with security there is no “done”
it can be clearly seen that:
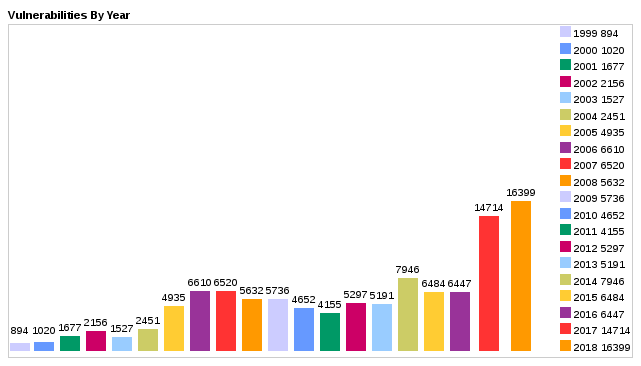
- the amounts of it-security problems is increasing
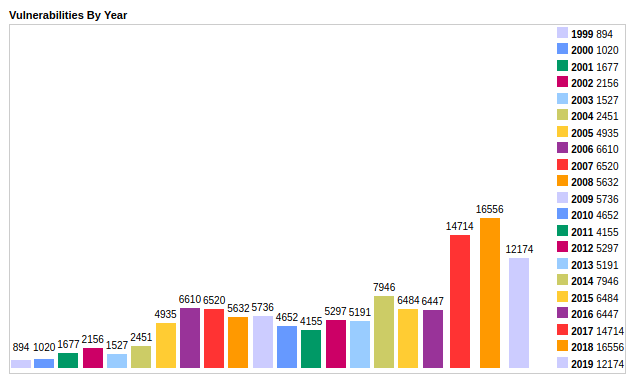
src: https://www.cvedetails.com/browse-by-date.php (data of 2020 is still missing… )
- of course there is no 100% security with state-actors playing “hot” “cold war” in cyberspace
- private-spy-companies developing exploits that then leak to “the public”, where it is then used by hackers to interrupt companies and profiteer via ransomware and cause massive damage (as it happened recently to FireEye)
at the beginning: security was not a problem
- C is still a great language, but unfortunately it was build (just as the mail) in times where it-security was not a problem
- re-writing critical services in security-focused languages like RUST could be a good idea (some things will always stay C).
it-security means: constant iterations over those question:
- is the system/network safe?
- what can be improved?
- what can be improved -> should be improved, no matter the costs, because loss of data & reputation & trust of customers by ransomware attack will always cost the company MORE and endanger even it’s existence & all jobs attached (lawsuits by customers)
- software-minimalism is key: (KISS philosophy)
- does the company really need this and that software installed? (more software = more problems, but yes, to work while listening to good music is important for well being of employees)
- schedule a once-a-week or once-a-month update routine:
- all systems (modems, (vpn/internet) routers, servers, switches) that have direct connection to the internet must be updated on a regular basis
- automatic update servers are very very critical infrastructure (just as nuclear power plants)
- automatic updates are a good idea and work well for systems that follow the UNIX KISS philosophy
- updates for systems that are increasingly complex (bad) it is a better (but more effort) idea of “supervised updates”
- make complete backup of system and data
- update the system
- test according to created test-function-case-document
- are all needed functions still working? (yes -> great, no -> restore and contact software vendor/producer and support)
- do users run unsafe programs/services that can receive messages from outside?
- any program that scripting support (JavaScript and Makros are EVIL) (Office, Browser but also Adobe.PDF?) must be considered unsafe to use inside a company-net
- anything that receives messages is potential vulnerable (mail-server, mail-client, chat-client, ms-teams) must be considered unsafe to use inside a company-net
- all unsafe programs should be placed on physically separate machines which are placed on separate networks with no access to company-net-data or production-machines
- is the backup and restore system sufficient?
- test once a year
- is restore possible? (to different (newer or older) server-hardware?)
- how long does it take to restore? (USB 2.0 WAY TOO SLOW! (here eSATA connections are nice)
- admin should ALWAYS have one complete data backup
- off-site: physically separate place (in fire & emp (double metal casing) vault)
- off-line: not physically connected to PC or internet
- test once a year
- firewalls & routers:
- what ports are internet-reachable on the router/firewall?
- only white-listed clients and (update)servers with fixed IP-Adresses should be able to communicate, anything else needs to be blocked
- maybe even update-servers need to be blocked and only unblocked prior to an update
Humans make mistakes and thus in Open Source just as in Closed Source concepts and software (and even hardware) there can will be bugs and flaws that can be exploited to allow malicious access to systems and data (mostly in order to exploit it for money or bitcoin mining or DDoS attacks on other hosts or sabotage (halt infrastructure, cause dataloss for quiet a significant amount of time (also hospitals can get virus infections… not funny!)).
Example: Microsoft’s File Sharing system “Server Message Block” (SMB), one version of which was also known as “Common Internet File System” (CIFS) had a (we hope not on purpose?) DESIGN-CONCEPT (!) flaw in (SMBv1) of the protocol, which allowed the Ethernal Blue exploit to basically get into any Windows AND (!) LINUX system (samba) that was running it.
Let yourself be educated by security researches on a regular basis – to estimate – what is possible today – and maybe in the future – and do your best to stay safe.
Update your knowledge! Update your software (but before: Power down and backup, or maybe on an identical non-production test-system to see what the update could fix but also break (yes updates do those things))
backup the backup! X-D
stay up-to-date on it-security: with RSS-Feeds
(rss feeds are usually automatically generated by Blogs, just try domain.com/rss (Newsletters/Mailing Lists are okay, imho RSS feeds are superior)
the user can subscribe and manage RSS feeds via Thunderbird! with ease (good Job Mozilla)
English:
https://blog.feedspot.com/information_security_rss_feeds/
https://googleprojectzero.blogspot.com/ (rss)
blog: https://krebsonsecurity.com/
newsletter: https://krebsonsecurity.com/subscribe/
https://onlinedegrees.sandiego.edu/top-cyber-security-blogs-websites/
Russian:
German:
blog: http://www.golem.de/specials/security/
