who is who? concepts:
docker is written in Google Go by Docker Inc, SanFrancisco 
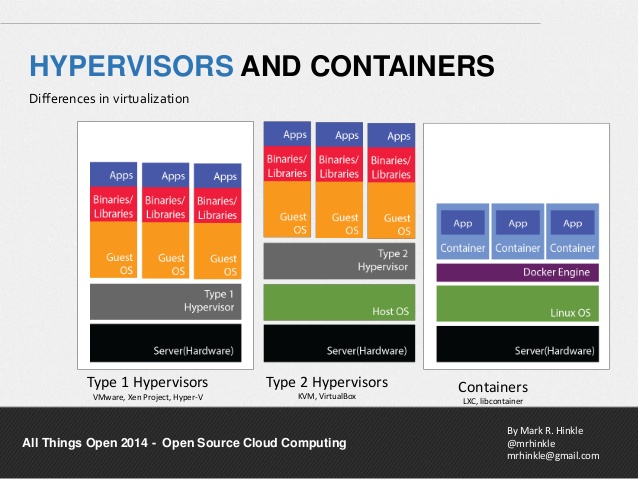
because it does not emulate any hardware – it is a linux container / sandbox or jail like Free BSD Jail or Solaris Zones or OpenVZ so containers are not a brand new concept.
But they get more attention as datacenter admins want to increase density of hardware-usage. (so no CPU core or RAM chip get’s bored, more users per machine etc.)
So in this way containers are usually used inside virtual machines so one real hardware server is running many VMs which run many containers.
Limitations of docker: docker on a linux host can only run linux instances (various distributions though) – docker on a windows host can only run windows instances.
So you can run debian as container on a centos/redhat/fedora host – but not windows as a container on a linux host.
For example if a Apache webserver inside a jail gets compromised – it can not escape the sandbox and hack the host.
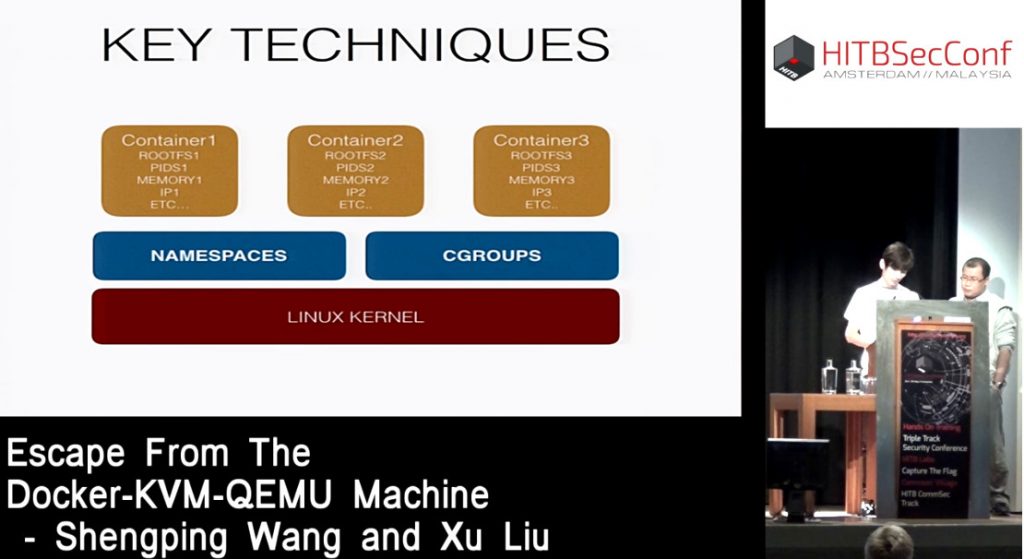
Containers share the same kernel and isolate applications from the rest of the system. (RedHat)
Sandbox concepts need to be implementation in the kernel.
It is a pretty complex concept that comes with a lot of commands – which can be overwhelming / daunting without good documentation: examples, tutorials (youtube?), howtos, usecase “when to use what” and cheat sheet.
What especially confuses me is the “run” vs “start” concept.
run will create a new container and start it.
start only starts existing containers.
takes a while to register.
after all – simplicity is a virtue.
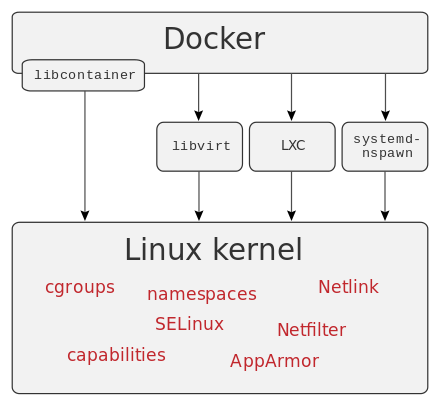
Docker can use different interfaces to access virtualization features of the Linux kernel.[13]
The Linux kernel’s support for namespaces mostly[10] isolates an application’s view of the operating environment, including process trees, network, user IDs and mounted file systems, while the kernel’s cgroups provide resource limiting, including the CPU, memory, block I/O, and network.
Since version 0.9, Docker includes the libcontainer library as its own way to directly use virtualization facilities provided by the Linux kernel, in addition to using abstracted virtualization interfaces via libvirt, LXC (Linux Containers) and systemd-nspawn.[11][12][13]
advantages:
- portability – developer can ship exactly “his/her” version including environment.
- “With Docker, developers can build any app in any language using any toolchain. “Dockerized” apps are completely portable and can run anywhere – colleagues’ OS X and Windows laptops, QA servers running Ubuntu in the cloud, and production data center VMs running Red Hat. (src)
- repositories – up and download ready to run appliances.
- versioning – save and restore – compute with confidence.
- security – it should (no grantees) not be possible for an application inside an container to take over control of the host.
all processes that run inside a docker container get two process-IDs: one inside the container, and one on bare-metal os.
changes at config files are saved in separate files with an automatically generated version-number attached to them.
so all processes seem to run directly on the hardware – which makes it (of course) fast –
problems:
- containers harddisk space once used – does not shrink!? (unless you export/import)
- i would understand this if all files were in ONE FILE but they are NOT, i really do NOT understand, that when you copy a large file into your container and delete it from the container… the harddisk space is still in USE!
- exporting containers takes 3x times the harddisk space it needs for a container
- so if you have a container that uses 50GBytes of harddisk space and your harddisk is only 100GBytes you are screwed! you can not migrate your docker container to a bigger harddisk by commit and save.
- fail2ban / iptables does not work!?
-
- not in the container and not on the host!?
- the problem here is nftables, the maybe soon replacement for iptables, docher expects iptables, nftables only provides “basic” backward compatibility with iptables commands, solution: uninstall nftables, install iptables, before installing docker
- “docker network security and routing: By default, docker creates a virtual ethernet card for each container.
- Each container has its own routing tables and iptables.
- When specific ports are forwarded, docker creates certain host iptables rules.
- The docker daemon itself does some of the proxying.
- If you map applications to containers, you provide flexibility to yourself by limiting network access on a per-application basis.
