Update! Ransomeware mal 4
US-Justizministerium: Angriffe durch Ransomware haben sich im vergangenen Jahr vervierfacht.
Laut dem US-Justizministerium greift die Ransomware immer weiter um sich. Angeblich werden am Tag 4.000 Computer infiziert. Das FBI schätzt derweil den durch Ransomware entstandenen Schaden auf 200 Millionen Dollar. Immerhin gibt es für manche Betroffene Hilfe.
Falls Ihr Computer in diesen Tagen beginnt, ein Windows-Update auszuführen, sollten Sie sicherheitshalber den Stecker ziehen. Denn eine der neusten Inkarnationen der Ransomware tarnt sich als Windows-Updater.
Eine Datei namens criticalupdate01.exe wird über E-Mails auf einen Rechner geschleust und bittet dann um Ausführung, um das Windows-Update durchzuführen. Wer die Ausführung gestattet, muss zusehen, wie die Ransomware Fantom die eigenen Dateien mit AES-128 und RAS verschlüsselt werden – und das Programm Bitcoins sehen will, um die Dateien wieder zu entschlüsseln.
Ransomware ist ein wenig die Plage des Internets im Jahr 2016. Sie ist die harte Art, zu lernen, dass man Anhänge von E-Mails nur öffnen sollte, wenn man den Sender wirklich kennt, und dass ein Backup von Daten kein Privatvergnügen der Paranoiden ist, sondern eine Notwendigkeit.
Prevention: User OpenDNS on all your routers. DO NOT CONNECT THE MOST VITAL PARTS OF THE COMPANY TO THE INTERNET.  “we wanted it that way” – a lot of companies are completely dependant on digital services and computers in general. “wir haben es so gewollt” – viele betriebe haben sich komplett von der digitalen welt abhängig gemacht. these services can be taken as hostages. just as bankers used the “too big to fail” argument to take the money-system as a hostage and threaten to let it fail… so the states paid. wir sind erpressbar geworden.
