the victim to give them access to their computer by installing a remote control service, which can allow the attacker to take over the computer in real time and infect the computer with malware or to delete or copy personal files or to pretend to have removed malware for which they charge a fee.”
“A Wired journalist investigating the scams was asked by a scammer to install TeamViewer.[26][27]”
“It was reported that ransomware programs were utilizing TeamViewer as a tool to obtain remote access to infected machines.[28][29]”
“In the United Kingdom, the Internet service provider TalkTalk blocked many remote access tools to protect its customers from remote service scams.[30]”
“Account access misuse and possible breach”
“In June 2016, hundreds of TeamViewer users reported having their computers accessed by an unauthorized address in China and bank accounts misappropriated.[31]
TeamViewer attributed the outcome to user’s “careless password use” and denied all responsibility, saying “neither was TeamViewer hacked nor is there a security hole, TeamViewer is safe to use and has proper security measures in place.
Our evidence points to careless use as the cause of the reported issue, a few extra steps will prevent potential abuse.”[32]
Following the reported misuse, TeamViewer went offline several hours due to a denial-of-service attack.[33]
The outage kept users from remotely logging into their computers.
The company published a statement on its Web site summarizing the events and giving guidance in how users can protect themselves.[34]
TeamViewer referred to previous LinkedIn, Tumblr, and MySpace security breaches where millions of email and password pairs were hacked and the stolen login passwords were reused by the TeamViewer accounts of the victims.
Teamviewer also claimed in the same statement that they do “not store any password-equivalent data”.[35]
Throughout the ordeal, TeamViewer has maintained that it is not at fault for the account thefts.
The company’s handling of the matter has brought harsh criticism[36] from aggrieved customers, who accuse TeamViewer of being in “complete denial” of the problem.
Following this event, TeamViewer launched additional security measures, namely Trusted Devices and enforced account password reset on unusual activity, to improve the security.”
https://en.wikipedia.org/wiki/TeamViewer
so…
Really hope TeamViewer company does all it can to keep this software secure.
TeamViewer & Co are a convenient way to do remote support, but for regular remote administration & maintenance, VPNs / SSH-tunnels are probably still the best solution, but require more effort to be setup (VPN server needs DynDNS (newer AVM FritzBox 7490 and 7590 routers now have DynDNS “build-in”) or even fixed IP).
Just as with automatic updates the convenience of TeamViewer comes at the cost of security.
For the occasional remote support, TeamViewer (portable version!) might be okay, but it should never not be left unattended in the background… to wait for day X, that the TeamViewer infrastructure get’s hacked.
Links:
https://en.wikipedia.org/wiki/Comparison_of_remote_desktop_software
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!