if ssh server is up and secured, it is possible to do so much more with ssh like secure file-transfer of large files (SFTP via FileZilla) or even forward the graphical output of a server-application locally (only that window, not the full screen! 🙂
ssh -X forwarding graphical output of a single program
unique to GNU Linux a powerfull feature is to have only the screen output of a single GUI program be shown local (client) while it is actually started and running on the (ssh x11 forwarding enabled) server 🙂
imagine one has a powerful (like 16x XEon Cores and 128GB of RAM + RAID10) server somewhere remote
the local client is a laptop with external monitor, not so powerful
but one needs the massive computational power of a server running very resource intense (GUI) programs, while one does not want to sit next to a noisy server farm, ssh -X aka x11 forwarding is the answer.
the program will run on the server, but it’s graphical output will be displayed on the local client that is connected via ssh.
the best: it’s all ssh encrypted, the cons: forwarding graphical output over ssh and tcp-ip might be a bit slow refresh rate (no compression!?), if the dev-admin-user needs better performance (frame rate) take a look at xpra.
if the user-dev-admin needs full-screen output look at: x11vnc (it can DEFINATELY should be tunneled through ssh for weak vnc security reasons) or checkout vnc section of this article
from the ssh man page: ssh.man.txt
X11 FORWARDING
If the ForwardX11 variable is set to “yes” (or see the description of the
-X, -x, and -Y options above) and the user is using X11 (the DISPLAY en‐
vironment variable is set)
# on client: # userid is: id -u 1000 # output of env variable DISPLAY is echo $DISPLAY :0 # on server: # userid is: id -u 1000 # output of env variable DISPLAY is echo $DISPLAY localhost:10.0
the connection to the X11 display is automat‐
ically forwarded to the remote side in such a way that any X11 programs
started from the shell (or command) will go through the encrypted chan‐
nel, and the connection to the real X server will be made from the local
machine. The user should not manually set DISPLAY. Forwarding of X11
connections can be configured on the command line or in configuration
files.
The DISPLAY value set by ssh will point to the server machine, but with a
display number greater than zero. This is normal, and happens because
ssh creates a “proxy” X server on the server machine for forwarding the
connections over the encrypted channel.
ssh will also automatically set up Xauthority data on the server machine.
For this purpose, it will generate a random authorization cookie, store
it in Xauthority on the server, and verify that any forwarded connections
carry this cookie and replace it by the real cookie when the connection
is opened. The real authentication cookie is never sent to the server
machine (and no cookies are sent in the plain).
If the ForwardAgent variable is set to “yes” (or see the description of
the -A and -a options above) and the user is using an authentication
agent, the connection to the agent is automatically forwarded to the re‐
mote side.
-X Enables X11 forwarding. This can also be specified on a per-host
basis in a configuration file.
X11 forwarding should be enabled with caution. Users with the
ability to bypass file permissions on the remote host (for the
user’s X authorization database) can access the local X11 display
through the forwarded connection. An attacker may then be able
to perform activities such as keystroke monitoring.
For this reason, X11 forwarding is subjected to X11 SECURITY ex‐
tension restrictions by default. Please refer to the ssh -Y op‐
tion and the ForwardX11Trusted directive in ssh_config(5) for
more information.
(Debian-specific: X11 forwarding is not subjected to X11 SECURITY
extension restrictions by default, because too many programs cur‐
rently crash in this mode. Set the ForwardX11Trusted option to
“no” to restore the upstream behaviour. This may change in fu‐
ture depending on client-side improvements.)
-x Disables X11 forwarding.
-Y Enables trusted X11 forwarding. Trusted X11 forwardings are not
subjected to the X11 SECURITY extension controls.
(Debian-specific: This option does nothing in the default config‐
uration: it is equivalent to “ForwardX11Trusted yes”, which is
the default as described above. Set the ForwardX11Trusted option
to “no” to restore the upstream behaviour. This may change in
future depending on client-side improvements.)