Golem rss feed security: https://rss.golem.de/rss.php?tp=sec&feed=RSS2.0
blog: https://www.heise.de/security/

- Aktuelle News von heise Security via rss
https://www.heise.de/security/rss/news-atom.xml - Aktuelle Security-Warnungen
https://www.heise.de/security/rss/alert-news-atom.xml
newsletter: https://www.heise.de/newsletter/manage/heisec-summary
Events to attend:
https://csrc.nist.gov/Events/2019
https://csrc.nist.gov/Events/2018
Germany:
https://www.it-defense.de/it-defense-2019/programm
https://www.heise-events.de/konferenzen/konferenzen_security
https://hacktoberfest.digitalocean.com/
Very General:
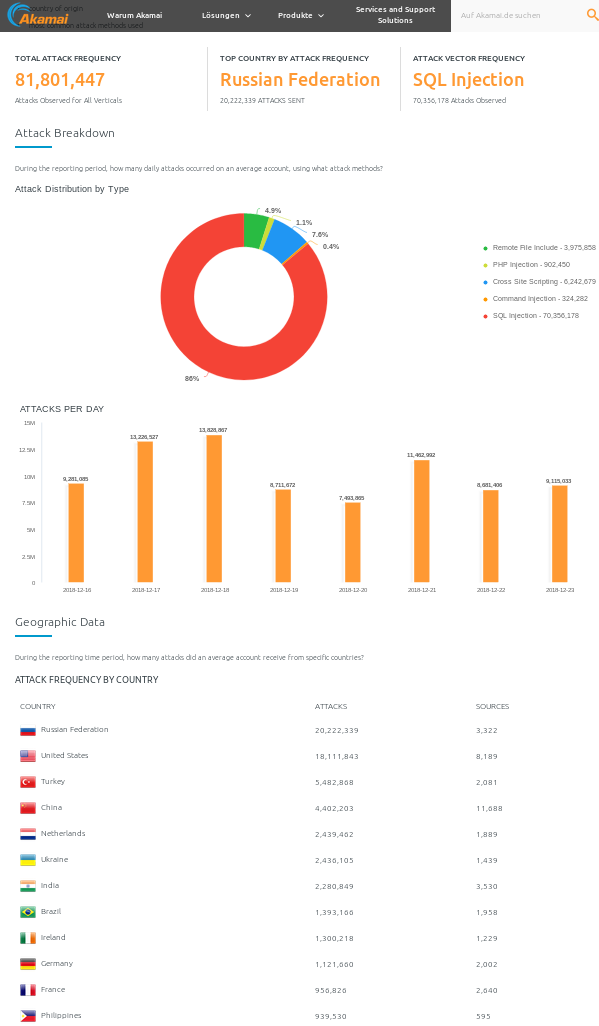
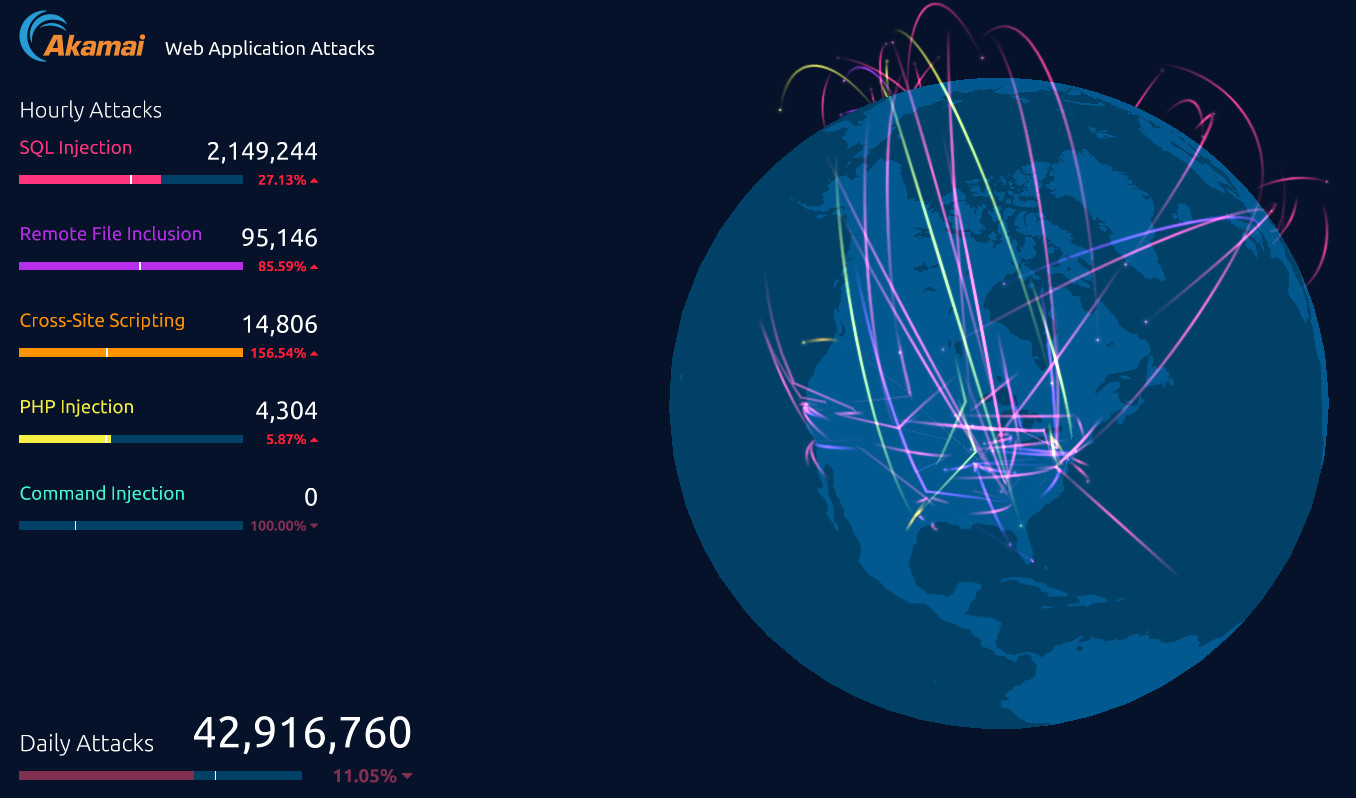
very general: https://www.akamai.com/de/de/about/our-thinking/state-of-the-internet-report/
https://www.bsi.bund.de/EN/Publications/SecuritySituation/SecuritySituation_node.html
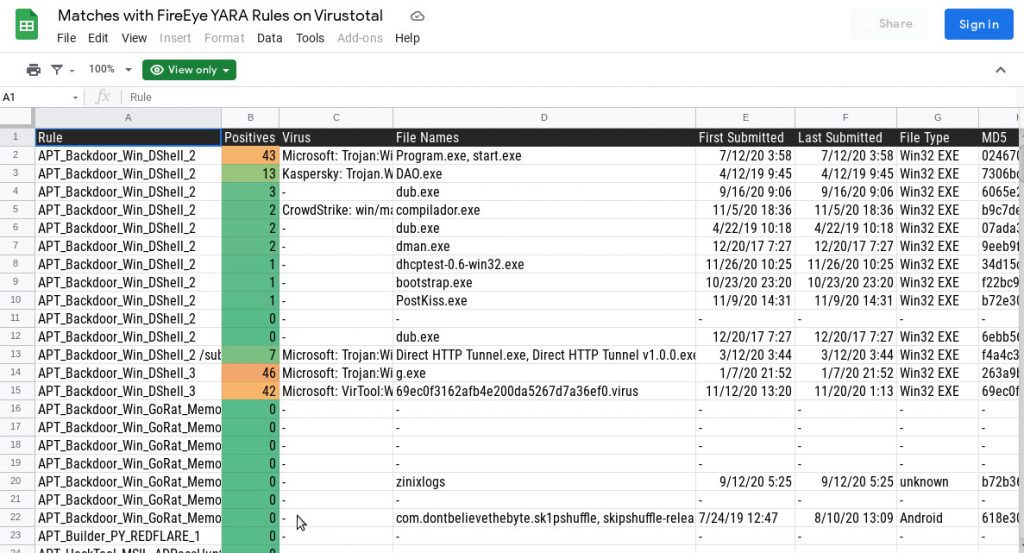
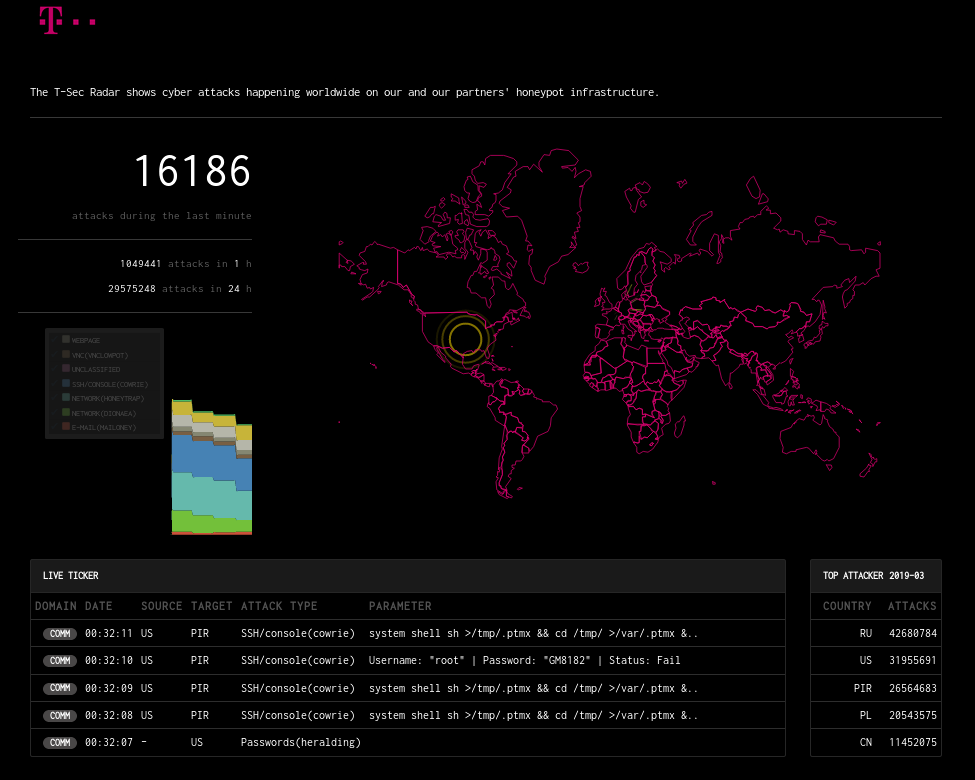
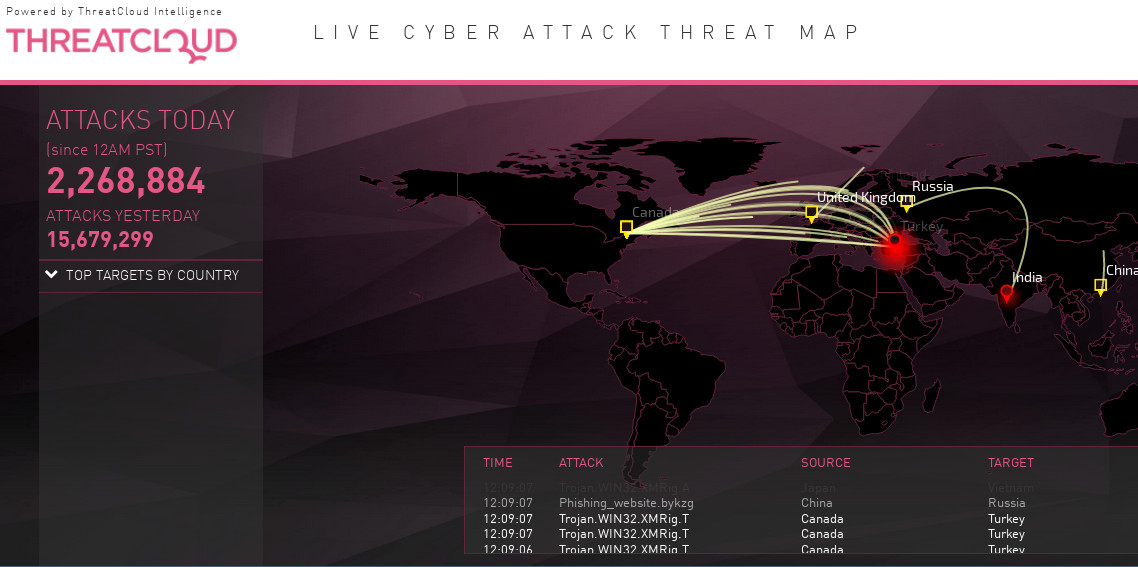
live map:
Databases of IT Vulnerabilities: CVE: Common Vulnerabilities Exposures
https://www.securityfocus.com/
https://kb.cert.org/vuls/bypublished/desc/
by vendor: https://www.cvedetails.com/vendor.php
nice to look at: https://nvd.nist.gov/
search/browse by product: https://nvd.nist.gov/vuln/search/results?form_type=Advanced&results_type=overview&search_type=all&cpe_product=cpe%3A%2F%3A%3Aandroid
https://nvd.nist.gov/ncp/repository
https://seclists.org/fulldisclosure/2018/Dec/
https://dwaves.de/category/hacking/
https://dwaves.de/category/sicherheit-security/
https://dwaves.de/category/cybercrime/
https://dwaves.de/category/cyberwar/
in German: https://www.cert-bund.de/overview/AdvisoryShort
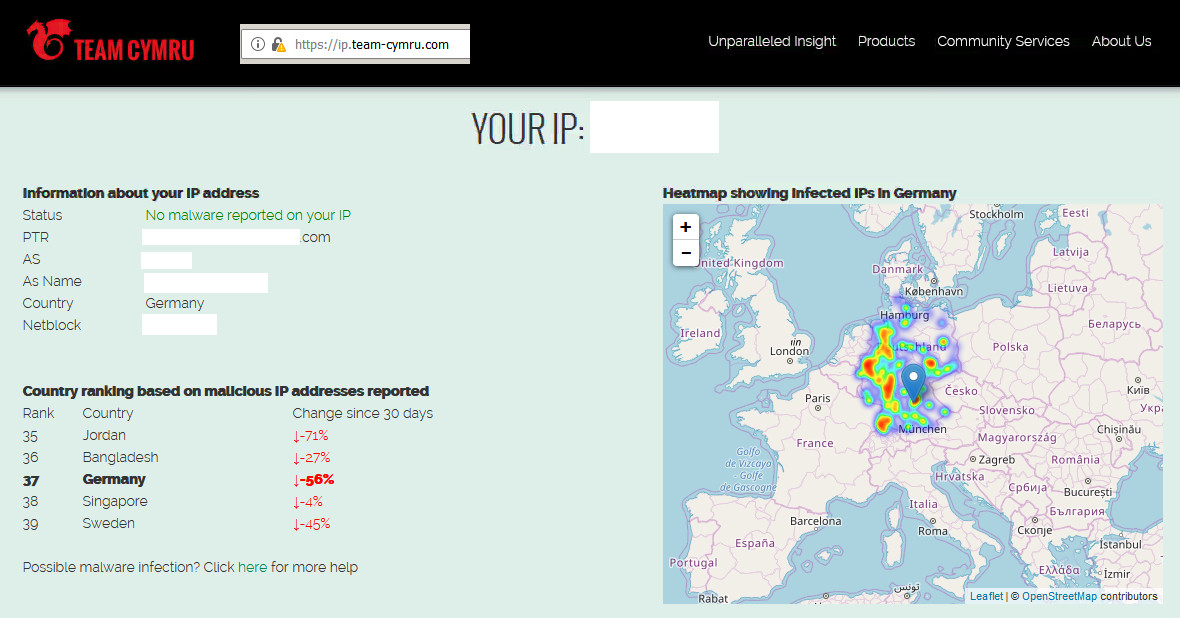
list of ips of malicious hosts:
https://urlhaus.abuse.ch/browse/
reads like:
Tools:
let’s you check if the ip you are browsing with related to any cyber security problems
Linux specific news and updates:
PenTesting Service providers:
so you think you did all you can do? have yourself tested!