“we wanted it that way” – a lot of companies are completely dependant on digital services and computers in general. “wir haben es so gewollt” – viele betriebe haben sich komplett von der digitalen welt abhängig gemacht. these services can be taken as hostages. just as bankers used the “too big to fail” argument to take the money-system as a hostage and threaten to let it fail… so the states paid. wir sind erpressbar geworden. 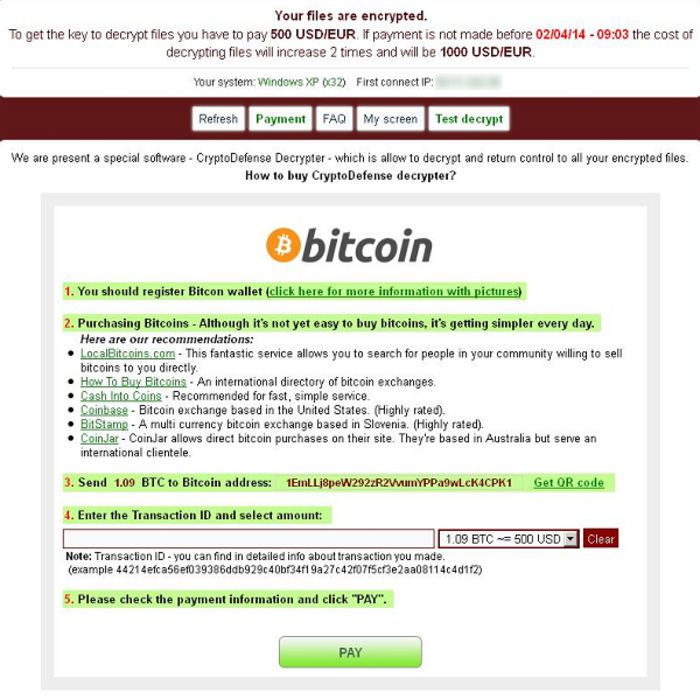 wenn der hacker rein kommt… und deine dateien verschlüsselt… und ein lösegeld verlang damit du wieder an deine dateien kommst… dann ist das…. perverse idiotie… nicht nur vom hacker… sondern von der menschheit als ganzes. shall we give into this shit? NO! “CryptoDefense also spreads mostly through spam email campaigns, and it also claims to use RSA with 2048 bit keys to encrypt the user’s files.” http://blog.emsisoft.com/2014/04/04/cryptodefense-the-story-of-insecure-ransomware-keys-and-self-serving-bloggers/ join the discussion, i hope the community can work out an solution to this latest computer-abuse of the most evil sort: http://blog.emsisoft.com/2014/04/04/cryptodefense-the-story-of-insecure-ransomware-keys-and-self-serving-bloggers/ someone made a good start: http://howdecrypt.blogspot.de/ skype: Sonny_k88 mail: howdecrypt@gmail.com CryptoDefense Keys Recovery_(720p) https://www.youtube.com/watch?v=1E8uQtVu5CE
wenn der hacker rein kommt… und deine dateien verschlüsselt… und ein lösegeld verlang damit du wieder an deine dateien kommst… dann ist das…. perverse idiotie… nicht nur vom hacker… sondern von der menschheit als ganzes. shall we give into this shit? NO! “CryptoDefense also spreads mostly through spam email campaigns, and it also claims to use RSA with 2048 bit keys to encrypt the user’s files.” http://blog.emsisoft.com/2014/04/04/cryptodefense-the-story-of-insecure-ransomware-keys-and-self-serving-bloggers/ join the discussion, i hope the