In General:
while a update/upgrade between major releases in theory is always “possible” – i realized it comes with a lot of problems.
A complete reinstall “from scratch” is probably always the cleaner approach.
apt-get dist-upgrade; # fails miserably because it can not resolve all the dependencies
aptitude upgrade; # takes ages – installs billions of packages that were not installed previously – in the end succeeds on the server but breaks functionality.
(decided to keep 99% of all config files, services like fail2ban refuses to start)
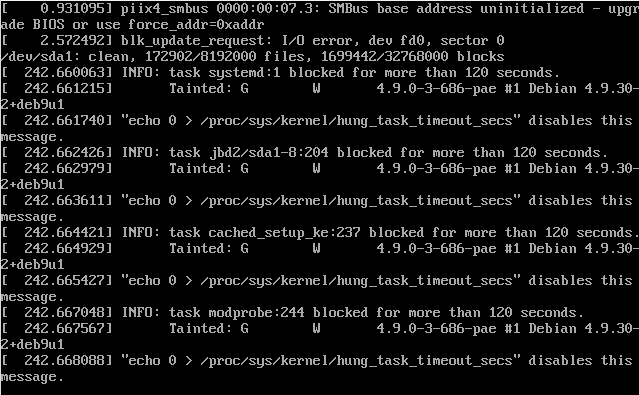
Could not wait for the desktop-dist-upgrade to finish… you are probably faster reinstalling the damn thing 😀
sad but true.
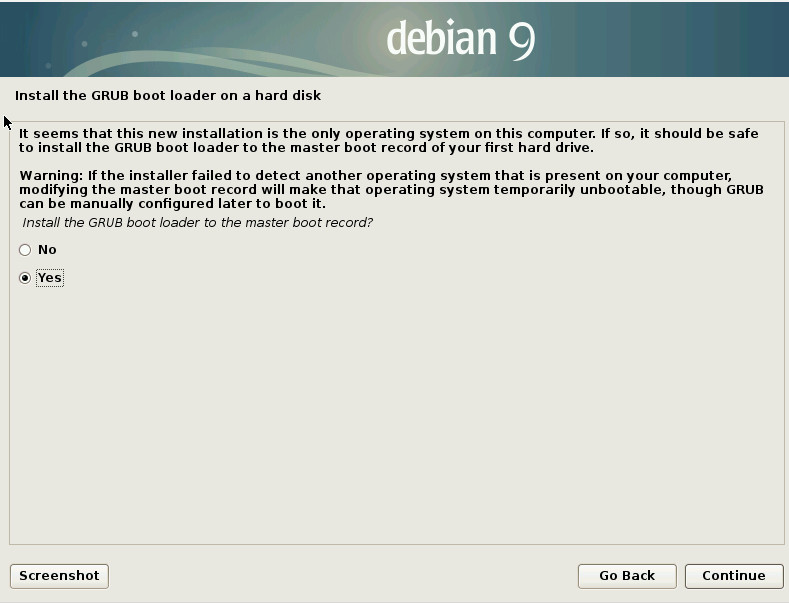
Hurray! The grafical setup is back! i was completely fine with the terminal ASCII GUI setup. whatever works better.
the problem:
a lot of config files need to be updated that might have been modified by the administrator of the server or some software like VestaControlPanel.
If you can afford it (time-wise):
- snapshot your running installation
- backup all your data in a form that let’s you as-easy as possible restore it
- dump every mysql database into a separate file
- save your whole server file-wise
- do a clean reinstall of Debian9
- restore data
- test functionality and speed, if good keep if not revert to snapshot
i really like the debian repository app store thing – but what could be improved is the apt-cache search PATTERN results and yes – the dist-upgrade process.
So i have to say: live-kernel-patching yeah – distro-upgrade – too much fail.
So the debian upgrade tool knows what files have been modified – but does not know exactly what lines have been added/deleted.
