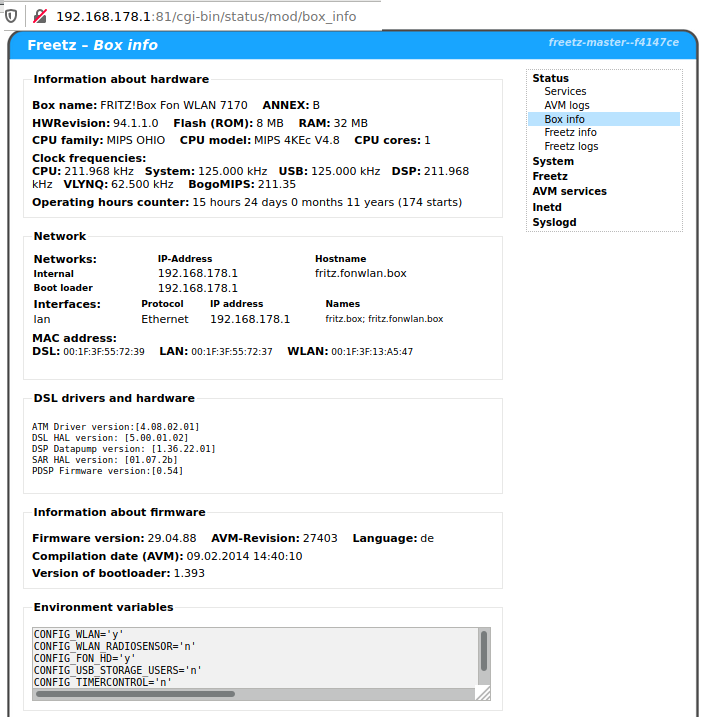
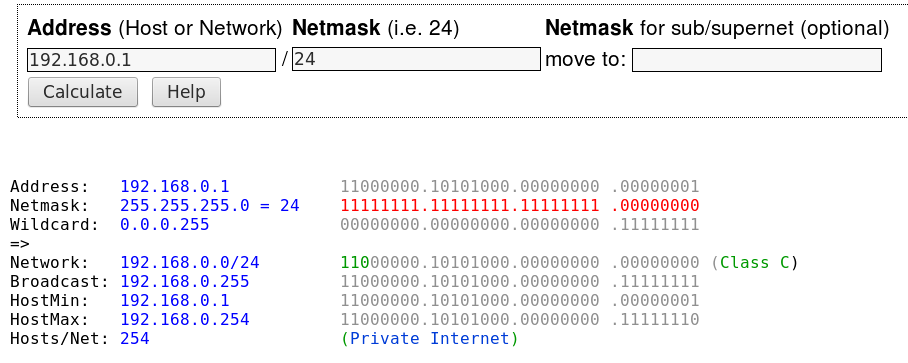
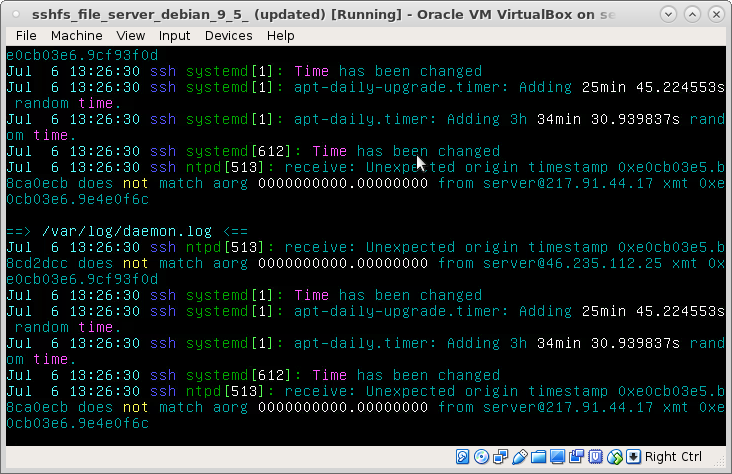
Connection refused nothing has changed on server or client side so was the server hacked? NO! the solution is way more simple: the guest wifi might block ssh traffic give it a try: if not even telnet can get at […]
JavaScript can compromise the user’s network devices! pretty evil are devices/routers with security problems, that can be exploited from javascript. so basically opening a webpage with a browser that has javascript enabled (which most browsers have) might scan the user’s […]
the idea is: ssh is running on 22 what if user can connect localport 2222<->22 and user can then connect to localport:2222 and it will be forwarded to localport:22? and YES IT IS POSSIBLE 🙂 which the massively complex socat: […]
this age of mass surveillance… … who is observing “the observers”? guess with it-security and internet-security (internet = roads, cars = computers that users use every day) it is like with real-life-security – there is no 100% security. all users […]
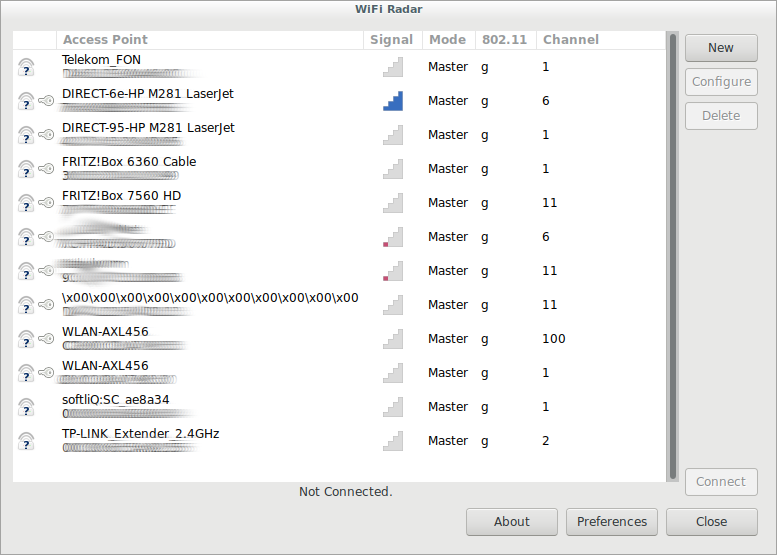
it is nice to get an graphical overview what wifi wlan networks access points one is surrounded by. also good to know what direction to point antenna/laptop to have best reception. because this allows to fine-tune what channel best to […]
scroll down and behave! (slaves of digital dictatorships) short version summary of 1984: short version: 1984 needs to be avoided at any cost. because: it is evil. (Google did not drop it’s motto “don’t be evil” for nothing) in essence: […]
hostnamectl; # tested on Icon name: computer-desktop Chassis: desktop Operating System: Debian GNU/Linux 10 (buster) Kernel: Linux 4.19.0-8-amd64 Architecture: x86-64 su – root; # become root apt update apt install rfkill rfkill list all 0: phy0: Wireless LAN Soft blocked: […]
firewall & the GNU-Linux Pinguin: firewalls: where do thy go? and does thee protect from DDoS? as always in software development and as always in GNU Linux, there is not “one” firewall system, no, there are many and it is […]
wishes for next year: free wifi for eels (and other creatures) Why does EVERYONE have to run their own WIFI / pay their OWN internet access? When it would be enough to have one fast internet access plus 2-3x WIFI […]
every once and a while… laptops and notebooks run out of battery… and when one manages to plug them in just 1% before stalling… the wifi on Debian might already be in hibernation and hardware on off does not help […]
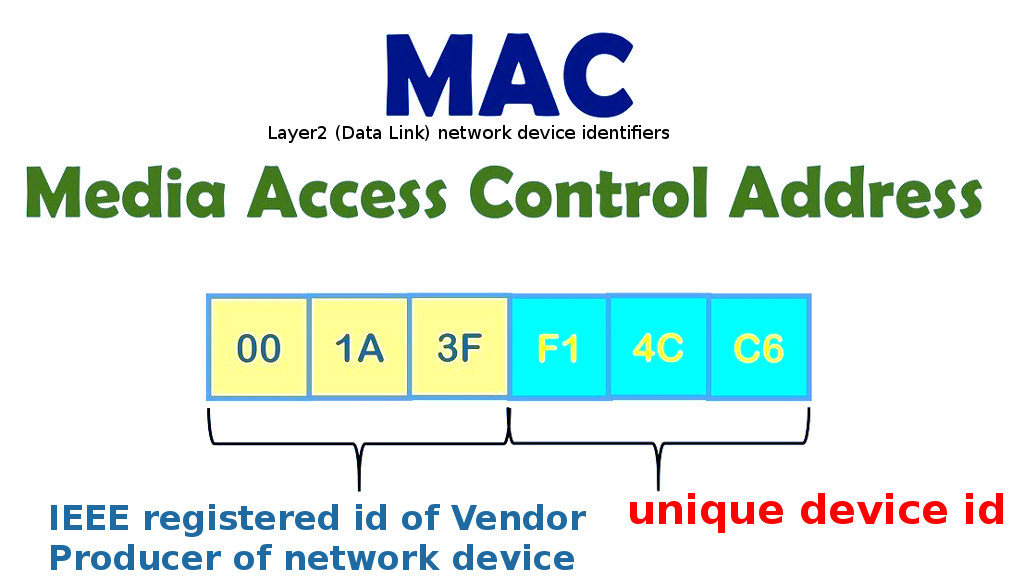
about MAC address(es) not every switch has an IP assigned (if it has no web management interface, it does not need to) but it will have a MAC address. MAC address are per vendor and per device unique identifiers that […]
EDIMAX EW-7612UAn V2 THE ONLY (?) GNU Linux WIFI WLAN Adapter that works OUT OF THE BOX on all GNU Linux systems (ODROID RASPBERRY AND Desktop GNU Linux) ONLY BUY FROM HARDWARE VENDORS THAT SUPPORT FREE & OPEN […]
what IT can learn from nature: (src) mostly US users affected. Big Business: Big Companies and Big Money can afford Big Staff to maintain and secure their products, but they also provide Big Infrastructure (AWS, Office) and thus a single […]
bc is a nice calculator that one can use under linux terminal. a good exercise: count from 0 to 255 and convert it to binary # install # debian/ubuntu apt install bc # fedora/redhat/centos yum install bc # run bc […]
Why is quantum computing important: optimization Update: Google claims to have reached quantum supremacy The tech giant unveiled its x-quantum computer chip Bristlecone in March 2018 (src: cnet) original nasa paper: https://drive.google.com/file/d/19lv8p1fB47z1pEZVlfDXhop082Lc-kdD/view book: https://deepai.org/machine-learning/researcher/eleanor-g-rieffel https://www.amazon.com/Quantum-Computing-Introduction-Engineering-Computation/dp/0262015064 Scott’s Supreme Quantum Supremacy FAQ! […]
