the best about samba:
thanks for samba, it provides users with a fast (of course depends also on harddisk speed) rock-solid no-limit-to-maximum-users file-server for maximum file-transfer-and-sharing-and-storage productivity (and they will USE that T: temp drive for EVERYTHING! prepare for TERRABYTES OF DATA!)
shortcut: vms
here is a debian 12 based vm pre-installed that offers samba and a smb mountable “public” directory
- wget https://dwaves.de/vms/fileshare_samba_debian12.vdi.bz2.sha512sum
- wget https://dwaves.de/vms/fileshare_samba_debian12.vdi.bz2
- sha512sum -c fileshare_samba_debian12.vdi.bz2.sha512sum; # check integrity of download
- bunzip2 -v fileshare_samba_debian12.vdi.bz2; # unpack
- reate a new vm in virt-manager and select the above
- default password is: root (pwd: root) and user (pwd user) CHANGE THOSE PASSWORDS AFTER SSH LOGIN!
- if the user needs this to be in kvm qcow format just go:
-
# convert vdi to qcow2 qemu-img convert -f vdi -O qcow2 fileshare_samba_debian12.vdi fileshare_samba_debian12.qcow2
-
under gnu linux just mount it like:
su - root mkdir /media/user/cifs mount -t cifs -o username=user,uid=1000,gid=1000 //192.168.122.162/public /media/user/cifs # (password also: user, plz change also with smbpasswd -a user)
possible problems:
if the samba server is rebooted frequently (daily) samba kept losing files after reboot, why?
- this most likely has to do with changes being RAM cached and NOT written to disk during shutdown (#wtf?)
- workaround:
- cronjob that runs “sync” every minute
- crontab -e
- * * * * * /usr/bin/sync; # sync samba cache to disk every minute, so not to lose changes during frequent reboots
how to mount:
https://dwaves.de/2015/06/23/linux-mount-windows-samba-share-as-linux-client/
best hint ever: if there is an errors while smb mounting!
like “Mounting cifs drive gives: mount error(22): Invalid argument”
have a separate root-terminal open that is running this “debug the logs live” script
ext3+gnu_linux+samba = fast and reliable fileserver. 
WARNING! Security problems Versions from Version 3.5.0 to 4.6.4 (recent in May 2017 ) are affected and need to be patched!
patches are available from: https://www.samba.org/samba/patches/
Unfortunately EVEN Debian9 (!!!! GUYS FIX THAT FAST !!!!) is shipping an affected version?: 4.5.8-Debian https://packages.debian.org/en/stretch/samba
prior to running an debian8 fileserver a small and medium sized company was running ubuntu server with smb as virtualbox VM (1GB RAM is more than enough) on windows 7 professional.
both work flawlessly fast, reliable and we haven’t lost a single file (except when some ransomeware decided to encrypt all network shares…. but that is a different story and is not samba to blame) – while at the same time circumvent the maximum of 20 simultaneous connections that windows 7 comes with.
unfortunately – some software vendors explicitly demand a windows-share for their software to work properly. (i guess they do not want to do the double-testing)
With samba the user can have as many connections as the server can handle.
Plus: it is pretty easy to get started.
setup and install
this is relatively easy (everything is RELATIVE!)
hostnamectl; # tested with (but probably works the same accross distros) Static hostname: debian Operating System: Debian GNU/Linux 9 (stretch) Kernel: Linux 4.9.0-3-amd64 Architecture: x86-64 # client version C:\Users>ver Microsoft Windows [Version 6.3.9600] su; # become root apt update; apt install -y samba; # debian/ubuntu yum install -y samba; # centos/redhat samba -b; # show build/version Samba version: 4.5.8-Debian Build environment: Paths: BINDIR: /usr/bin SBINDIR: /usr/sbin CONFIGFILE: /etc/samba/smb.conf NCALRPCDIR: /var/run/samba/ncalrpc LOGFILEBASE: /var/log/samba LMHOSTSFILE: /etc/samba/lmhosts DATADIR: /usr/share MODULESDIR: /usr/lib/x86_64-linux-gnu/samba LOCKDIR: /var/run/samba STATEDIR: /var/lib/samba CACHEDIR: /var/cache/samba PIDDIR: /var/run/samba PRIVATE_DIR: /var/lib/samba/private CODEPAGEDIR: /usr/share/samba/codepages SETUPDIR: /usr/share/samba/setup WINBINDD_SOCKET_DIR: /var/run/samba/winbindd WINBINDD_PRIVILEGED_SOCKET_DIR: /var/lib/samba/winbindd_privileged NTP_SIGND_SOCKET_DIR: /var/lib/samba/ntp_signd # on a separate root console follow samba logs tail -f /var/log/samba/log.* & # or even better: all logs
download as script here: mon_logs_all.sh.txt
manpage: multitail.man.txt
# without color but: scrollable :) find /var/log/* -type f \( -name "*" \) ! -path '*.gz*' -exec tail -n0 -f "$file" {} + # with color but no scroll :( (ccze is only available in CentOS7 and Debian 9 and 10) # ccze is not longer maintained but still available for Debian/Ubuntu/DEB based systems find /var/log/* -type f \( -name "*" \) ! -path '*.gz*' -exec tail -n0 -f "$file" {} + | ccze
creating a free for all shared folder: sharing files with everybody
The user wants a share where all users in the network can upload but also delete files, can do it like this:
WARNING POSSIBLE ABUSE: angry users might upload a virus.doc or delete the whole directory!
Always make backups (DAILY!) on external devices for example: USB-harddiskA and USB-harddiskB
- make backups EVEN for shares that are meant als “temp” “temporary” folders
- users WILL abuse easy accessible password UNPROTECTED temp shares for storing VIP (Very Important) files that if gone will threaten all of mankind (real life experience!)
- while system backs up on USB-harddiskA
- USB-harddiskB is PHYSICALL DISCONNECTED sitting in a double-metal-wall safe
- swap daily, weekly, monthly depending on how many days of dataloss can be tolerated
# prepare storage dirs mkdir -p /home/shares/public chown -R root:users /home/shares/public/ chmod -R ugo+rwx /home/shares/public/ # edit main config file and add those lines at the very end vim /etc/samba/smb.conf echo '[public]' >> /etc/samba/smb.conf echo ' path = /home/shares/public/' >> /etc/samba/smb.conf echo ' force group = users' >> /etc/samba/smb.conf echo ' create mask = 0660' >> /etc/samba/smb.conf echo ' directory mask = 0771' >> /etc/samba/smb.conf echo ' browsable = yes' >> /etc/samba/smb.conf echo ' writable = yes' >> /etc/samba/smb.conf echo ' guest ok = yes' >> /etc/samba/smb.conf :wq # save and quit
test the config for errors:
testparm
testparm -v; # show all settings
example output: testparm.verbose.all.settings.txt
if everything is fine restart samba service like this:
systemctl restart smbd.service; # activate config
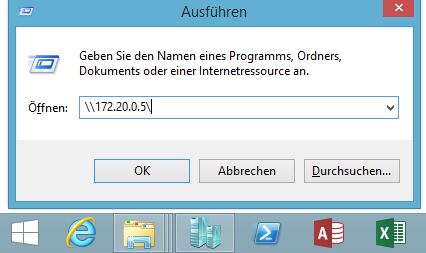
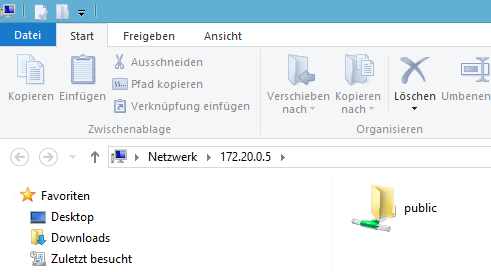
accessing the share from windows
on windows client hit Win+R -> RUN -> test to access the share:
with a config like this new folders and files are created (from a windows client) with those users and permissions:
ll /home/shares/public/
total 20K
drwxrwxr-x 3 root users 4.0K Aug 2 15:04 .
drwxr-xr-x 4 root root 4.0K Aug 2 15:01 ..
drwxrwx--x 2 nobody users 4.0K Aug 2 15:04 test
-rw-rw---- 1 nobody users 6 Aug 2 15:04 test2.txt
-rw-rw---- 1 nobody users 4 Aug 2 15:03 test.txt
accessing the share from gnu linux
is also doable.
