if fail2ban fails to ban:
https://dwaves.de/2017/07/27/centos7-replaced-firewall-iptables-with-firewalld-iptables-vs-nftables-benchmark-performance-comparison-scalability-when-facing-ddos-scenarios
Update!
“Within hours of that story running, the two alleged owners — 18-year-old Israeli men identified in the original report — were arrested in Israel in connection with an FBI investigation into the shady business, which earned well north of $600,000 for the two men.
In my follow-up report on their arrests, I noted that vDOS itself had gone offline, and that automated Twitter feeds which report on large-scale changes to the global Internet routing tables observed that vDOS’s provider — a Bulgarian host named Verdina[dot]net — had been briefly relieved of control over 255 Internet addresses (including those assigned to vDOS) as the direct result of an unusual counterattack by BackConnect.
Asked about the reason for the counterattack, BackConnect CEO Bryant Townsend confirmed to this author that it had executed what’s known as a “BGP hijack.” In short, the company had fraudulently “announced” to the rest of the world’s Internet service providers (ISPs) that it was the rightful owner of the range of those 255 Internet addresses at Verdina occupied by vDOS.
Short for Border Gateway Protocol, BGP is a mechanism by which ISPs of the world share information about which providers are responsible for routing Internet traffic to specific addresses. However, like most components built into the modern Internet, BGP was never designed with security in mind, which leaves it vulnerable to exploitation by rogue actors.”
Source: http://krebsonsecurity.com/2016/09/ddos-mitigation-firm-has-history-of-hijacks/
There are people with malicous business ideas – one of them is – DDoS as a service – you pay for “stress testing” other people’s (except israeli websites) webservers, which could lead of RAM depletion on those servers which might make MySQL crash and so on…
i think fail2ban can help protect against DDoS
https://www.maketecheasier.com/fail2ban-protect-apache-ddos/
https://easyengine.io/tutorials/nginx/fail2ban/
https://www.startpage.com/do/dsearch?query=fail2ban+DDoS&cat=web&pl=opensearch&language=english
“Multiple vDOS tech support tickets were filed by customers who complained that they were unable to order attacks on Web sites in Israel. Responses from the tech support staff show that the proprietors of vDOS are indeed living in Israel and in fact set the service up so that it was unable to attack any Web sites in that country — presumably so as to not attract unwanted attention to their service from Israeli authorities. Here are a few of those responses:
(‘4130′,’Hello `d0rk`,\r\nAll Israeli IP ranges have been blacklisted due to security reasons.\r\n\r\nBest regards,\r\nP1st.’,’03-01-2015 08:39),”
It isn’t going to change anytime soon. Good ISPs won’t allow customers to announce just any network. They first verify that the customer is actually assigned that network in the LIR/RIR, and then and only then add it to the filter of networks which a customer can announce. This works in an honest and ethical world. The Internet goes beyond this to many shady places.
There is a standard to try to protect against this. I’ve not read it, but I would assume the LIR/RIR will sign a record basically giving the assigned entity authority to announce it. This would protect against forgery. Unfortunately, no BGP routers speak this language (yet):
http://packetpushers.net/bgpsec-signatures-performance/
As always, great reporting Brian.
Unfortunately, as with most of these kinds of stories, the important take-aways, both for policy makers and for the public at large, kind-of get lost in the shuffle.
One of these is that the smallest unit of IPv4 address space that can, in practice, be hijacked is a so-called /24 block of consecutive addresses. Such a block consists of exactly 256 consecutive addresses. Thankfully, it is still somewhat rare that any such block of addresses is inhabited entirely and exclusively by bad actors. The implication is that BGP hijacking of the type you’ve described WILL, in general, result in some collateral damage to innocents, and perhaps even a lot of that.
Also, of course, on the other side of the ledger, strong DDoS attacks quite frequently impact many of the nearby neighbors of the actual intended victim, in many cases taking down entire ISPs.
As at least a couple of people noted in the NANOG mailing list thread you provided a pointer to, self-regulation in the Internet industry simply has not worked. It has not worked to stop hijacks, it hasn’t worked to stop DDoS attacks, and it hasn’t worked to stop spamming, hacking, etc. So one naturally is forced to wonder “Where are the grownups?”