https://www.cirosec.de/unternehmen/wir-ueber-uns
what if your SmartPhone gets hacked and dials expensive numbers?
also checkout: “StealthCalls”
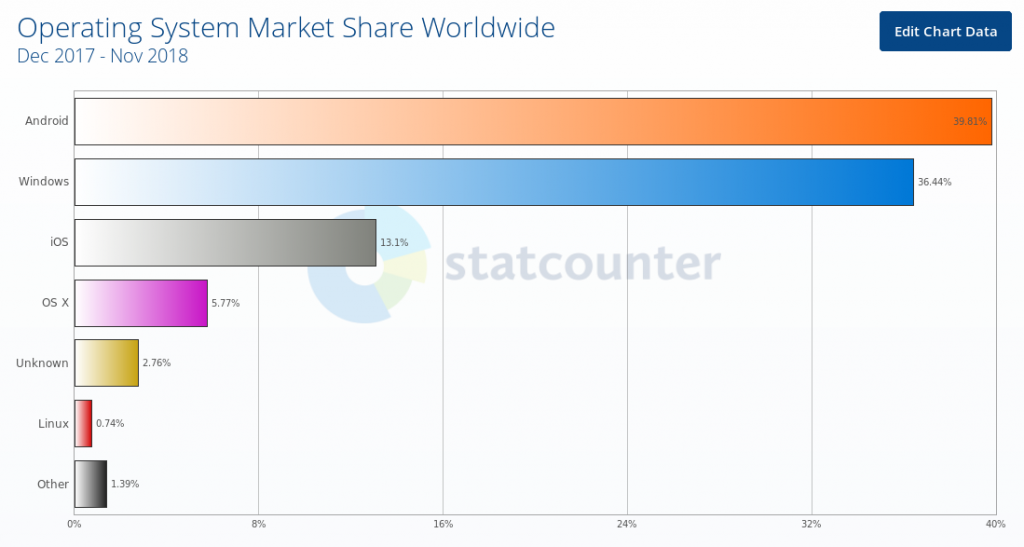
congratulations to Google: The made Android the Number #1 – much to the horror of Microsoft – that tries to counter with increased lobbying. The problem of a market leader: how to stay secure – you have just become a major target that is attractive to be attacked. Android with Linux Kernel… how long will you be save?
heise: “Google fixes critical security holes” – most of them reside in Closed-Source-components of Qualcomm – that’s why there is no further detail.
videos:
https://vimeopro.com/vgtcommunity/vizsec2017
HP FIRMWARE HACK VIA FAX! ? HP YOU MUST BE KIDDING US ALL! https://mirror-1.server.selfnet.de/CCC/congress/2018/h264-hd/35c3-9462-eng-What_The_Fax.mp4
not sure if this is real or scam: https://www.simpliv.com/search/sub-category/cybersecurity
“GREAT” – thanks to all involved!
Qualcomm but also Cisco are all US based manufacturers known to implement backdoors ON PURPOSE probably for gov agencies to spy and collect data on you – the citizen – that they are so afraid of.
“We are also having tough times with GPS: all the GPS chips found in the Android phones we support implement a secret and non-documented protocol that we just cannot figure out.” (src)
it is called: is it a bug or a feature?
deliberate security holes – now also in the Intel Management Engine
src: http://gs.statcounter.com/os-market-share#monthly-201712-201811-bar
i thought it’s a thing of the past, but now, “expensive numbers” is back!
Google and FSB, CAN YOU FIX THIS HOLE? IT ANNOYS EUROPE! THANKS 🙂
tweets / twitter:
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!