passwd -l maria; # disables account maria
passwd: password expiry information changed.
grep maria /etc/shadow
maria:!$6$w9DaelrP$/tJiXC2PU0B.XOupP0sFTySis5VfkMwv0DnoFy3.d.nC8gXJU.DSbU0Uryyex40P67keCFoQuxEjZ8RD9kDGU0:17325:0:99999:7:::
passwd -u maria; # enable account maria
passwd: password expiry information changed.
/etc/passwd
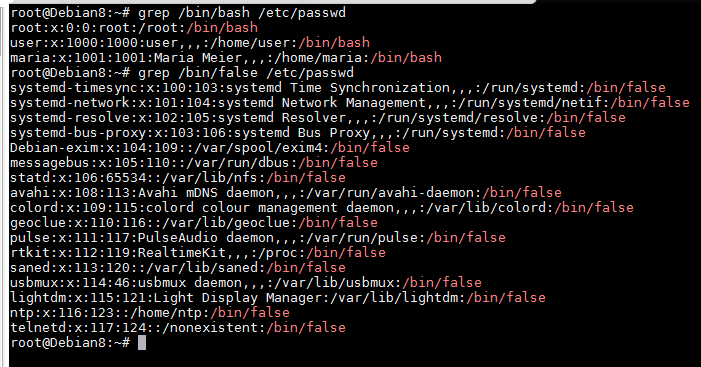
grep /bin/bash /etc/passwd; # output all interactive user accounts that use bash as shell
grep /bin/sh /etc/passwd; # output all interactive user accounts that use sh as shell
grep /bin/false /etc/passwd; # output all service accounts that can not used to login
usermod -s /bin/false maria; # change login-shell of maria to /bin/false (no login shell)
inted vs xinted vs iptables vs netfilter
is xinetd still in use?
most functionality of xinetd is replaed by stateful firewalling, through iptables/netfilter… but xinetd still exists and can be used.
yes – suse12 and centos7 come with xinetd pre-installed. debian8 is using neither xinetd nor inetd – just iptables.
inted: OpenBSD Internet Superserver
main config file /etc/inetd.conf
(if installed: apt-get install openbsd-inetd; # debian8)
# you can check if the inetd.conf is correct with
tcpdchk
The inetd server is a network daemon program that specializes in managing incoming network connections.
Its configuration file tells it what program needs to be run when an incoming connection is received.
Any service port may be configured for either of the tcp or udp protocols.
This is a port of the OpenBSD daemon with some debian-specific features.
This package supports IPv6, built-in libwrap access control, binding to specific addresses, UNIX domain sockets and socket buffers tuning.
https://packages.debian.org/en/jessie/openbsd-inetd
xinetd
replacement for inetd with many enhancements
xinetd has access control mechanisms, extensive logging capabilities, the ability to make services available based on time, and can place limits on the number of servers that can be started, among other things.
It has the ability to redirect TCP streams to a remote host and port.
This is useful for those of that use IP masquerading, or NAT, and want to be able to reach your internal hosts.
It also has the ability to bind specific services to specific interfaces.
This is useful when you want to make services available for your internal network, but not the rest of the world. Or to have a different service running on the same port, but different interfaces.
https://packages.debian.org/en/jessie/xinetd
apt-get update && apt-get install xinetd; # first you will need to install xinetd on debian8, in suse12 and centos7 come with xinetd pre-installed
root@Debian8:~# ll /etc/xinetd.d/
total 20K
-rw-r–r– 1 root root 640 Oct 26 2013 chargen
-rw-r–r– 1 root root 502 Oct 26 2013 daytime
-rw-r–r– 1 root root 391 Oct 26 2013 discard
-rw-r–r– 1 root root 422 Oct 26 2013 echo
-rw-r–r– 1 root root 569 Oct 26 2013 time
[root@CentOS7 ~]# ll /etc/xinetd.d
insgesamt 60K
drwxr-xr-x. 2 root root 242 4. Mai 17:13 .
drwxr-xr-x. 111 root root 8,0K 8. Jun 12:15 ..
-rw——-. 1 root root 1,2K 5. Nov 2016 chargen-dgram
-rw——-. 1 root root 1,2K 5. Nov 2016 chargen-stream
-rw——-. 1 root root 1,2K 5. Nov 2016 daytime-dgram
-rw——-. 1 root root 1,2K 5. Nov 2016 daytime-stream
-rw——-. 1 root root 1,2K 5. Nov 2016 discard-dgram
-rw——-. 1 root root 1,2K 5. Nov 2016 discard-stream
-rw——-. 1 root root 1,2K 5. Nov 2016 echo-dgram
-rw——-. 1 root root 1,2K 5. Nov 2016 echo-stream
-rw——-. 1 root root 1,2K 5. Nov 2016 tcpmux-server
-rw-r–r–. 1 root root 518 5. Nov 2016 tftp
-rw——-. 1 root root 1,2K 5. Nov 2016 time-dgram
-rw——-. 1 root root 1,2K 5. Nov 2016 time-stream
suse12:~ # ll /etc/xinetd.d/
insgesamt 76
-rw-r–r– 1 root root 313 23. Sep 2014 chargen
-rw-r–r– 1 root root 333 23. Sep 2014 chargen-udp
-rw-r–r– 1 root root 256 7. Jun 2016 cups-lpd
-rw-r–r– 1 root root 313 23. Sep 2014 daytime
-rw-r–r– 1 root root 333 23. Sep 2014 daytime-udp
-rw-r–r– 1 root root 313 23. Sep 2014 discard
-rw-r–r– 1 root root 332 23. Sep 2014 discard-udp
-rw-r–r– 1 root root 305 23. Sep 2014 echo
-rw-r–r– 1 root root 324 23. Sep 2014 echo-udp
-rw-r–r– 1 root root 492 21. Sep 2014 netstat
-rw-r–r– 1 root root 207 23. Sep 2016 rsync
-rw-r–r– 1 root root 332 23. Sep 2014 servers
-rw-r–r– 1 root root 334 23. Sep 2014 services
-rw-r–r– 1 root root 536 30. Mai 2016 systat
-rw-r–r– 1 root root 411 8. Jun 15:08 telnet
-rw-r–r– 1 root root 323 4. Mai 09:31 time
-rw-r–r– 1 root root 333 23. Sep 2014 time-udp
-rw-r–r– 1 root root 2685 14. Okt 2016 vnc
-rw——- 1 root root 916 8. Jun 2016 vsftpd
xinetd example
zypper –no-remote in telnet-server; # suse12: install telnet server on suse12 a highly insecure service
apt-get install telnetd; # debian8
# under suse12 a new config file will be created under /etx/xinetd.d
cat /etc/xinetd.d/telnet
# default: off
# description: Telnet is the old login server which is INSECURE and should \
# therefore not be used. Use secure shell (openssh).
# If you need telnetd not to “keep-alives” (e.g. if it runs over a ISDN \
# uplink), add “-n”. See ‘man telnetd’ for more details.
service telnet
{
disable = yes
socket_type = stream
protocol = tcp
wait = no
user = root
server = /usr/sbin/in.telnetd
}
suse12:~ # chkconfig telnet on
# will change config file to and remove the disabled = yes line
suse12:~ # vim /etc/xinetd.d/telnet; # open up xinetd config file for telnet and add this line
# default: off
# description: Telnet is the old login server which is INSECURE and should \
# therefore not be used. Use secure shell (openssh).
# If you need telnetd not to “keep-alives” (e.g. if it runs over a ISDN \
# uplink), add “-n”. See ‘man telnetd’ for more details.
service telnet
{
socket_type = stream
protocol = tcp
wait = no
user = root
server = /usr/sbin/in.telnetd
only_from = 127.0.0.1
}
suse12:~ # service xinetd restart; # restart xinetd to activate settings
suse12:~ #telnet localhost; # works
root@Debian8:# telnet suse12; # fails
Trying 172.20.0.25…
^C
# if you add
only_from = 172.20.0.0
# and debian8 has 172.20.0.12
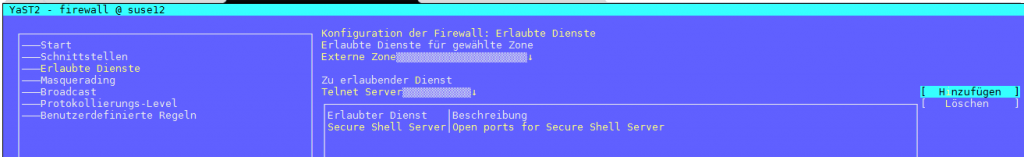
# and you enabled telnet in the yast2 fireall
yast2 firewall; # modify firewall settings
# you should now also be able to login from a different machine
tcp wrapper (tcpd)
with: /etc/hosts.deny and /etc/hosts.allow
ldd $(which in.telnetd); # tcp wrapper only work with binaries that support libwrap.so.0
which in.telnetd
/usr/sbin/in.telnetd
root@Debian8:# ldd $(which in.telnetd)
linux-gate.so.1 (0xb7779000)
libutil.so.1 => /lib/i386-linux-gnu/i686/cmov/libutil.so.1 (0xb7762000)
libc.so.6 => /lib/i386-linux-gnu/i686/cmov/libc.so.6 (0xb75b5000)
/lib/ld-linux.so.2 (0x800eb000)
ldd $(which xinetd)
linux-gate.so.1 (0xb7712000)
libwrap.so.0 => /lib/i386-linux-gnu/libwrap.so.0 (0xb76f5000)
ldd $(which sshd)|grep libwrap
libwrap.so.0 => /lib/i386-linux-gnu/libwrap.so.0 (0xb76da000)
# install telnet and test if it works
apt-get install telnetd; # debian8
# confirmed telnet works
vim /etc/hosts.deny; # edit hosts.deny and add this line
# /etc/hosts.deny: list of hosts that are _not_ allowed to access the system.
# See the manual pages hosts_access(5) and hosts_options(5).
#
# Example: ALL: some.host.name, .some.domain
# ALL EXCEPT in.fingerd: other.host.name, .other.domain
#
# If you’re going to protect the portmapper use the name “rpcbind” for the
# daemon name. See rpcbind(8) and rpc.mountd(8) for further information.
#
# The PARANOID wildcard matches any host whose name does not match its
# address.
#
# You may wish to enable this to ensure any programs that don’t
# validate looked up hostnames still leave understandable logs. In past
# versions of Debian this has been the default.
# ALL: PARANOID
in.telnetd : ALL
# try to login via telnet again – does not work
Links:
see more here: https://dwaves.de/2017/05/04/linux-security-config-hosts-deny-hosts-allow/
https://dwaves.de/2017/06/08/lpic-1-102-110-2-setup-host-security/
more Links:
https://www.theurbanpenguin.com/lpic-1-102-110-2-setup-host-security/
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!