-y Send log information using the syslog(3) system module. By de‐
fault this information is sent to stderr.
ssh may additionally obtain configuration data from a per-user configura‐
tion file and a system-wide configuration file. The file format and con‐
figuration options are described in ssh_config(5).
….
to achieve this simply setup ssh on server and client and then go:
hostnamectl; # tested with server Static hostname: devstation Icon name: computer-desktop Chassis: desktop Operating System: Debian GNU/Linux 10 (buster) Kernel: Linux 4.19.0-13-amd64 Architecture: x86-64 hostnamectl; # tested with client Static hostname: giada Icon name: computer-desktop Chassis: desktop Operating System: Debian GNU/Linux 10 (buster) Kernel: Linux 4.19.0-13-amd64 Architecture: x86-64 # become root su - root # probably already installed but make sure it is apt install ssh # also make sure this package is installed # or the user will encounter error: Error: Can't open display apt install xauth # xeyes is a great way to check if x11 forwarding is working apt install x11-apps # check if in sshd config x11 forwarding is enabled on server cat /etc/ssh/sshd_config |grep X11 X11Forwarding yes # now become non-root user Ctrl+D # logout of server Ctrl+D # re-login to server with -X x11 forwarding parameter enabled ssh -v -X user@192.ip.of.server # simply start a gui program from the server's terminal # the program will start running on the sever # while the gui output will be displayed on the client # welcome to the power of x11! amazing! xeyespluma # pluma is a nice universal no formatting clutter text editor like notepad++
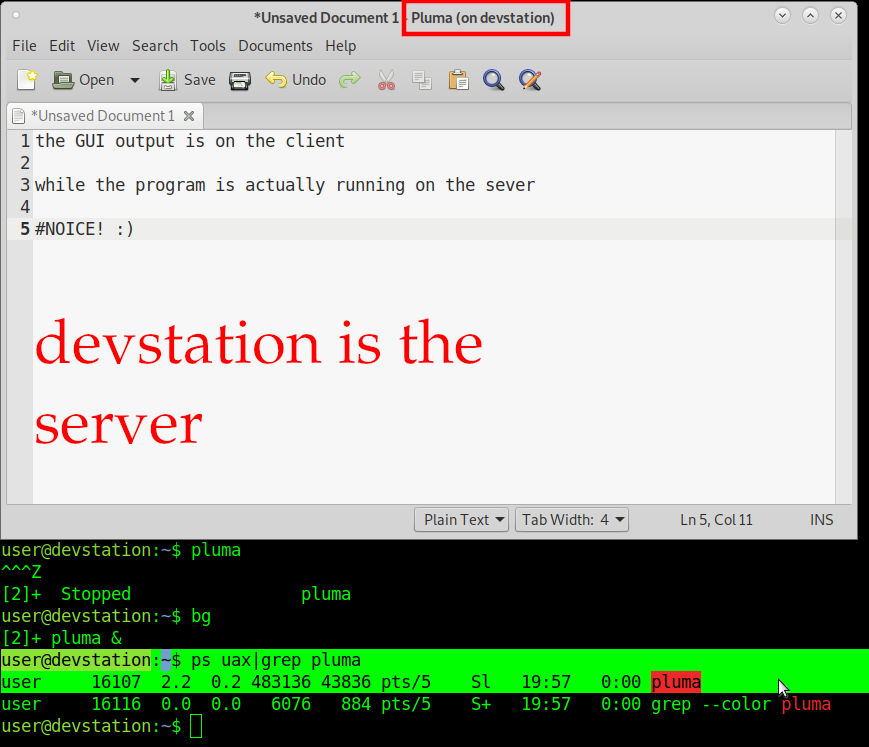
what was also done here is using GNU Linux job control to control how processes run, hit:
Ctrl+Z - to pause the program
let the process keep running in the background
bg [enter]
show all running jobs:
jobs [enter]
[1]- Running android-studio &
[2]+ Running pluma &
bring job 1 into foreground
fg 1 [enter]
okay probably not intended for gaming 😀
while xclock (vector grafics) runs smooth
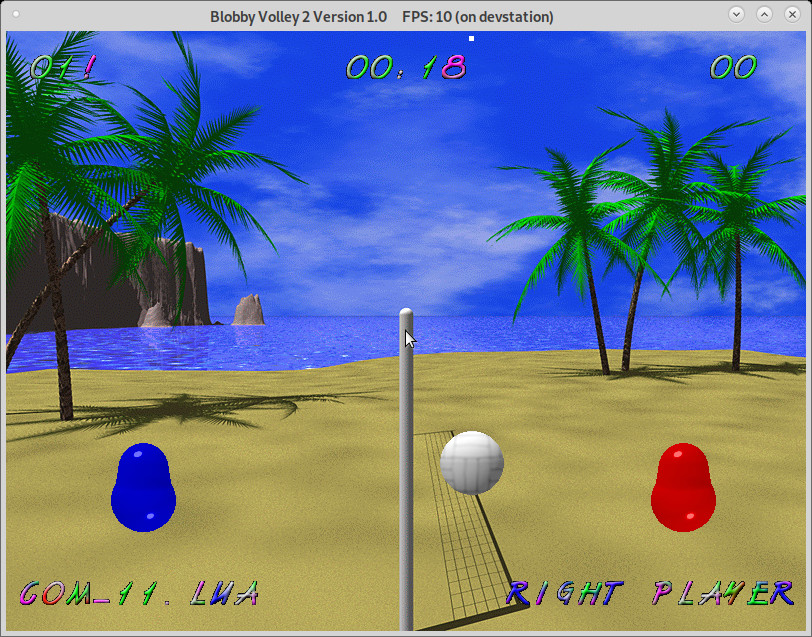
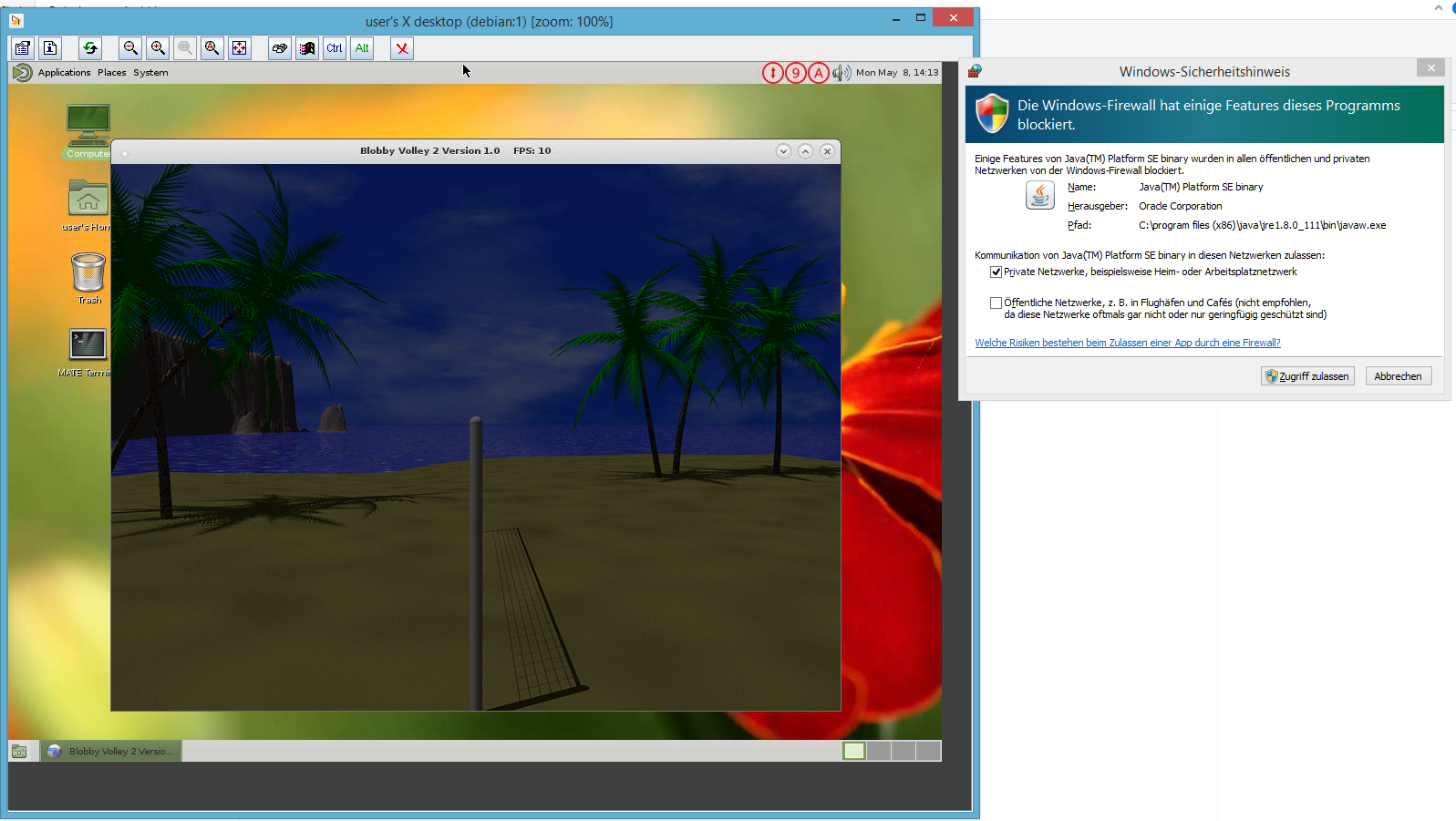