- Because containers have their own routing tables, they can be used to limit incoming and outgoing traffic: use the ip route command in the same way you would use it on a host. ” (src: RedHat)
/usr/sbin/iptables -w2 -t nat -C DOCKER -p tcp -d 0/0 --dport 443 -j DNAT --to-destination 172.18.0.4:443 ! -i br-6ce196858fd2' failed: iptables: No chain/target/match by that name. /usr/sbin/iptables -w2 -t filter -C DOCKER ! -i br-6ce196858fd2 -o br-6ce196858fd2 -p tcp -d 172.18.0.4 --dport 443 -j ACCEPT' failed: iptables: Bad rule (does a matching rule exist in that chain?). /usr/sbin/iptables -w2 -t nat -C POSTROUTING -p tcp -s 172.18.0.4 -d 172.18.0.4 --dport 443 -j MASQUERADE' failed: iptables: No chain/target/match by that name. /usr/sbin/iptables -w2 -t nat -C DOCKER -p tcp -d 0/0 --dport 80 -j DNAT --to-destination 172.18.0.4:80 ! -i br-6ce196858fd2' failed: iptables: No chain/target/match by that name. /usr/sbin/iptables -w2 -t filter -C DOCKER ! -i br-6ce196858fd2 -o br-6ce196858fd2 -p tcp -d 172.18.0.4 --dport 80 -j ACCEPT' failed: iptables: Bad rule (does a matching rule exist in that chain?). /usr/sbin/iptables -w2 -t nat -C POSTROUTING -p tcp -s 172.18.0.4 -d 172.18.0.4 --dport 80 -j MASQUERADE' failed: iptables: No chain/target/match by that name. Aug 13 13:39:17 username containerd: time="2019-08-13T13:39:17.854035652-04:00" level=info msg="shim containerd-shim started" address="/containerd-shim/moby/6504c13edb18274caa289df84cb422d290bde171cc9f6a910c12794f9d750e28/shim.sock" debug=false pid=14019 ==> /var/log/firewalld <== 2019-08-13 13:39:17 WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t nat -C DOCKER -p tcp -d 0/0 --dport 443 -j DNAT --to-destination 172.18.0.4:443 ! -i br-6ce196858fd2' failed: iptables: No chain/target/match by that name. 2019-08-13 13:39:17 WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t filter -C DOCKER ! -i br-6ce196858fd2 -o br-6ce196858fd2 -p tcp -d 172.18.0.4 --dport 443 -j ACCEPT' failed: iptables: Bad rule (does a matching rule exist in that chain?). 2019-08-13 13:39:17 WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t nat -C POSTROUTING -p tcp -s 172.18.0.4 -d 172.18.0.4 --dport 443 -j MASQUERADE' failed: iptables: No chain/target/match by that name. 2019-08-13 13:39:17 WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t nat -C DOCKER -p tcp -d 0/0 --dport 80 -j DNAT --to-destination 172.18.0.4:80 ! -i br-6ce196858fd2' failed: iptables: No chain/target/match by that name. 2019-08-13 13:39:17 WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t filter -C DOCKER ! -i br-6ce196858fd2 -o br-6ce196858fd2 -p tcp -d 172.18.0.4 --dport 80 -j ACCEPT' failed: iptables: Bad rule (does a matching rule exist in that chain?). 2019-08-13 13:39:17 WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w2 -t nat -C POSTROUTING -p tcp -s 172.18.0.4 -d 172.18.0.4 --dport 80 -j MASQUERADE' failed: iptables: No chain/target/match by that name.
-
- more strange problems: “can’t remove directory” under certain conditions
it seems the docker-complexity is going south!
the concept is great – similar to OpenVZ increasing server density even more – (hardware -> virtualization -> container) but i am seriously thinking about not using it again for exactly those issues.
security?
security wise seems this concept been tested for a while.
but as you might now – hackers even managed to break out of VMWare VMs in the past! (VM escape)
Virtual machine escape fetches $105,000 at Pwn2Own hacking contest [updated]
Hack worked by stitching together three separate exploits.
“We used a JavaScript engine bug within Microsoft Edge to achieve the code execution inside the Edge sandbox, and we used a Windows 10 kernel bug to escape from it and fully compromise the guest machine,” Qihoo 360 Executive Director Zheng Zheng wrote in an e-mail. “Then we exploited a hardware simulation bug within VMware to escape from the guest operating system to the host one. All started from and only by a controlled a WEBSITE.”
