Fritz!Box Webcm Unauthenticated Command Injection
Different Fritz!Box devices are vulnerable to an unauthenticated OS command injection.
This module was tested on a Fritz!Box 7270 from the LAN side.
The vendor reported the following devices vulnerable:
- 7570, 7490, 7390, 7360, 7340, 7330, 7272, 7270, 7170 Annex A A/CH, 7170 Annex B English, 7170 Annex A English, 7140, 7113, 6840 LTE, 6810 LTE, 6360 Cable, 6320 Cable, 5124, 5113, 3390, 3370, 3272, 3270
- breaking.systems
- s3cur1ty.de
- src: https://www.exploit-db.com/exploits/32753
What if there is no update support from AVM anymore for your (once expensive) Fritzbox router? Chuck it away?- AVM ships updates even for older models when severe security problems get known
-> “For me, the best solution is to unplug it and change for a Open-wrt or DD-wrt appliance…”
Check this out: https://dwaves.de/2017/01/31/how-to-create-your-own-pfsense-firewall-proxy/
Solutions? Anyone?
While the conceptual deficits of capitalism will not be solved over night – i hope there are router producers out there that take security a little more serious than AVM did.
“If you care about the security of your router, and you should, it is best to avoid consumer grade routers. On the whole, the software in these routers is buggy as heck.
…
WPS is like having a “hack me” sign on your back
”
http://routersecurity.org/bugs.php
“When you buy a consumer router you are buying the hardware. The software is provided as cheaply as possible. When you buy a business class router you are buying the software.
That said, do not use a consumer router… avoid D-Link, Netgear, Asus, Belkin, Linksys, TP-LINK, AVM.. The most important decision when buying a router is to get one with more professionally done software/firmware.”
src: http://routersecurity.org/consumerrouters.php
router security checklist: http://routersecurity.org/checklist.php
so what router Mr Horowitz is using?
“Me? I use a router that few have heard of. Even if it’s just as bad as all the rest (it’s not), hopefully it flies under the radar.”
http://www.computerworld.com/article/3108383/networking/a-router-security-cheat-sheet.html
UNTESTED (!!!) Alternatives:
Build your own ADSL Router? 😀
https://wiki.openwrt.org/toh/start
http://www.techradar.com/news/networking/how-to-build-your-own-router-915419
http://arstechnica.com/gadgets/2016/01/numbers-dont-lie-its-time-to-build-your-own-router/
Peplink (US)
http://www.peplink.com/products/pepwave-surf-soho/
Professional Grade Router for Power Users
The Surf SOHO is a professional-grade router that is secure, reliable, and easy to use. This router will stay with you for the long run.
“COMING THIS FALL” (AHA! WAIT FOR IT IF YOU CAN. SHOULD BE WORTH IT.)
If you can not wait look at those:
Sophos (UK)
probably better known for doing Antivirus software since 1985.
you might even apply their software to your own hardware: https://www.sophos.com/en-us/products/free-tools/sophos-xg-firewall-home-edition.aspx
https://nakedsecurity.sophos.com/tag/adsl-modem/
Deliberate security holes
We’ve written regularly, and sadly fairly frequently, about security holes in SoHo routers – holes that in many cases do not instil much confidence at all.
Some of these holes were simple bugs; even more alarmingly, others weren’t bugs, but deliberately-programmed security flaws.
For example, we’ve had:
- A remote code execution hole in Cisco devices allowing a cunningly crafted web request to take over your router.
- A Linksys bug allowing an external website to change the router’s password, and to enable login access over the internet.
- “Joel’s Backdoor” in D-Link routers, where a simple change in the User-Agent string in your browser would bypass the login screen.
- Sercomm’s undocumented ScMM backdoor interface that allowed you to bypass not just the login screen but the admin web pages too.
- Sercomm’s patch for the ScMM backdoor, implemented by hiding the backdoor behind a new backdoor.
“But neither ISE nor the EFF agrees, and one important reason is that insecurities in popular router products are like gold dust to cybercrooks.”
LevelOne (Germany)
Ubiquiti (US)
“like the Ubiquiti Amplifi” very stylish thing…
FortiNet (US)
https://www.fortinet.com/products-services/products/firewall/fortigate-entry-level-firewall.html
Juniper (US)
SRX210, SRX210HE2-> FIRMWARE SUPPORT ENDS 2020!
a lot of hacking: https://kb.juniper.net/InfoCenter/index?page=content&id=KB15737
not for soho!