# this is the ssh-server ps uax|grep clock user 3358 0.3 0.6 9984 6476 pts/1 S+ 14:21 0:00 xclock -update -1 user 3360 0.0 0.2 4556 2296 pts/2 S+ 14:21 0:00 grep clock # install blobby volley on server su - root apt update apt install blobby Ctrl+D # log off root, become non-root again # run it blobby
the framerate for x11 over ssh is pretty bad (like 6 to 10 fps) because it is not a very efficient protocol when it comes to animations and games
it is possible to speed up things a little by enabling compression
-C
Requests compression of all data (including stdin, stdout, stderr, and data for forwarded X11, TCP and UNIX-domain connections).
The compression algorithm is the same used by gzip(1).
Compression is desirable on modem lines and other slow connections, but will only slow down things on fast networks. The default value can be set on a host-by-host basis in the configuration files; see the Compression option.
but all the cyphers seem to be “equally” slow X-D
sh -Q cipher; # show list of available cyphers 3des-cbc aes128-cbc aes192-cbc aes256-cbc rijndael-cbc@lysator.liu.se aes128-ctr aes192-ctr aes256-ctr aes128-gcm@openssh.com aes256-gcm@openssh.com chacha20-poly1305@openssh.com ssh -Y -C -c aes128-gcm@openssh.com user@192.ip.of.sever
here is the xplanation:
“To clarify why X11 over ssh will never be fast: the X protocol deals with low-level drawing like lines and circles, and with low-level events such as “the mouse moved 3 pixels to the left.” Modern GUI toolkits like GTK and Qt don’t draw lines, they draw images. When X11 goes over SSH, it must constantly send image data and low-level mouse events. A high-level protocol like NX, VNC, or Remote Desktop can reduce bandwidth and latency by being aware of how toolkits work.” (src)
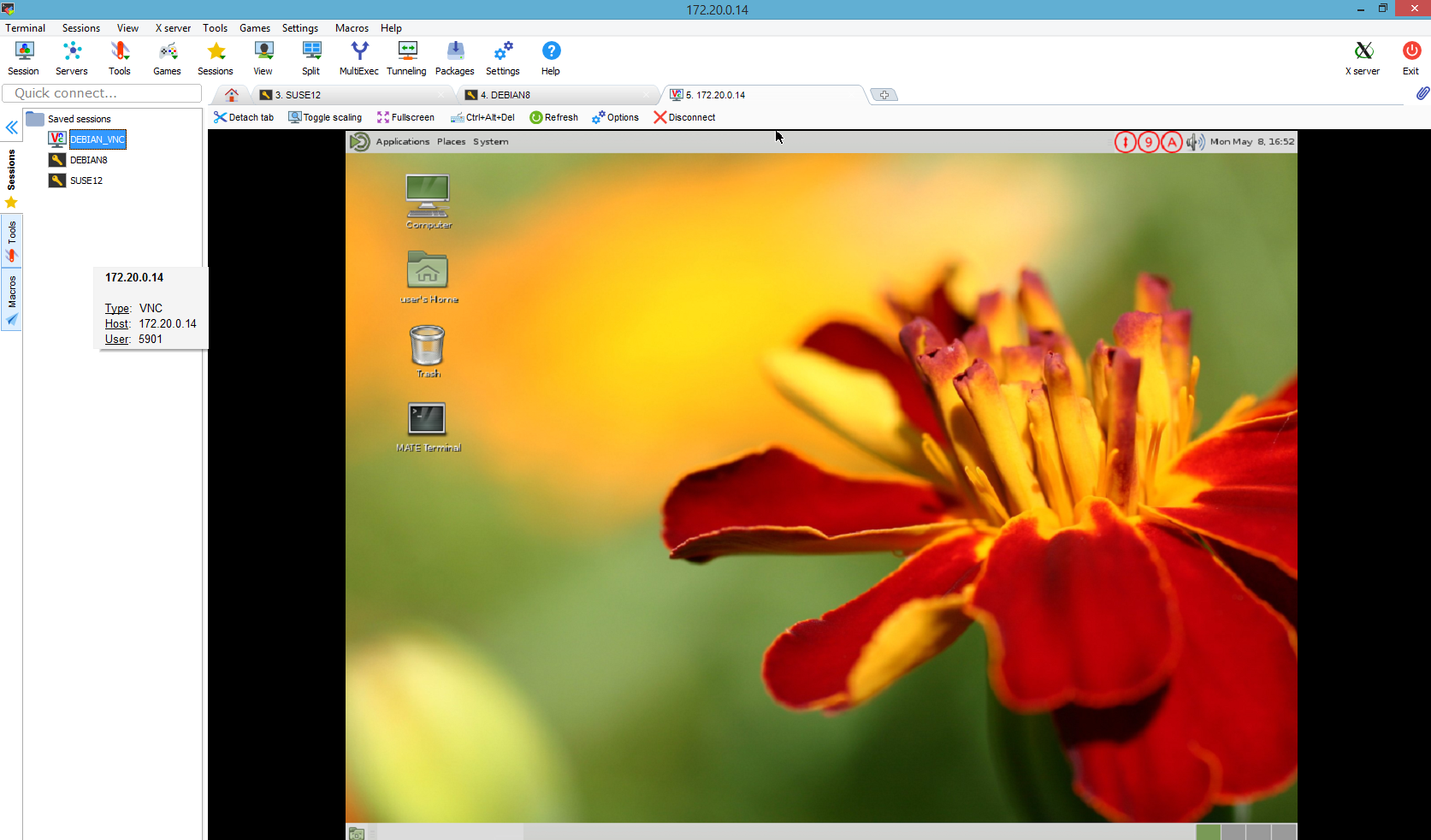
now: 100% remote desktop
there seem to be problems forwarding a whole session, when different display-managers (gdm3, lightdm etc. pp.) are used – so it is probably better
1. to use a VNC server-client architecture
2. allow on server only VNC connections from localhost
3. tunnel all VNC traffic over ssh
…so weak VNC passwords “do not matter” so much.