Warum VoIP? Viele Anbieter von LTE z.B. bieten gar keine Festnetz-Telefonie an, sondern nur Internet. (das zum Teil (nicht günstiger) aber schneller (und schnurloser via Handy-Netz) als die Telekom (4G/LTE/UMTS)). D.h. man braucht dann noch einen weiteren Anbieter der die […]
it might sound strange… and even if it sucks, but if you are concerned about security, call me paranoid but: your company’s critical infrastructure SHALL NOT BE REACHABLE BY WIFI! (especially not if you are running a nuclear power plant, […]
the similarity is startling. They could be clones! (they probably are) except: D-Link is from Taiwan (still not China) and TP-Link is from Shenzen China bought recently 3x of the TP-Link 108 and can confirm they are doing a great […]
also roaming within the “(more or less)United States of Europe” (EU) is pretty scary endavor. If you travel across the EU and wish to use your home mobile phone number – you will NEVER know what this phone call or […]
servers/clients/computers/programs/services/webservers need accurate time… they usually get it from time servers that have an atomic clock attached to their USB port. (just guessing) ping time.google.com PING time.google.com (216.239.35.4) 56(84) bytes of data. 64 bytes from time2.google.com (216.239.35.4): icmp_seq=1 ttl=46 time=43.5 […]
the best about samba: thanks for samba, it provides users with a fast (of course depends also on harddisk speed) rock-solid no-limit-to-maximum-users file-server for maximum file-transfer-and-sharing-and-storage productivity (and they will USE that T: temp drive for EVERYTHING! prepare for TERRABYTES […]
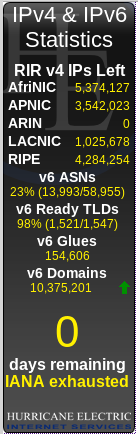
IPv6: Introduction it’s the year 2019, roughly 14% of the web is running ipv6. you can watch real time statistics here: (i have no clue how accurate the data is, how they are generated) https://ipv6.he.net/v4ex/sidebar/? … but it seems there […]
firewall & pinguin: iptables where do thou go? it is said that when using “ip-sets” iptables and nftables achieve almost same performance (amounts of ips possible to block, without server becoming slow/unresponsive) Redhat and nftables on DDoS “so the only […]