Chinese Hackers escape Docker-KVM-Quemu in 2016!(src)
Holy moly. And you really want a cashless society with those massive security holes in your software? Call me paranoid but I am not so sure about that – a lot of people are paying cashless in China (just with their cellphones).
back to topic: but than again: it is great that you can run Docker inside a VM.
let’s get started
i assume you have a running CentOS7 VM 64Bit inside some virtualization technology or directly on hardware.
hostnamectl; # tested on
Static hostname: docker_on_centos.localdomain
Virtualization: kvm
Operating System: CentOS Linux 7 (Core)
Kernel: Linux 3.10.0-693.11.1.el7.x86_64
Architecture: x86-64
preparations:
nmtui; # tool that allows you to change your ip to fixed # per default CentOS is not activating network card yum -y install epel-release; yum -y update; yum install NetworkManager-tui; # install nmtui ping yahoo.com; # test that your vm has access to the internet ip addr show; # you might want to know the IP of your VM and ssh into it yum update && yum upgrade; # upgrade system to latest yum install htop; # nice tool to check your ram and cpu usage yum install docker; # install docker service docker start; # start docker service docker ps; # lists all currently running docker containers docker ps -a; # lists all installed docker containers # search for all ubuntu related templates images docker search ubuntu INDEX NAME DESCRIPTION STARS OFFICIAL AUTOMATED docker.io docker.io/ubuntu Ubuntu is a Debian-based Linux operating s... 8133 [OK] docker.io docker.io/dorowu/ubuntu-desktop-lxde-vnc Ubuntu with openssh-server and NoVNC 204 [OK] docker.io docker.io/rastasheep/ubuntu-sshd Dockerized SSH service, built on top of of... 164 [OK] docker.io docker.io/ansible/ubuntu14.04-ansible Ubuntu 14.04 LTS with ansible 94 [OK] docker.io docker.io/ubuntu-upstart Upstart is an event-based replacement for ... 87 [OK] docker.io docker.io/neurodebian NeuroDebian provides neuroscience research... 51 [OK] docker.io docker.io/1and1internet/ubuntu-16-nginx-php-phpmyadmin-mysql-5 ubuntu-16-nginx-php-phpmyadmin-mysql-5 43 [OK] docker.io docker.io/ubuntu-debootstrap debootstrap --variant=minbase --components... 39 [OK] docker.io docker.io/nuagebec/ubuntu Simple always updated Ubuntu docker images... 23 [OK] docker.io docker.io/tutum/ubuntu Simple Ubuntu docker images with SSH access 18 docker.io docker.io/i386/ubuntu Ubuntu is a Debian-based Linux operating s... 13 docker.io docker.io/1and1internet/ubuntu-16-apache-php-7.0 ubuntu-16-apache-php-7.0 12 [OK] docker.io docker.io/ppc64le/ubuntu Ubuntu is a Debian-based Linux operating s... 12 docker.io docker.io/1and1internet/ubuntu-16-nginx-php-phpmyadmin-mariadb-10 ubuntu-16-nginx-php-phpmyadmin-mariadb-10 8 [OK] docker.io docker.io/eclipse/ubuntu_jdk8 Ubuntu, JDK8, Maven 3, git, curl, nmap, mc... 6 [OK] docker.io docker.io/codenvy/ubuntu_jdk8 Ubuntu, JDK8, Maven 3, git, curl, nmap, mc... 4 [OK] docker.io docker.io/darksheer/ubuntu Base Ubuntu Image -- Updated hourly 4 [OK] docker.io docker.io/1and1internet/ubuntu-16-nginx-php-5.6-wordpress-4 ubuntu-16-nginx-php-5.6-wordpress-4 3 [OK] docker.io docker.io/1and1internet/ubuntu-16-sshd ubuntu-16-sshd 1 [OK] docker.io docker.io/pivotaldata/ubuntu A quick freshening-up of the base Ubuntu d... 1 docker.io