update: 2024-04: “how to fix name resolution works (host nslookup) but no ping”
no kidding: on a Debian installed from live iso, the host domain.com resolved fine but ping would result into “Name or service not known”
hostnamectl; # tested on Operating System: Debian GNU/Linux 12 (bookworm) Kernel: Linux 6.1.0-18-amd64 Architecture: x86-64 echo "[main]" >> /etc/NetworkManager/conf.d/dns.conf echo "dns=none" >> /etc/NetworkManager/conf.d/dns.conf echo "main.systemd-resolved=false" >> /etc/NetworkManager/conf.d/dns.conf # restart network manager systemctl restart NetworkManager
(creditz)
DNS servers are the “yellow pages” “phone book” of the internet.
Whoever is running DNS servers get’s to know all queries send (what client is requesting and probably connecting to what address… basically: what websites the user have visited, this is very private sensitive data, so DNS servers need to be trustworthy use encryption and respect user’s privacy)
https://dnsprivacy.org/wiki/display/DP/DNS+Privacy+Test+Servers
what DNS server should user use?
it’s a hard choice.
most users probably simply go with whatever the vendor of their router or ISP provider seems fit. (in the case of StarLink that would be Google’s DNS 8.8.8.8).
Of course a user does (usually) not type “185.222.222.222” into one’s browser.
no the user just types: https://dns.sb
(or yahoo.com or domain.com)
the DNS software then asks the nearby (usually router) “what ‘phone number’ (ip) does domain yahoo.com have?”
If the router does not know, the router will ask again the DNS server that either the user pre-configured or the internet service provider pre-conigured. (usually on port 53 (the server side software most used under GNU Linux is BIND))
So yes – the DNS server is a very important part of the internet.
Also: the DNS server “knows” all the sites a user might contact (because the user-program is asking it for the ‘phone number’ (ip) of yahoo.com)
So it is critical if a user does not want to be mass surveillance spied on to pick a ethic DNS server. (not easy, who is running what? and: will it log all user’s lookups?)
some public dns servers:
nice explanation video: why privacy protecting DNS servers-resolver are important: https://www.youtube.com/watch?v=olW9jtOMMSI
(alphabetical order, no preference!)
new list:
https://wiki.ipfire.org/dns/public-servers
List of Public DNS Servers
This is a list of publicly available DNS servers suitable for use with IPFire. They are operated by many different organisations in many different countries. Please consider carefully which ones you would like to use.
DNS Servers that support UDP/TCP
host 116.202.176.26 https://libredns.gr/
| Operator | Address(es) | Hostname |
|---|---|---|
| Anycast | ||
| C1VHosting | 152.89.170.250 | |
| 152.89.170.250 | ||
| 152.89.170.251 | ||
| 2a0e:97c0:210::250 | ||
| censurfridns.dk | 91.239.100.100 | anycast.uncensoreddns.org |
| 2002:d596:2a92:1:71:53:: | ||
| Cloudflare | 1.1.1.1 | cloudflare-dns.com |
| 1.0.0.1 | ||
| 2606:4700:4700::1111 | ||
| 2606:4700:4700::1001 | ||
| dns.sb | 185.222.222.222 | dns.sb |
| 185.184.222.222 | ||
| 2a09:: | ||
| 2a09::1 | ||
| Hurricane Electric | 74.82.42.42 | |
| 2001:470:20::2 | ||
| Google Public Free DNS | 8.8.8.8 | dns.google |
| 8.8.4.4 | ||
| Germany (DE) | ||
| Lightning Wire Labs | 81.3.27.54 | recursor01.dns.ipfire.org |
| 2001:678:b28::54 | ||
| 81.3.27.54 | recursor01.dns.lightningwirelabs.com |
|
| 2001:678:b28::54 | ||
| Denmark (DK) | ||
| censurfridns.dk | 89.233.43.71 | unicast.uncensoreddns.org |
| 2a01:3a0:53:53:: | ||
| Spain (ES) | ||
| puntCAT | 109.69.8.51 | |
| France (FR) | ||
| French Data Network (FDN) | 80.67.169.12 | |
| 80.67.169.40 | ||
| 2001:910:800::12 | ||
| 2001:910:800::40 | ||
| Netherlands (NL) | ||
| Freenom World | 80.80.80.80 | |
| 80.80.81.81 | ||
| United Kingdom (UK) | ||
| CyberGhost | 194.187.251.67 | |
| United States (US) | ||
| Alternate DNS | 198.101.242.72 | |
| 23.253.163.53 | ||
| Comcast / Xfinity | 75.75.75.75 | |
| 75.75.76.76 | ||
| CyberGhost | 38.132.106.139 | |
| Neustar DNS Advantage | 156.154.70.1 | |
| 156.154.71.1 | ||
| Sprintlink General DNS | 204.117.214.10 | |
| 199.2.252.10 | ||
| 204.97.212.10 | ||
| Verisign | 64.6.64.6 | |
| 64.6.65.6 | ||
DNS-over-TLS service
| Operator | Address(es) | DNS over TLS Hostname |
|---|---|---|
| Anycast | ||
| censurfridns.dk | 91.239.100.100 | anycast.uncensoreddns.org |
| 2002:d596:2a92:1:71:53:: | ||
| Cloudflare | 1.1.1.1 | cloudflare-dns.com |
| 1.0.0.1 | ||
| 2606:4700:4700::1111 | ||
| 2606:4700:4700::1001 | ||
| Freifunk München e.V. | 5.1.66.255 | anycast01.ffmuc.net |
| 2001:678:e68:f000:: | ||
| 5.1.66.255 | dot.ffmuc.net |
|
| 2001:678:e68:f000:: | ||
| dns.sb | 185.222.222.222 | dns.sb |
| 185.184.222.222 | ||
| 2a09:: | ||
| 2a09::1 | ||
| Google Public Free DNS | 8.8.8.8 | dns.google |
| 8.8.4.4 | ||
| Austria (AT) | ||
| Foundation for Applied Privacy | 146.255.56.98 | dot1.applied-privacy.net |
| 2a01:4f8:c0c:83ed::1 | ||
| Canada (CA) | ||
| CMRG DNS | 199.58.81.218 | dns.cmrg.net |
| 2001:470:1c:76d::53 | ||
| Switzerland (CH) | ||
| Digitale Gesellschaft Schweiz | 185.95.218.42 | dns.digitale-gesellschaft.ch |
| 185.95.218.43 | ||
| 2a05:fc84::42 | ||
| 2a05:fc84::43 | ||
| post-factum | 140.238.215.192 | dot.post-factum.tk |
| Germany (DE) | ||
| Digitalcourage e.V. | 5.9.164.112 | dns3.digitalcourage.de |
| Lightning Wire Labs | 81.3.27.54 | recursor01.dns.ipfire.org |
| 2001:678:b28::54 | ||
| 81.3.27.54 | recursor01.dns.lightningwirelabs.com |
|
| 2001:678:b28::54 | ||
| Denmark (DK) | ||
| censurfridns.dk | 89.233.43.71 | unicast.uncensoreddns.org |
| 2a01:3a0:53:53:: | ||
| Finland (FI) | ||
| Snopyta | 95.216.24.230 | fi.dot.dns.snopyta.org |
| 2a01:4f9:2a:1919::9301 | ||
| France (FR) | ||
| Neutopia | 89.234.186.112 | dns.neutopia.org |
| 2a00:5884:8209::2 | ||
| Luxembourg (LU) | ||
| Restena Foundation | 158.64.1.29 | kaitain.restena.lu |
| 2001:a18:1::29 | ||
| Netherlands (NL) | ||
| GetDNS | 185.49.141.37 | getdnsapi.net |
| 2a04:b900:0:100::37 | ||
| Surfnet | 145.100.185.17 | dnsovertls2.sinodun.com |
| 145.100.185.18 | dnsovertls3.sinodun.com |
|
| 2001:610:1:40ba:145:100:185:17 | ||
| 2001:610:1:40ba:145:100:185:18 | ||
| United States (US) | ||
| Comcast / Xfinity (beta) | 96.113.151.145 | dot.xfinity.com |
DNS providers that are not recommended
These providers are not recommended for use with IPFire because they do not support DNSSEC or tamper with DNS traffic in another way, such as filtering malware or porn.
| Operator | IP Addresses |
|---|---|
| Cleanbrowsing | 2a0d:2a00:1::2 / 185.228.168.9, 2a0d:2a00:2::2 / 185.228.169.9 |
| DNS for Family | 94.130.180.225 / 2a01:4f8:1c0c:40db::1, 78.47.64.161 / 2a01:4f8:1c17:4df8::1, dns-dot.dnsforfamily.com, https://dns-doh.dnsforfamily.com/dns-query |
| Comodo Secure DNS | 8.26.56.26, 8.20.247.20 |
| DNSReactor | 45.55.155.25, 104.236.210.29 |
| FreeDNS | 37.235.1.174, 37.235.1.177 |
| GreenTeamDNS | 81.218.119.1, 09.88.198.133 |
| Nuernberg Internet Exchange (N-IX) | 194.8.57.12 |
| OpenDNS (Hosted Blacklists) | 208.67.222.222, 208.67.220.220, 208.67.220.222, 208.67.222.220 |
| Quad 9 | 9.9.9.9, 149.112.112.112, 9.9.9.10, 149.112.112.10 |
| SWITCH (Hosted Blacklists) | 130.59.31.248 / 2001:620:0:ff::2, 130.59.31.251 / 2001:620:0:ff::3 |
| Yandex.DNS | 77.88.8.88, 77.88.8.2 |
| SafeDNS | 195.46.39.39, 195.46.39.40 |
| Level 3 / CentryLink / Verizon | 4.2.2.1, 4.2.2.2, 4.2.2.3, 4.2.2.4, 4.2.2.5, 4.2.2.6 |
| SkyDNS | 193.58.251.251 |
| New Nations | 5.45.96.220 |
| SecureDNS 1 | 146.185.167.43 |
About location and DNSSEC status
The location of the servers has been stated by using the IPFire Location database. However, it might be possible that the location is wrong (or has been changed meanwhile).
The servers that are marked with “Anycast” are using anycasts so that traffic will be routed to the nearest of the many instances that are there on the network. Thereof the exact location of the server(s) cannot be determined. Worse, different configurations of Anycast instances cannot be determined reliable.
Security Considerations
A DNS server has a very powerful function in network topology. Please keep in mind that it might log your queries (which is a huge information leak).
Further, not all of the DNS servers listed above return correct answers in any case. Some of them return failures for harmful or malicious sites. Check the operators website for more information on this topic.
For security reasons, it is required to use DNS servers which support DNSSEC. For privacy and availability reasons, avoid using just one providers’ DNS servers.