VipRinet.com (Germany)
https://www.viprinet.com/de/technologie/ruggedvpn
https://www.viprinet.com/en/technology/combinable-media/dsl
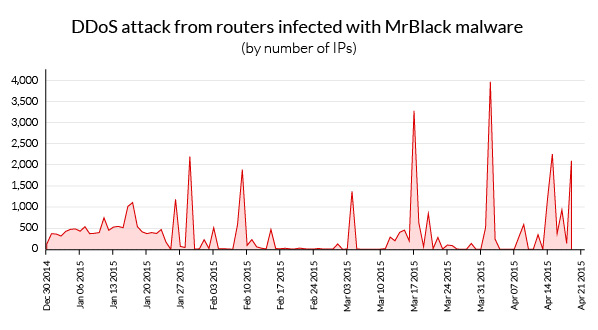
Routers and DDoS
as you might have known – KrebsOnSecurity.com was DDoSED to #Death with 680GByte/Sec from (probably) a lot of hacked embedded devices. From surveillance cameras to soho-adsl-routers.
Google helped him out to shield from such attacks.
As society becomes dependent on electricity (!!!) and internet (!!!) to work – (from home :-D) the working of this infrastructure becomes critical. One second of blackout would be a lot of damage to amazon.com, unfortunately, it seems that only the “good guys” like Krebs get attacked.
| Malware | Type | Variants Observed | Commonness |
| MrBlack | DDoS tool | 137 | 86.57% |
| Dofloo | DDoS tool | 19 | 5.48% |
| Mayday | DDoS tool | 24 | 2.84% |
| BillGates | DDoS tool | 5 | 2.30% |
| Skynet | Backdoor | 5 | 1.46% |
| Unknown/New | DDoS Bot | 2 | 1.35% |
src: https://www.incapsula.com/blog/ddos-botnet-soho-router.html
The FritzHack Story:
as seen on: https://heinrichs.io/?s=fritzbox
https://www.exploit-db.com/exploits/32753/
https://www.speckmarschall.de/?page_id=10
this is bad news for AVM and it’s customers.
The Fritzbox 7170 and 7270 are still a lot around in Germany.
IF YOU CAN NOT CONNECT TO YOUR WEBINTERFACE http://fritz.box ANYMORE! YOU SHOULD GET PARANOID! YOUR BOX JUST MIGHT BE HACKED!
They do not have an automated update service and i guess AVM they kind of phased out firmware update support – unless MASSIVE BUGS come to surface – like they did.
“Heise security to have discovered in collaboration with the reverse-engineering specialists of Hanno Henry the exact position of the vulnerability in the vulnerable firmware versions.
These work independent from remote access feature being enabled or not.
An attacker can get through this gap root privileges and thus complete control over the router.
This is even possible when the victim clicks only a Web page with malicious code.
The Fritz box run some commands, the configuration file of router on an external server will copy. This file contains many other personal data in clear text, as the DSL and DynDNS credentials in addition to the administration password of the Fritz box.”
translated from src: http://www.golem.de/news/fritzbox-hack-sicherheitsluecke-betrifft-offenbar-nicht-nur-fernzugang-1402-104621.html
the last update for the 7270 is from https://download.avm.de/fritz.box/fritzbox.fon_wlan_7270_v2/firmware/deutsch/
Index of /fritz.box/fritzbox.fon_wlan_7270_v2/firmware/deutsch
| Name | Last modified | Size | Description | |
|---|---|---|---|---|
|
|
||||
| Parent Directory | – | |||
| FRITZ.Box_Fon_WLAN_7270_v2.54.06.06.image | 2015-10-20 09:48 | 14M | ||
| info.txt | 2015-10-20 09:43 | 54K | ||
|
|
||||
“AVM isn’t a particularly well-known brand in the UK, but in Germany it’s the top ADSL router manufacturer, with over 50 percent market share.”
src: http://www.zdnet.com/product/avm-fritz-box-fon-wlan-7390/
Fritz!Box is a series of residential gateway devices produced by the German company AVM GmbH. In 2010 it was estimated the series had a market share of 68% of the digital subscriber line (DSL) consumer equipment in Germany.[1]
src: https://en.wikipedia.org/wiki/Fritz!Box
7390: “appliance was also vulnerable even if remote access was disabled”
src: https://www.hacking-lab.com/misc/downloads/Fritzbox-night-tale.pdf
mirror download: fritzbox-night-tale.pdf
just imagine
what you could do with 10.000.000 hacked Fritzboxes.
Not only could you launch massive DDoS attacks to silence your competition or critics.
You could steal DSL-access-passwords.
Call expensive numbers.
You could probably forge DNS entries and redirect traffic and steal a lot of passwords. (from onlinebanking to blogs to logins)
I guess that is just my imagination – expect the hacking community to come up with a billion more ideas how to exploit that situation.