docker.io/1and1internet/ubuntu-16-healthcheck ubuntu-16-healthcheck 0 [OK] docker.io docker.io/1and1internet/ubuntu-16-rspec ubuntu-16-rspec 0 [OK] docker.io docker.io/ossobv/ubuntu Custom ubuntu image from scratch (based on... 0 docker.io docker.io/pivotaldata/ubuntu-gpdb-dev Ubuntu images for GPDB development 0 docker.io docker.io/smartentry/ubuntu ubuntu with smartentry 0 [OK] docker run ubuntu:14.04 /bin/echo 'Hello World'; # install and run this docker container docker run -it centos:centos7 /bin/bash; # download and install centos7 image (200MByte) and run /bin/bash in that instance Unable to find image 'centos:centos7' locally Trying to pull repository docker.io/library/centos ... centos7: Pulling from docker.io/library/centos af4b0a2388c6: Downloading [=================================> ] 49.74 MB/73.67 MB # what is pretty impressive here that with a 74MByte download you get a full running version of centos7? yum install epel-release yum install htop htop# like nuthin running in that instance [root@d2ff6ccb98e6 /]# pwd / exit; # exit the instance/container, this will stop the instance/container and free resources docker pull busybox; # install busybox image (1.5MBytes) docker run busybox /bin/echo "Hello World" Hello World docker run alexeiled/docker-oracle-xe-11g; # installs Oracle Express Edition 11g Release 2 and Ubuntu 14.04 LTS (Trusty) (over 1GB) docker images; # show sizes of downloaded images REPOSITORY TAG IMAGE ID CREATED SIZE docker.io/busybox latest 5b0d59026729 7 days ago 1.146 MB docker.io/centos centos7 ff426288ea90 3 weeks ago 207.2 MB docker.io/alexeiled/docker-oracle-xe-11g latest f7304758169d 21 months ago 2.39 GB docker ps -a; # show all created containers (running and not running) CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 5a512c285f4f centos:centos7 "/bin/sleep 3" About a minute ago Exited (0) About a minute ago admiring_bhabha 5931eda908b4 centos:centos7 "/bin/sleep 3" 3 minutes ago Exited (0) 2 minutes ago kickass_galileo 26224f0a6971 busybox "/bin/echo 'Hello Wor" 4 minutes ago Exited (0) 4 minutes ago furious_raman 848eb2b20ec4 centos:centos7 "/bin/bash" 8 minutes ago Exited (127) 6 minutes ago sleepy_curie d2ff6ccb98e6 centos:centos7 "/bin/bash" 13 minutes ago Exited (0) 9 minutes ago evil_khorana docker run -it centos:centos7 /bin/bash; # will create a new container centos:centos7 image # and run /bin/bash interactively in it # when you exit the container, the container will stop running docker run -d centos:centos7 /bin/sleep 3; # will create a new container centos:centos7 image # will run /bin/sleep 3 in it in detached mode (no interaction possible) # when finished the container stops running docker start 848eb2b20ec4; # start this container docker pause 848eb2b20ec4; # pause this container docker unpause 848eb2b20ec4; # resume this container docker stop 848eb2b20ec4; # stop this container docker stop $(docker ps -a -q); # stop ALL containers docker attach 848eb2b20ec4; # connect-attach shell/STDIN/STDOUT to currently running process of container # problem:
docker attach will let you connect to your Docker container, but this isn’t really the same thing as ssh. If your container is running a webserver, for example, docker attach will probably connect you to the stdout of the web server process. It won’t necessarily give you a shell.