apt install cifs-utils; # install samba-client software mkdir /mnt/cifs; # create mountpoint mount -t cifs //172.20.0.5/public /mnt/cifs --verbose -o user=nobody; mount.cifs kernel mount options: ip=172.20.0.5,unc=\\172.20.0.5\public,user=nobody,pass=******** Password for nobody@//172.20.0.5/public: # simply hit enter (no password) mkdir /media/user/cifs mount -t cifs -o username=user,uid=1000,gid=1000 //192.168.122.162/public /media/user/cifs passwd: (the password that was set with smbpasswd -a user) root@debian9:/home/user# ll /mnt/cifs/ total 4.0K drwxrwxr-x+ 3 root users 0 Aug 2 15:35 . drwxr-xr-x 3 root root 4.0K Aug 2 16:25 .. drwxrwx--x+ 2 nobody users 0 Aug 2 15:35 secret
possible problems:
# if the user gets the error: umount: /media/user/fileshare: no mount point specified. mount: /media/user/fileshare: cannot mount //192.168.122.100/public read-only. dmesg(1) may have more information after failed mount system call. # output from dmesg [ 1554.220956] CIFS: Attempting to mount \\192.168.122.100\public [ 1554.231686] CIFS: Status code returned 0xc000006d STATUS_LOGON_FAILURE [ 1554.231696] CIFS: VFS: \\192.168.122.100 Send error in SessSetup = -13 [ 1554.231709] CIFS: VFS: cifs_mount failed w/return code = -13 [ 1554.231749] CIFS: Attempting to mount \\192.168.122.100\public [ 1554.236543] CIFS: Status code returned 0xc000006d STATUS_LOGON_FAILURE [ 1554.236548] CIFS: VFS: \\192.168.122.100 Send error in SessSetup = -13 [ 1554.236556] CIFS: VFS: cifs_mount failed w/return code = -13 [ 1639.211299] CIFS: Attempting to mount \\192.168.122.100\public # these are A LOT OF missleading errors # root cause: cifs-utils is not installed: apt install cifs-utils; # install samba-client software
gnu linux: auto mount on startup: fstab
convenience vs security: to make shares automatically available right after boot, it is possible to mount them via fstab
problem: the password will be saved in CLEARTEXT (this is for security reasons OBVIOUSLY no good practice)
ideally those passwords should come out of a keyring that is master-password protected and user is asked on boot/after login: ‘would like to auto mount password protected share “sharename”, please provide master-password to unlock keyring’ (it is possible to set this up)
su - root vim /etc/fstab # at the very end add a entry like //192.168.122.162/sharename /media/user/mountpoint cifs username=user,password=PASSWORD,uid=1000,gid=1000 0 0
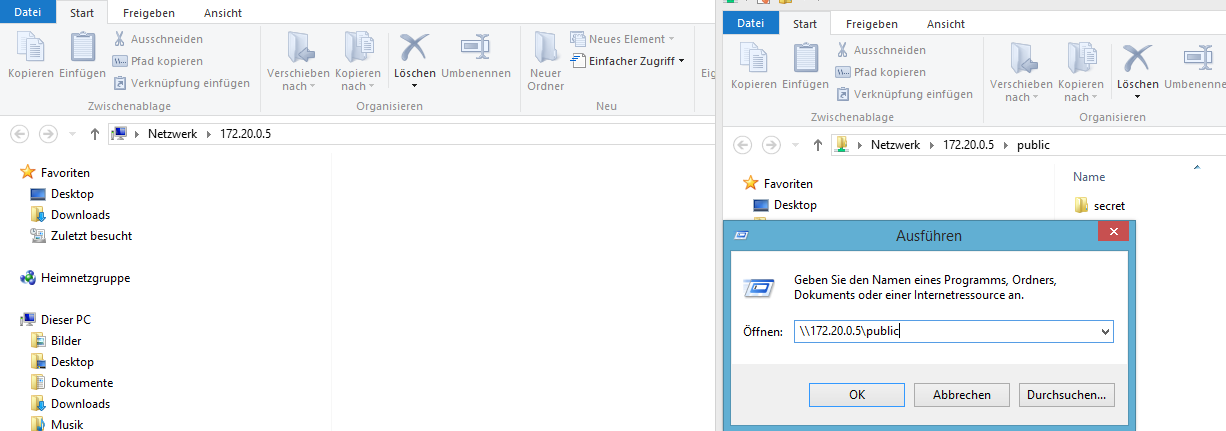
hidden share:
if user sets:
browsable = no
can still access the share but the folder itself is not visible when accessing the host via smb.
this can be usefull to hide shares from the “normal” user – but don’t expect super-hackers to not find and encrypt-for-ransom all your hidden files….
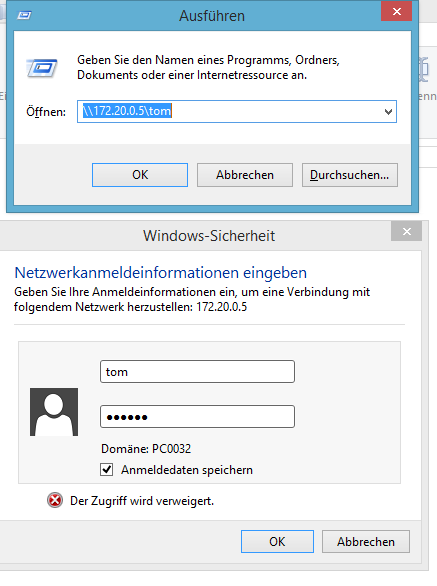
accessing user’s home directories with password protection/auth
useradd tom -m -G users; # add new user to linux passwd tom; # define linux-login-password for user smbpasswd -a tom; # define smb-password for user could use "tomtom" but it would be HIGHLY too little complex and thus UNSAFE! DON'T! vim /etc/samba/smb.conf; # edit main config file and add those lines at the very end [homes] comment = Home Directories browseable = no valid users = %S writable = yes create mask = 0700 directory mask = 0700 :wq # save and quit vim systemctl restart smbd.service; # restart samba
works like a charm:
manpages:
samba and security:
- of course: it is VERY important to keep the system as up-to-date as possible
- SMB v1 and SMB v2 are INSECURE and should NOT be used anymore
- “SMB 3.1. 1 — the latest version of SMB — was released along with Windows Server 2016 and Windows 10. SMB 3.1. 1 includes security enhancements such as: enforcing secure connections with newer (SMB2 and later) clients and stronger encryption (AES-256 from Windows 11 and Windows Server 2022)” (src)
- NEVER ALLOW SMB-OVER-INTERNET (even not SMB v3.1) WITHOUT tunneling it through more secure protocol as VPN or SSH
if user needs to share files securely over internet or inside a LAN SFTP IS THE CHOICE!