community can work out an solution to this latest computer-abuse of the most evil sort: http://blog.emsisoft.com/2014/04/04/cryptodefense-the-story-of-insecure-ransomware-keys-and-self-serving-bloggers/ someone made a good start: http://howdecrypt.blogspot.de/ skype: Sonny_k88 mail: howdecrypt@gmail.com CryptoDefense Keys Recovery_(720p) https://www.youtube.com/watch?v=1E8uQtVu5CE
More screenshots on this topic: there seems currently no antidote against this? FBI-NSA-CIA stop drone-killing innocent-random people in Afghanistan and focus on helping people with those virus problems! 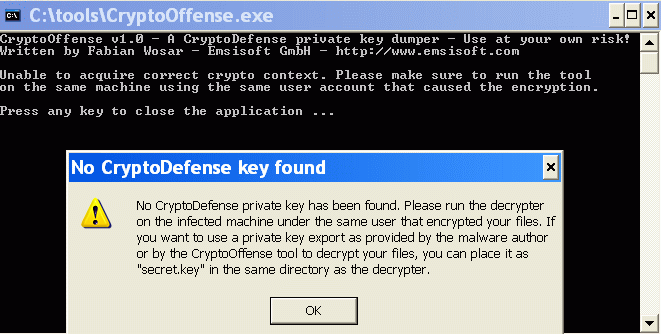 http://www.symantec.com/connect/blogs/cryptodefense-cryptolocker-imitator-makes-over-34000-one-month
http://www.symantec.com/connect/blogs/cryptodefense-cryptolocker-imitator-makes-over-34000-one-month
BINARIES
the virus seems to spread via e-mail attachments. the mails are professionally facked… the sender adress -> @ups.com! nice one. hot all hosts allow this. 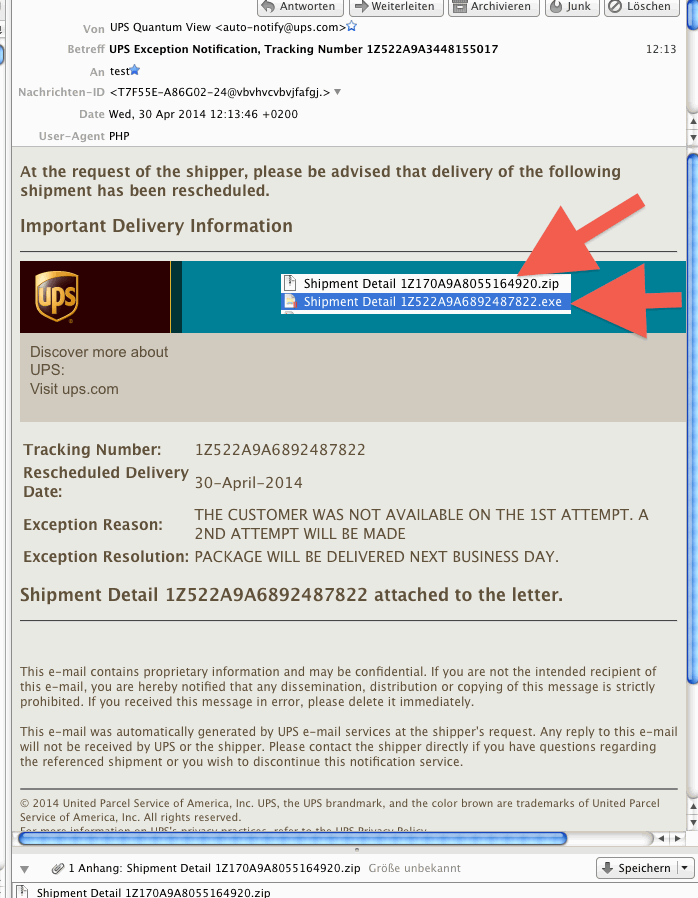 i just got an e-mail that i suspect of having such an virus: ( i am not 100% shure ) evilMail_fullHeaders_invoice.8813544.exe.txt.tar (which was identified by sophos as Mal/DrodZp-A)
i just got an e-mail that i suspect of having such an virus: ( i am not 100% shure ) evilMail_fullHeaders_invoice.8813544.exe.txt.tar (which was identified by sophos as Mal/DrodZp-A)
attachment: (renamed from .exe to .exe_ to prevent execution by accident) invoice.992110098323.exe_ here is another one: evilMail.txt.tar which was identified by sophos as Troj/Wonton-CR) i compared the attachments… and one clearly see similarities… but also how there are certain characters randomized to avoid virus scan detection. that’s like HIV. 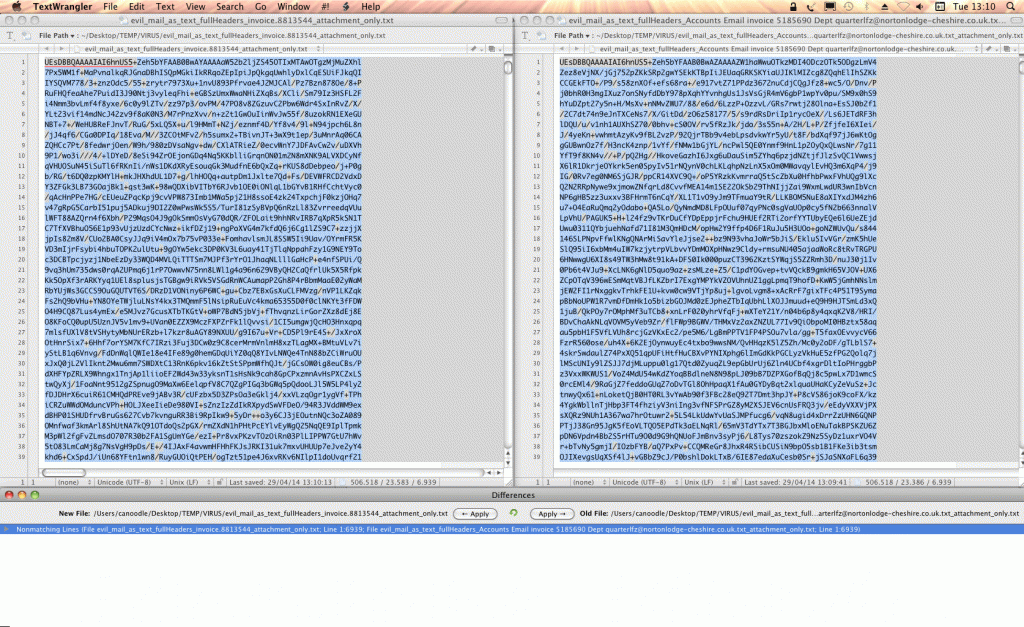
I offer 300€ to the first one showing me a solution to this problem.