still have to find out what vnc-server-client combination works best across distributions and operating systems. (also windows<->linux, osx<->linux, linux<->windows)
# i tried "gnome-session", suse12(gdm)->debian8.7(lightdm+gnome2)
apt-cache search gnome-session; # search for gnome-session package
gnome-session-fallback - GNOME Session Manager - GNOME Flashback (transitional package)
gnome-session-flashback - GNOME Session Manager - GNOME Flashback session
gnome-session - GNOME Session Manager - GNOME 3 session
gnome-session-bin - GNOME Session Manager - Minimal runtime
gnome-session-common - GNOME Session Manager - common files
gnome-session-canberra - GNOME session log in and log out sound events
openbox-gnome-session - command line utility to run Openbox as GNOME session
# or vice-versa suse12(gdm)<-debian8.7(lightdm+gnome2) did not work.
WARNING **: Couldn't connect to accessibility bus: Failed to connect to socket /tmp/dbus-R6bKx4jMEh: Connection refused
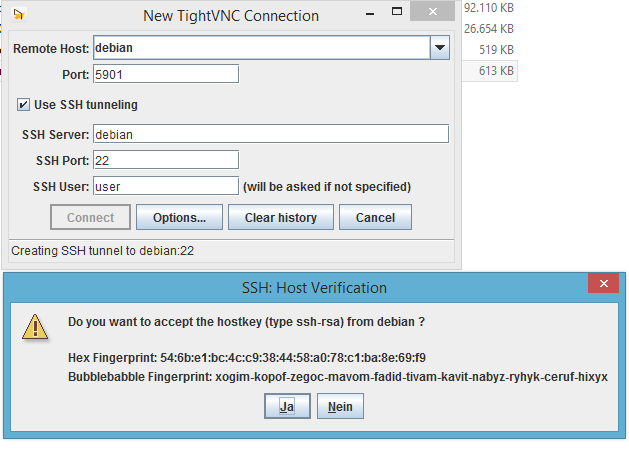
therefore it would be vice to tunnel VNC
tightVNCserver on Debian and Java Client on Windows 8
works like a charm.
http://www.tightvnc.com/download.php
su; # become root apt-get update; apt-get install tightvncserver; # install server exit; # become normal user tightvncserver; # initial setup of server You will require a password to access your desktops. Password: # should be 8 characters Verify: Would you like to enter a view-only password (y/n)? n # now run server again, to start the server with your password settings tightvncserver; # you see console output like this New 'X' desktop is debian:1 Creating default startup script /home/user/.vnc/xstartup Starting applications specified in /home/user/.vnc/xstartup Log file is /home/user/.vnc/debian:1.log # checkout what port it is using # try 5900 or 5901 netstat -tulp | grep vnc (Not all processes could be identified, non-owned process info will not be shown, you would have to be root to see it all.) tcp 0 0 *:5901 *:* LISTEN 2025/Xtightvnc tcp 0 0 *:x11-1 *:* LISTEN 2025/Xtightvnc
ssh yes – full desktop yes – but no gaming 😀
tightVNCserver on Debian8.7 and MobaXterm client on Windows 8
availabel VNC software
apt-cache search vnc|grep server # vnc servers tightvncserver - virtual network computing server software vino - VNC server for GNOME vnc4server - Virtual network computing server software vncsnapshot - A utility that takes JPEG snapshots from VNC servers websockify - WebSockets support for any application/server x11vnc - VNC server to allow remote access to an existing X session xrdp - Remote Desktop Protocol (RDP) server linuxvnc - VNC server to allow remote access to a tty pagekite - Make localhost servers publicly visible. # for developers interesting libvncclient0 - API to write one's own vnc server - client library libvncserver-config - API to write one's own vnc server - library utility libvncserver-dev - API to write one's own vnc server - development files libvncserver0 - API to write one's own vnc server # what vnc related software is available? apt-cache search vnc archipel-agent-virtualmachine-vnc - Virtual Machine Orchestration (Agent Virtualmachine VNC) autocutsel - Keep the X clipboard and the cutbuffer in sync avahi-ui-utils - Avahi GTK+ utilities chaosreader - trace network sessions and export it to html format conspy - Remote control of Linux virtual consoles directvnc - VNC client using the framebuffer as display dmtcp - Checkpoint/Restart functionality for Linux processes dmtcp-dbg - Debug package for dmtcp gitso - simple frontend for reverse VNC connections (remote assistance) gnome-rdp - remote