The docker exec command is probably what you are looking for; this will let you run arbitrary commands inside an existing container. For example:
docker exec -it sh docker exec -it bash # "login" interactively without disturbing running autostarted process docker exec -it 848eb2b20ec4 sh # snapshot/save container/create a new image from this container docker commit 848eb2b20ec4 centos-with-htop; # Create a new image from a container’s changes # Usage: # docker commit [OPTIONS] CONTAINER [REPOSITORY[:TAG]] # docker commit container_instance_name image_name:v2 # show all available images docker images REPOSITORY TAG IMAGE ID CREATED SIZE centos-with-htop latest c5bf4ece7f83 32 seconds ago 389.5 MB docker.io/ubuntu trusty dc4491992653 6 days ago 221.9 MB docker.io/busybox latest 5b0d59026729 8 days ago 1.146 MB docker.io/centos centos7 ff426288ea90 3 weeks ago 207.2 MB docker.io/alexeiled/docker-oracle-xe-11g latest f7304758169d 21 months ago 2.39 GB # if you want to export/move to another computer you can: docker save centos-with-htop | gzip -vc > /backups/centos-with-htop.tar.gz; # export this image to file ll -rw-r--r--. 1 root root 133M Feb 1 08:31 centos-with-htop.tar.gz docker rmi centos-with-htop; # remove docker image Untagged: centos-with-htop:latest Deleted: sha256:c5bf4ece7f831a3271fc324d7af80866e796181e5601956d0d597d26710bcf44 Deleted: sha256:141f9a93dbcf9cd5736f30454a544fabe547c02dc4863e1c1a94e89fe3e79f8d cat centos-with-htop.tar.gz | docker load; # import image to docker 3af37c724bd3: Loading layer [==================================================>] 184.5 MB/184.5 MB Loaded image: centos-with-htop:latest docker images|grep centos-with-htop centos-with-htop latest c5bf4ece7f83 13 minutes ago 389.5 MB docker logs -f 848eb2b20ec4; # show console output without login of this container docker rename CONTAINER NEW_NAME; # rename docker container
cheat sheed
docker stop $(docker ps -q); # stop all running containers docker exec -it container bash; # logon / login to container # to exit from a container exit; # but also stops the container # hotkey / shortcut logout :hit keys Ctrl + p + Ctrl + q # to exit container and keep it running # add a new port to an existing container docker stop container docker commit container container2 # create new network docker network create example-net # will start a copy of container2 # with port 80 and 443 open # with a fixed ip of 172.18.0.5 # become a member of virtual network example-net docker run -it --name=container2-instance -p 80:80 -p 443:443 --net=example-net --ip 172.18.0.5 container2
start options for run
-d
start container detached, run in background
-it
start container in interactive mode
--attach = [STDIN,STDERR,STDOUT]
redirect StandardIn, StandardError and StandardOut
--rm
remove container after exit (self destruct?)
--name = ContainerName
container is given a name automatically unless specified with –name
--restart = no / on-failure:10 / always
if something crashes, docker will restart the container 10 times
--cpuset="0,1"
how many cpus are available to that instance (in this case cpu0 and cpu1 are made available)
--cpu-shares=512
100% cpu usage 0 or 1024, 512 = 50% cpu usage
-m 256m
limit usage of RAM to 256MBytes
--privileged
allow container access to host machine (reboot host)
--cap-add
add a privilege to container
--cap-drop
remove a privilege to container
-P 8080
all ports used by the container are automatically also opened on the host
-p 80:8080
redirect host port 80 to container port 8080
will show like this:
docker ps a 0.0.0.0:80->8080/tcp
--net=bridge / container:id / host / none
bridge
allow network access of container via bridge
host
pass all ports through from host to container
--link=name:alias --expose=PORT
non root user usage
in order to allow non-root users to use docker add them to the group “docker”
# create group docker groupadd docker # add user username to group docker usermod -aG docker username
re-login to activate changes. non-root user username should be able to run:
docker run hello-world
autostart on boot
to enable docker service to be available on boot:
systemctl enable docker service docker status; # check docker service status Redirecting to /bin/systemctl status docker.service ● docker.service - Docker Application Container Engine Loaded: loaded (/usr/lib/systemd/system/docker.service; enabled; vendor preset: disabled) Active: active (running) since Wed 2018-01-31 17:18:26 EST; 45s ago Docs: http://docs.docker.com Main PID: 948 (dockerd-current) CGroup: /system.slice/docker.service ├─948 /usr/bin/dockerd-current --add-runtime docker-runc=/usr/libe... └─974 /usr/bin/docker-containerd-current -l unix:///var/run/docker... Jan 31 17:18:25 localhost.localdomain dockerd-current[948]: time="2018-01-31T... ... Jan 31 17:18:26 localhost.localdomain systemd[1]: Started Docker Application ... Hint: Some lines were ellipsized, use -l to show in full.