to contact me you can add a comment or click the red text above to send me an e-mail. “Most of the time, major PC users prefer to safeguard their computer and prevent from potential threats with their trusted antivirus. However, even though you have the top antivirus program installed, the CryptoDefense virus still gets through without your consent. You may ask why. I should say there is actually no such thing as perfect protection. Virus is created every day. Such virus like the CryptoDefense is designed to have been changed the code so antivirus can’t keep up. Once executed, CryptoDefense virus can disable your security tool. In such circumstance, manual removal is required.” http://viruz.hol.es/remove-cryptodefense-scam-how-to-decrypt-your-files-on-pc/ ELM-Soft-Scanner Results: Emsisoft Emergency Kit - Version 4.0 Letztes Update: N/A Benutzerkonto: COMPUTERNAMEUsername Scan Einstellungen: Scan Methode: Detail Scan Objekte: Rootkits, Speicher, Traces, C:, D: PUPs-Erkennung: Aus Archiv Scan: An ADS Scan: An Dateitypen-Filter: Aus Erweitertes Caching: An Direkter Festplattenzugriff: Aus Scan Beginn: 29.04.2014 06:33:43 C:Dokumente und EinstellungenUsernameAnwendungsdatensoftonic gefunden: Application.AppInstall (A) C:Dokumente und EinstellungenUsername.UsernameAnwendungsdatensoftonic gefunden: Application.AppInstall (A) C:Programmesoftonic gefunden: Application.AppInstall (A) C:Dokumente und EinstellungenUsername.UsernameAnwendungsdatenMozillaFirefoxProfilessjodvpjt.defaultExtensionsffxtlbra@softonic.com gefunden: Application.FireExt (A) C:Dokumente und EinstellungenUsername.UsernameAnwendungsdatenMozillaFirefoxProfilessjodvpjt.defaultSearchpluginssoftonic.xml gefunden: Application.SearchPlug (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESCLSID{4E92DB5F-AAD9-49D3-8EAB-B40CBE5B1FF7} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESCLSID{933B95E2-E7B7-4AD9-B952-7AC336682AE3} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESCLSID{94496571-6AC5-4836-82D5-D46260C44B17} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESCLSID{95B7759C-8C7F-4BF1-B163-73684A933233} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESCLSID{B658800C-F66E-4EF3-AB85-6C0C227862A9} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESCLSID{BC9FD17D-30F6-4464-9E53-596A90AFF023} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESCLSID{DE9028D0-5FFA-4E69-94E3-89EE8741F468} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESCLSID{F25AF245-4A81-40DC-92F9-E9021F207706} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESINTERFACE{4E92DB5F-AAD9-49D3-8EAB-B40CBE5B1FF7} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESINTERFACE{C401D2CE-DC27-45C7-BC0C-8E6EA7F085D6} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESSCRIPTHELPER.SCRIPTHELPERAPI gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESSCRIPTHELPER.SCRIPTHELPERAPI.1 gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESSOFTONIC.DSKBND gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESSOFTONIC.DSKBND.1 gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESSOFTONIC.SOFTONICHLPR gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESSOFTONIC.SOFTONICHLPR.1 gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESSOFTONICAPP.APPCORE gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESSOFTONICAPP.APPCORE.1 gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESSRV.SOFTONICSRVC gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESSRV.SOFTONICSRVC.1 gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESTYPELIB{13ABD093-D46F-40DF-A608-47E162EC799D} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESTYPELIB{74FB6AFD-DD77-4CEB-83BD-AB2B63E63C93} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESTYPELIB{C2AC8A0E-E48E-484B-A71C-C7A937FAAB94} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESVIPROTOCOL.VIPROTOCOLOLE gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESVIPROTOCOL.VIPROTOCOLOLE.1 gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWAREMICROSOFTWINDOWSCURRENTVERSIONEXPLORERBROWSER HELPER OBJECTS{95B7759C-8C7F-4BF1-B163-73684A933233} gefunden: Application.BHO (A) Key: HKEY_LOCAL_MACHINESOFTWAREMICROSOFTWINDOWSCURRENTVERSIONEXPLORERBROWSER HELPER OBJECTS{E87806B5-E908-45FD-AF5E-957D83E58E68} gefunden: Application.BHO (A) Key: HKEY_USERSS-1-5-21-1214440339-1637723038-725345543-1003SOFTWARESOFTONIC gefunden: Application.InstallAd (A) Key: HKEY_USERSS-1-5-21-776561741-515967899-725345543-1150SOFTWARESOFTONIC gefunden: Application.InstallAd (A) Key: HKEY_LOCAL_MACHINESOFTWAREMICROSOFTWINDOWSCURRENTVERSIONUNINSTALLSOFTONIC gefunden: Application.InstallAd (A) Key: HKEY_LOCAL_MACHINESOFTWARESOFTONIC gefunden: Application.InstallAd (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESAPPID{09C554C3-109B-483C-A06B-F14172F1A947} gefunden: Application.InstallDeal (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESAPPID{4E1E9D45-8BF9-4139-915C-9F83CC3D5921} gefunden: Application.InstallTool (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESAPPID{B12E99ED-69BD-437C-86BE-C862B9E5444D} gefunden: Application.InstallTool (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESAPPID{D7EE8177-D51E-4F89-92B6-83EA2EC40800} gefunden: Application.InstallTool (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESAPPIDESCORT.DLL gefunden: Application.Win32.WSearch (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESAPPIDESCORTAPP.DLL gefunden: Application.Win32.WSearch (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESAPPIDESCORTENG.DLL gefunden: Application.Win32.WSearch (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESAPPIDESCORTLBR.DLL gefunden: Application.Win32.WSearch (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESAPPIDESRV.EXE gefunden: Application.Win32.WSearch (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESESCORT.ESCORTIEPANE gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESESCORT.ESCORTIEPANE.1 gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESTYPELIB{4E1E9D45-8BF9-4139-915C-9F83CC3D5921} gefunden: Application.AdReg (A) Key: HKEY_LOCAL_MACHINESOFTWARECLASSESTYPELIB{D7EE8177-D51E-4F89-92B6-83EA2EC40800} gefunden: Application.AdReg (A) C:System Volume Information_restore{E5F384F8-F12C-4169-81A8-2875DBA7BC99}RP120A0018161.exe gefunden: Trojan.GenericKD.1644312 (B) C:System Volume Information_restore{E5F384F8-F12C-4169-81A8-2875DBA7BC99}RP120A0018247.exe gefunden: Trojan.GenericKD.1644312 (B) C:System Volume Information_restore{E5F384F8-F12C-4169-81A8-2875DBA7BC99}RP120A0018248.exe gefunden: Trojan.GenericKD.1644312 (B) C:System Volume Information_restore{E5F384F8-F12C-4169-81A8-2875DBA7BC99}RP120A0018279.exe gefunden: Trojan.GenericKD.1644312 (B) C:System Volume Information_restore{E5F384F8-F12C-4169-81A8-2875DBA7BC99}RP120A0018280.exe gefunden: Trojan.GenericKD.1644312 (B) C:System Volume Information_restore{E5F384F8-F12C-4169-81A8-2875DBA7BC99}RP120A0018449.exe gefunden: Trojan.GenericKD.1644312 (B) C:System Volume Information_restore{E5F384F8-F12C-4169-81A8-2875DBA7BC99}RP120A0018450.exe gefunden: Trojan.GenericKD.1644312 (B) Gescannt 162406 Gefunden 56 Scan Ende: 29.04.2014 09:41:25 Scan Zeit: 3:07:42
How to decrypt my files
- Click Start menu and navigate to Control Panel (for Windows 8, move mouse cursor to the bottom right of the screen, click Settings on Charm bar and go to Control Panel).
- Click User Accounts and Family Safety.
- Go to User Accounts.
- Click Manage your file Encryption Certificates.
- Click Next on Encrypting File System wizard.
- Select all the files you want to decrypt on Certificate details and click Next.
- Choose All Logical Drives and click Next.
In case you have any questions on how to decrypt your files, or the provided method does not word for you, please leave us a comment below and we will reply as soon as possible.
source: http://www.pcthreat.com/parasitebyid-41051en.html
i wonder if the secret.key file is written to harddisk… and then deleted… maybe you could recover this file with get data back ntfs? but this probably works best if you mount the disk in a different pc IMMEDIATELY and read only. otherwise stuff gets overwritten fast. any other ideas?
Pay the thiefes?
CryptoDefense have earned over $34,000 in just one month.