It is basically FTP-over-SSH, setup of SSH-FTP server is a keep-it-simple-process (thanks! all involved 🙂
FileZilla or MobaXTerm can do SFTP – allowing user to access gnu linux files and folders with a windows client.
when it comes to SMB and security: it got upgrades, but it hasn’t been great X-D (NFS security is not much better, basically supporting no password or key auth at all (?) and completely relying on “this is probably the system that is allowed to access, because it got the right IP address”)
what is kind-of-funny: that if software-protocols-and-concepts (SMB v1 and SMB v2) are implemented across-other-os-than-windows: the security problems might travel with that port.
- https://www.samba.org/samba/security/CVE-2017-7494.html
- https://wiki.illumos.org/display/illumos/WannaCry+-+SambaCry+CVE-2017-7494
- Versions from Version 3.5.0 to 4.6.4 (recent in May 2017 ) are affected.
- patches are available from:
scanning for security problems: (aka old outdated SMB v1 and v2) testing for wcry:
start up a second debian linux, modify the host’s IP (172.20.0.5) to that of your samba-server and go:
apt install nmap; # install nmap scanner wget https://raw.githubusercontent.com/Waffles-2/SambaCry/master/CVE-2017-7494.nse nmap -sC -p 445 --script CVE-2017-7494.nse 172.20.0.5 Starting Nmap 7.40 ( https://nmap.org ) at 2017-08-02 16:48 CEST Nmap scan report for 172.20.0.5 Host is up (0.00065s latency). PORT STATE SERVICE 445/tcp open microsoft-ds MAC Address: 00:15:5D:XX:XX:XX (Microsoft) Host script results: | CVE-2017-7494: | State is: POTENTIALLY VULNERABLE | Samba-vuln-CVE-2017-7494 | Summary: Remote code execution from a writable share. | Description: A Samba vulnerability (CVE-2017-7494) enables a malicious attacker with valid write access to a file share to upload and execute an arbitrary binary file which will run with Samba permissions. | Affected Version: All versions of Samba from 3.5.0 onwards. |_ For more info: https://www.guardicore.com/2017/05/samba/ Nmap done: 1 IP address (1 host up) scanned in 0.88 seconds # IF YOU WANT TO SCAN AN ENTIRE NETWORK! (WARNING! THIS MIGHT CRASH THE SMB-SERVER!) nmap -sC -p 445 --script CVE-2017-7494.nse 172.20.0.0/24
Im Mai 2017 wurde bekannt, dass in Anlehnung an Sicherheitsprobleme bei der Software von Microsoft, welche in Form von WannaCry ausgenutzt werden können, in ähnlicher Form auch bei Samba bestehen.
[11]Bei diesem Fehler, welcher in Anlehnung als SambaCry bezeichnet wird, ist es möglich injizierten Schadcode am betreffenden Samba-System auszuführen.
Der Fehler betrifft alle Samba-Versionen seit der Version 3.5.0 bis zur der im Mai 2017 aktuellen Version 4.6.4.
[12]Dieser Fehler ist vor allem bei NAS-Systemen, welche üblicherweise auf Samba aufsetzen, kritisch. D
links:
https://www.howtoforge.com/tutorial/debian-samba-server/
Donations
Nowadays, the Samba Team needs a dollar instead of pizza 😉
-> Samba Team
c/o Software Freedom Conservancy, Inc.
137 Montague St Ste 380
Brooklyn, NY 11201-3548
Why do we need money?
You may be wondering why the Samba Team needs money. The main expenses that we have are travel expenses for team members to the major Samba related conferences and expenses for running the main samba.org site. We occasionally have other expenses (eg. small pieces of hardware and books) but that is less common.
A good example of our travel expenses is the CIFS conference in San Jose. We usually have between ten and fifteen team members attending each year and while most of them are covered by the company they work for, we do need to provide international travel and accomodation for some of them.
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!