I suspect that the Tier 1 backbones, if they elected to work together, could rapidly stomp out all of these problems. So the question then becomes “Why don’t they?” It may be for fear of being dragged into some sort of hypothetical future anti-trust litigation, but more probably it is just simple economics. They’ve probably done the calculations and concluded that they’ll make more money by just allowing all of this nonsense to continue. Certainly, the more DDoS attacks that occur, the more everyone needs additional bandwidth to try to defend against those, and this ever-increasing need for bandwidth probably suits all of the sellers of bandwidth just fine.
I don’t see any of this ending well, or even ending without government intervention, as odious as that may be. The best analogy that comes immediately to mind is that the Tier 1 backbones are, in effect, selling both guns and bullet-proof vests, and then kicking back and sipping champaign in their luxury condos in Vail while the Interent for the rest of us slides inexorably into chaos.
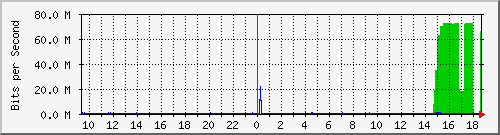
655Gbps DDoS against Krebs to try and silence this story, BackConnect must be quite upset with you! Impressive mitigation by Akamai though
!?!??
Source:
http://krebsonsecurity.com/2016/09/israeli-online-attack-service-vdos-earned-600000-in-two-years/
What is a layer 4 DDoS attack?
What Is a Layer 4 DDoS Attack?
A distributed denial-of-service, or DDoS, attack is one of the most common ways to slow down or even disable a particular site’s servers. Sites that find themselves targeted by DDoS attacks can be out of commission for days due to the resulting server crash. As the methods of launching DDoS attacks continue to evolve, companies that want to protect their servers must reach for protection methods that evolve just as fast.
Among the various types of DDoS attacks are layer attacks, which target particular OSI layers. The Layer 4 attack is aimed at the transport layer, which uses TCP and UDP protocols to regulate transmissions between hosts and also between the hardware, data link and network layers. A typical Layer 4 attack uses SYN Flood or Smurf attacks to overload bandwidth, networking equipment and connectivity.
Layer 4 DDoS attack
Flooding and Smurfing
SYN flooding is a long-standing attack method that ties up the host’s TCP so that the server can no longer make new TCP connections in response to legitimate requests for access. Direct SYN flooding involves firing off a large number of SYN segments directly at the host’s servers, with no spoofing. This kind of attack is also easy to defend against with simple IP blocking. When SYN flooding is used in a DDoS attack, the flooding comes simultaneously from many drone machines with constantly changing IPs. For this reason, a SYN flooding attack can be difficult to defend against without highly effective ingress filtering that can keep out the bots while allowing access to legitimate clients.
A Smurf attack is a DDoS attack that uses ICMP ping-back functions to send large numbers of pings to the server’s IP. The server’s network then responds to the pings and is slowed down to the point of becoming unusable.
Simply blocking the ping request by firewall would help. VestaCP can do that from WebConfigInterface
A related type of attack is known as a Fraggle attack. This sends large volumes of spoofed UDP signals to the network’s routers. While most networks today are protected against these types of attacks due to changes in network and router configuration, a new form of this mode of attack is the DNS amplification. This attack uses public access to a domain name system server to overload the target host with DNS response traffic by sending open-ended requests that require a high-volume response.
DNS amplification attack on a root DNS server
Layer 4 Attack Mitigation
As increasingly sophisticated Layer 4 DDoS attacks have been around for a long time, solutions have also continued to evolve. There are several common types of defenses.
1. Local Software
Some companies such as Akamai, Cloudflare, and Incapsula try to defend against attacks by installing or writing protective software, such as filtering code or local firewalls. This is generally not very effective, as the extensive and complex attacks common today are easily able to overload off-the-rack firewalls or filtering software.
