CheckPoint Security found security problems in OpenSource and closed source rdp clients/servers – the product vendors including MS have been informed and everybody except MS will update their products. X-D
a hacked rdp server can “attack” the client – in the moment – the client pastes content from server (files or other stuff) – at this moment a malicious/compromised server running outside of corporate LAN could place a file at any path of the client (autostart folder) and run it next time the system boots. not cool.
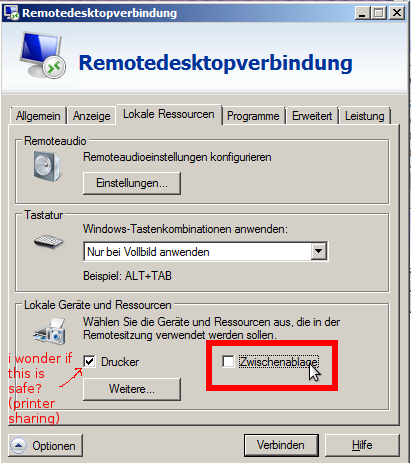
proposed solution: disable clipboard sharing
… obviously sharing other resources with the server then is also unsafe. folders of course but maybe even printers?
more research would have to be conducted in this field.
my proposed solution: internet access from within the corporate LAN can not be done anymore.
set your router/firewall to only accept connections from certain IPs or even better: pull the plug.
All internet access needs to be done from computers that are NOT connected to the corporate LAN, e.g. via demilitarized WIFI only.
Microsoft’s Response:
During the responsible disclosure process, we sent the details of the path traversal in mstsc.exe to Microsoft.
This is Microsoft’s official response:
“Thank you for your submission. We determined your finding is valid but does not meet our bar for servicing. For more information, please see the Microsoft Security Servicing Criteria for Windows (https://aka.ms/windowscriteria).”
As a result, this path traversal has no CVE-ID, and there is no patch to address it.
https://research.checkpoint.com/reverse-rdp-attack-code-execution-on-rdp-clients/
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!