Links
old list: Public DNS Servers
- Cloudflare: 1.1.1.1 and 1.0.0.1
2606:4700:4700::1111
2606:4700:4700::1001 - Alternate DNS
198.101.242.72
23.253.163.53 - BlockAid Public DNS (or PeerDNS)
205.204.88.60
178.21.23.150 - Censurfridns
91.239.100.100
89.233.43.71
2001:67c:28a4::
2002:d596:2a92:1:71:53:: - Christoph Hochstätter
209.59.210.167
85.214.117.11 - ClaraNet
212.82.225.7
212.82.226.212 - Comodo Secure DNS
8.26.56.26
8.20.247.20 - DNS.Watch
84.200.69.80
84.200.70.40
2001:1608:10:25::1c04:b12f
2001:1608:10:25::9249:d69b - DNSReactor
104.236.210.29
45.55.155.25 - Dyn
216.146.35.35
216.146.36.36 - FDN
80.67.169.12
2001:910:800::12 - FoeBud
85.214.73.63 - FoolDNS
87.118.111.215
213.187.11.62 - FreeDNS
37.235.1.174
37.235.1.177 - Freenom World
with massive amounts of tutorials for many routers: https://www.freenom.world/en/test-my-device.html
80.80.80.80
80.80.81.81 - German Privacy Foundation e.V.
87.118.100.175
94.75.228.29
85.25.251.254
62.141.58.13 - Google Public DNS
8.8.8.8
8.8.4.4
2001:4860:4860::8888
2001:4860:4860::8844 - GreenTeamDNS
81.218.119.11
209.88.198.133 - Hurricane Electric
74.82.42.42
2001:470:20::2 - Level3
209.244.0.3
209.244.0.4 - Neustar DNS Advantage
156.154.70.1
156.154.71.1 - New Nations
5.45.96.220
185.82.22.133 - Norton DNS
198.153.192.1
198.153.194.1 - OpenDNS
208.67.222.222
208.67.220.220
2620:0:ccc::2
2620:0:ccd::2 - OpenNIC
58.6.115.42
58.6.115.43
119.31.230.42
200.252.98.162
217.79.186.148
81.89.98.6
78.159.101.37
203.167.220.153
82.229.244.191
216.87.84.211
66.244.95.20
207.192.69.155
72.14.189.120
2001:470:8388:2:20e:2eff:fe63:d4a9
2001:470:1f07:38b::1
2001:470:1f10:c6::2001 - PowerNS
194.145.226.26
77.220.232.44 - Quad9
9.9.9.9
2620:fe::fe - SafeDNS
195.46.39.39
195.46.39.40 - SkyDNS
193.58.251.251 - SmartViper Public DNS
208.76.50.50
208.76.51.51 - ValiDOM
78.46.89.147
88.198.75.145 - Verisign
64.6.64.6
64.6.65.6
2620:74:1b::1:1
2620:74:1c::2:2 - Xiala.net
77.109.148.136
77.109.148.137
2001:1620:2078:136::
2001:1620:2078:137:: - Yandex.DNS
77.88.8.88
77.88.8.2
2a02:6b8::feed:bad
2a02:6b8:0:1::feed:bad - puntCAT
109.69.8.51
2a00:1508:0:4::9operated by: xTom (xtom.com)
https://de-dus.doh.sb/dns-query
host de-dus.doh.sb
de-dus.doh.sb has address 62.133.35.15
de-dus.doh.sb has IPv6 address 2a09:0:8::15https://de-fra.doh.sb/dns-query
host de-fra.doh.sb
de-fra.doh.sb has address 147.78.178.171
de-fra.doh.sb has address 147.78.178.172
de-fra.doh.sb has address 147.78.178.170
de-fra.doh.sb has address 147.78.178.174
de-fra.doh.sb has address 147.78.178.173
de-fra.doh.sb has IPv6 address 2a09:0:1:a::ahttps://nl-ams.doh.sb/dns-query
host nl-ams.doh.sb
nl-ams.doh.sb has address 78.142.193.52
nl-ams.doh.sb has address 78.142.193.50
nl-ams.doh.sb has address 78.142.193.54
nl-ams.doh.sb has address 78.142.193.51
nl-ams.doh.sb has address 78.142.193.53
nl-ams.doh.sb has IPv6 address 2a0c:59c0:19::3https://nl-ams2.doh.sb/dns-query
host nl-ams2.doh.sb
nl-ams2.doh.sb has address 194.169.181.36
nl-ams2.doh.sb has address 194.169.181.38
nl-ams2.doh.sb has address 194.169.181.34
nl-ams2.doh.sb has address 194.169.181.35
nl-ams2.doh.sb has address 194.169.181.37
nl-ams2.doh.sb has IPv6 address 2a09:0:7:4::2https://ee-tll.doh.sb/dns-query
host ee-tll.doh.sb
ee-tll.doh.sb has address 185.37.252.149
ee-tll.doh.sb has address 185.37.252.150
ee-tll.doh.sb has address 185.37.252.148
ee-tll.doh.sb has address 185.37.252.147
ee-tll.doh.sb has address 185.37.252.146
ee-tll.doh.sb has IPv6 address 2a04:6f00:3::2https://jp-kix.doh.sb/dns-query
host jp-kix.doh.sb
jp-kix.doh.sb has address 202.5.221.134
jp-kix.doh.sb has address 202.5.221.132
jp-kix.doh.sb has address 202.5.221.133
jp-kix.doh.sb has address 202.5.221.130
jp-kix.doh.sb has address 202.5.221.131
jp-kix.doh.sb has IPv6 address 2403:ac80:1030::2https://us-chi.doh.sb/dns-query
host us-chi.doh.sb
us-chi.doh.sb has address 104.128.62.173https://in-blr.doh.sb/dns-query
host in-blr.doh.sb
in-blr.doh.sb has address 143.244.128.32
in-blr.doh.sb has IPv6 address 2400:6180:100:d0::798:d001https://sg-sin.doh.sb/dns-query
host sg-sin.doh.sb
sg-sin.doh.sb has address 139.162.25.51
sg-sin.doh.sb has IPv6 address 2400:8901::f03c:92ff:fe4d:9e04https://hk-hkg.doh.sb/dns-query
host hk-hkg.doh.sb
hk-hkg.doh.sb has address 45.125.0.26
hk-hkg.doh.sb has IPv6 address 2403:2c80::26
is the internet connection working?
ping 1.1.1.1 # should return (if inet connection and routing is working) PING 1.1.1.1 (1.1.1.1) 56(84) bytes of data. 64 bytes from 1.1.1.1: icmp_seq=1 ttl=59 time=28.3 ms 64 bytes from 1.1.1.1: icmp_seq=3 ttl=59 time=29.7 ms 64 bytes from 1.1.1.1: icmp_seq=4 ttl=59 time=27.8 ms 64 bytes from 1.1.1.1: icmp_seq=5 ttl=59 time=34.1 ms ^C --- 1.1.1.1 ping statistics --- 5 packets transmitted, 4 received, 20% packet loss, time 38ms rtt min/avg/max/mdev = 27.799/29.995/34.145/2.497 ms # alternatively ping yahoo.com ping 98.137.246.7
should work
is DNS working?
ping yahoo.com
# should return PING yahoo.com (74.6.231.20) 56(84) bytes of data. 64 bytes from media-router-fp73.prod.media.vip.ne1.yahoo.com (74.6.231.20): icmp_seq=1 ttl=45 time=144 ms # if inet connection is is working # or test if DNS is working:
# should return the IP address of yahoo.com if DNS is working
host yahoo.com
# should return something like (if DNS is working)
yahoo.com has address 98.137.11.164
yahoo.com has address 74.6.143.25
yahoo.com has address 74.6.143.26
yahoo.com has address 74.6.231.20
yahoo.com has address 74.6.231.21
yahoo.com has address 98.137.11.163
yahoo.com has IPv6 address 2001:4998:44:3507::8001
yahoo.com has IPv6 address 2001:4998:24:120d::1:1
yahoo.com has IPv6 address 2001:4998:124:1507::f001
yahoo.com has IPv6 address 2001:4998:24:120d::1:0
yahoo.com has IPv6 address 2001:4998:44:3507::8000
yahoo.com has IPv6 address 2001:4998:124:1507::f000
yahoo.com mail is handled by 1 mta5.am0.yahoodns.net.
yahoo.com mail is handled by 1 mta7.am0.yahoodns.net.
yahoo.com mail is handled by 1 mta6.am0.yahoodns.net.
should work.
probably the most important GNU Linux DNS (client)config file
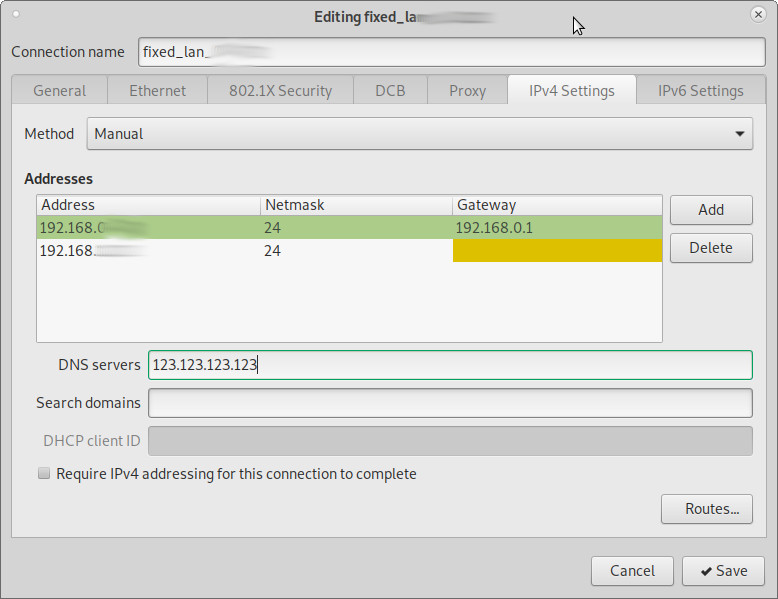
hostnamectl; # tested with Operating System: Debian GNU/Linux 10 (buster) Kernel: Linux 4.19.0-16-amd64 Architecture: x86-64 cat /etc/resolv.conf # Generated by NetworkManager nameserver 123.123.123.123 nameserver 192.168.0.1
here are the DNS servers listed that are used by the system.
it seems that GNU Linux Debian 10 (+Gnome2 MATE Desktop -> Network Manager)
changed taken here do not take effect until system reboot
apt show network-manager
Package: network-manager
Version: 1.14.6-2+deb10u1
Priority: optional
Section: net
Maintainer: Utopia Maintenance Team
Description: network management framework (daemon and userspace tools)
NetworkManager is a system network service that manages your network devices
and connections, attempting to keep active network connectivity when
available. It manages ethernet, WiFi, mobile broadband (WWAN), and PPPoE
devices, and provides VPN integration with a variety of different VPN
services.
This package provides the userspace daemons and a command line interface to
interact with NetworkManager.
Optional dependencies:
* ppp: Required for establishing dial-up connections (e.g. via GSM).
* dnsmasq-base/iptables: Required for creating Ad-hoc connections and
connection sharing.
address configuration.
* libteam-utils: Network Team driver allows multiple network interfaces to be
teamed together and act like a single one. This process is called “ethernet
bonding”, “channel teaming” or “link aggregation”.
what tools are there to debug connection problems?
traceroute
man: traceroute.man.txt
traceroute tracks the route packets taken from an IP network on their way to a given host. It utilizes the IP protocol’s time to live (TTL) field and attempts to elicit an ICMP TIME_EXCEEDED response from each gateway along the path to the host.
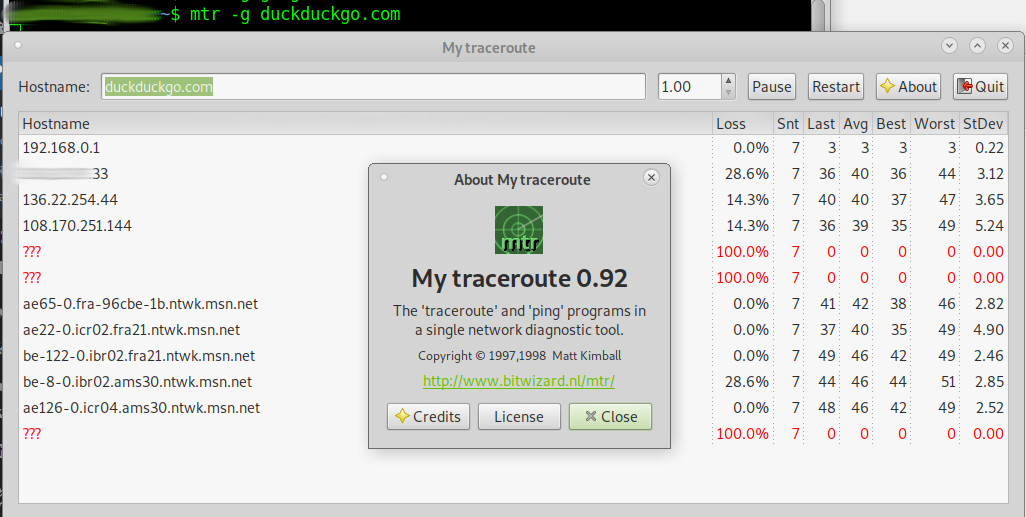
traceroute duckduckgo.com
traceroute to duckduckgo.com (40.114.177.156), 30 hops max, 60 byte packets
1 192.168.0.1 (192.168.0.1) 4.908 ms 5.862 ms 6.531 ms
2 136.22.97.33 (136.22.97.33) 41.515 ms 41.490 ms 41.433 ms
3 136.22.254.44 (136.22.254.44) 41.394 ms 142.250.160.202 (142.250.160.202) 41.429 ms 136.22.254.44 (136.22.254.44) 41.255 ms
4 108.170.252.19 (108.170.252.19) 49.669 ms 108.170.252.18 (108.170.252.18) 49.623 ms 108.170.251.144 (108.170.251.144) 49.630 ms
5 * 142.250.234.45 (142.250.234.45) 49.591 ms *
6 * * *
7 209.85.251.72 (209.85.251.72) 39.394 ms ae65-0.fra-96cbe-1b.ntwk.msn.net (198.200.130.254) 49.240 ms 49.175 ms
8 ae22-0.icr02.fra21.ntwk.msn.net (104.44.232.129) 49.141 ms 49.100 ms ae65-0.fra-96cbe-1a.ntwk.msn.net (198.200.130.132) 49.051 ms
9 ae26-0.icr01.fra21.ntwk.msn.net (104.44.232.127) 49.085 ms be-102-0.ibr01.fra21.ntwk.msn.net (104.44.23.105) 64.543 ms ae26-0.icr01.fra21.ntwk.msn.net (104.44.232.127) 54.937 ms
10 be-14-0.ibr01.ams30.ntwk.msn.net (104.44.28.103) 64.476 ms 64.464 ms be-100-0.ibr01.fra21.ntwk.msn.net (104.44.23.103) 43.527 ms
11 be-8-0.ibr02.ams30.ntwk.msn.net (104.44.28.123) 50.886 ms be-1-0.ibr02.ams21.ntwk.msn.net (104.44.16.146) 54.597 ms be-8-0.ibr02.ams30.ntwk.msn.net (104.44.28.123) 113.315 ms
12 be-22-0.ibr01.bom30.ntwk.msn.net (104.44.23.245) 54.436 ms be-1-0.ibr01.ams21.ntwk.msn.net (104.44.16.148) 54.562 ms ae100-0.icr01.ams30.ntwk.msn.net (104.44.22.214) 54.529 ms
13 * be-21-0.ibr02.bom30.ntwk.msn.net (104.44.23.247) 59.677 ms *
14 * * *
15 * * *
16 * * *
17 * * *
18 * * *
19 * * *
20 * * *
21 * * *
22 * * *
23 * * *
24 * * *
25 * * *
26 * * *
27 * * *
28 * * *
29 * * *
30 * * *
mtr (my traceroute)
has a nice gui and is good for tracing package “Loss”
su - root; apt install mtr; mtr -g duckduckgo.com
man: mtr.man.txt
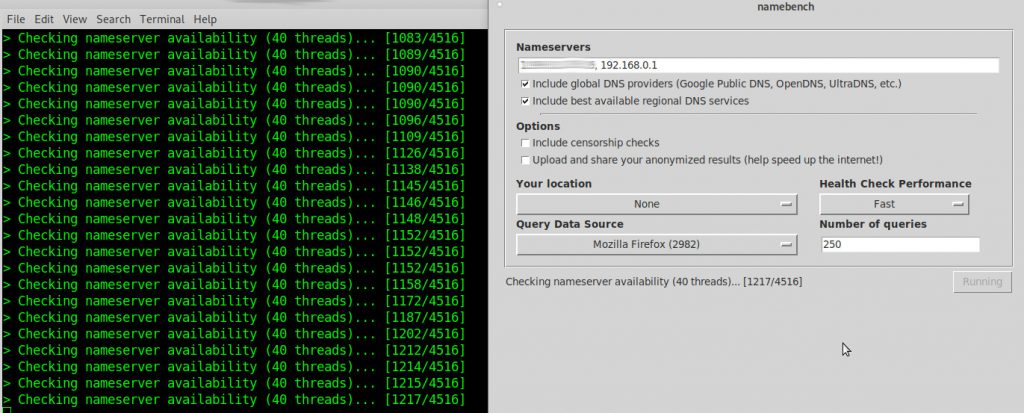
bench dns servers:
WARNING! https://code.google.com/archive/p/namebench/
was developed by someone working at-for Google.
would leave the “Upload and share your anonymized results” box unchecked.
it will run for a very long time… (does checking of 4500 name servers 250x)
su - root apt install namebench Ctrl+D # logout root namebench # start it (it's a gui program)
manpage: namebench.man.txt
what does the user get for all this hazzle?
after a pretty long wait…
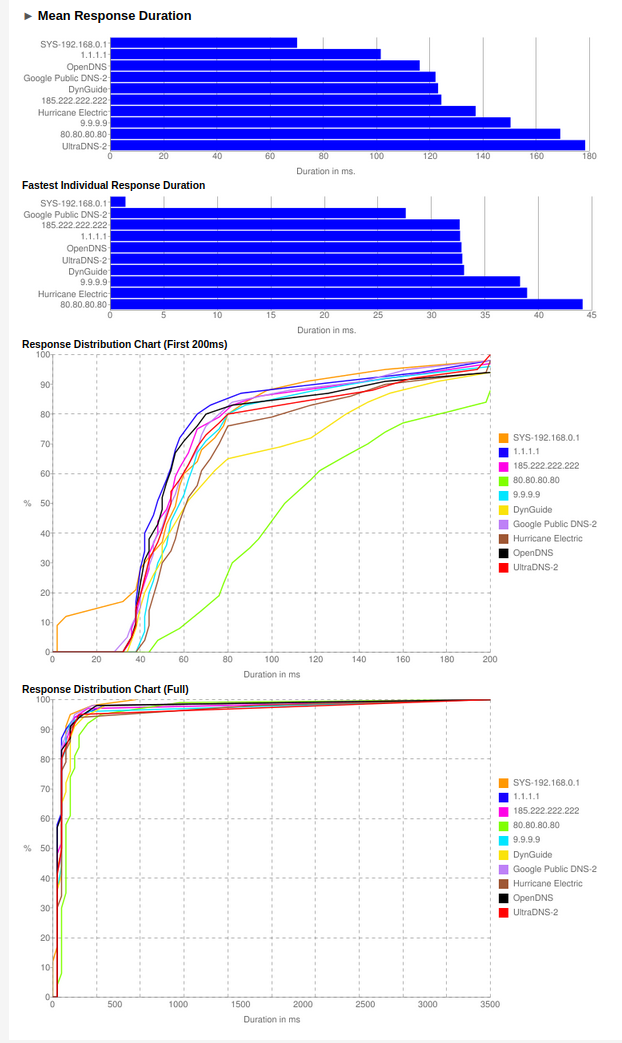
namebench_2021-06-07_2002.html
is produced that includes nice graphs such as:
what tools are there to query dns?
host is a simple utility for performing DNS lookups.
It is normally used to convert names to IP addresses and vice versa.
When no arguments or options are given, host prints a short summary of its command line arguments and options.
host google.com google.com has address 216.58.207.46 google.com has IPv6 address 2a00:1450:4001:824::200e google.com mail is handled by 10 aspmx.l.google.com. google.com mail is handled by 50 alt4.aspmx.l.google.com. google.com mail is handled by 40 alt3.aspmx.l.google.com. google.com mail is handled by 20 alt1.aspmx.l.google.com. google.com mail is handled by 30 alt2.aspmx.l.google.com. # use specific DNS server/specify DNS server to use for this DNS query dig @62.133.35.15 dwaves.de -t A ; <<>> DiG 9.11.5-P4-5.1+deb10u3-Debian <<>> @62.133.35.15 dwaves.de -t A ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 8111 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;dwaves.de. IN A ;; ANSWER SECTION: dwaves.de. 3600 IN A 78.46.181.43 ;; Query time: 80 msec ;; SERVER: 62.133.35.15#53(62.133.35.15) ;; WHEN: Mon Jun 07 14:57:30 CEST 2021 ;; MSG SIZE rcvd: 54 host -v google.com
Trying "google.com"
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 14663
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;google.com. IN A
;; ANSWER SECTION:
google.com. 71 IN A 142.250.185.206
Received 44 bytes from 195.10.195.195#53 in 33 ms
Trying "google.com"
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 10797
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;google.com. IN AAAA
;; ANSWER SECTION:
google.com. 174 IN AAAA 2a00:1450:4001:812::200e
Received 56 bytes from 195.10.195.195#53 in 32 ms
Trying "google.com"
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 40525
;; flags: qr rd ra; QUERY: 1, ANSWER: 5, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;google.com. IN MX
;; ANSWER SECTION:
google.com. 381 IN MX 30 alt2.aspmx.l.google.com.
google.com. 381 IN MX 10 aspmx.l.google.com.
google.com. 381 IN MX 50 alt4.aspmx.l.google.com.
google.com. 381 IN MX 20 alt1.aspmx.l.google.com.
google.com. 381 IN MX 40 alt3.aspmx.l.google.com.
# the dns server used port 53 (DNS)
Received 146 bytes from 195.10.195.195#53 in 33 ms
manpage: of command host.man.txt # why this tool is not installed per default on RedHat/Fedora/CentOS/rpm based distributions, i don't know # if "host" command is missing install: yum install bind-utils rpm -qi bind-utils-9.9.4-72.el7.x86_64 Name : bind-utils Epoch : 32 Version : 9.9.4 Release : 72.el7 Architecture: x86_64 Install Date: Tue 29 Jan 2019 03:43:36 PM CET Group : Applications/System Size : 441404 License : ISC Signature : RSA/SHA256, Mon 12 Nov 2018 03:22:04 PM CET, Key ID 24c6a8a7f4a80eb5 Source RPM : bind-9.9.4-72.el7.src.rpm Build Date : Wed 31 Oct 2018 01:29:37 AM CET Build Host : x86-01.bsys.centos.org Relocations : (not relocatable) Packager : CentOS BuildSystem <http://bugs.centos.org> Vendor : CentOS URL : http://www.isc.org/products/BIND/ Summary : Utilities for querying DNS name servers Description : Bind-utils contains a collection of utilities for querying DNS (Domain Name System) name servers to find out information about Internet hosts. These tools will provide you with the IP addresses for given host names, as well as other information about registered domains and network addresses. You should install bind-utils if you need to get information from DNS name servers. # what is in the package? rpm -ql bind-utils-9.9.4-72.el7.x86_64 /etc/trusted-key.key /usr/bin/dig /usr/bin/host /usr/bin/nslookup /usr/bin/nsupdate /usr/share/man/man1/dig.1.gz /usr/share/man/man1/host.1.gz /usr/share/man/man1/nslookup.1.gz /usr/share/man/man1/nsupdate.1.gz rpm -ql bind-libs-9.9.4-72.el7.x86_64 /usr/lib64/libbind9.so.90 /usr/lib64/libbind9.so.90.0.8 /usr/lib64/libdns.so.100 /usr/lib64/libdns.so.100.1.1 /usr/lib64/libisc.so.95 /usr/lib64/libisc.so.95.2.1 /usr/lib64/libisccc.so.90 /usr/lib64/libisccc.so.90.0.4 /usr/lib64/libisccfg.so.90 /usr/lib64/libisccfg.so.90.0.7 /usr/lib64/liblwres.so.90 /usr/lib64/liblwres.so.90.0.5
OpenDNS – Website Filter
Es ist möglich via DNS den Zugang zu bestimmten Seiten zu sperren z.B. wenn Sie nicht möchten, dass in ihrer Firma auf Facebook.com zugegriffen werden kann, dann sollten Sie sich einen Account bei: https://use.opendns.com/ holen (prinzipiell kostenlos) und dort die Filter-Funktion aktivieren und zentral in ihren DSL-Router oder sonstigen dedizierten DNS-Server (ist meistens auch der DHCP-Server) diese zwei Namen-Server eintragen: 208.67.222.222, 208.67.220.220.
Kann auch dezentral – pro PC – pro Host – in den Netzwerkeinstellungen der Netzwerkkarte (IPv4/IPv6) gemacht werden.
Dann erhält der User eine Fehlermeldung “Diese Seite ist gesperrt” statt facebook.com.
Allerdings: Wenn der User seinen eigenen DNS-Server eintragen kann (Administrator-Rechte hat) kann er diese Sperre umgehen.
Die Filter-Funktion versucht auch gehackte Server zu sperren – von denen eventuell in Webseiten versteckte Viren/Trojaner/Schadsoftware versucht (JavaScript am besten standardmäßig deaktivieren -> NoScript Addon für Firefox!!!) Schad-Code nachzuladen.
Dies hätte vermutlich die Installation des “Fake-Flashplayer-Updates” auch ohne Virenscanner verhindert.
Man MUSS die User vor sich selbst schützen.
Wer?
Verschiedene regionale Organisationen – https://www.nic.at/ = Österreich.
About BIND
BIND stands for “Berkeley Internet Name Domain”, because the software originated in the early 1980s at the University of California at Berkeley.
BIND is by far the most widely used DNS software on the Internet, providing a robust and stable platform on top of which organizations can build distributed computing systems with the knowledge that those systems are fully compliant with published DNS standards.
BIND and DNS
BIND implements the DNS protocols. The DNS protocols are part of the core Internet standards. They specify the process by which one computer can find another computer on the basis of its name. The BIND software distribution contains all of the software necessary for asking and answering name service questions.
The BIND software distribution has three parts:
1. Domain Name Resolver
A resolver is a program that resolves questions about names by sending those questions to appropriate servers and responding appropriately to the servers’ replies. In the most common application, a web browser uses a local stub resolver library on the same computer to look up names in the DNS. That stub resolver is part of the operating system. (Many operating system distributions use the BIND resolver library.) The stub resolver usually will forward queries to a caching resolver, a server or group of servers on the network dedicated to DNS services. Those resolvers will send queries to one or multiple authoritative servers in order to find the IP address for that DNS name.
2. Domain Name Authority server
An authoritative DNS server answers requests from resolvers, using information about the domain names it is authoritative for. You can provide DNS services on the Internet by installing this software on a server and giving it information about your domain names.
3. Tools
We include a number of diagnostic and operational tools. Some of them, such as the popular DIG tool, are not specific to BIND and can be used with any DNS server.
on newer debian9 minimal isos – dig does not come pre installed – you will have to install it manually:
apt install dnsutils
Why Use BIND?
- BIND is transparent open source. If your organization needs some functionality that is not in BIND, you can modify it, and contribute the new feature back to the the community by sending us your source. Download a tar ball from the ISC web site or ftp.isc.org, or a binary from your operating system repository.
- BIND has evolved to be a very flexible, full-featured DNS system. Whatever your application is, BIND most likely has the features required.
- As the first, oldest and most commonly deployed solution, there are more network engineers who are already familiar with BIND than any other system. Help is available via our community mailing-list, or you may subscribe for expert, confidential 7×24 support from the ISC team.
Getting Started
BIND is distributed as source code, with executables provided for Windows. You download the code from this website, unpack the archive, and build it for whatever system you plan to run it on. You will need a UNIX system with an ANSI C compiler, basic POSIX support, and a 64 bit integer type. BIND runs and is supported on a very wide variety of new and old operating systems, including most UNIX and LINUX variants, and some Windows platforms.
Most users run BIND on CentOS, Red Hat Enterprise Linux, Debian, Fedora, FreeBSD, Solaris, Ubuntu or Windows. The most up-to-date versions of BIND are always available from ISC on our web site and ftp server. Most operating systems also offer BIND packages for their users. These may be built with a different set of defaults than the standard BIND distribution and some of them add a version number of their own that does not map exactly to the BIND version.
For configuration assistance, and overall understanding of how to use BIND, the BIND Administrative Reference Manual (ARM) is the primary tool. Resolver users may find Getting started for Recursive Resolvers to be useful. Windows users may find the explanation of the versions available for Windows useful. There are a number of excellent books on BIND. Ron Hutchinson’s DNS for Rocket Scientists is generously posted on the Internet at Zytrax.com and can be a very helpful on-line reference tool.
src: https://www.isc.org/downloads/bind/
Kurioses:
- .dd wurde für die DDR vorgesehen, jedoch ausschließlich intern bei den Universitäten in Jena und Dresden benutzt. Es gab keine DNS-Delegation in den Root-Nameservern der IANA, die Top-Level-Domain .dd wurde nach der Wende durch .de der Bundesrepublik Deutschland ersetzt.[13]
root dns server
root_servers_etc_bind_db.root.debian.txt
Root Servers
The authoritative name servers that serve the DNS root zone, commonly known as the “root servers”, are a network of hundreds of servers in many countries around the world.
They are configured in the DNS root zone as 13 named authorities, as follows.
who is running this infrastructure?
List of Root Servers
| Hostname | IP Addresses | Manager |
|---|---|---|
| a.root-servers.net | 198.41.0.4, 2001:503:ba3e::2:30 | VeriSign, Inc. |
| b.root-servers.net | 192.228.79.201, 2001:500:200::b | University of Southern California (ISI) |
| c.root-servers.net | 192.33.4.12, 2001:500:2::c | Cogent Communications |
| d.root-servers.net | 199.7.91.13, 2001:500:2d::d | University of Maryland |
| e.root-servers.net | 192.203.230.10, 2001:500:a8::e | NASA (Ames Research Center) |
| f.root-servers.net | 192.5.5.241, 2001:500:2f::f | Internet Systems Consortium, Inc. |
| g.root-servers.net | 192.112.36.4, 2001:500:12::d0d | US Department of Defense (NIC) |
| h.root-servers.net | 198.97.190.53, 2001:500:1::53 | US Army (Research Lab) |
| i.root-servers.net | 192.36.148.17, 2001:7fe::53 | Netnod |
| j.root-servers.net | 192.58.128.30, 2001:503:c27::2:30 | VeriSign, Inc. |
| k.root-servers.net | 193.0.14.129, 2001:7fd::1 | RIPE NCC |
| l.root-servers.net | 199.7.83.42, 2001:500:9f::42 | ICANN |
| m.root-servers.net | 202.12.27.33, 2001:dc3::35 | WIDE Project |
src: https://www.iana.org/domains/root/servers
https://www.iana.org/domains/root/files
attacks and centralization
Ausfallsicherheit und Angriffe
Die Root-Server bearbeiten eine sehr große Anzahl von Anfragen, ein erheblicher Teil davon verursacht durch fehlerhafte Software oder Netzwerkkonfiguration.[3] Eine Filterung auf DNS-Ebene findet nicht statt, da dies aufgrund der Einfachheit einer DNS-Anfrage mehr Ressourcen aufwenden würde, als alle Anfragen zu beantworten.
Gemäß RFC 2870 muss jeder Root-Server mit dem dreifachen Peak des am stärksten belasteten Root-Servers umgehen können. Das bedeutet, dass ein Root-Server im Normalbetrieb nur maximal ein Drittel seiner Kapazität ausnutzen darf. Fallen zwei Drittel der Root-Server aus, soll das noch betriebsfähige Drittel die Anfragen beantworten können.
Der Angriff mit der größten Wirkung auf die Root-Server fand am 21. Oktober 2002 statt. Ein DDoS erfolgte 75 Minuten lang mit zusammen 900 MBit/s (1,8 Mpkts/s) auf alle 13 Root-Server. Alle Root-Server blieben zwar lauffähig, da die vorgeschalteten Firewalls den Angriffsverkehr verwarfen, allerdings waren etwa neun Root-Server durch die überfluteten Leitungen schlecht bis gar nicht erreichbar.
Root-Server-Lookups wurden dadurch deutlich verzögert, durch das Caching gab es jedoch kaum Störungen bei den Anwendern. Ausgelöst durch den DDoS-Angriff wurde die Umsetzung von Anycast beschleunigt.
Ein weiterer Angriff fand am 15. Februar 2006 statt, einige Tage, nachdem die Nameserver einer von der ICANN nicht genannten Top-Level-Domain angegriffen worden waren.[4]
Dieser DDoS-Angriff wurde als DNS Amplification Attack durchgeführt, wodurch sich das aufgekommene Datenvolumen vervielfachte. Zwei der lediglich drei angegriffenen Root-Server waren 15 Minuten lang nicht erreichbar.
Am 6. Februar 2007 fand ein weiterer DDoS-Angriff auf die Root-Server und gleichzeitig auf einige TLD-Nameserver statt. Zwei Root-Server waren nicht erreichbar.[5]
Kritik
Kritiker erachten das Mitspracherecht der US-Regierung als problematisch.[6] Dies betrifft zum einen den rechtlichen Status der ICANN, die als kalifornische Institution den US-Gesetzen untersteht. Zum anderen ist die ICANN seit ihrer Gründung mittels eines Memorandum of Understanding (MoU) an das US-Handelsministerium gebunden. Das MoU wurde zuletzt 2006 für drei Jahre verlängert.[7]
Auch VeriSign, die verteilende Instanz der Root-Zonenänderungen, unterliegt als kalifornisches Unternehmen der US-Gesetzgebung.
Um die Einflussnahme der USA auf das Domain Name System zu verringern, entstand unter Mitwirkung von Internetpionieren wie Paul Vixie 2002 das Open Root Server Network (ORSN) als alternativer Root. Der Betrieb des ORSN wurde zum 31. Dezember 2008 eingestellt,[8] 2013 als Reaktion auf PRISM und Tempora jedoch wieder aufgenommen.[9]
src: https://de.wikipedia.org/wiki/Root-Nameserver#Ausfallsicherheit_und_Angriffe
systemd != named
but it does dns resolution for applications? WTF?
“systemd-resolved is a system service that provides network name resolution to local applications.
It implements a caching and validating DNS/DNSSEC stub resolver, as well as an LLMNR resolver and responder.”
DNS Software
bind9 is the defacto standard in “the internet” and on linux. (Debian/Ubuntu/Centos/Redhat/Suse all use bind9)
installing bind9 in Debian/Ubuntu
dpkg -l|grep dns; # what is already installed? ii dnsutils 1:9.9.5.dfsg-9+deb8u10 i386 Clients provided with BIND ii libapache2-mod-dnssd 0.6-3.1 i386 Zeroconf support for Apache 2 via avahi ii libdns-export100 1:9.9.5.dfsg-9+deb8u10 i386 Exported DNS Shared Library ii libdns100 1:9.9.5.dfsg-9+deb8u10 i386 DNS Shared Library used by BIND ii libnss-mdns:i386 0.10-6 i386 NSS module for Multicast DNS name resolution ii python-dnspython 1.12.0-1 all DNS toolkit for Python apt-get install bind9; # install bind9 apt-get install bind9utils; # probably also usefull apt-get install dnsutils; # probably also usefull # what else is there concerning bind apt-cache search bind9; # search repo bind9 - Internet Domain Name Server <- what one is looking for bind9-doc - Documentation for BIND <- can not hurt bind9-host - Version of 'host' bundled with BIND 9.X bind9utils - Utilities for BIND <- sounds good, but i don't know exactly what comes with it libbind9-90 - BIND9 Shared Library used by BIND bindgraph - DNS statistics RRDtool frontend for BIND9 collectd-core - statistics collection and monitoring daemon (core system) designate - OpenStack DNS as a Service - metapackage designate-agent - OpenStack DNS as a Service - agent designate-api - OpenStack DNS as a Service - API server designate-central - OpenStack DNS as a Service - central daemon designate-common - OpenStack DNS as a Service - common files designate-doc - OpenStack DNS as a Service - doc designate-sink - OpenStack DNS as a Service - sink python-designate - OpenStack DNS as a Service - Python libs dlz-ldap-enum - Plug-in for bind9 that uses LDAP data to fulfill ENUM requests dms - bind9 DNS Management System, master server meta-package dms-core - bind9 DNS Management System, core system dms-dr - bind9 DNS Management System, DR scripts and setup. dms-wsgi - bind9 DNS Management System, WSGI JSON http RPC backend. gforge-dns-bind9 - collaborative development tool - DNS management (using Bind9) gadmin-bind - GTK+ configuration tool for bind9
https://packages.debian.org/jessie/bind9utils
installing bind9 in CentOS/REDHAT
rpm -qa --last|grep dns; # what is already installed? dnsmasq-2.66-21.el7.x86_64 Di 02 Mai 2017 15:58:17 CEST yum install bind; # install bind9 yum install bind-utils; # probably also usefull
installing bind9 in SUSE21
either you are a registered (paid) user of SUSE Enterprise Server 12 – or you won’t get any online-updates.
If you want to install software – it is hopefully on the SUSE12-DVD or you will have to checkout and add alternative repositories https://en.opensuse.org/Additional_package_repositories
rpm -qa --last|grep dns; # what is already installed? yast2-dns-server-3.1.24-7.6.noarch Mo 24 Apr 2017 12:58:03 CEST libadns1-1.4-101.65.x86_64 Mo 24 Apr 2017 12:27:04 CES zypper install bind bind-utils; # install bind9 and utilities Repository-Daten werden geladen... Installierte Pakete werden gelesen... Paketabhängigkeiten werden aufgelöst... Die folgenden 3 NEUEN Pakete werden installiert: bind bind-chrootenv libmysqlclient18 3 neue Pakete zu installieren. Gesamtgröße des Downloads: 907,5 KiB. Bereits im Cache gespeichert: 0 B. Nach der Operation werden zusätzlich 4,0 MiB belegt. Fortfahren? [j/n/? zeigt alle Optionen] (j): j Paket bind-chrootenv-9.9.9P1-46.1.x86_64 abrufen (1/3), 43,0 KiB ( 1,6 KiB entpackt) Paket libmysqlclient18-10.0.27-12.1.x86_64 abrufen (2/3), 560,0 KiB ( 3,3 MiB entpackt) Paket bind-9.9.9P1-46.1.x86_64 abrufen (3/3), 304,5 KiB (739,9 KiB entpackt) Überprüfung auf Dateikonflikte läuft: .....................................................................................................................[fertig] (1/3) Installieren: bind-chrootenv-9.9.9P1-46.1.x86_64 ....................................................................................................[fertig] Zusätzliche rpm-Ausgabe: Updating /etc/sysconfig/named... Updating /etc/sysconfig/syslog... (2/3) Installieren: libmysqlclient18-10.0.27-12.1.x86_64 ..................................................................................................[fertig] (3/3) Installieren: bind-9.9.9P1-46.1.x86_64 ..............................................................................................................[fertig] Zusätzliche rpm-Ausgabe: Updating /etc/sysconfig/named... wrote key file "/etc/rndc.key"
DNS commands and examples
there are 3 vms in the LAN with hostnames: suse, centos and debian.
suse:~ # host debian; # checkout what ip address is translated into what host or domain name debian.domainname.local has address 172.20.0.14 suse:~ # host centos centos.domainname.local has address 172.20.0.28 suse:~ # host suse suse.domainname.local has address 172.20.0.25 ### enable / disable bind9-named service ## enable # debian update-rc.d bind9 enable service bind9 start # suse / centos / redhat systemctl enable named service named start ## disable # debian service bind9 stop update-rc.d bind9 disable # suse / centos / redhat service named stop systemctl disable named ### how to restart service? ## suse / centos / redhat systemctl restart named.service; # restart ## debian service bind9 restart # try to get the full zonefile of a domain # this might fail -> because should not be allowed because of DDoS protection dig @dns.dwaves.de dwaves.de -t AXFR ; <<>> DiG 9.9.5-9+deb8u10-Debian <<>> @dns.dwaves.de dwaves.de -t AXFR ; (2 servers found) ;; global options: +cmd dwaves.de. 14400 IN SOA ns1.localhost.ltd. root.dwaves.de. 2017040902 7200 3600 1209600 180 dwaves.de. 14400 IN MX 10 mail.dwaves.de. dwaves.de. 14400 IN TXT "v=spf1 a mx ip4:172.31.1.100 ?all" dwaves.de. 14400 IN NS ns1.localhost.ltd. dwaves.de. 14400 IN NS ns2.localhost.ltd. dwaves.de. 14400 IN A 172.31.1.100 _domainkey.dwaves.de. 14400 IN TXT "t=y\; o=~\;" mail._domainkey.dwaves.de. 14400 IN TXT "k=rsa\; p=ajskdlfjklajsdkfljaklsdjfklajsdkfljaksldjfklajskldfjkaljsdkfljaksldjfklasjdkfl" ftp.dwaves.de. 14400 IN A 172.31.1.100 mail.dwaves.de. 14400 IN A 172.31.1.100 pop.dwaves.de. 14400 IN A 172.31.1.100 www.dwaves.de. 14400 IN A 172.31.1.100 dwaves.de. 14400 IN SOA ns1.localhost.ltd. root.dwaves.de. 2017040902 7200 3600 1209600 180 ;; Query time: 22 msec ;; SERVER: 78.46.249.71#53(78.46.249.71) ;; WHEN: Tue May 09 10:35:12 CEST 2017 ;; XFR size: 13 records (messages 1, bytes 588) # How to find SOA (Source Of Authority, domain server) of a domain? master-dns-server of a web server? dig SOA +multiline dwaves.de ; <<>> DiG 9.9.5-9+deb8u10-Debian <<>> SOA +multiline dwaves.de ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 4830 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 3 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4000 ;; QUESTION SECTION: ;dwaves.de. IN SOA ;; ANSWER SECTION: dwaves.de. 86395 IN SOA ns1.domainoffensive.de. hostmaster.domain-offensive.de. ( 2017042211 ; serial 10800 ; refresh (3 hours) 3600 ; retry (1 hour) 604800 ; expire (1 week) 86400 ; minimum (1 day) ) ;; ADDITIONAL SECTION: ns1.domainoffensive.de. 3540 IN A 95.130.22.130 ns1.domainoffensive.de. 3180 IN AAAA 2a02:2940:0:c004::130 ;; Query time: 4 msec ;; SERVER: 172.20.0.2#53(172.20.0.2) ;; WHEN: Tue May 09 10:01:00 CEST 2017 ;; MSG SIZE rcvd: 166 ### step by step name resolution dig +add +trace @8.8.8.8 www.dwaves.de ; <<>> DiG 9.9.4-RedHat-9.9.4-38.el7_3.3 <<>> +add +trace @8.8.8.8 www.dwaves.de ; (1 server found) ;; global options: +cmd . 219029 IN NS e.root-servers.net. . 219029 IN NS h.root-servers.net. . 219029 IN NS l.root-servers.net. . 219029 IN NS i.root-servers.net. . 219029 IN NS a.root-servers.net. . 219029 IN NS d.root-servers.net. . 219029 IN NS c.root-servers.net. . 219029 IN NS b.root-servers.net. . 219029 IN NS j.root-servers.net. . 219029 IN NS k.root-servers.net. . 219029 IN NS g.root-servers.net. . 219029 IN NS m.root-servers.net. . 219029 IN NS f.root-servers.net. . 219029 IN RRSIG NS 8 0 518400 20170521170000 20170508160000 14796 . jcbz3cVO6N5XAjpK2QSLcsiNAuRx7/Zcj35o0zMdT7baoT69ICm9hn18 nkmvoCUclz/k1Jin3QgD5CqgBmj8m3rVXlWFtD0YzDbKm+FhrqFRqv5h CdK+2sefHgMr+nnQl8h8nENNUiExK/YOdxeYvJ89aWzUEG4bvcoOWlJ0 rMMnAg3pQTcxNV8eCjMvTo2NZuGgulV0KJBDEZwh6q7WE7ArtPdbUXMb jKgU802MU98joviAJzdidRLCuQc8StzxjELtgyAlMHdAJu5h+ceEiY9L twkT3Cv+bgBufw0Yjnwf4zdObzVNsbl7GhpaPVGLDhAeOPoJX5qJX4e2 HfElVw== ;; Received 525 bytes from 8.8.8.8#53(8.8.8.8) in 379 ms de. 172800 IN NS f.nic.de. de. 172800 IN NS l.de.net. de. 172800 IN NS s.de.net. de. 172800 IN NS z.nic.de. de. 172800 IN NS a.nic.de. de. 172800 IN NS n.de.net. de. 86400 IN DS 39227 8 2 AAB73083B9EF70E4A5E94769A418AC12E887FC3C0875EF206C3451DC 40B6C4FA de. 86400 IN RRSIG DS 8 1 86400 20170522050000 20170509040000 14796 . VDjCrWKH0VTdUd2u2tZyZljyiBg9nfkcNPbKDbrAtPmGlMhS5JGOcJvM Zst/L762tu1J5Bu0afqMEffcA0u2N1oboDsiwAI30ITmDE49qJ8b5RKy D85YNvtiRCllrxNPz5KKboEWksOj15/k+ZpeUUaiKT1fStKSq6+qt3hP XYjxnCA5SBTXjkN/Y8RdlrGSmNDx7c+PM3ZaHptp9aXmr85zwl7NHfjl Nq5gNA68XAw1YhjdUzRsL1oIHtkZMfudZ75zzhnbIaozHTezvfNdWCQ7 X2xAMrNMbbeKgAMAo9KkajTCW5Q4y6OhR0sQgx+owiTlPlKDP/YYm84s 7Oib8A== ;; Received 691 bytes from 192.33.4.12#53(c.root-servers.net) in 199 ms dwaves.de. 86400 IN NS ns1.domainoffensive.de. dwaves.de. 86400 IN NS ns2.domainoffensive.de. dwaves.de. 86400 IN NS ns3.domainoffensive.de. h319dm5gc3edek691vqbhehot7vggj2b.de. 7200 IN NSEC3 1 1 15 BA5EBA11 H31BJ3G4QCC5ICBKQH14CB2K8KTQICPL NS SOA RRSIG DNSKEY NSEC3PARAM h319dm5gc3edek691vqbhehot7vggj2b.de. 7200 IN RRSIG NSEC3 8 2 7200 20170516090125 20170509090125 11884 de. cQdflumcmOHlFfcOKaTVBcfkTZnH/reKqm4T92C9DKHzhmtTCFcZVO7N Ja+QYSNd4suhuEALgkacUc4e1SeFIVMM7bF4WM+9nb3iCT1JUBdixhUC bHHSJ/FhXvQbkAht2FVpvObDQrr4crEX7pfdjEGlJTfe9vZZelUiJ9vT VgY= js21fd6n8hdn1hbr6i57e843sagjtgue.de. 7200 IN NSEC3 1 1 15 BA5EBA11 JS26MHADL8MQ6Q5J4IP56DJ1T54DMDV1 A RRSIG js21fd6n8hdn1hbr6i57e843sagjtgue.de. 7200 IN RRSIG NSEC3 8 2 7200 20170516090125 20170509090125 11884 de. t4mhKWoUHUM6wgk97I36ZPReVfZX7ji0MWJ0AnwTxtgYOP3vGjE0UnCT ccbV62HuwoXD2L8oMKeOh7HJQOlIVhcF5UCglfwaNk1W0+I3MLvZXqNG QwxGAFa2B1QEHGNk0E0KKdL5/o0qRp2X/LqvzHWj+BqJZa4XsueYrMZO m78= ;; Received 603 bytes from 194.246.96.1#53(z.nic.de) in 101 ms www.dwaves.de. 86400 IN A 78.46.249.71 ;; Received 58 bytes from 95.130.22.138#53(ns3.domainoffensive.de) in 28 ms
named example output /var/log/messages: named.messages.txt
ZoneFile
in SUSE12 those are located under:
ll /var/lib/named insgesamt 12 -rw-r--r-- 1 root root 192 19. Nov 2009 127.0.0.zone <- this is a zone file drwxr-xr-x 1 root root 26 8. Mai 16:42 dev drwxr-xr-x 1 named named 0 23. Sep 2016 dyn drwxr-xr-x 1 root root 110 8. Mai 16:15 etc drwxr-xr-x 1 root root 14 8. Mai 14:33 lib drwxr-xr-x 1 root root 14 8. Mai 14:33 lib64 -rw-r--r-- 1 root root 182 19. Nov 2009 localhost.zone <- this is a zone file drwxr-xr-x 1 named named 0 23. Sep 2016 log drwxr-xr-x 1 root root 0 23. Sep 2016 master drwxr-xr-x 1 root root 0 8. Mai 14:33 proc -rw-r--r-- 1 root root 3048 23. Sep 2016 root.hint drwxr-xr-x 1 named named 0 23. Sep 2016 slave drwxr-xr-x 1 root root 18 8. Mai 12:08 var ### let's create an example zone file vim /var/lib/named/ich.de.zone;
in Debian8.7 those are located under:
root@debian:~# ll /etc/bind
total 52K
-rw-r--r-- 1 root root 2.4K Feb 26 01:15 bind.keys
-rw-r--r-- 1 root root 237 Feb 26 01:15 db.0
-rw-r--r-- 1 root root 271 Feb 26 01:15 db.127
-rw-r--r-- 1 root root 237 Feb 26 01:15 db.255
-rw-r--r-- 1 root root 353 Feb 26 01:15 db.empty
-rw-r--r-- 1 root root 270 Feb 26 01:15 db.local
-rw-r--r-- 1 root root 3.0K Feb 26 01:15 db.root
-rw-r--r-- 1 root bind 463 Feb 26 01:15 named.conf
-rw-r--r-- 1 root bind 490 Feb 26 01:15 named.conf.default-zones
-rw-r--r-- 1 root bind 165 Feb 26 01:15 named.conf.local
-rw-r--r-- 1 root bind 890 May 8 13:50 named.conf.options
-rw-r----- 1 bind bind 77 May 8 13:50 rndc.key
-rw-r--r-- 1 root root 1.3K Feb 26 01:15 zones.rfc1918
vim /etc/bind/db.domainname; # create new zone-domain-file
;; db.domainname
;; Forwardlookupzone für domainname
;;
$TTL 2D
@ IN SOA rechnername.domainname. mail.domainname. (
2006032201 ; Serial
8H ; Refresh
2H ; Retry
4W ; Expire
3H ) ; NX (TTL Negativ Cache)
@ IN NS rechnername.domainname.
IN MX 10 mailserver.domainname.
IN A 192.168.0.10
rechnername IN A 192.168.0.10
localhost IN A 127.0.0.1
rechner1 IN A 192.168.0.200
mailserver IN A 192.168.0.201
rechner2 IN CNAME mailserver
explained test-example zone file: (no guarantee if this works)
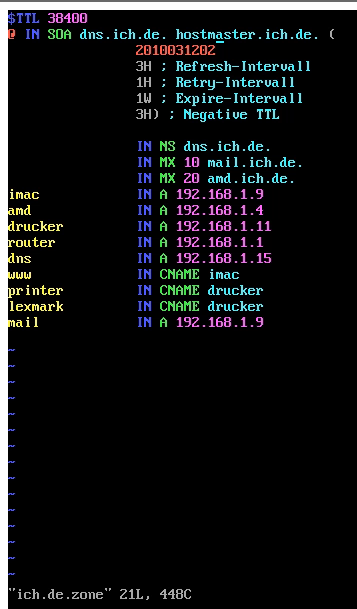
vim /var/lib/named/ich.de.zone; # create new zone file
### explanation:
$TTL 38400 <- Time to Live, 38400/60/60 = 10.66 hours, how often to refresh the dns cache, you might want to reduce this to minutes before moving a domain to a new ip
@ IN SOA <- IN = internet, SOA = Source Of Authority
dns.ich.de. <- domain-name with a dot at the end
hostmaster.ich.de. <- mail address of admin
(
2010030201 <- YYYYMMDDXX <- is basically the "serial-number" - how recent is the zone-file of this server? (higher = more up to date)
3H ; Refresh-Intervall <- every 3 hours slave-server asks master-dns-server (SOA) if there are changes (serial-number has increased?)
1H ; Retry-Intervall <- if slave-server can't reach master - slave retries to reach master every 1h
1W ; Expire-Intervall <- if slave can't reach master for 1 WEEK slave-server declares this zone file invalid
3H) ; NX (TTL Negativ Cache) <- how long should a negative response ("Name Error" / "NXDOMAIN") be cached (from 0Sec to 3h). -> this space is intentional do not delete! <-
IN NS dns.ich.de. <- all INternet NameServers of this domain - who is the nameserver of this domain?
IN MX 50 mail1.ich.de. <- who is the mailserver of this domain? 50 = higher priority, primary mail server
IN MX 100 mail2.ich.de. <- who is the mailserver of this domain? 100 = lower priority, backup mail server
debian IN A 172.20.0.14
centos IN A 172.20.0.7
dns IN A 172.20.0.252
www IN CNAME debian
how to get zone-file of a domain/real life example of domain-offensive.de (do.de):
this might fail, because should not be allowed because of DDoS protection.
# try to get the full zonefile of a domain dig @dns.dwaves.de dwaves.de -t AXFR ; <<>> DiG 9.9.5-9+deb8u10-Debian <<>> @dns.dwaves.de dwaves.de -t AXFR ; (2 servers found) ;; global options: +cmd dwaves.de. 14400 IN SOA ns1.localhost.ltd. root.dwaves.de. 2017040902 7200 3600 1209600 180 dwaves.de. 14400 IN MX 10 mail.dwaves.de. dwaves.de. 14400 IN TXT "v=spf1 a mx ip4:172.31.1.100 ?all" dwaves.de. 14400 IN NS ns1.localhost.ltd. dwaves.de. 14400 IN NS ns2.localhost.ltd. dwaves.de. 14400 IN A 172.31.1.100 _domainkey.dwaves.de. 14400 IN TXT "t=y\; o=~\;" mail._domainkey.dwaves.de. 14400 IN TXT "k=rsa\; p=ajksldfjklajsdfkljaskdlfjaklsjdfklajsdkfljaklsdjfklajsdkfl" ftp.dwaves.de. 14400 IN A 172.31.1.100 mail.dwaves.de. 14400 IN A 172.31.1.100 pop.dwaves.de. 14400 IN A 172.31.1.100 www.dwaves.de. 14400 IN A 172.31.1.100 dwaves.de. 14400 IN SOA ns1.localhost.ltd. root.dwaves.de. 2017040902 7200 3600 1209600 180 ;; Query time: 22 msec ;; SERVER: 78.46.249.71#53(78.46.249.71) ;; WHEN: Tue May 09 10:35:12 CEST 2017 ;; XFR size: 13 records (messages 1, bytes 588) # if it fails you probably get something like dig @some-domain.com some-domain.com -t AXFR ;; Connection to 88.198.176.XXX#53(88.198.176.XXX) for some-domain.com failed: connection refused. # or dig @dns.yahoo.de yahoo.de -t AXFR ; <<>> DiG 9.9.5-9+deb8u10-Debian <<>> @dns.yahoo.de yahoo.de -t AXFR ; (1 server found) ;; global options: +cmd ;; connection timed out; no servers could be reached whois 172.31.0.0 # ARIN WHOIS data and services are subject to the Terms of Use # available at: https://www.arin.net/whois_tou.html # # If you see inaccuracies in the results, please report at # https://www.arin.net/public/whoisinaccuracy/index.xhtml # The following results may also be obtained via: # https://whois.arin.net/rest/nets;q=172.31.0.0?showDetails=true&showARIN=false&showNonArinTopLevelNet=false&ext=netref2 NetRange: 172.16.0.0 - 172.31.255.255 CIDR: 172.16.0.0/12 NetName: PRIVATE-ADDRESS-BBLK-RFC1918-IANA-RESERVED NetHandle: NET-172-16-0-0-1 Parent: NET172 (NET-172-0-0-0-0) NetType: IANA Special Use OriginAS: Organization: Internet Assigned Numbers Authority (IANA) RegDate: 1994-03-15 Updated: 2013-08-30 Comment: These addresses are in use by many millions of independently operated networks, which might be as small as a single computer connected to a home gateway, and are automatically configured in hundreds of millions of devices. They are only intended for use within a private context and traffic that needs to cross the Internet will need to use a different, unique address. Comment: Comment: These addresses can be used by anyone without any need to coordinate with IANA or an Internet registry. The traffic from these addresses does not come from ICANN or IANA. We are not the source of activity you may see on logs or in e-mail records. Please refer to http://www.iana.org/abuse/answers Comment: Comment: These addresses were assigned by the IETF, the organization that develops Internet protocols, in the Best Current Practice document, RFC 1918 which can be found at:
another example file:
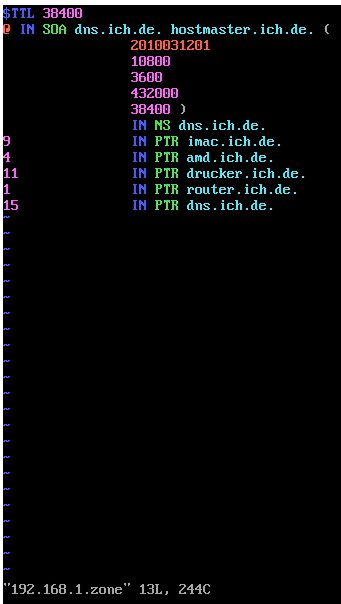
ich.de.zone – reverse lookup
Links: https://www.centos.org/docs/5/html/Deployment_Guide-en-US/s1-bind-zone.html
BIND log files
# suse tail -f /var/log/messages # debian tail -f /var/log/syslog May 9 11:55:39 debian named[1893]: zone 0.20.172-in-addr.arpa/IN: refresh: retry limit for master 172.20.0.25#53 exceeded (source 0.0.0.0#0) May 9 11:55:39 debian named[1893]: zone 0.20.172-in-addr.arpa/IN: Transfer started. May 9 11:55:39 debian named[1893]: zone ich.de/IN: refresh: retry limit for master 172.20.0.25#53 exceeded (source 0.0.0.0#0) May 9 11:55:39 debian named[1893]: zone ich.de/IN: Transfer started. May 9 11:57:28 debian systemd[1]: Starting Session 6 of user user. May 9 11:57:28 debian systemd[1]: Started Session 6 of user user. May 9 11:57:46 debian named[1893]: transfer of '0.20.172-in-addr.arpa/IN' from 172.20.0.25#53: failed to connect: timed out May 9 11:57:46 debian named[1893]: transfer of '0.20.172-in-addr.arpa/IN' from 172.20.0.25#53: Transfer completed: 0 messages, 0 records, 0 bytes, 127.198 secs (0 bytes/sec) May 9 11:57:47 debian named[1893]: transfer of 'ich.de/IN' from 172.20.0.25#53: failed to connect: timed out May 9 11:57:47 debian named[1893]: transfer of 'ich.de/IN' from 172.20.0.25#53: Transfer completed: 0 messages, 0 records, 0 bytes, 127.210 secs (0 bytes/sec)
BIND working directory
the binary-process-service of bind9 is called named – and it can have it’s own working directory.
If you have installed the bind-chroot package, the BIND service will run in the /var/named/chroot environment. All configuration files will be moved there. As such, you can find the zone files in /var/named/chroot/var/named. (src)
Under Debian/Ubuntu sind die wichtigsten bind-dateien im verzeichnis /etc/bind/ und Bind9#Bind_Chroot könnte man nachinstallieren.
suse:~ # cat /etc/named.conf |grep directory # The directory statement defines the name server's working directory directory "/var/lib/named"; suse:~ # ll /var/lib/named/ insgesamt 12 -rw-r--r-- 1 root root 192 19. Nov 2009 127.0.0.zone drwxr-xr-x 1 root root 20 8. Mai 12:08 dev drwxr-xr-x 1 named named 0 23. Sep 2016 dyn drwxr-xr-x 1 root root 110 8. Mai 14:33 etc drwxr-xr-x 1 root root 14 8. Mai 14:33 lib drwxr-xr-x 1 root root 14 8. Mai 14:33 lib64 -rw-r--r-- 1 root root 182 19. Nov 2009 localhost.zone drwxr-xr-x 1 named named 0 23. Sep 2016 log drwxr-xr-x 1 root root 0 23. Sep 2016 master drwxr-xr-x 1 root root 0 8. Mai 14:33 proc -rw-r--r-- 1 root root 3048 23. Sep 2016 root.hint drwxr-xr-x 1 named named 0 23. Sep 2016 slave drwxr-xr-x 1 root root 18 8. Mai 12:08 var [root@centos ~]# cat /etc/named.conf |grep directory directory "/var/named"; managed-keys-directory "/var/named/dynamic"; [root@centos ~]# ll /var/named insgesamt 16K drwxr-x---. 5 root named 127 8. Mai 14:19 . drwxr-xr-x. 20 root root 280 8. Mai 14:19 .. drwxrwx---. 2 named named 6 19. Apr 17:53 data drwxrwx---. 2 named named 6 19. Apr 17:53 dynamic -rw-r-----. 1 root named 2,1K 28. Jan 2013 named.ca -rw-r-----. 1 root named 152 15. Dez 2009 named.empty -rw-r-----. 1 root named 152 21. Jun 2007 named.localhost -rw-r-----. 1 root named 168 15. Dez 2009 named.loopback drwxrwx---. 2 named named 6 19. Apr 17:53 slaves
DNS config files – in general
the main bind-named-config file is called named.conf and located somewhere in the /etc directory 😀 (find / -iname named.conf) find it yourself 😀
# main config file of bind9: named.conf ###### Debian, different location and it is split over more config files than in SUSE/RedHat/CentOS /etc/bind/named.conf; vim /etc/bind/named.conf.default-zones; # zones ###### CentOS/RedHat /etc/named.conf ###### SUSE, same location but different content than RedHat/CentOS /etc/named.conf vim /etc/named.conf; # let's checkout SUSE's config
DNS config file named.conf in detail – mainly focusing on SUSE12, but also Centos7/Debian8.7
Debian8.7 Manpage: named.conf.man.txt
vim /etc/named.conf; # let's checkout SUSE's config # Copyright (c) 2001-2004 SuSE Linux AG, Nuernberg, Germany. <- aha # All rights reserved. # # Author: Frank Bodammer, Lars Mueller <lmuelle@suse.de> <- ask this guy if it does not work # # /etc/named.conf # # This is a sample configuration file for the name server BIND 9. It works as # a caching only name server without modification. # # A sample configuration for setting up your own domain can be found in # /usr/share/doc/packages/bind/sample-config. # # A description of all available options can be found in # /usr/share/doc/packages/bind/misc/options. options { # The directory statement defines the name server's working directory directory "/var/lib/named"; # enable DNSSEC validation # # If BIND logs error messages about the root key being expired, you # will need to update your keys. See https://www.isc.org/bind-keys # # dnssec-enable yes (default), indicates that a secure DNS service # is being used which may be one, or more, of TSIG # (for securing zone transfers or DDNS updates), SIG(0) # (for securing DDNS updates) or DNSSEC. #dnssec-enable yes; # dnssec-validation yes (default), indicates that a resolver # (a caching or caching-only name server) will attempt to validate # replies from DNSSEC enabled (signed) zones. To perform this task # the server also needs either a valid trusted-keys clause # (containing one or more trusted-anchors or a managed-keys clause. #dnssec-validation auto; managed-keys-directory "/var/lib/named/dyn/"; # Write dump and statistics file to the log subdirectory. The # pathenames are relative to the chroot jail. dump-file "/var/log/named_dump.db"; statistics-file "/var/log/named.stats"; # The forwarders record contains a list of servers to which queries # should be forwarded. Enable this line and modify the IP address to # your provider's name server. Up to three servers may be listed. ### these are the nameservers, this nameserver will ask - if this nameserver does not have an answer to "Who has heise.de?" ### here you might want to put your ISP's DNS Server or even your local DNS-Router, i completely ignore ISP's DNS and put both OpenDNS Servers here forwarders { 208.67.222.222; 208.67.220.220; }; # Enable the next entry to prefer usage of the name server declared in # the forwarders section. #forward first; # The listen-on record contains a list of local network interfaces to # listen on. Optionally the port can be specified. Default is to # listen on all interfaces found on your system. The default port is # 53. ### you probably need to uncomment this to make your DNS server work, otherwise it won't answer any requests #listen-on port 53 { 127.0.0.1; }; # The listen-on-v6 record enables or disables listening on IPv6 # interfaces. Allowed values are 'any' and 'none' or a list of # addresses. listen-on-v6 { any; }; # The next three statements may be needed if a firewall stands between # the local server and the internet. #query-source address * port 53; #transfer-source * port 53; #notify-source * port 53; # The allow-query record contains a list of networks or IP addresses # to accept and deny queries from. The default is to allow queries # from all hosts. #allow-query { 127.0.0.1; }; # If notify is set to yes (default), notify messages are sent to other # name servers when the the zone data is changed. Instead of setting # a global 'notify' statement in the 'options' section, a separate # 'notify' can be added to each zone definition. ### if you have DNS-slave servers, you might want to put this to yes notify no; disable-empty-zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.IP6.ARPA"; }; # To configure named's logging remove the leading '#' characters of the # following examples. #logging { # # Log queries to a file limited to a size of 100 MB. # channel query_logging { # file "/var/log/named_querylog" # versions 3 size 100M; # print-time yes; // timestamp log entries # }; # category queries { # query_logging; # }; # # # Or log this kind alternatively to syslog. # channel syslog_queries { # syslog user; # severity info; # }; # category queries { syslog_queries; }; # # # Log general name server errors to syslog. # channel syslog_errors { # syslog user; # severity error; # }; # category default { syslog_errors; }; # # # Don't log lame server messages. # category lame-servers { null; }; #}; # The following zone definitions don't need any modification. The first one # is the definition of the root name servers. The second one defines # localhost while the third defines the reverse lookup for localhost. ### root.hint contains all root-dns-server zone "." in { type hint; file "root.hint"; }; zone "localhost" in { type master; file "localhost.zone"; }; zone "0.0.127.in-addr.arpa" in { type master; file "127.0.0.zone"; }; zone "0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN { type master; file "127.0.0.zone"; }; # Include the meta include file generated by createNamedConfInclude. This # includes all files as configured in NAMED_CONF_INCLUDE_FILES from # /etc/sysconfig/named include "/etc/named.conf.include"; # You can insert further zone records for your own domains below or create # single files in /etc/named.d/ and add the file names to # NAMED_CONF_INCLUDE_FILES. # See /usr/share/doc/packages/bind/README.SUSE for more details. #### let's checkout root.hint suse:~ # vim /var/lib/named/root.hint ; This file holds the information on root name servers needed to ; initialize cache of Internet domain name servers ; (e.g. reference this file in the "cache . " ; configuration file of BIND domain name servers). ; ; This file is made available by InterNIC ; under anonymous FTP as ; file /domain/named.cache ; on server FTP.INTERNIC.NET ; -OR- RS.INTERNIC.NET ; ; last update: Jan 3, 2013 ; related version of root zone: 2013010300 ; ; formerly NS.INTERNIC.NET ; . 3600000 IN NS A.ROOT-SERVERS.NET. A.ROOT-SERVERS.NET. 3600000 A 198.41.0.4 A.ROOT-SERVERS.NET. 3600000 AAAA 2001:503:BA3E::2:30 ; ; FORMERLY NS1.ISI.EDU ; . 3600000 NS B.ROOT-SERVERS.NET. B.ROOT-SERVERS.NET. 3600000 A 192.228.79.201 ; ; FORMERLY C.PSI.NET ; . 3600000 NS C.ROOT-SERVERS.NET. C.ROOT-SERVERS.NET. 3600000 A 192.33.4.12 ; ; FORMERLY TERP.UMD.EDU ; . 3600000 NS D.ROOT-SERVERS.NET. D.ROOT-SERVERS.NET. 3600000 A 199.7.91.13 D.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:2D::D ; ; FORMERLY NS.NASA.GOV ; . 3600000 NS E.ROOT-SERVERS.NET. E.ROOT-SERVERS.NET. 3600000 A 192.203.230.10 ; ; FORMERLY NS.ISC.ORG ; . 3600000 NS F.ROOT-SERVERS.NET. F.ROOT-SERVERS.NET. 3600000 A 192.5.5.241 F.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:2F::F ; ; FORMERLY NS.NIC.DDN.MIL ; . 3600000 NS G.ROOT-SERVERS.NET. G.ROOT-SERVERS.NET. 3600000 A 192.112.36.4 ; ; FORMERLY AOS.ARL.ARMY.MIL ; . 3600000 NS H.ROOT-SERVERS.NET. H.ROOT-SERVERS.NET. 3600000 A 128.63.2.53 H.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:1::803F:235 ; ; FORMERLY NIC.NORDU.NET ; . 3600000 NS I.ROOT-SERVERS.NET. I.ROOT-SERVERS.NET. 3600000 A 192.36.148.17 I.ROOT-SERVERS.NET. 3600000 AAAA 2001:7FE::53 ; ; OPERATED BY VERISIGN, INC. ; . 3600000 NS J.ROOT-SERVERS.NET. J.ROOT-SERVERS.NET. 3600000 A 192.58.128.30 J.ROOT-SERVERS.NET. 3600000 AAAA 2001:503:C27::2:30 ; ; OPERATED BY RIPE NCC ; . 3600000 NS K.ROOT-SERVERS.NET. K.ROOT-SERVERS.NET. 3600000 A 193.0.14.129 K.ROOT-SERVERS.NET. 3600000 AAAA 2001:7FD::1 ; ; OPERATED BY ICANN ; . 3600000 NS L.ROOT-SERVERS.NET. L.ROOT-SERVERS.NET. 3600000 A 199.7.83.42 L.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:3::42 ; ; OPERATED BY WIDE ; . 3600000 NS M.ROOT-SERVERS.NET. M.ROOT-SERVERS.NET. 3600000 A 202.12.27.33 M.ROOT-SERVERS.NET. 3600000 AAAA 2001:DC3::35 ; End of File ####### CentOS vim /etc/named.conf // named.conf // // Provided by Red Hat bind package to configure the ISC BIND named(8) DNS // server as a caching only nameserver (as a localhost DNS resolver only). // // See /usr/share/doc/bind*/sample/ for example named configuration files. // // See the BIND Administrator's Reference Manual (ARM) for details about the // configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html options { listen-on port 53 { 127.0.0.1; }; listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; allow-query { localhost; }; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable yes; dnssec-validation yes; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key"; # let's checkout the next included config file vim /etc/named.rfc1912.zones // named.rfc1912.zones: // // Provided by Red Hat caching-nameserver package // // ISC BIND named zone configuration for zones recommended by // RFC 1912 section 4.1 : localhost TLDs and address zones // and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt // (c)2007 R W Franks // // See /usr/share/doc/bind*/sample/ for example named configuration files. // zone "localhost.localdomain" IN { type master; file "named.localhost"; allow-update { none; }; }; zone "localhost" IN { type master; file "named.localhost"; allow-update { none; }; }; zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN { type master; file "named.loopback"; allow-update { none; }; }; zone "1.0.0.127.in-addr.arpa" IN { type master; file "named.loopback"; allow-update { none; }; }; zone "0.in-addr.arpa" IN { type master; file "named.empty"; allow-update { none; }; }; # let's checkout the next included config file vim /etc/named.root.key managed-keys { # DNSKEY for the root zone. # Updates are published on root-dnssec-announce@icann.org . initial-key 257 3 8 "AwEAAagAIKlVZrpC6Ia7gEzahOR+9W29euxhJhVVLOyQbSEW0O8gcCjF FVQUTf6v58fLjwBd0YI0EzrAcQqBGCzh/RStIoO8g0NfnfL2MTJRkxoX bfDaUeVPQuYEhg37NZWAJQ9VnMVDxP/VHL496M/QZxkjf5/Efucp2gaD X6RS6CXpoY68LsvPVjR0ZSwzz1apAzvN9dlzEheX7ICJBBtuA6G3LQpz W5hOA2hzCTMjJPJ8LbqF6dsV6DoBQzgul0sGIcGOYl7OyQdXfZ57relS Qageu+ipAdTTJ25AsRTAoub8ONGcLmqrAmRLKBP1dfwhYB4N7knNnulq QxA+Uk1ihz0="; };
DNS config file hosts – SUSE12/Centos7/Debian8.7
Debian 8.7 Manpage: hosts.man.txt
# files that exist even without bind # /etc/hosts usually manual LAN-hosts ip<->name style [root@centos ~]# cat /etc/hosts 127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6 suse:~ # cat /etc/hosts # # hosts This file describes a number of hostname-to-address # mappings for the TCP/IP subsystem. It is mostly # used at boot time, when no name servers are running. # On small systems, this file can be used instead of a # "named" name server. # Syntax: # # IP-Address Full-Qualified-Hostname Short-Hostname # 127.0.0.1 localhost # special IPv6 addresses ::1 localhost ipv6-localhost ipv6-loopback fe00::0 ipv6-localnet ff00::0 ipv6-mcastprefix ff02::1 ipv6-allnodes ff02::2 ipv6-allrouters ff02::3 ipv6-allhosts root@debian:~# cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 debian # The following lines are desirable for IPv6 capable hosts ::1 localhost ip6-localhost ip6-loopback ff02::1 ip6-allnodes ff02::2 ip6-allrouters
DNS config file resov.conf – SUSE12/Centos7/Debian8.7
Debian8.7 Manpage: resolv.conf.man.txt
#### resolv.conf <- is automatically altered/changed by DHCP root@debian:~# cat /etc/resolv.conf domain domainname.local search domainname.local nameserver 172.20.0.2 [root@centos ~]# cat /etc/resolv.conf # Generated by NetworkManager search domainname.local nameserver 172.20.0.2
DNS config file nsswitch.conf – SUSE12/Centos7/Debian8.7
Debian8.7 Manpage: nsswitch.conf.man.txt
[root@centos ~]# cat /etc/nsswitch.conf # # /etc/nsswitch.conf # # An example Name Service Switch config file. This file should be # sorted with the most-used services at the beginning. # # The entry '[NOTFOUND=return]' means that the search for an # entry should stop if the search in the previous entry turned # up nothing. Note that if the search failed due to some other reason # (like no NIS server responding) then the search continues with the # next entry. # # Valid entries include: # # nisplus Use NIS+ (NIS version 3) # nis Use NIS (NIS version 2), also called YP # dns Use DNS (Domain Name Service) # files Use the local files # db Use the local database (.db) files # compat Use NIS on compat mode # hesiod Use Hesiod for user lookups # [NOTFOUND=return] Stop searching if not found so far # # To use db, put the "db" in front of "files" for entries you want to be # looked up first in the databases # # Example: #passwd: db files nisplus nis #shadow: db files nisplus nis #group: db files nisplus nis passwd: files sss shadow: files sss group: files sss #initgroups: files #hosts: db files nisplus nis dns hosts: files dns myhostname # Example - obey only what nisplus tells us... #services: nisplus [NOTFOUND=return] files #networks: nisplus [NOTFOUND=return] files #protocols: nisplus [NOTFOUND=return] files #rpc: nisplus [NOTFOUND=return] files #ethers: nisplus [NOTFOUND=return] files #netmasks: nisplus [NOTFOUND=return] files bootparams: nisplus [NOTFOUND=return] files ethers: files netmasks: files networks: files protocols: files rpc: files services: files sss netgroup: files sss publickey: nisplus automount: files aliases: files nisplus suse:~ # cat /etc/nsswitch.conf # # /etc/nsswitch.conf # # An example Name Service Switch config file. This file should be # sorted with the most-used services at the beginning. # # The entry '[NOTFOUND=return]' means that the search for an # entry should stop if the search in the previous entry turned # up nothing. Note that if the search failed due to some other reason # (like no NIS server responding) then the search continues with the # next entry. # # Legal entries are: # # compat Use compatibility setup # nisplus Use NIS+ (NIS version 3) # nis Use NIS (NIS version 2), also called YP # dns Use DNS (Domain Name Service) # files Use the local files # [NOTFOUND=return] Stop searching if not found so far # # For more information, please read the nsswitch.conf.5 manual page. # # passwd: files nis # shadow: files nis # group: files nis passwd: compat group: compat hosts: files dns networks: files dns services: files protocols: files rpc: files ethers: files netmasks: files netgroup: files nis publickey: files bootparams: files automount: files nis aliases: files root@debian:~# cat /etc/host.conf multi on [root@centos ~]# cat /etc/host.conf multi on suse:~ # cat /etc/host.conf # # /etc/host.conf - resolver configuration file # # Please read the manual page host.conf(5) for more information. # # # The following option is only used by binaries linked against # libc4 or libc5. This line should be in sync with the "hosts" # option in /etc/nsswitch.conf. # order hosts, bind # # The following options are used by the resolver library: # multi on
Links:
https://wiki.ubuntuusers.de/DNS-Server_Bind/
http://www.silicon.de/41638648/android-malware-switcher-hackt-wlan-router-und-aendert-das-dns/
https://www.welivesecurity.com/deutsch/2017/02/28/dns-attacken-fake-webseiten/
http://thesprawl.org/projects/dnschef/
https://blog.apnic.net/2017/07/25/ietf-99-prague-theres-lot-going-dns/
Tweets:
liked this article?
- only together we can create a truly free world
- plz support dwaves to keep it up & running!
- (yes the info on the internet is (mostly) free but beer is still not free (still have to work on that))
- really really hate advertisement
- contribute: whenever a solution was found, blog about it for others to find!
- talk about, recommend & link to this blog and articles
- thanks to all who contribute!