What is AVM’s stand on that?
https://avm.de/ratgeber/sicherheit/ -> “keep your firmware updated” haha! good joke! there seems no update-firmware-support anymore for 7170 and 7270 –
shame on you AVM!
lost overview over hardware-changes?
same as Apple!
SELL SELL SELL. FIX LATER OR ALSO LEAVE UNFIXED.
SO YOU SPECULATE ON PLANNED OBSOLESCENCE:
“LET THEM REBUY AND REBUY AND REBUY EVERY YEAR A NEW FRITZBOX… AFTER ALL: HEY!
ITS CAPITALISM!
AND THE GAME IS: HOW TO MAKE THE MOST PROFIT!
REGARDLESS SOCIAL AND ENVIRONMENTAL COSTS!
THIS IS THE OPPOSITE OF SUSTAINABILITY – AND THIS SHIT GOTTA GO!
YOU JUST LOST A CUSTOMER!
FOREVER! TRUST LOST ON “AVM” – FUCK IT!
Other routers under attack:
“How millions of DSL modems were hacked in Brazil, to pay for Rio prostitutes”
https://nakedsecurity.sophos.com/2012/10/01/hacked-routers-brazil-vb2012/
“The new report details 56 new Common Vulnerabilities and Exposures, or CVEs, that Holcomb and the other ISE researchers have found in popular routers. These include the Asus RT-AC66U, D-Link DIR-865L, and TrendNet TEW-812DRU, for which Holcomb plans on demonstrating vulnerabilities at Defcon on Saturday and Sunday.
…
Holcomb said that while TP-Link fixed all the vulnerabilities that ISE reported to it, D-Link has never responded. And Linksys, he said, chose not to repair many of the vulnerabilities reported to it. ”
src: https://www.cnet.com/news/wi-fi-routers-more-security-risks-than-ever/?_escaped_fragment_=#!
Tools:
Gibson Research Corp.’s Shields Up port-scanning service at https://www.grc.com/shieldsup
It will test your router for hundreds of common vulnerabilities, most of which can be mitigated by the router’s administrator.
Related Links:
https://www.redteam-pentesting.de/en/advisories/rt-sa-2015-001/-avm-fritz-box-remote-code-execution-via-buffer-overflow
http://www.wehavemorefun.de/fritzbox/Allcfgconv
AVM FRITZ!Box: Remote Code Execution via Buffer Overflow The original source. Jan. 7, 2016
http://www.tomsguide.com/us/scariest-security-threats,review-2144.html
https://www.incapsula.com/blog/ddos-botnet-soho-router.html
https://krebsonsecurity.com/2015/11/the-lingering-mess-from-default-insecurity/
http://www.securityweek.com/attackers-use-exploit-kit-hijack-routers-researcher
http://www.golem.de/news/avm-fritzbox-liefert-neues-os-mit-auto-update-aus-1408-108525.html
http://www.golem.de/news/fritzbox-hack-avm-und-telekom-mit-weiteren-updates-1402-104671.html
Related Documents:
Related Videos:
#HITBGSEC 2015 – Lyon Yang – Advanced SOHO Router Exploitation”>
PRESENTATION MATERIALS: http://gsec.hitb.org/materials/sg2015/ PRESENTATION ABSTRACT: In this talk we will look into how a series of 0-day vulnerabilities ca…
keywords: hitb, hitbsecconf, hackinthebox, hitbgsec
http://gsec.hitb.org/sg2015/sessions/session-003/
LTE-Hotspot als Sicherheitsalptraum: Der D-Link DWR-932B
“A security researcher who has discovered a series of serious security holes in the device recommends owners to discard the product.
D-Link promises patches, but does not say when they should be expected.”
“Ein Sicherheitsforscher, der eine ganze Reihe schwerwiegende Sicherheitslücken in dem Gerät entdeckt hat, empfiehlt Besitzern, es zu entsorgen. D-Link verspricht Patches, sagt aber nicht, wann diese zu erwarten sind.”
Related Podcasts
http://x.hope.net/schedule.html#securingah
Securing a Home Router
Sun, 20 Jul 2014 15:00:59 +0000 (olson)
Download Audio: 16kbps or 128kbps
Routers sit between all your computing devices and the Internet, making them a perfect target for abuse (Glenn Greenwald has written about the NSA hacking into them). The presentation will explain some of the configuration options in home routers that can make your Local Area Network more secure. Among these are locking down access to the router, Wi-Fi security, firewalls, DNS, and hiding on the Internet. Also covered are known security flaws in routers and how to defend against them. Some of the covered flaws are: WPS, UPnP, port 32764, Heartbleed, and smartphones leaking Wi-Fi passwords. Speakers: Michael Horowitz
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!