Ransomware hitting a new dimension – with the NSA-backdoors pre-installed in a lot of soft and hardware (check out Intel AMT/ME disaster) – hackers/attackers are trying to find and exploit those in order to make some profit. Millions of € and $ are earned by hackers by ransomware – probably the most profitable way to use an exploit. This money is – of course – re invested into finding further security holes – making it a true cat-and-mouse game for data and data protection.
Even Cisco (!!!) routers contain NSA-backdoors that also could be used by hackers.
“could allow remote code execution if an attacker sends specially crafted messages to a Microsoft Server Message Block 1.0 (SMBv1) server.”
MS17-010 Security in Microsoft’s SMB-Server
Win XP patched to avert new outbreaks spawned by NSA-leaking Shadow Brokers
download patch for Windows XP
EN:
https://www.microsoft.com/en-us/download/confirmation.aspx?id=3205
DE:
https://www.microsoft.com/de-de/download/confirmation.aspx?id=3205
Company warns of “destructive cyberattacks” as it tries to prevent another WCry.
sophos podcast:
What it means for IT-crowd:
updates updates updates! 😀
means a lot of work for Administrators…
snapshot – update – test…
http://www.chip.de/downloads/CHIP-Windows-7-Update-Pack-32-Bit_69083747.html
Security Security Security
Administrators will have to ramp up security massively and constantly. Unfortunately a lot of companies like to learn from mistakes – before investing more money into cyber security.
Have a anti virus software installed on every client.
Also: separate internet (www,mail) usage from your business-networks as much as possible – allowing by firewall only contact to certain servers that are needed for online-updates – and nothing more.
What you can and should do:
all other Unix-like operating system such as macOS, FreeBSD and others are not vulnerable to the flaw. However, you must take care if you are using Samba software on Linux or Unix-like system. Make sure you disable SMB version 1 on Windows clients.
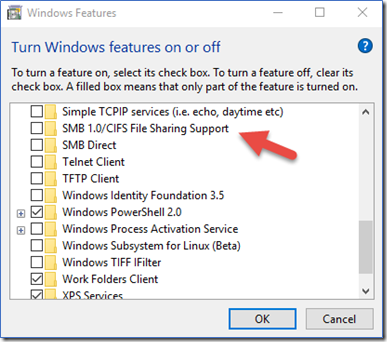
Long answer: WannaCrypt/WannaCry targets the Microsoft Windows operating system. The attack spreads by phishing emails but also uses the EternalBlue exploit and DoublePulsar backdoor developed by the U.S. National Security Agency (NSA). If you are using older and unsupported operating systems such as Windows XP and Windows Server 2003, you will get infected. All of your files will be encrypted. To get back your files, you need to pay ransom payments in the cryptocurrency Bitcoin. Microsoft has released software updates for Windows XP and Windows Server 2003. You must apply those patches ASAP. In short Linux users are not affected by this attack.
How to protect yourself from ransomware attacks
I recommend that everyone should do the following regardless of operating system:
- Backup all your files and data regularly. Ideally you should make three copies of your backup data on two different media. One backup copy must be offline all the time.
- Patch your system including BIOS and device drivers
- Turn on automatic updates
- Do not use outdated and unsupported software
- Turn on firewall on both your router and computer
- You should turn on anti-virus software on Windows
- All Windows XP user should upgrade to the latest version of Microsoft Windows such as Windows 10. All Windows 2003 server user should upgrade to the latest version of Windows server
- Avoid using pirated software
- See Decentsecurity website, it has a guide that is reasonable for non-techies to understand and follow
In Addition:
- internet-clients should NOT be connected physically to the LAN, but to a WIFI-AP in demilitarized zone (between internet-DSL-router and your firewall – blocking all access to your LAN) (use noscript!)
- LAN-clients should not use Administrator accounts to work (would allow them to install software – unfortunately/luckily portable firefox can be run without Administrator rights!)
- LAN-clients should NOT use www or mail and have only access to certain servers (Microsoft Updates other Update-Servers)
- LAN-clients should NOT be able to bring USB sticks from home and plugin at work. (disable USB)
- Use OpenDNS as dns-servers on all your DHCP-Servers (Fritzbox can do it)
- NoJS: i think it’s highly critical if Internet and JavaScript usage is allowed inside a company-LAN.
- Always a good idea if possible: Separate programs (C:) from data (D:) and have regular backups of atleast the data (not possible for all programs to separate) Actually ONLY the data is supposed to change during normal operating.
- IMHO also a good idea – but increasing time and costs for updates – lock C: against changes 😀 – this can be done software-wise with: http://www.dr-kaiser.de/ (can also block access to internet, USB, DVD/CD)
Backups Backups Backups
a clean and robust backup strategy needs to be put in place…
Automatic backups are nice… but could theoretically also be reached by Virus.
Critical data should be backuped to robust MDISCs every year. (untested)
And therefore secured against – electro magnetic problems but also hackers 😉
“Wanna Decrypter 2.0 ransomware that started its assault against hospitals across the UK before spilling across the globe.
The attack appears to have exploited a Windows vulnerability Microsoft released a patch for in March. That flaw was in the Windows Server Message Block (SMB) service, which Windows computers use to share files and printers across local networks. Microsoft addressed the issue in its MS17-010 bulletin.
SophosLabs said the ransomware – also known as WannaCry, WCry, WanaCrypt and WanaCrypt0r – encrypted victims’ files and changed the extensions to .wnry, .wcry, .wncry and .wncrypt.
Sophos is protecting customers from the threat, which it now detects as Troj/Ransom-EMG, Mal/Wanna-A, Troj/Wanna-C, and Troj/Wanna-D. Sophos Customers using Intercept X will see this ransomware blocked by CryptoGuard. It has also published a Knowledge Base Article (KBA) for customers.”
https://nakedsecurity.sophos.com/2017/05/12/wanna-decrypter-2-0-ransomware-attack-what-you-need-to-know/
https://www.heise.de/thema/Ransomware
update: ransomeware generated 25Millione$ https://www.theverge.com/2017/7/25/16023920/ransomware-statistics-locky-cerber-google-research
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!


Firewalls:
http://www.phoenixcontact-cybersecurity.com/en/
https://secure2.sophos.com/en-us/products/free-tools/sophos-xg-firewall-home-edition/software.aspx
https://dwaves.de/2017/01/31/how-to-create-your-own-pfsense-firewall-proxy/
Links: