https://youtu.be/Z9z66ksWtlg
one week downtime – they got backups and are not planing on paying the ransome.
“Norwegian oil and gas and metallurgical Corporation Norsk Hydro was hit by the encoder LockerGoga — to stop the spread of malware, IT-specialists had to isolate the enterprise and transfer several of them to manual control.
- The attack occurred on the night of Tuesday 19 March and hit information systems at several production sites.
- At a press conference related to the incident, representatives of the Corporation reported that they had to stop several plants that provide metal extrusion.
Norsk Hydro CFO Eivind Kallevik (Eivind Kallevik) assessed the situation as “quite serious”.
“The attack brought down our networks around the world, which affected both production and office processes,” said the top Manager.
At the moment we are trying to resume work, reduce financial and operational damage.
To date, the incidents have not resulted in accidents [at work].”
Kallevik said that experts have stopped the spread of malware in the company’s systems.
As can be seen in the network ads published by Norsk Hydro security services, employees were asked not to turn on computers and not to join the corporate network.
According to Kallevik, the Corporation does not plan to pay the ransom and hopes to restore the affected data from backups.
The company did not specify which SOFTWARE caused the problems.
According to experts of the center NorCERT, the criminals used a relatively new encoder LockerGoga.
In January, the malware attacked the French firm Altran Technologies, which is engaged in consulting in the field of engineering.
As explained by the IB-experts, criminals install LockerGoga through a compromised account with administrator rights and place the malicious distribution in the Netlogon folder, to which all computers on the corporate network have access.
The attackers then configure group policy so that all computers and servers run the file with maximum privileges.
This mechanics allows LockerGoga to quickly spread over the network without self-replication.
In addition, by using Active Directory, attackers bypass corporate firewalls.
At the end of last year, Kaspersky Lab analysts included attacks on the industry in the list of key threats.
The reason for this is the low security of production processes in this segment.
Experts stressed that the purpose of the attackers can be not only profit, but also to put pressure on the company or the country, if the enterprise is among the critical ones.
Source: https://threatpost.ru/lockergaga-ransomware-hits-hydro-norsk/31927/
auto translated from src: https://exploit.in/2019/12293/
Vector? Probably links in Social Engineering Spam Mails
E-Mail Box could bring out the Ransomware
Scam email campaigns are the most preferred method that developers use especially with Ransomware programs. In such a fraud campaign, thousands of Spam e-Mails are designed and sent on the Internet, trying to convince recipients that these e-Mails come from real sources (because malicious actors use names like DHL, Amazon, PayPal).
These E-Mails contain a malicious Link that contains “important” files to Download.
These attachments can from MS Office Word documents, executable files (fake flashplayer / antivirus update), archives, etc., which contain a payload of a Ransomware.
Running such files causes the infection to be installed in the System without the user’s consent. You should therefore avoid clicking on the Spam e-Mails, in particular on the areas that contain Links / ads / offers.
You use official Websites and direct Links if you need Software / files / Apps in your System.
src: malware-board.com
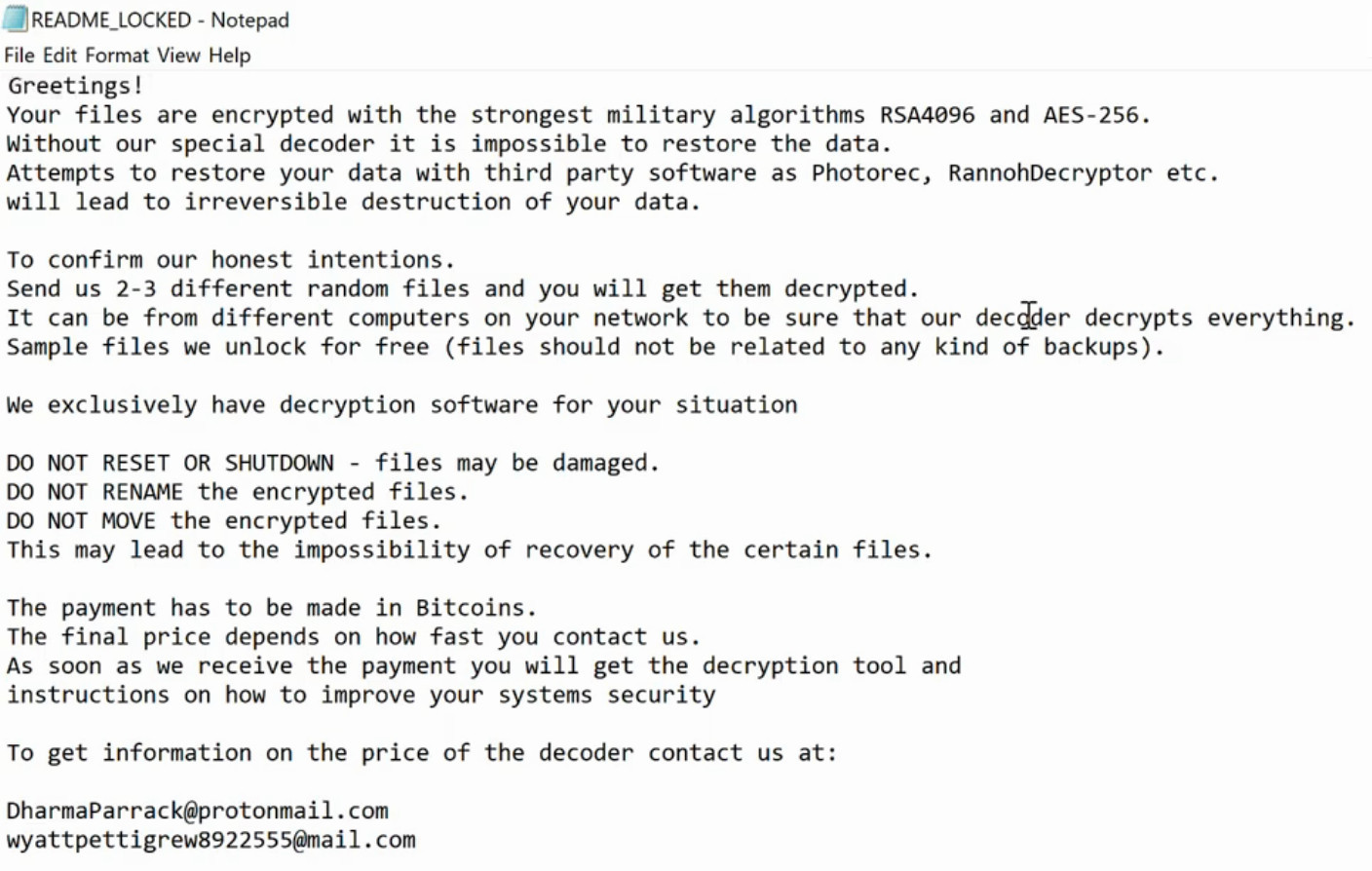
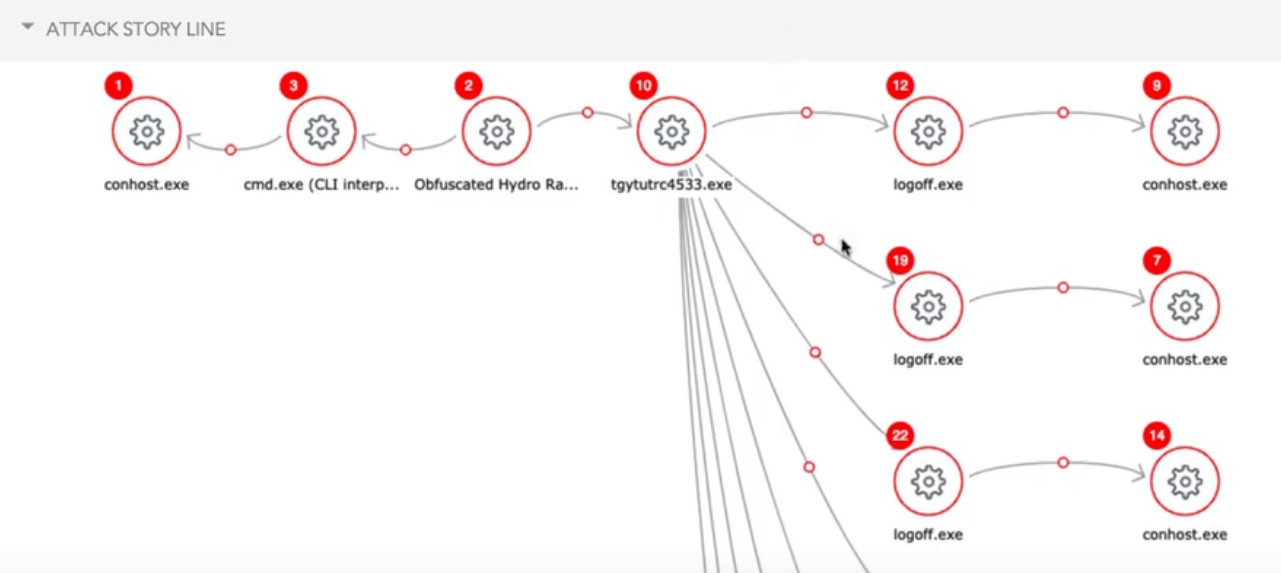
Screenshots:
Safeguarding the way we live and work
https://youtu.be/p8sWOOsTFDE
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!