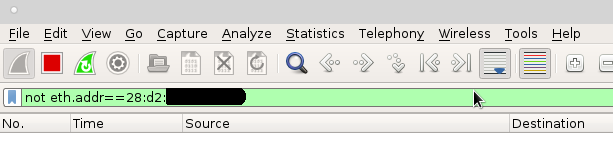
sometimes you just want to listen to incoming traffic… not the noise that your machine generates: # checkout what mac your NIC has ip addr show; ifconfig -a; # filter it in wireshark not eth.addr==28:d2:XX:XX:XX:XX it’s not just a tool…. […]
CentOS8: ccze author not willing to maintain ccze. no ccze and not even lnav available. how to monitor all logs… https://dwaves.de/2017/06/15/linux-monitor-all-logs-in-real-time-d-follow-all-show-changes-to-log-files-under-varlog/ as i was wondering what combination of less -R with or without ccze would allow me to view log […]
Linux is pretty hardware independent, so most of the time you can just 1:1 clone/move harddisk to new machine and in 99% of cases it will just boot. make sure – target (new) machine’s harddisk is same or bigger size […]
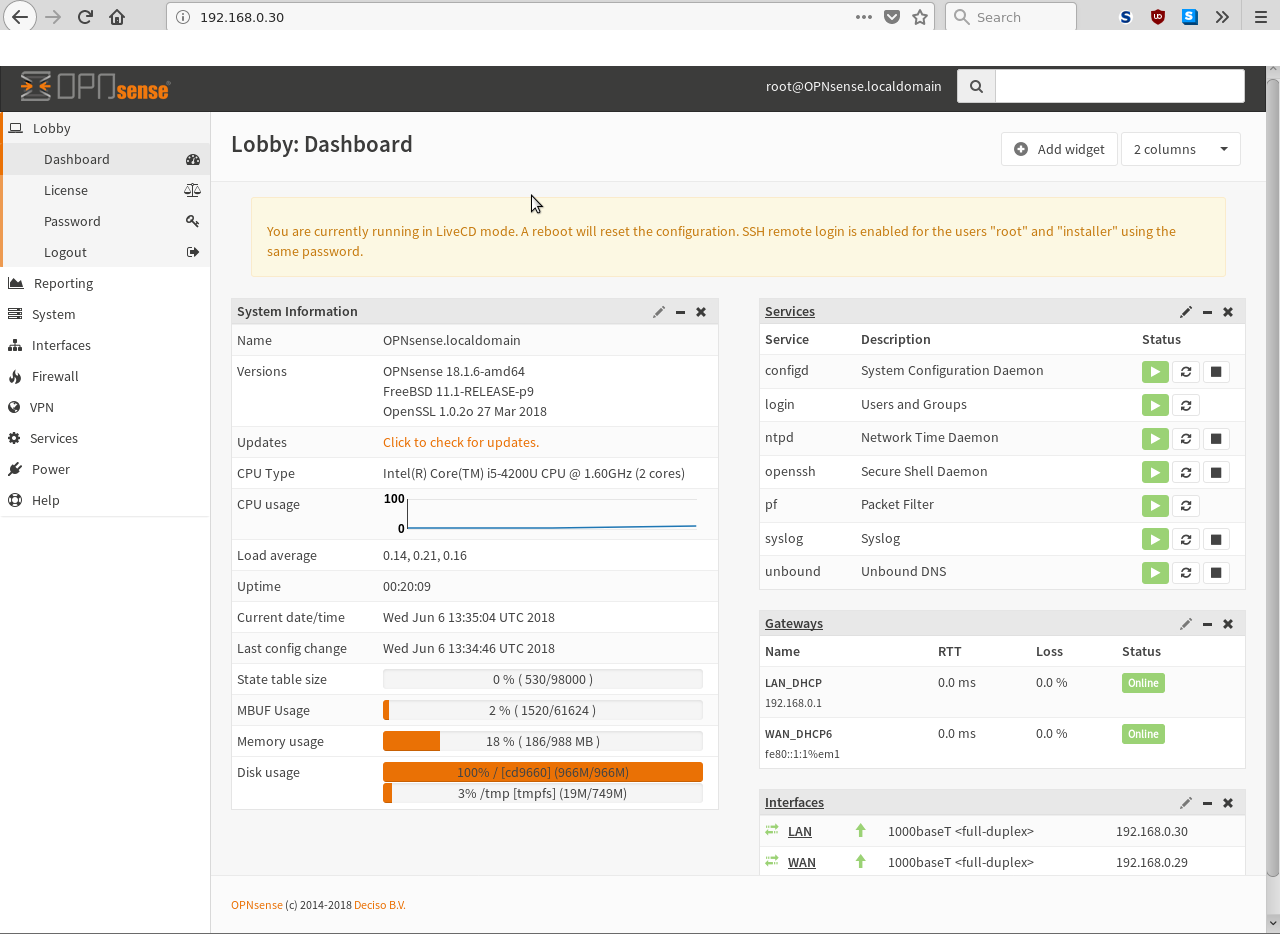
basically the advanced version of PiHole. WARNING! THIS IS not a complete OPNSense / PFSense tutorial it is rather just to get started. right now, one is (still) using iptables without any gui. there seems to be a lot of […]
monitor (andoird) devices with bpf: https://www.socallinuxexpo.org/sites/default/files/presentations/bcc-scale.pdf so guess “monitoring” is about two things: availability and performance: detect performance bottlenecks get informed if parts (harddisks) / servers have failed / are about to fail security: detect, report and (if possible) automatically […]
sad update: Peter Eckersley of Let’s Encrypt is Dead may his soul find rest in the open source nirvana from earthly troubles… may the pain of his family and friends be overcome may let’s encrypt live on! Why: Do MAJOR […]
What devices lurk in the user’s network? What computers are online what offline? quick arp scan with netdiscover (manpage: netdiscover.man.txt scanning with nmap What services/ports in what versions are online/open? over poorly or not so poorly documented LANs the user-admin […]