desktop client for GNOME gir1.2-gtk-vnc-2.0 - GObject introspection data for GTK-VNC. gvncviewer - VNC viewer using gtk-vnc libgtk-vnc-1.0-0 - VNC viewer widget for GTK+2 (runtime libraries) libgtk-vnc-1.0-0-dbg - VNC viewer widget for GTK+2 (debugging symbols) libgtk-vnc-1.0-dev - VNC viewer widget for GTK+2 (development files) libgtk-vnc-2.0-0 - VNC viewer widget for GTK+3 (runtime libraries) libgtk-vnc-2.0-0-dbg - VNC viewer widget for GTK+3 (debugging symbols) libgtk-vnc-2.0-dev - VNC viewer widget for GTK+3 (development files) libgvnc-1.0-0 - VNC gobject wrapper (runtime libraries) libgvnc-1.0-0-dbg - VNC gobject wrapper (debugging symbols) libgvnc-1.0-dev - VNC GObject wrapper (development files) python-gtk-vnc - VNC viewer widget for GTK+2 (Python binding) guacamole-tomcat - Tomcat-based Guacamole install with VNC support guacd - Guacamole proxy daemon libguac-client-vnc0 - VNC support plugin for Guacamole hydra - very fast network logon cracker hydra-gtk - very fast network logon cracker - GTK+ based GUI libsvnqt7 - Qt wrapper library for Subversion krdc - Remote Desktop Connection client krdc-dbg - Remote Desktop Connection client debugging symbols krfb - Desktop Sharing utility libnet-vnc-perl - Perl module implementing a simple VNC client libvncclient0 - API to write one's own vnc server - client library libvncclient0-dbg - debugging symbols for libvncclient libvncserver-config - API to write one's own vnc server - library utility libvncserver-dev - API to write one's own vnc server - development files libvncserver0 - API to write one's own vnc server libvncserver0-dbg - debugging symbols for libvncserver linuxvnc - VNC server to allow remote access to a tty nova-console - OpenStack Compute - console nova-consoleproxy - OpenStack Compute - NoVNC proxy novnc - HTML5 VNC client - daemon and programs python-novnc - HTML5 VNC client - libraries pagekite - Make localhost servers publicly visible. pyvnc2swf - screen recording tool with Flash (SWF) output libsvncpp-dev - Subversion C++ library (development files) libsvncpp3 - Subversion C++ shared library remmina - remote desktop client for GNOME desktop environment manpage remmina: remmina.man.txt remmina-plugin-vnc - VNC plugin for remmina remote desktop client ssvnc - Enhanced TightVNC viewer with SSL/SSH tunnel helper libsvnclientadapter-java - High-level Java API for Subversion (library) libsvnclientadapter-java-doc - High-level Java API for Subversion (documentation) tightvncserver - virtual network computing server software xtightvncviewer - virtual network computing client software for X vinagre - remote desktop client for the GNOME Desktop vino - VNC server for GNOME virt-manager - desktop application for managing virtual machines virt-viewer - Displaying the graphical console of a virtual machine vnc4server - Virtual network computing server software xvnc4viewer - Virtual network computing client software for X vncsnapshot - A utility that takes JPEG snapshots from VNC servers vtgrab - A VNC like console monitoring websockify - WebSockets support for any application/server winswitch - tool to start and control remote sessions x11vnc - VNC server to allow remote access to an existing X session x11vnc-data - data files for x11vnc x2vnc - Link a VNC and an X display together, simulating a multiheaded display xorg-server-source - Xorg X server - source files xpra - tool to detach/reattach running X programs xpra-dbg - xpra -- debugging symbols xrdp - Remote Desktop Protocol (RDP) server
man pages:
Links:
https://access.redhat.com/discussions/3240641
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!