update: 2024
2017 version:
# tested on uname -a Linux debian 3.16.0-4-686-pae #1 SMP Debian 3.16.39-1+deb8u2 (2017-03-07) i686 GNU/Linux ssh -V OpenSSH_6.7p1 Debian-5+deb8u3, OpenSSL 1.0.1t 3 May 2016 vim /etc/ssh/sshd_config; # open up ssh server config file AllowUsers user1 user2 user3 # this would allow user1, user2 and user3 to login from ANY host/ip address AllowUsers user1@172.20.0.7 user2@172.20.0.28 user2@172.20.0.33 # this would allow user1 ONLY to login from 0.7, user2 ONLY from 0.28 and user3 ONLY from 0.33 DebianBanner no # while you are on it - turn off that Debian-OS version info during ssh login attempts # a little bit more security # but SSH-Version info is still shown (it is required for clients to chose protocols) # super-hackers may have other ways to determine which OS and ssh version your server is using LoginGraceTime 1m PermitRootLogin no StrictModes yes MaxAuthTries 1 #MaxSessions 10
PubkeyAuthentication yes # this was considered very safe until spectre-meltdown came along # depending what os one is on # fedora/redhat/centos # stop printing version number PrintMotd no # if this is a headless server and one does not plan to ssh forward any gui output X11Forwarding no # write and quit
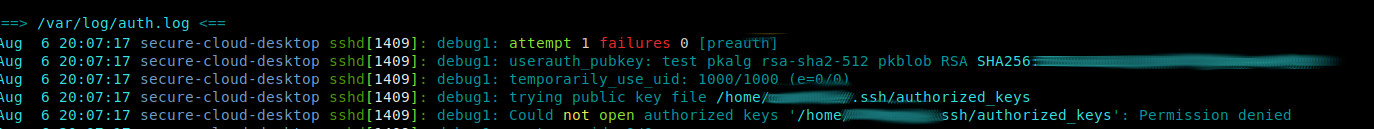
:wq # restart ssh service to make changes take effect # no fear: one will stay connected # (no forceful disconnect) service sshd restart # older debian /etc/init.d/ssh restart; # do not forget to restart the service or the changes won't be applied immediately [ ok . Restarting ssh (via systemctl): ssh.service # LEAVE CURRENT SSH SESSION OPEN! # hit this to live-debug ssh login problems tail -f /var/log/auth.log May 5 11:48:07 debian sshd[2246]: reverse mapping checking getaddrinfo for suse.domainname.local [172.20.0.25] failed - POSSIBLE BREAK-IN ATTEMPT! May 5 11:48:07 debian sshd[2246]: User user from 172.20.0.25 not allowed because not listed in AllowUsers May 5 11:48:07 debian sshd[2246]: input_userauth_request: invalid user user [preauth] May 5 11:48:08 debian sshd[2246]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=172.20.0.25 user=user May 5 11:48:10 debian sshd[2246]: Failed password for invalid user user from 172.20.0.25 port 40820 ssh2 # testing/debugging: leave the current ssh session open # on client machine start a new terminal ssh -v AllowedUser@ip.of.one.server # works? great! :) # one is now save to close all connections by hitting Ctrl+D
how to test / debug ssh settings / problems
- connect via ssh
- become root (su – root)
- edit/modify
-
vim /etc/ssh/sshd_config-
LogLevel DEBUG # or even more verbose LogLevel DEBUG3
-
- restart ssh service (service sshd restart)
- leave that terminal open and start real time log viewing
- https://dwaves.de/2017/06/15/linux-monitor-all-logs-in-real-time-d-follow-all-show-changes-to-log-files-under-varlog/
-
start a new terminal and try to ssh connect to the server... works? great! fails? the logs should have the details
-
inted (replaced by xinetd (replaced by netfilter and iptables))
has nothing to do with ssh… except that it is another form of access-control. just in case if you wonder why you can’t access your server.
/etc/hosts.allow
/etc/hosts.deny
hosts.allow overrides hosts.deny.
so if a host is listed in hosts.allow
The example below allows shows some of the possible ways to configure the hosts.allow file.
portmap : localhost : allow portmap : 10. : allow portmap : .insecure.net : allow portmap : ALL : deny sshd : ALL : allow sshd : bad.host : deny sshd : 88.4.2. : deny (1) ALL : ALL : deny
(src)
Links:
see more here: https://dwaves.de/2017/05/04/linux-security-config-hosts-deny-hosts-allow/
https://dwaves.de/2017/06/08/lpic-1-102-110-2-setup-host-security/
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!