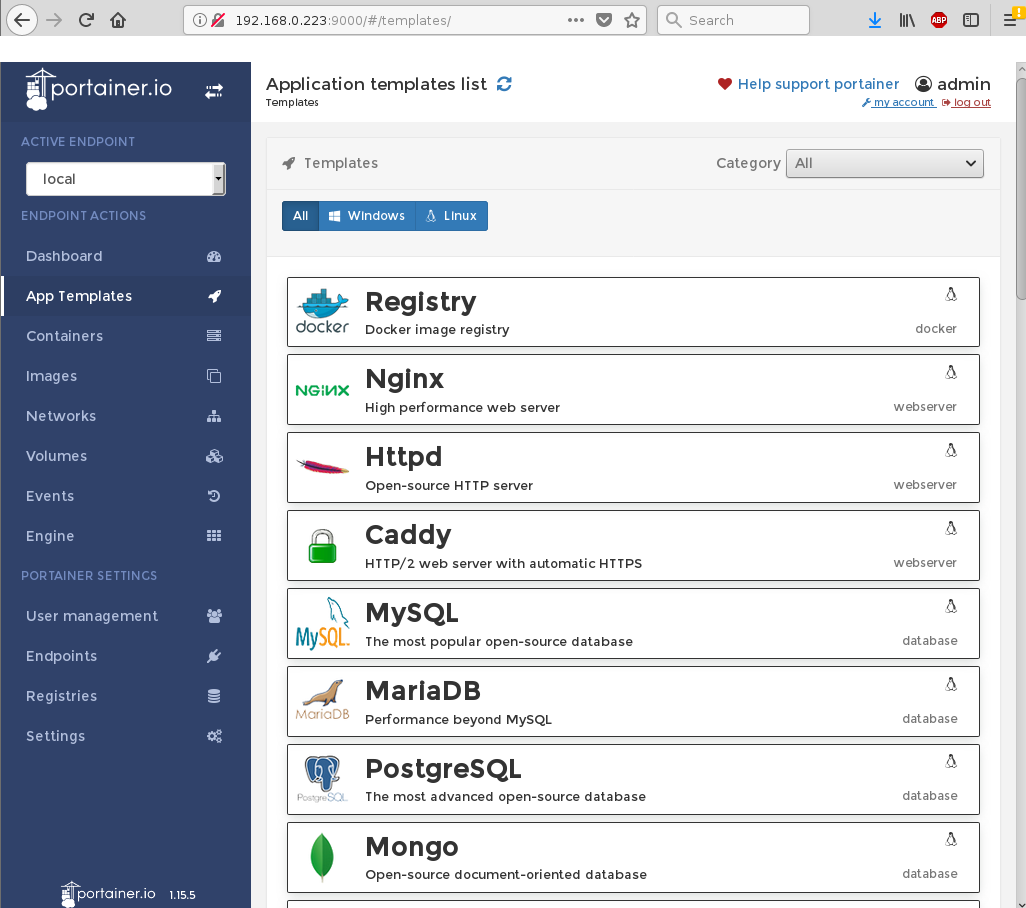
Are there any GUIs? docker web interface portainer.io
is probably accessing https://hub.docker.com/explore/
this is the repository where all the basic images come from (push/pull like git).