2. ISP
Some businesses use their internet service provider’s bandwidth to guard against attacks. However, not all ISPs are seriously committed to providing effective protection. Their main goal is to provide bandwidth, not security. They often do not have the resources or expertise to provide up-to-date protection. Another problem with purchasing protection from an ISP is that many businesses today do not rely on just one provider. Purchasing protection from each provider separately can raise costs and result in an ineffective patchwork of various solutions.
3. Hardware
Many companies have developed dedicated hardware to combat attacks. Typically, these are devices designed to detect and block malicious signals. However, there are several disadvantages to using hardware. First of all, the components are expensive. Businesses also spend additional resources on maintenance and operation, at times needing to hire someone just to operate and monitor the devices. Hardware will also fail to protect servers when network capacity is overloaded. As most attacks today rely on sheer volume, the majority of potential attacks will not be mitigated by specialized hardware.
4. Cloud Provider
In today’s world, cloud providers are considered by many to offer the most up-to-date and effective mitigation against DDoS attacks. A cloud provider specializes in defending from attacks. This means that all of its resources are going to be dedicated to developing new techniques, watching for new types of threats and providing large amounts of bandwidth capable of handling all amounts of network traffic. Cloud providers combine hardware and software innovations to filter out malicious traffic while admitting legitimate clients so that attacks do not slow down business. They also provide tools such as an IP stresser, also called a booter, to simulate overloads from an attack and then use the resulting data to shore up the system’s defences.
Simulating DDoS attacks
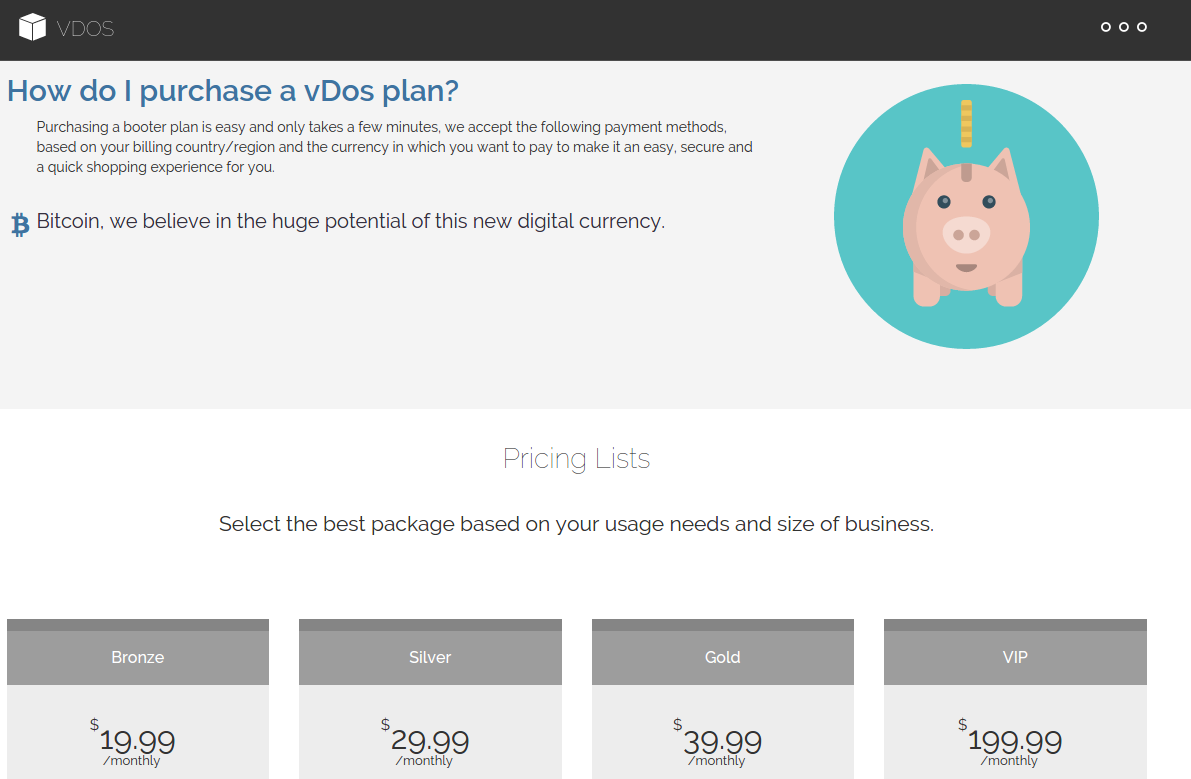
Simulating DDoS attacks is now easier than ever, vDos IP stresser offers 13 layer 4/3 attack methods including DNS, SNMP and NTP amplification floods along with TCP based methods such as spoofed SYN-flood, ACK flood and TCP-AMP to satisfy all your stress testing needs.
How to Prevent DDoS Attacks
Just as the way we use the internet has evolved over the years, so too have the threats that endanger internet users. Distributed denial-of-service attacks, more commonly known as DDoS attacks, pose a serious threat not only to websites, but also to apps and web services. If you depend on your site, service or app for business, knowing how to prevent a crippling attack can mean the difference between your business going strong and extensive as well as expensive downtime. Learn how to protect and strengthen your site while safeguarding your revenue and peace of mind.

On-going DDoS attack
Know How Much You Can Handle
One of the biggest problems with online companies is that they have no idea of how much traffic their sites or apps can easily handle before performance starts suffering. This lack of information often results in a company not being able to recognize an attack when one is launched. Statistics reports and tools are available that deposit data into a statistics file. You’ll be able to see signs of an attack, such as socket errors and query rates. Rather than using statistics reports to see what DDoS attacks look like, use the information to establish a foundation for the amount of traffic your site, app or server can process. It’s when that baseline is irregular that you should grow concerned.
Use an IP stresser
Now, if you truly want to see what an attack looks like, you’ll want to use an IP booter. The way the tool works is you can simulate a barrage of heavy traffic under controlled circumstances. Rather than remain within the limits of what your site can easily handle, the booster instead stresses it beyond its normal capabilities. Here is where you get a solid idea of what an attack looks like and the different ways in which attacks affect your online stability and limits. You can use the results of the stress test to design mitigation strategies so that your business doesn’t fold in on itself if it’s ever attacked by a real hacker.
Pay Attention to Your Internet-Facing Infrastructure
Besides knowing your limits and using an IP stresser to prevent malicious assaults, it’s also a good idea to take a close look at your router and switch framework, online connections, firewalls and other protective measures. What you’re looking for are weaknesses and potential points of failure. Once you’ve found them, see if there’s a way to effectively remedy the situation, and do so in a way that’s cost efficient. Depending on where most of your traffic originates, you may want to look into establishing a server near that location for faster responses.
Buy More Bandwidth
While one of the easiest ways to prevent an attack, buying more bandwidth is also one of the most expensive. If you can afford it, you want to go beyond simply buying more capacity than a hacker can overload. Specifically, you want your extra bandwidth spread out over several servers and in several data centers, all with a well-balanced load. One thing to bear in mind with this prevention strategy is that DDoS attacks have started to grow in size, and that size might outstrip your financial capacity to buy up more bandwidth.
Give Your DNS Server Some TLC
In order to keep it from being caught up in an online attack, it’s best that you lock down your DNS server rather than allow it to remain as an open resolver. One issue to bear in mind with this tip is it’s still possible that your servers will be attacked rather than your site. Should this happen, your site will function, but visitors will find themselves unable to connect to your servers and resolve your domain name. The same type of protection that shields your site should be used to safeguard your DNS. You may also want to look into working with a company that offers a redundant DNS.
Contingency Plans
Going back to the mitigation strategies touched on above, one good idea is to utilize caching servers to create static content that can take the place of dynamic resources during an online onslaught. There should also be detection systems that alert you the moment something might be amiss so that you can act accordingly.
Much like insurance, learning how to prevent a DDoS attack ensures you and your network, app or site are prepared for the worst. Make sure you occasionally update and review your prevention methods so that you’re ready for the latest methods of attack.
Related Links:
http://research.dyn.com/2016/09/backconnects-suspicious-bgp-hijacks/
https://dwaves.de/2017/02/10/simple-self-made-ddos-test-of-your-site/
https://dwaves.de/2016/09/08/ddos-as-a-service-vdos-poodlestresser-and-israel-fbi-arrests/
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!