Because then you could tell your user: “hey we know you modified this /etc/file.config – you added those lines and changed those lines – commented out those lines – here is the new config file – you will have to do the process all over again – or have me automatically apply your changes to the new config file (++ — +# -#) ”
What is new?
https://www.debian.org/releases/stretch/i386/release-notes/ch-whats-new.en.html
Howto:
you should backup all config files you manually modified (haha!) 😀 (just backup the whole system file-wise with rsync)
cp /etc/ssh/sshd_config /etc/ssh/sshd_config.bak; # backup ssh-server-config cp /etc/ssh/ssh_config /etc/ssh/ssh_config.bak; # backup ssh-client-config apt-get update && apt-get -y upgrade; # update to latest debian8 aptitude update && aptitude -y upgrade; # same same but different sed -i 's/jessie/stretch/g' /etc/apt/sources.list; # modify sources.list aptitude update && aptitude -y dist-upgrade; # try to update from debian8 to debian9
Fetched 19.6 MB in 8s (2,181 kB/s) Current status: 1106 updates [+1106], 14870 new [+14870 new packages will be installed? holy cow why?]. # it will present you changelogs simply type q; # for quit Fetched 734 MB in 1min 27s (8,377 kB/s)Current default time zone: 'Europe/Berlin' Local time is now: Mon Jun 26 17:01:12 CEST 2017. Universal Time is now: Mon Jun 26 15:01:12 UTC 2017. Run 'dpkg-reconfigure tzdata' if you wish to change it.
why is it changing the timezone during upgrade? does not make sense to me 😀
tested this howto on 14:08 26.06.2017: https://linuxconfig.org/how-to-upgrade-debian-8-jessie-to-debian-9-stretch
and it gave me issues… (scroll down to issues).
“the less software installed on your system, the higher chance for a successful upgrade”
wohoo! again the “keep it simple and beautiful unix philosophy” approach rules – but well – sometimes you just want to make your server to run-it-all (as much as it can and ignore the software-package-management issues).
Warning:
MariaDB replaces MySQL database in Debian 9 Stretch. This introduces a new database binary data file format which is not backwards compatible with your current ( Debian 8 Jessie ) database format. During the upgrade your databases will be upgraded automatically. However, when you run into some issues during or after the upgrade, you will not be able revert back! From this reason it is important to backup all your current databases before you proceed with a Debian 9 Stretch upgrade!
REFERENCE: debian.org
i really wonder if MariDB is more RAM-efficient than MySQL which says 8GByte RAM is now the new Minimum Hardware recommended…. you read this on a webserver with 2GByte RAM… 😀
time and size:
the update itself on my test machine was only few hundres MBytes in size… but it takes quite a while to download, unpack, install, configure all those new packages.
manually changed files:
the setup process will ask you e.g. “lightdm.conf was modified – do you want to keep your modified version (default) or overwrite with the package-author’s version”.
so it would be wise to backup those files and then continue the update… in my case it is simply a line i added to enable lightdm auto-login without password (INSECURE!!!).
changelog:
– This release removes the AUTOLOAD and compile optimisations from CGI.pm
that were introduced into CGI.pm twenty (20) years ago as a response to
its large size, which meant there was a significant compile time penalty.
[…]
– This essentially deprecates the -compile pragma and ->compile method. The
-compile pragma will no longer do anything, whereas the ->compile method
will raise a deprecation warning. More importantly this also REMOVES the
-any pragma because as per the documentation this pragma needed to be
“used with care or not at all” and allowing arbitrary HTML tags is almost
certainly a bad idea. If you are using the -any pragma and using arbitrary
tags (or have typo’s in your code) your code will *BREAK*
– Although this release should be back compatible (with the exception of any
code using the -any pragma) you are encouraged to test it throughly as if
you are doing anything out of the ordinary with CGI.pm (i.e. have bugs
that may have been masked by the AUTOLOAD feature) you may see some issues.
From upstream Changes, 4.13:
– CGI::Pretty is now DEPRECATED and will be removed in a future release.
Please see GH #162 (https://github.com/leejo/CGI.pm/issues/162) for more
information and discussion (also GH #140 for HTML function deprecation
discussion: https://github.com/leejo/CGI.pm/issues/140)
— gregor herrmann <gregoa@debian.org> Sat, 09 May 2015 22:01:44 +0200
net-tools (1.60+git20161116.90da8a0-1) unstable; urgency=medium
After 15 years without upstream development, net-tools is being worked on
again, fixing many long-standing issues.
The bad news is that the output of many commands has changed, and it is sure
to break scripts that relied on parsing it.
If you have customs scripts that use any of these commands, please make sure
they still work after this upgrade:
netstat, ifconfig, ipmaddr, iptunnel, mii-tool, nameif, plipconfig, rarp,
route, slattach, arp.
Apologies in advance for the trouble that this may cause, but maintaining a
separate version of net-tools just to keep the old format is something I am
not able to do.
— Martín Ferrari <tincho@debian.org> Mon, 26 Dec 2016 05:29:25 +0000
pinentry-gtk2 (0.9.6-3) unstable; urgency=medium
Since pinentry-gtk2 0.9.6, upstream now uses the default GTK text
entry widget instead of a custom text-entry widget. The GTK text
entry widget in password mode may display characters while typed based
on the setting of gtk-entry-password-hint-timeout. This value
defaults to 0 (never display), but may be overridden in
/etc/gtk-2.0/gtkrc or ~/.gtkrc-2.0. If your password entry shows the
last character typed, please ensure that this value is not set in your
system’s configuration files.
See
https://developer.gnome.org/gtk2/stable/GtkSettings.html#GtkSettings–gtk-entry-password-hint-timeout
and https://bugs.debian.org/801757 for more details.
— Daniel Kahn Gillmor <dkg@fifthhorseman.net> Mon, 19 Oct 2015 20:39:25 -0400
samba (2:4.4.1+dfsg-1) experimental; urgency=medium
This Samba security addresses both Denial of Service and Man in
the Middle vulnerabilities.
Both of these changes implement new smb.conf options and a number
of stricter behaviours to prevent Man in the Middle attacks on our
network services, as a client and as a server.
Between these changes, compatibility with a large number of older
software versions has been lost in the default configuration.
See the release notes in WHATNEW.txt for more information.
Here are some additional hints how to work around the new stricter default behaviors:
* As an AD DC server, only Windows 2000 and Samba 3.6 and above as
a domain member are supported out of the box. Other smb file
servers as domain members are also fine out of the box.
* As an AD DC server, with default setting of “ldap server require
strong auth”, LDAP clients connecting over ldaps:// or START_TLS
will be allowed to perform simple LDAP bind only.
The preferred configuration for LDAP clients is to use SASL
GSSAPI directly over ldap:// without using ldaps:// or
START_TLS.
To use LDAP with START_TLS and SASL GSSAPI (either Kerberos or
NTLMSSP) sign/seal protection must be used by the client and
server should be configured with “ldap server require strong
auth = allow_sasl_over_tls”.
Consult OpenLDAP documentation how to set sign/seal protection
in ldap.conf.
For SSSD client configured with “id_provider = ad” or
“id_provider = ldap” with “auth_provider = krb5”, see
sssd-ldap(5) manual for details on TLS session handling.
* As a File Server, compatibility with the Linux Kernel cifs
client depends on which configuration options are selected, please
use “sec=krb5(i)” or “sec=ntlmssp(i)”, not “sec=ntlmv2”.
* As a file or printer client and as a domain member, out of the
box compatibility with Samba less than 4.0 and other SMB/CIFS
servers, depends on support for SMB signing or SMB2 on the
server, which is often disabled or absent. You may need to
adjust the “client ipc signing” to “no” in these cases.
* In case of an upgrade from versions before 4.2.0, you might run
into problems as a domain member. The out of the box compatibility
with Samba 3.x domain controllers requires NETLOGON features only
available in Samba 3.2 and above.
However, all of these can be worked around by setting smb.conf
options in Samba, see WHATSNEW.txt the 4.2.0 release notes at
https://www.samba.org/samba/history/samba-4.2.0.html and the Samba
wiki for details, workarounds and suggested security-improving
changes to these and other software packages.