if you want to create your own repository you create a registry for local images.
service docker start; # start docker service, make sure docker volume create --name portainer_data; docker run -d --privileged -p 9000:9000 -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer
boot2docker:
you could think of boot2docker as EXSi for docker – the most minimalistic installation possible… using busybox and 50MByte of RAM.
is a tinycore based extremely small distribution bootable livecd that comes with linux kernel 4, guest additions for virtualbox and vmware and docker.
https://github.com/boot2docker/boot2docker/releases <- download iso here
create a new virtual machine inside virtualbox with 64Bit “Other” Linux settings and for example 2xCPUs, 2GB of RAM and 512GByte of harddisk.
how to ssh into boot2docker: https://stackoverflow.com/questions/24286007/how-do-i-ssh-into-the-boot2docker-host-vm-that-the-vagrant-1-6-docker-provider-s
ifconfig; # show dhcp assigned ip address passwd; # as root change root password to e.g. "root" (it will complain but still do it) ssh docker@192.168.0.78; # ssh into the vm usr: docker pwd: tcuser su; # become root docker@192.168.0.78's password: ## . ## ## ## == ## ## ## ## ## === /"""""""""""""""""\___/ === ~~~ {~~ ~~~~ ~~~ ~~~~ ~~~ ~ / ===- ~~~ \______ o __/ \ \ __/ \____\_______/ _ _ ____ _ _ | |__ ___ ___ | |_|___ \ __| | ___ ___| | _____ _ __ | '_ \ / _ \ / _ \| __| __) / _` |/ _ \ / __| |/ / _ \ '__| | |_) | (_) | (_) | |_ / __/ (_| | (_) | (__| < __/ | |_.__/ \___/ \___/ \__|_____\__,_|\___/ \___|_|\_\___|_| Boot2Docker version 17.12.0-ce-rc2, build HEAD : 952219e - Tue Dec 12 22:12:18 UTC 2017 Docker version 17.12.0-ce-rc2, build f9cde63
of course this is a live cd… nothing will be saved or stored until one uses some form of storage/harddisk:
mkfs.ext4 /dev/sda; # format harddisk tune2fs -L boot2docker-data /dev/sda; # label harddisk reboot; # reboot
…and wait for boot2docker to make your harddisk usable… as long as there is this red dot the vm harddisk is signaling “busy”:
the ip might change as well so recheck with ifconfig and ssh back into it. you will have to redo the change-root password passwd thing all over again – because remember – it was just a live cd – nothing was saved. HAHA! but now changes are permanent…. not. you will have to setup this bootlocal.sh file in order to make your root password permanent.
saving root passwords in text files… *ARGH*
echo 'echo "root:root" | chpasswd' > /mnt/sda/var/lib/boot2docker/bootlocal.sh; chmod +x /mnt/sda/var/lib/boot2docker/bootlocal.sh; # give it a testrun chmod +x /mnt/sda/var/lib/boot2docker/bootlocal.sh; # you should see chpasswd: password for 'root' changed root@boot2docker:/home/docker# df -Th Filesystem Type Size Used Available Use% Mounted on tmpfs tmpfs 1.8G 206.1M 1.6G 11% / tmpfs tmpfs 1001.1M 0 1001.1M 0% /dev/shm /dev/sda ext4 503.0G 70.5M 477.3G 0% /mnt/sda cgroup tmpfs 1001.1M 0 1001.1M 0% /sys/fs/cgroup /dev/sda ext4 503.0G 70.5M 477.3G 0% /mnt/sda/var/lib/docker/plugins /dev/sda ext4 503.0G 70.5M 477.3G 0% /mnt/sda/var/lib/docker/overlay2
Links:
https://github.com/wsargent/docker-cheat-sheet
https://docs.docker.com/get-started/
http://www.zdnet.com/article/docker-libcontainer-unifies-linux-container-powers/
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!