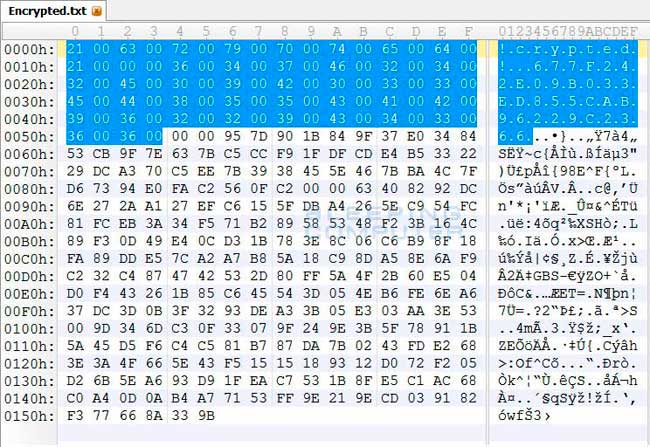
links: http://www.computerbetrug.de/ransomware-erpressung-per-losegeld-trojaner http://www.computerbetrug.de/2014/05/loesegeld-trojaner-verschluesselt-daten-und-fordert-bitcoin-zahlung-8412 what does cryptodefense do on your harddisk: “The files are encrypted using RSA-2048 encryption, which makes them impossible to decrypt via brute force methods. At the beginning of each encrypted file will be two strings of text. The first string is !crypted! and the second string is a unique identifier for the infected computer. An example identifier is 18177F25DA00CD4CBC3D1b8B9F55F018. All encrypted files on the same computer will contain the same unique identifier. This identifier is probably used by the Decrypt Service web site to identify the private key that can be used to decrypt the file when performing a test decryption. You can see these strings of text in a hex editor as shown below:”
Based on research performed by DecrypterFixer, it appears that this infection is installed through programs that pretend to be flash updates or video players required to view an online video. When these downloads are run, numerous adware will be installed along with CryptoDefense. From screenshots of other infected computers, it is also not uncommon for infected computer’s to also have CryptoDefense or CryptorBit installed on them as well. http://www.bleepingcomputer.com/virus-removal/cryptodefense-ransomware-information join the discussion: (in german) http://forum.computerbetrug.de/threads/cryptodefense-cryptowall-decrypter.46139/ english: http://www.bleepingcomputer.com/forums/t/527937/cryptodefense-newest-cryptolocker-variant-details-inside/?hl=%20cryptodefense If you are affected – sign the petition to make governments care: https://www.change.org/petitions/european-union-and-us-government-nsa-recover-our-valuable-files all their NSA-CIA surveillance could not help us… the tor to good and evil: https://dwaves.de/index.php/2014/05/01/tor-anonymizer-technology-can-always-be-used-for-good-and-evil/ http://www.darkreading.com/cryptowall-more-pervasive-less-profitable-than-cryptolocker/d/d-id/1306813? “CryptoWall has encrypted 5.25 billion files. To retrieve their files, victims generally pay ransoms ranging from $200 to $2,000 apiece, but one unfortunate person paid $10,000. Over the course of six months, the CryptoWall operators convinced 1,683 victims to pay up and made $1,101,900 in ransoms. This is rather a small haul when compared to CryptoLocker, which made $27 million in its first two months. Researchers have a few theories as to why CryptoWall is less profitable.”
Links:
https://dwaves.de/2017/05/13/rans0me-ware-updates-wana-crypt0r-2-0/
update: ransomeware generated 25Millione$ https://www.theverge.com/2017/7/25/16023920/ransomware-statistics-locky-cerber-google-research
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!


 CryptoDefense targets text, picture, video, PDF and MS Office files and encrypts these with a strong RSA-2048 key which is hard to undo, KnowBe4 said, adding, “It also wipes out Shadow Copies which are used by many backup programs.
CryptoDefense targets text, picture, video, PDF and MS Office files and encrypts these with a strong RSA-2048 key which is hard to undo, KnowBe4 said, adding, “It also wipes out Shadow Copies which are used by many backup programs. Figure 1. Malicious spam email example Network communications When first executed, CryptoDefense attempts to communicate with one of the following remote locations:
Figure 1. Malicious spam email example Network communications When first executed, CryptoDefense attempts to communicate with one of the following remote locations: