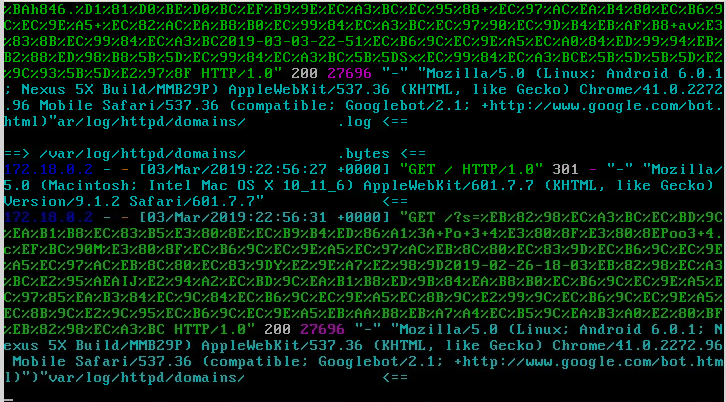
lately this blog gets bombarded with queries like these:
which decoded are Korean SPAM?
which translates as:
iptables / firewalld seem not to work and have to really really figure out why.
until then this is a little workaround, it limits the ?search=pattern query to authenticated users and should save some traffic and resources, after all this is going on for days and i suspect these hosts of malfunction:
host 66.249.64.24 24.64.249.66.in-addr.arpa domain name pointer crawl-66-249-64-24.googlebot.com.
host 66.249.64.26 26.64.249.66.in-addr.arpa domain name pointer crawl-66-249-64-26.googlebot.com.
are DDoSing this blog with Korean search patterns!?
the whole .htaccess looks like this:
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
# RewriteRule 404 index.php?s=$1 [L,QSA]
</IfModule>
# END WordPress
<FilesMatch "wp-login.php">
AuthName "WordPress Admin"
AuthType Basic
AuthUserFile /home/admin/web/.htpasswd
require valid-user
</FilesMatch>
<If "%{QUERY_STRING} =~ /^.?s=/">
AuthName "WordPress Admin"
AuthType Basic
AuthUserFile /home/admin/web/.htpasswd
require valid-user
</If>
<If "%{QUERY_STRING} =~ /^.?search=/">
AuthName "WordPress Admin"
AuthType Basic
AuthUserFile /home/admin/web/.htpasswd
require valid-user
</If>
result:
apache now answers those requests with “401 Unauthorized”
Links:
https://httpd.apache.org/docs/2.4/expr.html
https://serverfault.com/questions/956570/htaccess-to-disable-wordpress-search-domain-s-test/956579
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!