Suggested further improvements after patching:
It is recommended that administrators set these additional options,
if compatible with their network environment:
server signing = mandatory
ntlm auth = no
Without “server signing = mandatory”, Man in the Middle attacks
are still possible against our file server and
classic/NT4-like/Samba3 Domain controller. (It is now enforced on
Samba’s AD DC.) Note that this has heavy impact on the file server
performance, so you need to decide between performance and
security. These Man in the Middle attacks for smb file servers are
well known for decades.
Without “ntlm auth = no”, there may still be clients not using
NTLMv2, and these observed passwords may be brute-forced easily using
cloud-computing resources or rainbow tables.
— Andrew Bartlett <abartlet+debian@catalyst.net.nz> Tue, 12 Apr 2016 16:18:57 +1200
lsb (9.20150826) unstable; urgency=low
This update drops all lsb-* compatibility packages, and is therefore an
abandon of the pursuit of LSB compatibility for Debian. Only lsb-release and
lsb-base are kept as they continue to be used throughout the archive.
— Didier Raboud <odyx@debian.org> Wed, 26 Aug 2015 12:00:00 +0200
issues:
after upgrade i can login, but MATE Desktop is not loaded/hangs.
the menu-bar at lightdm login looks Gnome3 alike… but Gnome3 was not installed previously.
apt-get upgrade; # reports 0 upgraded, 0 newly installed, 0 to remove and 431 not upgraded. aptitude update; aptitude upgrade; # tries to resolve the dependencies problem taking ages... aptitude dist-upgrade; 404 packages upgraded, 332 newly installed, 156 to remove and 0 not upgraded. Need to get 526 MB/527 MB of archives. After unpacking 663 MB will be used. The following packages have unmet dependencies: perl-modules-5.24 : Conflicts: perl-modules (< 5.22.0~) but 5.20.2-3+deb8u7 is installed. libsigc++-2.0-0v5 : Conflicts: libsigc++-2.0-0c2a but 2.4.0-1 is installed. xserver-xorg-core : Conflicts: xserver-xorg-video-modesetting but 0.9.0-2 is installed. linux-image-4.9.0-3-686-pae : Breaks: xserver-xorg-input-vmmouse (< 1:13.0.99) but 1:13.0.0-1+b3 is installed. xserver-xorg-video-modesetting : Depends: xorg-video-abi-18 which is a virtual package. perl-base : Breaks: perl-modules (< 5.24.1~) but 5.20.2-3+deb8u7 is installed. libstdc++6 : Breaks: libsigc++-2.0-0c2a (<= 2.4.1-1+b1) but 2.4.0-1 is installed. xserver-xorg-input-vmmouse : Depends: xorg-input-abi-21 which is a virtual package. The following actions will resolve these dependencies: Remove the following packages: 1) libsigc++-2.0-0c2a 2) perl-modules 3) xserver-xorg-input-vmmouse 4) xserver-xorg-video-modesetting Accept this solution? [Y/n/q/?] Y # .... wait for a long long time until... Processing triggers for python-support (1.0.15) ... Processing triggers for fontconfig (2.11.0-6.7+b1) ... Processing triggers for libc-bin (2.24-11+deb9u1) ... Processing triggers for systemd (232-25) ... Processing triggers for dbus (1.10.18-1) ... Processing triggers for dictionaries-common (1.27.2) ... Processing triggers for libvlc-bin:i386 (2.2.6-1~deb9u1) ... Processing triggers for gconf2 (3.2.6-4+b1) ... Processing triggers for initramfs-tools (0.130) ... update-initramfs: Generating /boot/initrd.img-4.9.0-3-686-pae Processing triggers for menu (2.1.47+b1) ... Current status: 0 updates [-427]. reboot; # you probably want to test if it still boots :-D
… not sooo well…. revert to previous snapshot.
results:
i am testing in a virtual test machine… and later snapshot and upgrade the live-server.
reboots are okay. high-availability not highest priority. (speed, stability, security is)
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!